1. Which statements correctly describe Cisco access control lists? (Choose two.)
- Extended ACLs are created in interface configuration mode.
- Extended ACLs filter traffic based on source and destination IP, port number, and protocol.
- Standard IP ACLs are numbered 1 to 99, and extended ACLs are numbered 100 to 199.
- Standard ACLs permit or deny traffic to specific IP addresses.
- Standard ACLs do not permit the use of wildcard masks.
2. Which statement is true about applying an access list to an interface?
- Access lists are applied in global configuration mode.
- Named access lists are applied using the ip access-name command.
- Standard access lists should be applied to an interface as close as possible to the destination.
- The command for applying access list 101 inbound is ip access-list 101.
3. Which statement is a guideline to be followed when designing access control lists?
- Because ACL tests are executed in order, they should be organized from the most general condition to the most specific.
- Because ACL tests are executed in order, they should be organized from the most specific condition to the most general.
- Because all statements in an ACL are evaluated before they are executed, an explicit deny any statement must be written for an ACL to function properly.
- Because all statements in an ACL are evaluated before they are executed, an explicit permit any statement must be written for an ACL to function properly.
4. What occurs if the network administrator applies an IP access control list that has no permit statement outbound on an interface? (Choose two.)
- All traffic outbound is denied.
- All traffic outbound is allowed.
- Only traffic originating from the router is allowed outbound.
- The ACL restricts all incoming traffic and filters outgoing traffic.
5. Which solutions can be implemented with ACLs? (Choose two.)
- Segment the network to increase available bandwidth.
- Create a firewall on a router to filter inbound traffic from an external network.
- Control traffic entering or exiting different areas of a local network.
- Distribute DHCP traffic to allow easier network availability.
- Allow or deny traffic into the network based on the MAC address.
6. Match each command with its description:
any
show running-config
show access-list
host
show ip interface
A. Substitutes for the 0.0.0.0 mask.
B. Indicates whether any ACLs are set on an interface.
C. Displays the contents of all ACLs on the router.
D. Represents an IP address and mask pair of 0.0.0.0 255.255.255.255.
E. Reveals the ACLs and interface assignments on a router.
7. Which IP address and wildcard mask test for hosts from an entire subnet of network 192.168.12.0 using a 29-bit mask?
- 192.168.12.56 0.0.0.15
- 192.168.12.56 0.0.0.8
- 192.168.12.56 0.0.0.31
- 192.168.12.84 0.0.0.7
- 192.168.12.84 0.0.0.3
- 192.168.12.84 0.0.0.255
8. What kind of access list is created with the command ip access-list standard fastaccess?
- Turbo ACL
- Reflexive ACL
- Named ACL
- Dynamic ACL
9. Refer to the following configuration, which shows an ACL that already exists on the router. The network administrator wants to insert the command access-list 101 deny ip any 192.168.1.0 0.0.0.255 eq ftp as the third line in the ACL shown. The network administrator enters the command in global configuration mode on the router. What effect does this have?
access-list 101 deny ip any 192.168.1.0 0.0.0.255 eq 8080 access-list 101 deny ip any 192.168.1.0 0.0.0.255 eq 80 access-list 101 deny icmp any 192.168.1.0 0.0.0.255 access-list 101 deny icmp any 192.168.2.0 0.0.0.255 access-list 101 permit ip any 192.168.1.0 0.0.0.255 access-list 101 permit ip any 192.168.2.0 0.0.0.255
- It inserts the line in the desired position in the ACL.
- It inserts the line as the first statement in the ACL.
- It inserts the line as the last statement in the ACL.
- It deletes the entire list and replaces it with the new line only.
10. Refer to the exhibit and the following configuration. Which statement correctly describes how Router1 processes packets with this configuration?
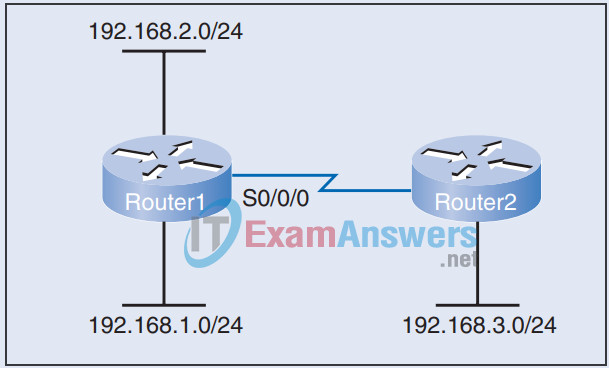
Router1(config)# access-list 201 deny icmp 192.168.1.0 0.0.0.255 any Router1(config)# access-list 201 deny icmp 192.168.2.0 0.0.0.255 any Router1(config)# access-list 201 permit any any Router1(config)# access-list 101 deny tcp any 192.168.1.0 0.0.0.255 eq 8080 Router1(config)# access-list 101 deny tcp any 192.168.1.0 0.0.0.255 eq 80 Router1(config)# access-list 101 deny icmp any 192.168.1.0 0.0.0.255 Router1(config)# access-list 101 deny icmp any 192.168.2.0 0.0.0.255 Router1(config)# access-list 101 permit ip any 192.168.1.0 0.0.0.255 Router1(config)# access-list 101 permit ip any 192.168.2.0 0.0.0.255 Router1(config)# interface serial 0/0/0 Router1(config-if)# ip access-group 101 in Router1(config-if)# ip access-group 201 out
- Traffic exiting interface serial 0/0/0 is filtered by both ACL 101 and ACL 201.
