8.5.2 Packet Tracer – Troubleshooting Enterprise Networks 2 Answers
Topology
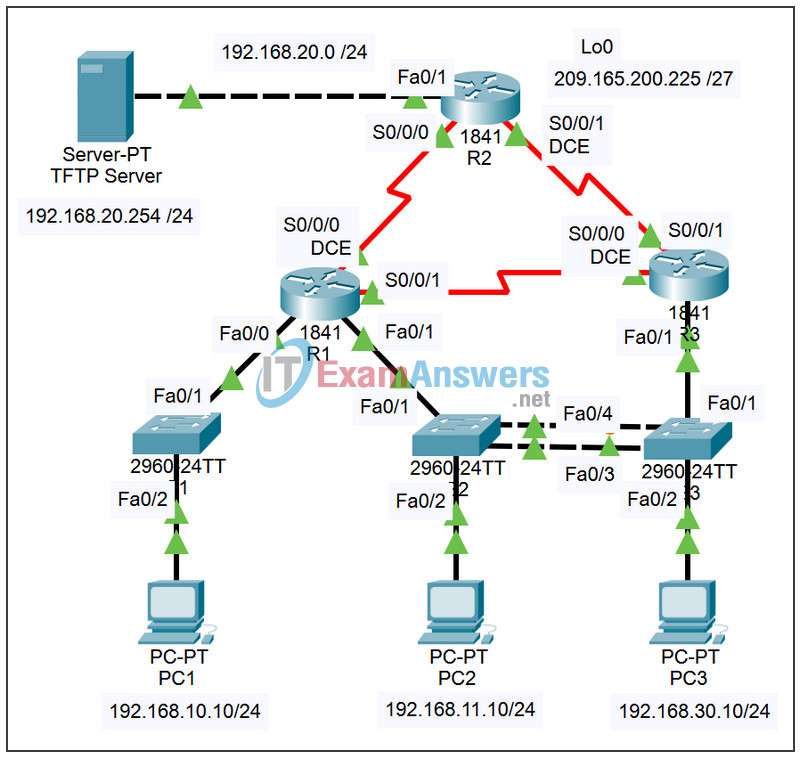
Addressing Table
| Device | Interface | IP Address | Subnet Mask | Default Gateway |
|---|---|---|---|---|
| R1 | Fa0/0 | 192.168.10.1 | 255.255.255.0 | N/A |
| Fa0/1 | 192.168.11.1 | 255.255.255.0 | N/A | |
| S0/0/0 | 10.1.1.1 | 255.255.255.252 | N/A | |
| S0/0/1 | 10.3.3.1 | 255.255.255.252 | N/A | |
| R2 | Fa0/1 | 192.168.20.1 | 255.255.255.0 | N/A |
| S0/0/0 | 10.1.1.2 | 255.255.255.252 | N/A | |
| S0/0/1 | 10.2.2.1 | 255.255.255.252 | N/A | |
| Lo0 | 209.165.200.225 | 255.255.255.224 | 209.165.200.226 | |
| R3 | Fa0/1 | N/A | N/A | N/A |
| Fa0/1.11 | 192.168.11.3 | 255.255.255.0 | N/A | |
| Fa0/1.30 | 192.168.30.1 | 255.255.255.0 | N/A | |
| S0/0/0 | 10.3.3.2 | 255.255.255.252 | N/A | |
| S0/0/1 | 10.2.2.2 | 255.255.255.252 | N/A | |
| S1 | VLAN10 | DHCP | 255.255.255.0 | N/A |
| S2 | VLAN11 | 192.168.11.2 | 255.255.255.0 | N/A |
| S3 | VLAN30 | 192.168.30.2 | 255.255.255.0 | N/A |
| PC1 | NIC | DHCP | DHCP | DHCP |
| PC2 | NIC | 192.168.11.10 | 255.255.255.0 | 192.168.11.1 |
| PC3 | NIC | 192.168.30.10 | 255.255.255.0 | 192.168.30.1 |
| TFTP Server | NIC | 192.168.20.254 | 255.255.255.0 | 192.168.20.1 |
Learning Objectives
- Find and correct all network errors.
- Verify that requirements are fully met.
- Document the corrected network.
Scenario
For this activity, do not use login or password protection on any console lines to prevent accidental lockout. Use ciscoccna for all passwords in this activity.
Note: Because this activity is cumulative, you will be using all the knowledge and troubleshooting techniques that you have acquired from the previous material to successfully complete this activity.
Requirements
- S2 is the spanning-tree root for VLAN 11, and S3 is the spanning-tree root for VLAN 30.
- S3 is a VTP server with S2 as a client.
- The serial link between R1 and R2 is Frame Relay.
- The serial link between R2 and R3 uses HDLC encapsulation.
- The serial link between R1 and R3 is authenticated using CHAP.
- R2 must have secure login procedures because it is the Internet edge router.
- All vty lines, except those belonging to R2, allow connections only from the subnets shown in the topology diagram, excluding the public address.
- Source IP address spoofing should be prevented on all links that do not connect to other routers.
- Routing protocols must be used securely. EIGRP is used in this scenario.
- R3 must not be able to telnet to R2 through the directly connected serial link.
- R3 has access to both VLAN 11 and 30 via its Fast Ethernet port 0/1.
- The TFTP server should not get any traffic that has a source address outside the subnet. All devices have access to the TFTP server.
- All devices on the 192.168.10.0 subnet must be able to get their IP addresses from DHCP on R1. This includes S1.
- All addresses shown in diagram must be reachable from every device.
Task 1: Find and Correct All Network Errors
Use a clock rate of 4000000 and VLAN priority of 24576 where needed.
Task 2: Verify that Requirements Are Fully Met
Because time constraints prevent troubleshooting a problem on each topic, only a select number of topics have problems. However, to reinforce and strengthen troubleshooting skills, you should verify that each requirement is met. To do this, present an example of each requirement (for example a show or debug command).
