Lab 2.5.2 – Challenge PPP Configuration (Answers)
Topology Diagram
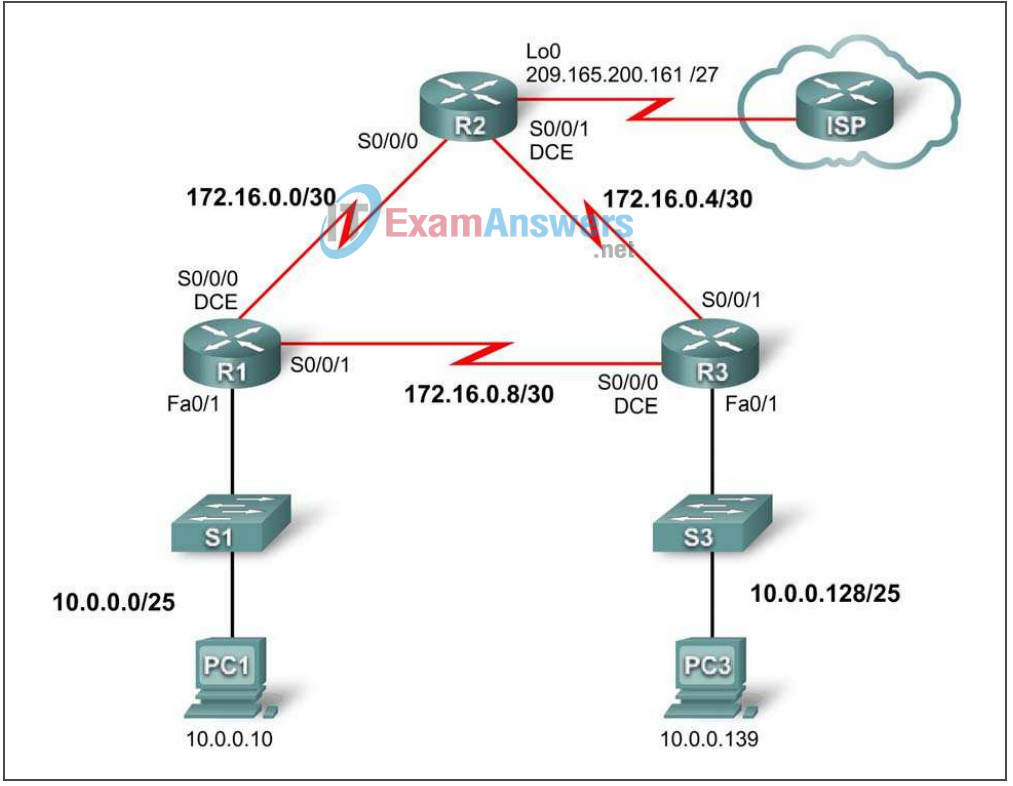
Addressing Table
| Device | Interface | IP Address | Subnet Mask | Default Gateway |
|---|---|---|---|---|
| R1 | Fa0/1 | 10.0.0.1 | 255.255.255.128 | N/A |
| S0/0/0 | 172.16.0.1 | 255.255.255.252 | N/A | |
| S0/0/1 | 172.16.0.9 | 255.255.255.252 | N/A | |
| R2 | Lo0 | 209.165.200.161 | 255.255.255.224 | N/A |
| S0/0/0 | 172.16.0.2 | 255.255.255.252 | N/A | |
| S0/0/1 | 172.16.0.5 | 255.255.255.252 | N/A | |
| R3 | Fa0/1 | 10.0.0.129 | 255.255.255.128 | N/A |
| S0/0/0 | 172.16.0.10 | 255.255.255.252 | N/A | |
| S0/0/1 | 172.16.0.6 | 255.255.255.252 | N/A | |
| PC1 | NIC | 10.0.0.10 | 255.255.255.128 | 10.0.0.1 |
| PC3 | NIC | 10.0.0.139 | 255.255.255.128 | 10.0.0.129 |
Learning Objectives
To complete this lab:
- Cable a network according to the topology diagram
- Erase the startup configuration and reload a router to the default state
- Perform basic configuration tasks on a router
- Configure and activate interfaces
- Configure OSPF routing on all routers
- Configure PPP encapsulation on all serial interfaces
- Change the encapsulation on the serial interfaces from PPP to HDLC
- Intentionally break and restore PPP encapsulation
- Configure PPP CHAP authentication
- Intentionally break and restore PPP CHAP authentication
Scenario
In this lab, you will learn how to configure PPP encapsulation on serial links using the network shown in the topology diagram. You will also configure PPP CHAP authentication. If you need assistance, refer back to the Basic PPP Configuration lab, but try to do as much on your own as possible.
