Module Group 2: Modules 5 – 8 Group Exam Answers
Networking Essentials (Version 2) – Modules 5 – 8: Network Protocols and Architecture Group Exam Answers
How to find: Press “Ctrl + F” in the browser and fill in whatever wording is in the question to find that question/answer. If the question is not here, find it in Questions Bank.
NOTE: If you have the new question on this test, please comment Question and Multiple-Choice list in form below this article. We will update answers for you in the shortest time. Thank you! We truly value your contribution to the website.
1. What action does the ARP process take when a host needs to build a frame, but the ARP cache does not contain an address mapping?
- The ARP process sends out an ARP request to the IPv4 broadcast address to discover the MAC address of the destination device.
- The ARP process sends out an ARP request to the IPv4 broadcast address to discover the IPv4 address of the destination device.
- The ARP process sends out an ARP request to the Ethernet broadcast address to discover the IPv4 address of the destination device.
- The ARP process sends out an ARP request to the Ethernet broadcast address to discover the MAC address of the destination device.
Explanation: The address resolution protocol (ARP) maintains a cache of MAC to IPv4 address mappings on the local computer. If there is no mapping in the cache for a specific IPv4 address, then the ARP process sends an Ethernet broadcast on the local link in an attempt to resolve the destination IPv4 address to a MAC address.
2. Which three layers of the OSI model map to the application layer of the TCP/IP model? (Choose three.)
- session
- application
- transport
- presentation
- data link
- network
Explanation: The application layer of the TCP/IP model maps to the top three layers of the OSI model, which are the application, presentation, and session layers.
3. Which statement is true about MAC addresses?
- The first three bytes are used by the vendor assigned OUI.
- MAC addresses are implemented by software.
- The ISO is responsible for MAC addresses regulations.
- A NIC only needs a MAC address if connected to a WAN.
Explanation: A MAC address is composed of 6 bytes. The first 3 bytes are used for vendor identification and the last 3 bytes must be assigned a unique value within the same OUI. MAC addresses are implemented in hardware. A NIC needs a MAC address to communicate over the LAN. The IEEE regulates the MAC addresses.
4. What process is used to place one message inside another message for transfer from the source to the destination?
- flow control
- encapsulation
- access control
- decoding
Explanation: Encapsulation is the process of placing one message format into another message format. An example is how a packet is placed in its entirety into the data field as it is encapsulated into a frame.
5. What type of message is sent to a specific group of hosts?
- broadcast
- unicast
- multicast
- dynamic
Explanation: A communication that has a single source going to a single destination is a unicast. A communication from a single source to a group of destinations is a multicast. A communication from a single source to all destinations on the same local network is a broadcast.
6. Which three IP addresses are private ? (Choose three.)
- 172.16.4.4
- 10.1.1.1
- 192.167.10.10
- 192.168.5.5
- 172.32.5.2
- 224.6.6.6
Explanation: The private IP addresses are within these three ranges:
10.0.0.0 – 10.255.255.255
172.16.0.0 – 172.31.255.255
192.168.0.0 – 192.168.255.255
7. Which two OSI model layers have the same functionality as two layers of the TCP/IP model? (Choose two.)
- transport
- data link
- physical
- network
- session
Explanation: The OSI transport layer is functionally equivalent to the TCP/IP transport layer, and the OSI network layer is equivalent to the TCP/IP internet layer. The OSI data link and physical layers together are equivalent to the TCP/IP network access layer. The OSI session layer (with the presentation layer) is included within the TCP/IP application layer.
8. Which type of network model describes the functions that must be completed at a particular layer, but does not specify exactly how each protocol should work?
- hierarchical design model
- reference model
- protocol model
- TCP/IP model
Explanation: There are two common types of network communication models:
Protocol model – This model closely matches the structure of a particular protocol suite and describes the functions that occur at each layer of protocols within the suite. The TCP/IP model is an example of a protocol model.
Reference model – The primary purpose is to aid in a clearer understanding of the functions and processes necessary for network communications.This type of model does not specify exactly how a function should be accomplished. The OSI model is an example of a reference model.
9. The Institute of Electrical and Electronics Engineers is responsible for standards in which two areas? (Choose two.)
- Ethernet media access control
- wireless LANs
- IP address allocation and management
- the OSI reference model
- TCP/IP technologies
- peer-to-peer application compliance
Explanation: Among the many standards for which the IEEE is responsible, the two major standards are IEEE 802.3 and IEEE 802.11. The IEEE 802.3 standard defines media access control (MAC) for wired Ethernet. The 802.11 standard defines a group of standards for implementing wireless local area networks (WLANs). The other options are standards that are developed and maintained by other standards organizations.
