Module Group 1: Modules 1 – 4 Group Exam Answers
Networking Essentials (Version 2) – Modules 1 – 4: Internet Connection: Getting Online Group Exam Answers
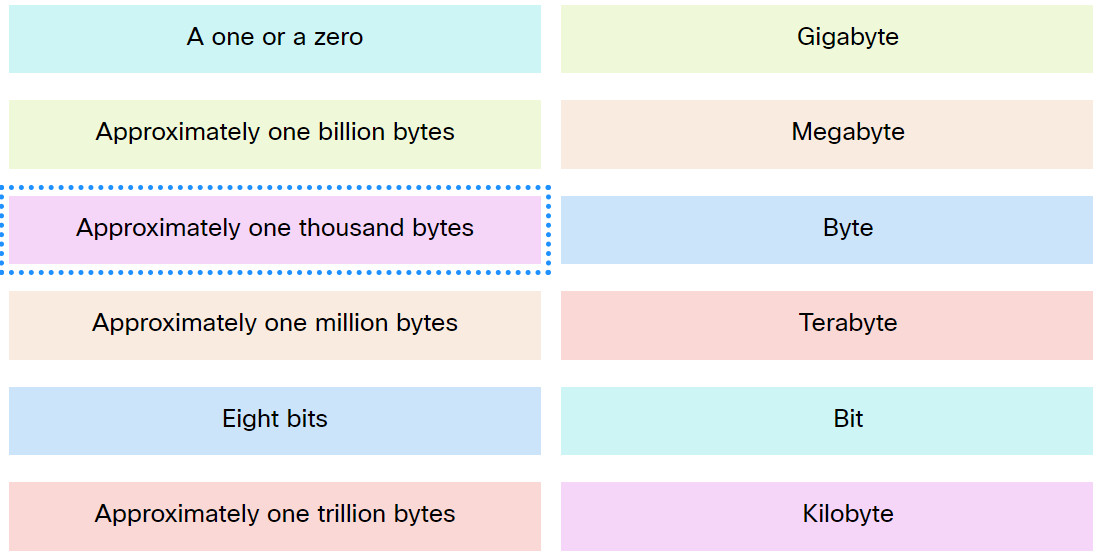
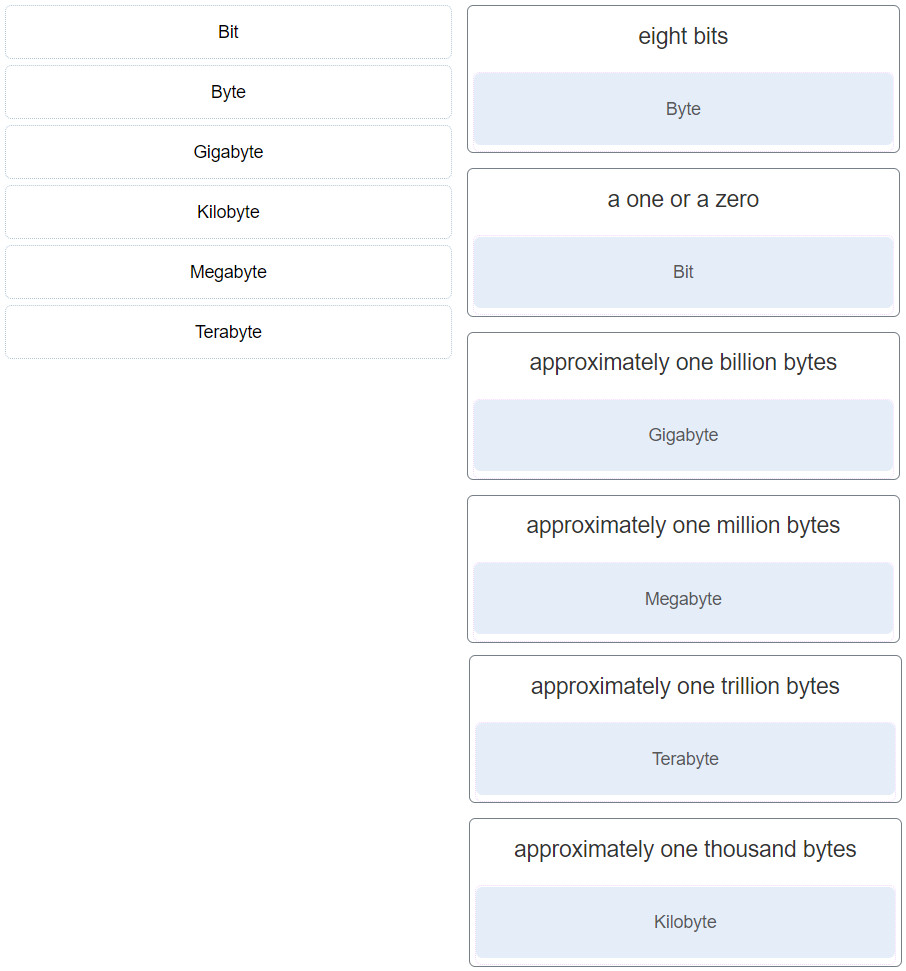
1. Match the term to the value represented.
Modules 1 – 4: Internet Connection: Getting Online Group Exam
Networking Essentials (Version 2) – Modules 1 – 4: Internet Connection: Getting Online Group Exam
2. What is a disadvantage of deploying a peer-to-peer network model?
- lack of centralized administration
- high degree of complexity
- high cost
- difficulty of setup
3. Which factor classifies a host as a server?
- the CPU speed
- the software installed
- the network connection
- the amount of memory
4. Which term is used to describe a network device that relies on another device to obtain information?
- console
- client
- web server
- server
5. How many unique values are possible using a single binary digit?
- 9
- 4
- 1
- 8
- 16
- 2
6. Which network device is used to translate a domain name to the associated IP address?
- router
- DHCP server
- DNS server
- default gateway
7. A consumer places a smartphone close to a pay terminal at a store and the shopping charge is successfully paid. Which type of wireless technology was used?
- Bluetooth
- NFC
- Wi-Fi
- 3G
8. A wireless network was recently installed in a coffee shop and customer mobile devices are not receiving network configuration information. What should be done to correct the problem?