Task 1: Prepare the Network
Step 1: Cable a network that is similar to the one in the topology diagram.
Step 2: Clear any existing configurations on the routers.
Task 2: Perform Basic Router Configuration
Configure the R1, R2, and R3 routers according to the following guidelines:
- Configure the router hostname.
- Disable DNS lookup.
- Configure an EXEC mode password.
- Configure a message-of-the-day banner.
- Configure a password for console connections.
- Configure synchronous logging.
- Configure a password for vty connections.
enable configure terminal no ip domain-lookup enable secret class banner motd ^CUnauthorized access strictly prohibited and prosecuted to the full extent of the law^C ! ! line con 0 exec-timeout 0 0 logging synchronous password cisco login ! line vty 0 4 password cisco login end copy running-config starting-config
Task 3: Configure and Activate Serial and Ethernet Addresses
Step 1: Configure interfaces on R1, R2, and R3.
R1
! interface FastEthernet0/1 ip address 10.0.0.1 255.255.255.128 no shutdown ! interface Serial0/0/0 ip address 172.16.0.1 255.255.255.252 no shutdown clock rate 64000 ! interface Serial0/0/1 ip address 172.16.0.9 255.255.255.252 no shutdown
R2
! interface Loopback0 ip address 209.165.200.161 255.255.255.224 ! ! interface Serial0/0/0 ip address 172.16.0.2 255.255.255.252 no shutdown ! interface Serial0/0/1 ip address 172.16.0.5 255.255.255.252 clock rate 64000 no shutdown
R3
! interface FastEthernet0/1 ip address 10.0.0.129 255.255.255.128 no shutdown ! interface Serial0/0/0 ip address 172.16.0.10 255.255.255.252 no shutdown ! interface Serial0/0/1 ip address 172.16.0.6 255.255.255.252 clock rate 64000 no shutdown
Step 2: Verify IP addressing and interfaces.
R1#show ip interface brief
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 unassigned YES manual administratively down down
FastEthernet0/1 10.0.0.1 YES manual up up
Serial0/0/0 172.16.0.1 YES manual up up
Serial0/0/1 172.16.0.9 YES manual up up
R2#show ip interface brief
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 unassigned YES unset administratively down down
FastEthernet0/1 unassigned YES unset administratively down down
Serial0/0/0 172.16.0.2 YES manual up up
Serial0/0/1 172.16.0.5 YES manual up up
Loopback0 209.165.200.161 YES manual up up
R3#show ip interface brief
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 unassigned YES unset administratively down down
FastEthernet0/1 10.0.0.129 YES manual up up
Serial0/0/0 172.16.0.10 YES manual up up
Serial0/0/1 172.16.0.6 YES manual up up
Step 3: Configure the Ethernet interfaces of PC1 and PC3.
Step 4: Test connectivity between the PCs.
Task 4: Configure OSPF on Routers
Step 1: Enable OSPF routing on the routers.
R1
! router ospf 1 network 10.0.0.0 0.0.0.127 area 0 network 172.16.0.0 0.0.0.3 area 0 network 172.16.0.8 0.0.0.3 area 0 !
R2
! router ospf 1 network 172.16.0.0 0.0.0.3 area 0 network 172.16.0.4 0.0.0.3 area 0 network 209.165.200.160 0.0.0.31 area 0 !
R3
! router ospf 1 network 10.0.0.128 0.0.0.127 area 0 network 172.16.0.4 0.0.0.3 area 0 network 172.16.0.8 0.0.0.3 area 0 !
Step 2: Verify that you have full network connectivity.