- If a packet entering interface serial 0/0/0 matches a condition in ACL 101, the router continues comparing the packet to the rest of the statements in ACL 101 to make sure that no other statements might apply.
- Router1 compares packets entering interface serial 0/0/0 first to all the ACL 101 statements for the IP protocol and then to all the ACL 101 statements for the ICMP protocol.
- A packet entering interface serial 0/0/0 is compared to each statement in ACL 101 until one statement matches the packet. Then the router drops or forwards the packet without considering the remaining statements in ACL 101.
11. An administrator wants to implement lock-and-key access to a host within the company network for specific users who are connecting from outside the company network. What type of ACL would best suit the situation?
- Dynamic
- Reflexive
- Extended
- Time-based
12. What type of ACL should the network administrator implement to limit Internet traffic during peak hours of the day?
- Dynamic
- Policy-based
- Reflexive
- Time-based
13. Which statement correctly describes a reflexive access list?
- An ACL that allows IP traffic for sessions originating from inside the network while denying traffic for sessions originating from the outside
- An ACL that controls traffic based on the time
- An ACL that uses an extended list to block users from traversing a router until they are authenticated
- An ACL that identifies only the source of traffic
14. Categorize the following descriptions as belonging to either a standard IP ACL or an extended IP ACL:
- Checks only the source address
- Access list numbers 100 to 199
- Checks protocol and port numbers
- Permits/denies only entire protocols based on network address
- Access list numbers 1 to 99
- Checks source and destination address
15. Refer to the following configuration. Assuming that this ACL is correctly applied to a router interface, which statements describe traffic on the network? (Choose two.)
access-list 199 deny tcp 178.15.0.0 0.0.255.255 any eq 23 access-list 199 permit ip any any
- All FTP traffic from network 178.15.0.0 will be permitted.
- All Telnet traffic destined for network 178.15.0.0 will be denied.
- Telnet and FTP will be permitted from all hosts on network 178.15.0.0 to any destination.
- Telnet will not be permitted from any hosts on network 178.15.0.0 to any destination.
- Telnet will not be permitted to any host on network 178.15.0.0 from any destination.
16. Describe the “three Ps” rule associated with access control lists.
17. Describe the two basic rules associated with the placement of standard and extended ACLs.
18. Refer to the exhibit and the following configuration. ACL 10, configured on R1, is designed to deny the host at 192.168.10.10 access to the 192.168.11.0 network, but all other hosts on the 192.168.10.0 network should be permitted access. However, the ACL does not accomplish this. Which changes would correct this problem?
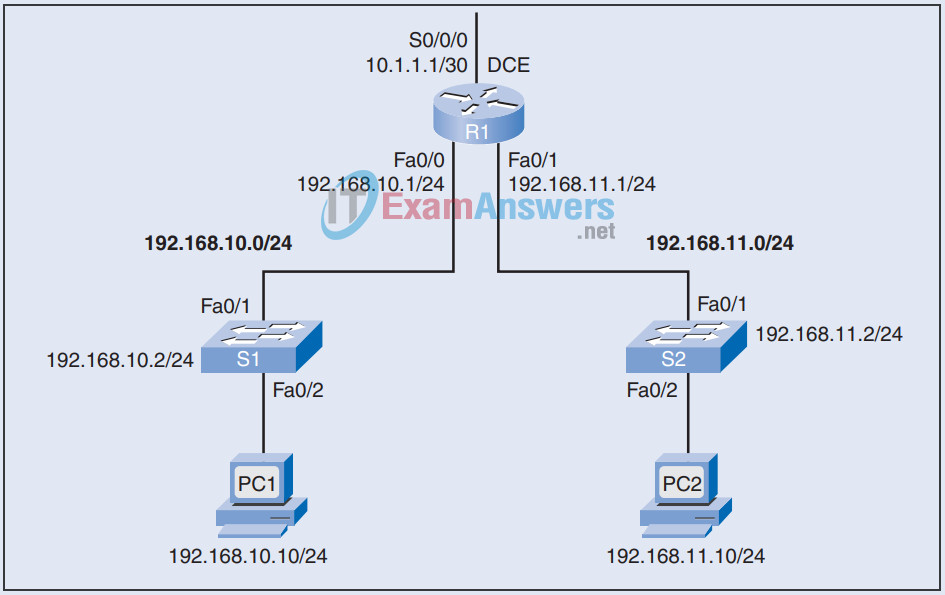
R1(config)# access-list 10 deny host 192.168.10.10 R1(config)# interface Fa0/1 R1(config-if)# ip access-group 10 in
19. Refer to the exhibit and the following configuration. The named ACL SURFING should enable only the hosts on the 192.168.10.0 network web and secure web access. The hosts on 192.168.11.0 should not be permitted any access. The BROWSING ACL should permit return access only to traffic that originated from the 192.168.10.0 network. However, the ACLs do not accomplish this. Which changes would correct this problem?

R1(config)# access-list extended SURFING R1(config-ext-nacl)# permit tcp 192.168.10.0 0.0.0.255 any eq 23 R1(config-ext-nacl)# permit tcp 192.168.10.0 0.0.0.255 any eq 443 R1(config)# access-list extended BROWSING R1(config-ext-nacl)# permit tcp any 192.168.10.0 0.0.0.255 R1(config-ext-nacl)# exit R1(config)# interface S0/0/0 R1(config-if)# ip access-group SURFING out R1(config-if)# ip access-group BROWSING in
20. Describe the three types of complex ACLs and their functions.