- Check the connection of the DNS server to the Internet.
- Provide peripheral devices to customers.
- Make sure the DHCP server is functional.
- Ensure that the default gateway device is working properly.
9. A user is looking for a wireless headphone for listening to songs stored on a smartphone. What wireless technology would the headphone use?
- 3G/4G
- Wi-Fi
- infrared
- Bluetooth
10. If you were drawing a physical topology of your school network, what type of information would you include?
- how devices are connected
- the location of devices in the building
- the path that data takes to reach destinations
- the IP addresses of all devices on the network
11. Refer to the exhibit. A student is creating a wired and wireless network in Packet Tracer. After inserting a router, switch, and PC, the student chooses a straight-through cable to connect the PC to the switch. Which connection would be the best port for the student to choose on the PC?
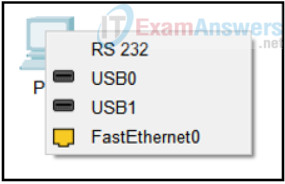
- RS 232
- USB0
- USB1
- FastEthernet0
12. Refer to the exhibit. An instructor wants to show a few prebuilt Packet Tracer sample labs in class. Which menu option would the instructor use to access a sample lab?

- File
- Edit
- Options
- View
- Tools
- Extensions
13. Refer to the exhibit. A home wireless network is being configured within Packet Tracer. The user adds a wireless router, a PC, and three laptops. The user is reviewing the wireless connection on one of the laptops. What can be determined?