10. What is indicated by the 100 in the 100BASE-T standard?
- megabits per second
- twists per meter
- meters
- feet
Explanation: 100BASE-T is an Ethernet standard that translates to 100 megabits per second, baseband transmission, and twisted pair cable.
11. Which IP address is a unicast address if a default subnet mask is used?
- 195.124.45.255
- 192.16.43.67
- 226.34.15.78
- 201.34.45.0
Explanation: The IP addresses 201.34.45.0, 192.16.43.67, and 195.124.45.255 are Class C addresses. With the default subnet mask of 255.255.255.0, 192.16.43.67 is a unicast address or host address, 195.124.45.255 is a broadcast address, and 201.34.45.0 is a network address. IP address 226.34.15.78 is a Class D multicast address.
12. What is the purpose of protocols in data communications?
- specifying the bandwidth of the channel or medium for each type of communication
- dictating the content of the message sent during communication
- providing the rules required for a specific type of communication to occur
- specifying the device operating systems that will support the communication
Explanation: Protocols provide rules that define how a message is transmitted across a network. Implementation requirements such as electronic and bandwidth details for data communication are specified by standards. Operating systems are not specified by protocols, but will implement protocols. Protocols determine how and when to send a message but they do not control the contents of a message.
13. What will a Cisco LAN switch do if it receives an incoming frame and the destination MAC address is not listed in the MAC address table?
- Drop the frame.
- Use ARP to resolve the port that is related to the frame.
- Forward the frame out all ports except the port where the frame is received.
- Send the frame to the default gateway address.
Explanation: A LAN switch populates the MAC address table based on source MAC addresses. When a switch receives an incoming frame with a destination MAC address that is not listed in the MAC address table, the switch forwards the frame out all ports except for the ingress port of the frame. When the destination device responds, the switch adds the source MAC address and the port on which it was received to the MAC address table.
14. Which logical address is used for delivery of data to a remote network?
- source MAC address
- destination port number
- source IP address
- destination MAC address
- destination IP address
Explanation: The destination IP address is used for end-to-end delivery of data to a remote network. The destination MAC address is used for delivery on a local network. The destination port number identifies the application that should process the data at the destination. Source addresses identify the sender of the data.
15. A small publishing company has a network design such that when a broadcast is sent on the LAN, 200 devices receive the transmitted broadcast. How can the network administrator reduce the number of devices that receive broadcast traffic?
- Segment the LAN into smaller LANs and route between them.
- Add more switches so that fewer devices are on a particular switch.
- Replace at least half of the switches with hubs to reduce the size of the broadcast domain.
- Replace the switches with switches that have more ports per switch. This will allow more devices on a particular switch.
Explanation: By dividing the one big network into two smaller network, the network administrator has created two smaller broadcast domains. When a broadcast is sent on the network now, the broadcast will only be sent to the devices on the same Ethernet LAN. The other LAN will not receive the broadcast.
16. Which two functions are primary functions of a router? (Choose two.)
- path selection
- flow control
- microsegmentation
- domain name resolution
- packet forwarding
Explanation: A router accepts a packet and accesses its routing table to determine the appropriate exit interface based on the destination address. The router then forwards the packet out of that interface.
17. Refer to the exhibit. Consider the IP address configuration shown from PC1. What is a description of the default gateway address?
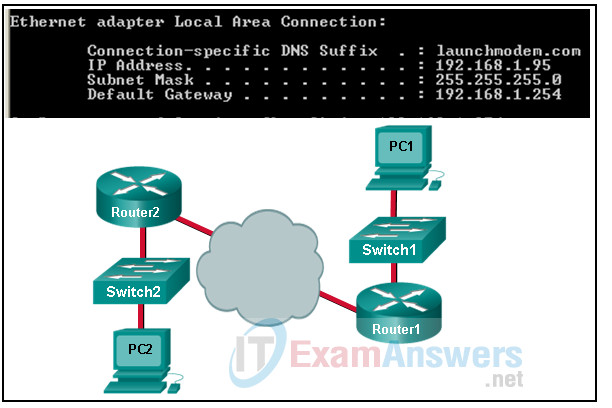
- It is the IP address of Switch1 that connects PC1 to other devices on the same LAN.
- It is the IP address of the Router1 interface that connects the PC1 LAN to Router1.
- It is the IP address of the Router1 interface that connects the company to the Internet.
- It is the IP address of the ISP network device located in the cloud.
Explanation: The default gateway is used to route packets destined for remote networks. The default gateway IP address is the address of the first Layer 3 device (the router interface) that connects to the same network.
