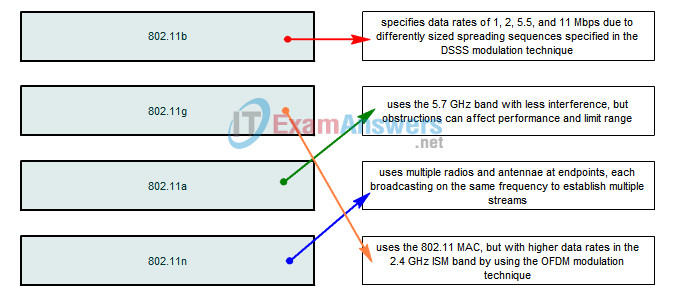
1. Drag the wireless standard on the left to the appropriate description on the right.
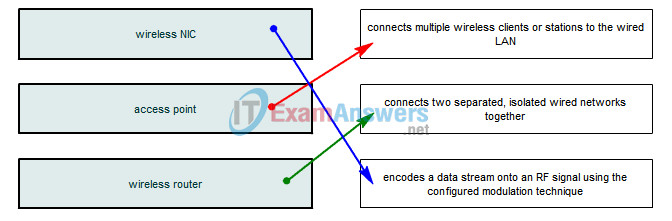
2. Drag the wireless device on the left to the appropriate description on the right.
3. At which layer of the OSI model do wireless access points operate?
- physical
- data link
- network
- application
4. Which two steps are required for a wireless client to associate with an access point? (Choose two.)
- IP addressing
- wireless address translation
- wireless client authentication
- channel identification
- wireless client association
5. Which three WLAN client authentication types require a preprogrammed network key to be set on the client? (Choose three.)
- OPEN with data encryption disabled
- SHARED with data encryption algorithm WEP
- WPA with data encryption algorithm TKIP
- WPA-PSK with data encryption algorithm TKIP
- WPA2 with data encryption algorithm AES
- WPA2-PSK with data encryption algorithm AES
6. Which two items contribute to the security of a WLAN? (Choose two.)
- WPA2
- use of multiple channels
- hiding the SSID
- open authentication
- AES
7. Which term is used for products that are tested to be interoperable in both PSK and 802.1X/Extensible Authentication Protocol (EAP) operation for authentication?
- personal mode
- WPA2 compatible
- RADIUS authenticated
- enterprise mode
- pre-shared key authenticated
8. To help ensure a secure wireless network, most enterprise networks should follow which IEEE standard?
- 802.11a
- 802.11b
- 802.11c
- 802.11i
9. Refer to the exhibit. Which method of network authentication provides the highest level of security?
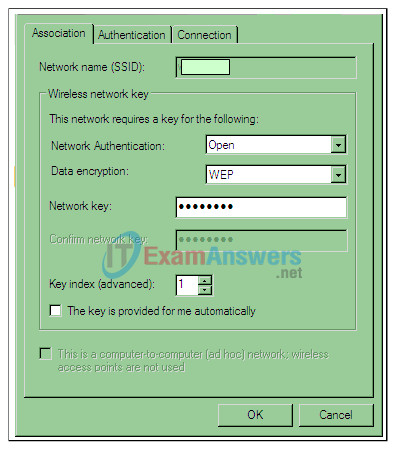
- Open
- Shared
- WPA
- WPA-PSK
10. Which two combinations of 802.11b RF channels would allow two wireless APs to operate simultaneously in the same room with no channel overlap? (Choose two.)
- channels 10 and 6
- channels 9 and 6
- channels 8 and 5
- channels 7 and 2
- channels 6 and 2
- channels 6 and 11
11. Why do cordless devices, such as cordless telephones, sometimes interfere with wireless access points?
- These devices operate at similar frequencies.
- These devices operate at the same frequencies and have higher RF power settings.
- These devices flood the entire frequency spectrum with low power noise, which may cause loss of signal for wireless devices trying to connect with an access point.
- The signal from the cordless device is non-polarized and combines with the access point polarized signal, thus reducing overall signal strength.
12. Refer to the exhibit. What is the recommended overlap between the two wireless access points to provide proper connectivity for users?
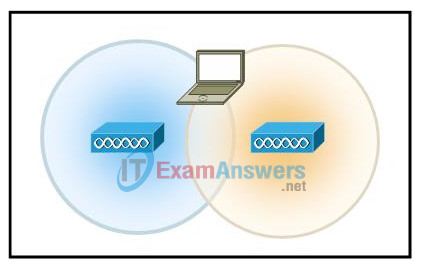
- 5 – 10%
- 10 – 15%
- 15 – 20%
- 20 – 25%
13. Drag the authentication method from the left column to the correct encryption algorithm or security protocol it would use on the right.
14. Which WLAN client settings would be reviewed to resolve encryption problems with the access point?
- wireless mode (802.11a, 802.11b, 802.11g)
- wireless network card drivers
- channel selection for ad hoc networks
- TCP/IP properties
- wireless association properties