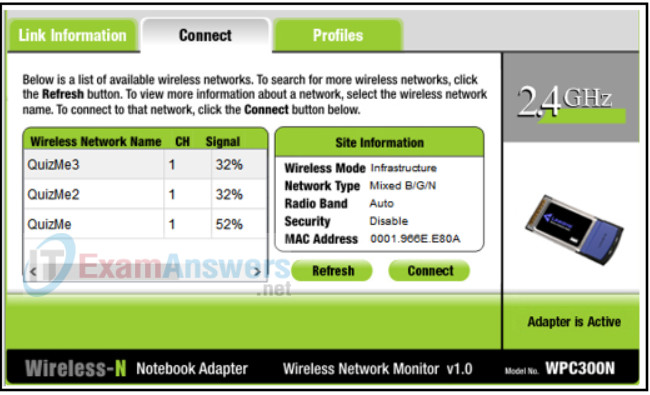
- The laptop must have a different wireless NIC installed before being able to connect to the wireless router.
- All three laptops are connected to the wireless network successfully.
- The laptop is connected to a wireless network.
- Because the password is not enabled, the laptop cannot connect to the wireless router.
14. When authenticating within Packet Tracer, which two items could you use? (Choose two.)
- a username associated with a specific school
- an email address found in the NetAcad profile
- a username associated with NetAcad
- a previously configured pattern
- a previously configured PIN
15. Refer to the exhibit. Which menu item would be used to bring up a command prompt environment to be able to ping another network device?
- Physical
- Config
- Desktop
- Programming
- Attributes
16. What are two advantages of using fiber-optic cabling to interconnect devices? (Choose two.)
- Fiber-optic cable is immune from EMI and RFI.
- Fiber-optic cables are commonly found in both homes and small businesses.
- Fiber-optic cables can extend several miles.
- Fiber-optic cables are easy to install..
- Fiber-optic cables use extra shielding to protect copper wires.
17. Which type of network cable is commonly used to connect office computers to the local network?
- coaxial cable
- glass fiber-optic cable
- twisted-pair cable
- plastic fiber-optic cable
18. Which statement describes the use of the ping command?
- The ping command can be used to determine the exact location of the problem when troubleshooting reachability issues.
- The ping command can be used to test reachability using the physical address of the device.
- The ping command tests end-to-end connectivity between two devices.
- The ping command shows current Layer 4 sessions.
19. Which type of network cable is used to connect the components that make up satellite communication systems?
- fiber-optic
- coaxial
- unshielded twisted-pair
- shielded twisted-pair
20. What are two sources of electromagnetic interference that can affect data transmissions? (Choose two.)
- infrared remote control
- LED monitor
- cordless phone
- florescent light fixture
- microwave oven
21. What terms represent the maximum and actual speed that can be utilized by a device to transfer data?
- throughput; bandwidth
- bandwidth; throughput
- throughput; goodput
- bandwidth; goodput
22. Which type of network component can be used to share an attached printer to the network?
- peripheral
- access point
- personal computer
- network media
23. Refer to the exhibit. A student has started a Packet Tracer network that includes a home wireless router to be used for both wired and wireless devices. The router and laptop have been placed within the logical workspace. The student clicks on the laptop and the window that opens is shown in the exhibit. What is the purpose of the modules on the left?
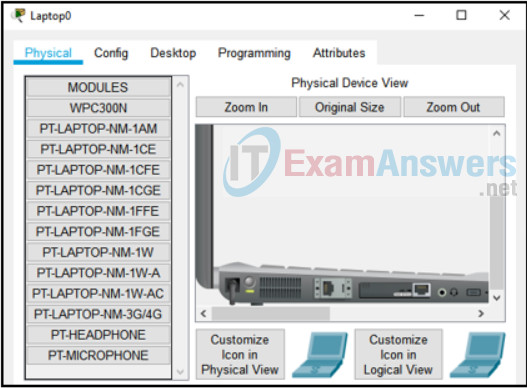
- These are modules that can be used by double-clicking on one module so that it automatically installs into the laptop.
- This is the list of modules currently installed in the laptop.
- These are optional modules that can be installed into the module slot if it is currently empty.
- This is a list of modules available from the manufacturer that can be clicked on and “purchased.”
24. Which criterion can be used to select the appropriate type of network media for a network?
- the types of data that need to be prioritized
- the number of intermediary devices that are installed in the network
- the cost of the end devices that are used in the network
- the environment where the selected medium is to be installed