18. A computer can access devices on the same network but cannot access devices on other networks. What is the probable cause of this problem?
- The computer has an invalid default gateway address.
- The cable is not connected properly to the NIC.
- The computer has an incorrect subnet mask.
- The computer has an invalid IP address.
Explanation: The default gateway is the address of the device a host uses to access the Internet or another network. If the default gateway is missing or incorrect, that host will not be able to communicate outside the local network. Because the host can access other hosts on the local network, the network cable and the other parts of the IP configuration are working.
19. A router receives an incoming packet and determines that the packet should be forwarded to a remote destination host. What will the router do to forward the packet?
- It encapsulates the frame with the destination IP address by using the specific IP address configured on the interface of the next hop router.
- It encapsulates the frame with a source IP address by using the specific IP address of the destination host.
- It encapsulates the frame with a destination MAC address by using the specific MAC address of the destination host device.
- It encapsulates the frame with the destination MAC address by using the MAC address of the interface of the next-hop router.
Explanation: A router contains a routing table of all locally connected networks and the interfaces that connect to them. The routing tables can also contain the routes that the router uses to reach remote networks. When a router determines that an incoming packet contains the destination host on a remote network, it encapsulates the frame to forward it towards to the next hop router. It uses the MAC address of the interface on the next hop router as the destination MAC address. The MAC address is obtained through ARP.
20. A router is receiving a stream of incoming packets and does not contain a route to the remote destination network. What configuration can a network administrator issue in order to successfully forward the incoming packets?
- Change the IP address of the ingress interface to match the targeted destination network.
- Enable a dynamic routing protocol.
- Add a default route.
- Share the routing table with the hosts on the local network.
Explanation: A router contains a routing table of all locally connected networks and the interfaces that connect to them. The routing tables can also contain the routes that the router uses to reach remote networks. Entries can be made to the routing table in two ways. The first is that the router via the use of a routing protocol can be dynamically updated by information received from other routers in the network. The second is that the entries can be manually entered by a network administrator. If the router cannot determine where to forward a packet, it will drop it. Network administrators can configure a default route to keep a packet from being dropped because the path to the destination network is not in the routing table. A default route is the interface through which the router forwards a packet containing an unknown destination IP network address.
21. Which two parts are components of an IPv4 address? (Choose two.)
- host portion
- subnet portion
- physical portion
- logical portion
- broadcast portion
- network portion
Explanation: An IPv4 address is divided into two parts: a network portion – to identify the specific network on which a host resides, and a host portion – to identify specific hosts on a network. A subnet mask is used to identify the length of each portion.
22. When a host sends a packet, how does it determine if the destination of the packet is on the same local network or on a remote network?
- It compares the source and destination MAC addresses.
- It queries the DNS server with the destination IP address.
- It checks to see if the default gateway is configured.
- It uses the subnet mask to compare the source and destination IP address.
Explanation: When a host sends a packet, it uses the subnet mask to compare the source IPv4 address and the destination IPv4 address. If the network bits match, both the source and destination host are on the same local network. Otherwise, the destination host is on a remote network.
23. What is the default subnet mask for an IP address of 198.133.219.4?
- 255.255.255.0
- 255.255.0.0
- 255.0.0.0
- 255.255.255.255
Explanation: In classful IPv4 addressing, a network with the first octet of 198 is a Class C network with the default subnet mask of 255.255.255.0.
24. What are the three layers of a hierarchical network design model? (Choose three.)
- network
- distribution
- core
- access
- Internet
- application
Explanation: The Cisco hierarchical network design model divides the network into three distinct layers. The access layer provides connectivity for the users. The distribution layer is used to forward traffic from one local network to another. The core layer represents a high-speed backbone layer between networks. The network layer is part of the OSI model. The Internet layer is part of the TCP/IP model. The application layer is part of both the OSI and TCP/IP models.
25. What addressing information is recorded by a switch to build its MAC address table?
- the source Layer 3 address of outgoing packets
- the destination Layer 2 address of outgoing frames
- the destination Layer 3 address of incoming packets
- the source Layer 2 address of incoming frames
Explanation: A switch builds a MAC address table by inspecting incoming Layer 2 frames and recording the source MAC address found in the frame header. The discovered and recorded MAC address is then associated with the port used to receive the frame.


100% correct
What process is used to place one message inside another message for transfer from the source to the destination?
Which three layers of the OSI model map to the application layer of the TCP/IP model? (Choose three.)
What type of message is sent to a specific group of hosts?
Added all, many thanks for sharing!!