Module 6: Application Deployment and Security Exam Answers
DevNet Associate (Version 1.0) – DevNet Associate Module 6 Exam Answers
1. Which technique is used to help mitigate SQL injection attacks?
- using the same owner or admin account in the web applications to connect to the database
- limiting the read access to specific fields of a table or joins of tables
- using stored procedures with the “db_owner” default role
- assigning DBA or admin access rights to the application account
2. Which security device is used to make responses to client requests look like they all come from the same server?
- stateful firewall
- forward proxy
- reverse proxy
- jump box
3. What is a characteristic of a virtual machine running on a PC?
- A virtual machine needs a physical network adapter to connect to the Internet.
- A virtual machine runs its own operating system.
- The number of virtual machines that can be made available depends on the software resources of the host machine.
- A virtual machine is not susceptible to threats and malicious attacks.
4. What is a characteristic of the blue-green upgrade deployment strategy?
- A new environment is created with the new code in it, while the old environment is held in reserve in case users experience problems.
- The code changes are periodically rolled out in such a way that they do not impact current users.
- The new code is deployed all at once to the old environment. If users experience no issues, it is then moved to the new environment.
- The new code version is first rolled out to a subset of users. Changes can then be rolled back if the users experience any problems.
5. Match the cloud model to its description. (Not all options are used.)
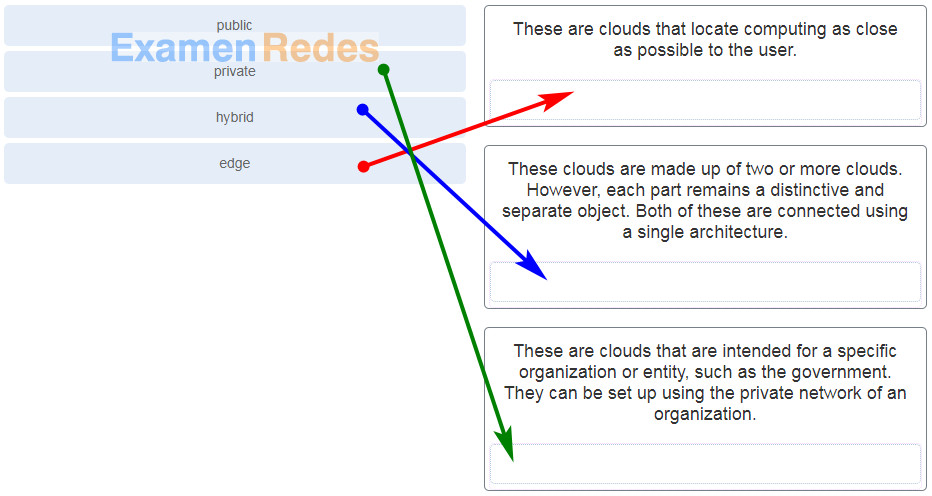
DevNet Associate (Version 1.0) – DevNet Associate Module 6 Exam 1
6. Which mitigation method is effective against cross-site scripting?
- requiring multifactor authentication
- consistent hardening of systems and applications
- sanitizing untrusted content
- using only necessary features and secure packages downloaded from official sources and verified with a signature
7. Match the environments in the four-tier development environment structure to the description.
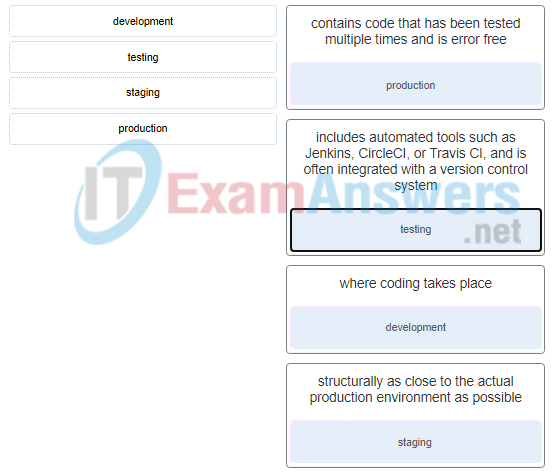
8. Which attack involves the insertion of malicious code into SQL statements?
- SQL injection
- cross-site scripting
- brute force
- local file inclusion
9. In software development, what is the purpose of a jump box?
- to act as a single trusted machine used to launch connections to sensitive systems
- to make all requests originating from within a network look like they come from the same source IP address
- to filter packets based on Layer 3 and Layer 4 addressing
- to receive incoming requests and forward them to multiple servers
10. Which characters are used to separate batched SQL statements?
- semicolons ;
- colons :
- parentheses ()
- pound signs #
11. What is a philosophy for software deployment used in the field of DevOps?
- OWASP
- DevNet
- SOAP
- CI/CD
12. Which statement is a characteristic of the broken access control threat to web applications?
- It allows attackers to access, and potentially change, serialized versions of data and objects.
- It allows an attacker to use the dynamic functions of a site to inject malicious content into the page.
- It allows users to circumvent existing authentication requirements.
- It allows attackers to steal sensitive information such as passwords or personal information.
13. Which technology is used to containerize applications and allows them to run in a variety of environments?
- Docker
- GitHub
- VirtualBox
- Cisco DNA
14. Match the OWASP resource with a description.
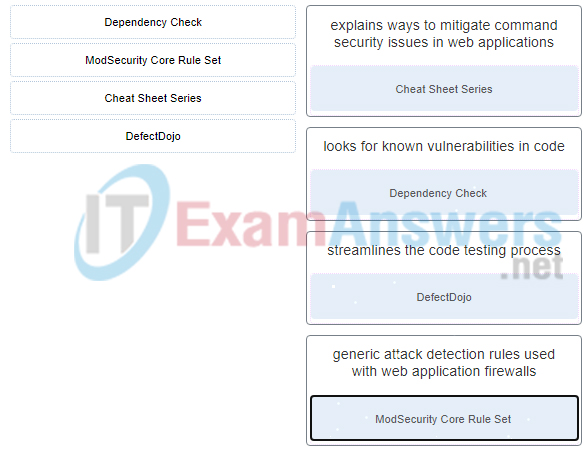
15. What is used to isolate the different parts of a running container?
- wrappers
- namespaces
- control groups
- union file systems
