Lab 7.4.3 – Troubleshooting DHCP and NAT (Answers)
Topology Diagram
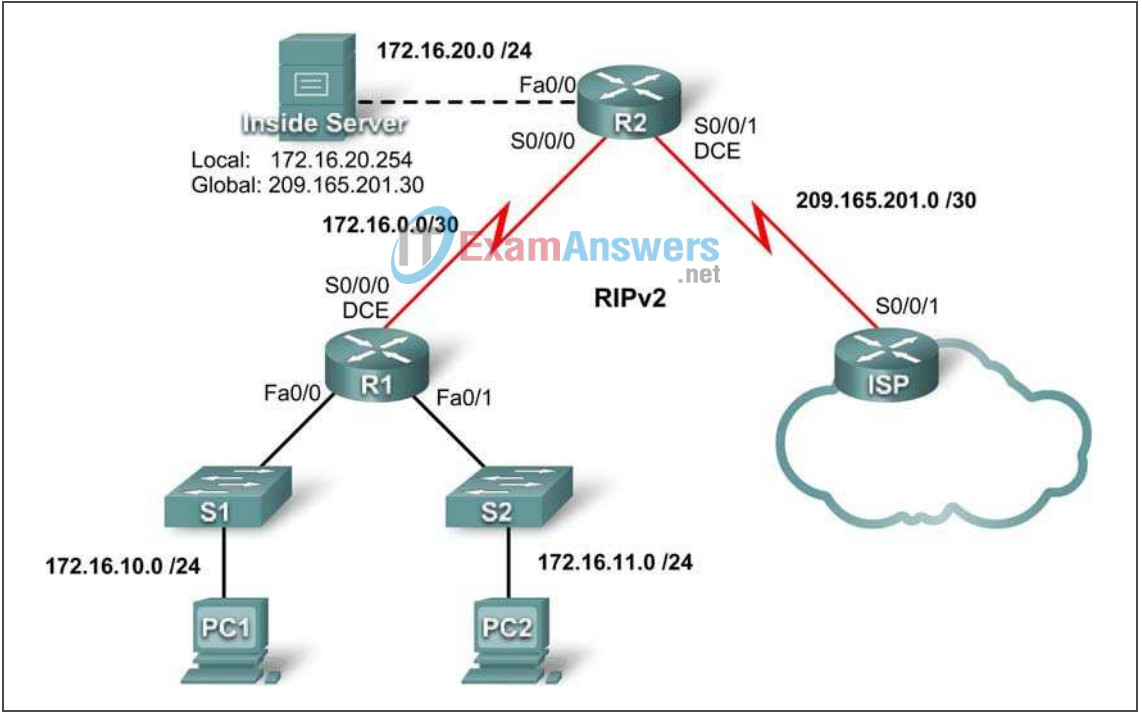
Addressing Table
| Device | Interface | IP Address | Subnet Mask |
|---|---|---|---|
| R1 | S0/0/0 | 172.16.0.1 | 255.255.255.252 |
| Fa0/0 | 172.16.10.1 | 255.255.255.0 | |
| Fa0/1 | 172.16.11.1 | 255.255.255.0 | |
| R2 | S0/0/0 | 172.16.0.2 | 255.255.255.252 |
| S0/0/1 | 209.165.201.1 | 255.255.255.252 | |
| Fa0/0 | 172.16.20.1 | 255.255.255.0 | |
| ISP | S0/0/1 | 209.165.201.2 | 255.255.255.252 |
Learning Objectives
Upon completion of this lab, you will be able to:
- Prepare the network
- Load routers with scripts
- Find and correct network errors
- Document the corrected network
Scenario
The routers, R1 and R2, at your company were configured by an inexperienced network engineer. Several errors in the configuration have resulted in connectivity issues. Your boss has asked you to troubleshoot and correct the configuration errors and document your work. Using your knowledge of DHCP, NAT, and standard testing methods, find and correct the errors. Make sure all clients have full connectivity. The ISP has been configured correctly.
Ensure that the network supports the following:
1. The router R2 should serve as the DHCP server for the 172.16.10.0/24 and 172.16.11.0/24 networks connected to R1.
2. All PCs connected to R1 should receive an IP address in the correct network via DHCP.
3. Traffic from the R1 LANs entering the Serial 0/0/0 interface on R2 and exiting the Serial 0/0/1 interface on R2 should receive NAT translation with a pool of addresses provided by the ISP.
4. The Inside Server should be reachable from outside networks using IP address 209.165.201.30, and to inside networks using IP address 172.16.20.254
Task 1: Prepare the Network
Step 1: Cable a network that is similar to the one in the topology diagram.
Step 2: Clear all existing configurations on the routers.
Step 3: Import the configurations below.
[Instructor Note: The configs below include misconfigured commands. These configs can be loaded into the routers in the topology. The final configs at the end of this document include missing commands shown in red and misconfigured commands shown in red strikethrough, followed by the correct command in red.]
R1
hostname R1 ! enable secret class ! no ip domain lookup ! interface FastEthernet0/0 ip address 172.16.10.1 255.255.255.0 ip helper-address 172.16.0.2 no shutdown ! interface FastEthernet0/1 ip address 172.16.11.1 255.255.255.0 no shutdown ! interface Serial0/0/0 ip address 172.16.0.1 255.255.255.252 clock rate 125000 no shutdown ! router rip version 2 network 172.16.0.0 no auto-summary ! banner motd $AUTHORIZED ACCESS ONLY$ ! line con 0 password cisco logging synchronous login line vty 0 4 password cisco logging synchronous login ! end
R2
hostname R2 ! enable secret class ! ip dhcp excluded-address 172.16.10.1 172.16.10.3 ip dhcp excluded-address 172.16.11.1 172.16.11.3 ! ip dhcp pool R1_LAN10 network 172.16.10.0 255.255.255.0 dns-server 172.16.20.254 ! ip dhcp pool R1_LAN11 network 172.16.11.0 255.255.255.0 dns-server 172.16.20.254 ! no ip domain lookup ! interface FastEthernet0/0 ip address 172.16.20.1 255.255.255.0 ip nat inside no shutdown ! interface Serial0/0/0 ip address 172.16.0.2 255.255.255.252 no shutdown ! interface Serial0/0/1 ip address 209.165.201.1 255.255.255.252 ip nat outside clock rate 125000 no shutdown ! router rip version 2 network 172.16.0.0 default-information originate no auto-summary ! ip route 0.0.0.0 0.0.0.0 209.165.201.2 ! ip nat pool NAT_POOL 209.165.201.9 209.165.201.14 netmask 255.255.255.248 ip nat inside source list NAT_ACL pool NATPOOL overload ! ip access-list standard NAT_ACL permit 172.16.10.0 0.0.0.255 ! banner motd $AUTHORIZED ACCESS ONLY$ ! line con 0 password cisco logging synchronous login line vty 0 4 password cisco logging synchronous login ! end
ISP
hostname ISP ! enable secret class ! interface Serial0/0/1 ip address 209.165.201.2 255.255.255.252 no shutdown ! ip route 0.0.0.0 0.0.0.0 Serial0/0/1 ! banner motd $AUTHORIZED ACCESS ONLY$ ! line con 0 password cisco logging synchronous login line vty 0 4 password cisco logging synchronous login ! end
Task 2: Find and Correct Network Errors
When the network is configured correctly:
- PC1 and PC2 should be able to receive IP addresses from the correct DHCP pool as evidenced by an ipconfig on the PCs. Additionally; a show ip dhcp bindings on R2 should show that both PCs have received IP addresses.
- Test pings from PC1 and PC2 to the ISP should receive NAT overload translation as evidenced by a show ip nat translations on R2.
- Test pings from the Inside Server to ISP should receive the static NAT translation indicated on the topology. Use the show ip nat translations command to verify this.
- A ping from the ISP to the global address of the Inside Server should be successful.
- Test pings from ISP to R1 should not receive NAT translation as evidenced by a show ip nat translations or a debug ip nat on R2.
Task 3: Document the Router Configurations
On each router, issue the show run command and capture the configurations.
Task 4: Clean Up
Erase the configurations and reload the routers. Disconnect and store the cabling. For PC hosts that are normally connected to other networks, such as the school LAN or to the Internet, reconnect the appropriate cabling and restore the TCP/IP settings.
Final Configurations
R1
hostname R1
!
enable secret class
!
no ip domain lookup
!
interface FastEthernet0/0
ip address 172.16.10.1 255.255.255.0
ip helper-address 172.16.0.2
no shutdown
!
interface FastEthernet0/1
ip address 172.16.11.1 255.255.255.0
ip helper-address 172.16.0.2
no shutdown
!
interface Serial0/0/0
ip address 172.16.0.1 255.255.255.252
clock rate 125000
no shutdown
!
router rip
version 2
network 172.16.0.0
no auto-summary
!
banner motd $AUTHORIZED ACCESS ONLY$
!
line con 0
password cisco
logging synchronous
login
line vty 0 4
password cisco
logging synchronous
login
!
end
R2
hostname R2 ! enable secret class ! ip dhcp excluded-address 172.16.10.1 172.16.10.3 ip dhcp excluded-address 172.16.11.1 172.16.11.3 ! ip dhcp pool R1_LAN10 network 172.16.10.0 255.255.255.0 default-router 172.16.10.1 dns-server 172.16.20.254 ! ip dhcp pool R1_LAN11 network 172.16.11.0 255.255.255.0 default-router 172.16.11.1 dns-server 172.16.20.254 ! no ip domain lookup ! interface FastEthernet0/0 ip address 172.16.20.1 255.255.255.0 ip nat inside no shutdown ! interface Serial0/0/0 ip address 172.16.0.2 255.255.255.252 ip nat inside no shutdown ! interface Serial0/0/1 ip address 209.165.201.1 255.255.255.252 ip nat outside clock rate 125000 no shutdown ! router rip version 2 network 172.16.0.0 default-information originate no auto-summary ! ip route 0.0.0.0 0.0.0.0 209.165.201.2 ! ip nat pool NAT_POOL 209.165.201.9 209.165.201.14 netmask 255.255.255.248ip nat inside source list NAT_ACL pool NATPOOL overloadip nat inside source list NAT_ACL pool NAT_POOL overload ip nat inside source static 172.16.20.254 209.165.201.30 ! ip access-list standard NAT_ACL permit 172.16.10.0 0.0.0.255 permit 172.16.11.0 0.0.0.255 ! banner motd $AUTHORIZED ACCESS ONLY$ ! line con 0 password cisco logging synchronous login line vty 0 4 password cisco logging synchronous login ! end
ISP
hostname ISP ! enable secret class ! interface Serial0/0/1 ip address 209.165.201.2 255.255.255.252 no shutdown ! ip route 0.0.0.0 0.0.0.0 Serial0/0/1 ! banner motd $AUTHORIZED ACCESS ONLY$ ! line con 0 password cisco logging synchronous login line vty 0 4 password cisco logging synchronous login ! end