R1#show ip route <output omitted> 172.16.0.0/30 is subnetted, 3 subnets C 172.16.0.8 is directly connected, Serial0/0/1 O 172.16.0.4 [110/1562] via 172.16.0.10, 00:09:11, Serial0/0/1 [110/1562] via 172.16.0.2, 00:09:11, Serial0/0/0 C 172.16.0.0 is directly connected, Serial0/0/0 209.165.200.0/32 is subnetted, 1 subnets O 209.165.200.161 [110/782] via 172.16.0.2, 00:09:11, Serial0/0/0 10.0.0.0/25 is subnetted, 2 subnets C 10.0.0.0 is directly connected, FastEthernet0/1 O 10.0.0.128 [110/782] via 172.16.0.10, 00:09:11, Serial0/0/1 R1#ping 209.165.200.161 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 209.165.200.161, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 28/28/28 ms R1#ping 10.0.0.129 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.0.0.129, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 28/28/28 ms R2#show ip route <output omitted> 172.16.0.0/30 is subnetted, 3 subnets O 172.16.0.8 [110/1562] via 172.16.0.6, 00:12:42, Serial0/0/1 [110/1562] via 172.16.0.1, 00:12:42, Serial0/0/0 C 172.16.0.4 is directly connected, Serial0/0/1 C 172.16.0.0 is directly connected, Serial0/0/0 209.165.200.0/27 is subnetted, 1 subnets C 209.165.200.160 is directly connected, Loopback0 10.0.0.0/25 is subnetted, 2 subnets O 10.0.0.0 [110/782] via 172.16.0.1, 00:12:42, Serial0/0/0 O 10.0.0.128 [110/782] via 172.16.0.6, 00:12:42, Serial0/0/1 R2#ping 10.0.0.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.0.0.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 28/28/28 ms R2#ping 10.0.0.129 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.0.0.129, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 28/28/32 ms R3#show ip route <output omitted> 172.16.0.0/30 is subnetted, 3 subnets C 172.16.0.8 is directly connected, Serial0/0/0 C 172.16.0.4 is directly connected, Serial0/0/1 O 172.16.0.0 [110/1562] via 172.16.0.9, 00:14:14, Serial0/0/0 [110/1562] via 172.16.0.5, 00:14:14, Serial0/0/1 209.165.200.0/32 is subnetted, 1 subnets O 209.165.200.161 [110/782] via 172.16.0.5, 00:14:14, Serial0/0/1 10.0.0.0/25 is subnetted, 2 subnets O 10.0.0.0 [110/782] via 172.16.0.9, 00:14:14, Serial0/0/0 C 10.0.0.128 is directly connected, FastEthernet0/1 R3#ping 209.165.200.161 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 209.165.200.161, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 28/28/28 ms R3#ping 10.0.0.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.0.0.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 28/28/32 ms
Task 5: Configure PPP Encapsulation on Serial Interfaces
Step 1: Configure PPP on the serial interfaces of all three routers.
R1
interface Serial0/0/0 encapsulation ppp ! interface Serial0/0/1 encapsulation ppp
R2
interface Serial0/0/0 encapsulation ppp ! interface Serial0/0/1 encapsulation ppp
R3
interface Serial0/0/0 encapsulation ppp ! interface Serial0/0/1 encapsulation ppp
Step 2: Verify that all serial interfaces are using PPP encapsulation.
R1
R1#show interface serial0/0/0 Serial0/0/0 is up, line protocol is up Hardware is GT96K Serial Internet address is 172.16.0.1/30 MTU 1500 bytes, BW 128 Kbit, DLY 20000 usec, reliability 255/255, txload 1/255, rxload 1/255 Encapsulation PPP, LCP Open Open: CDPCP, IPCP, loopback not set R1#show interface serial0/0/1 Serial0/0/1 is up, line protocol is up Hardware is GT96K Serial Internet address is 172.16.0.9/30 MTU 1500 bytes, BW 128 Kbit, DLY 20000 usec, reliability 255/255, txload 1/255, rxload 1/255 Encapsulation PPP, LCP Open Open: CDPCP, IPCP, loopback not set
R2
R2#show interface serial0/0/0 Serial0/0/0 is up, line protocol is up Hardware is GT96K Serial Internet address is 172.16.0.2/30 MTU 1500 bytes, BW 128 Kbit, DLY 20000 usec, reliability 255/255, txload 1/255, rxload 1/255 Encapsulation PPP, LCP Open Open: CDPCP, IPCP, loopback not set R2#show interface serial0/0/1 Serial0/0/1 is up, line protocol is up Hardware is GT96K Serial Internet address is 172.16.0.5/30 MTU 1500 bytes, BW 128 Kbit, DLY 20000 usec, reliability 255/255, txload 1/255, rxload 1/255 Encapsulation PPP, LCP Open Open: CDPCP, IPCP, loopback not set
R3
R3#show interface serial0/0/0 Serial0/0/0 is up, line protocol is up Hardware is GT96K Serial Internet address is 172.16.0.10/30 MTU 1500 bytes, BW 128 Kbit, DLY 20000 usec, reliability 255/255, txload 1/255, rxload 1/255 Encapsulation PPP, LCP Open Open: CDPCP, IPCP, loopback not set R3#show interface serial0/0/1 Serial0/0/1 is up, line protocol is up Hardware is GT96K Serial Internet address is 172.16.0.6/30 MTU 1500 bytes, BW 128 Kbit, DLY 20000 usec, reliability 255/255, txload 1/255, rxload 1/255 Encapsulation PPP, LCP Open Open: CDPCP, IPCP, loopback not set
Task 6: Intentionally Break and Restore PPP Encapsulation
Step 1: Choose a way to break PPP encapsulation on the network.
R1
interface Serial0/0/0 encapsulation hdlc
R2
interface Serial0/0/1 encapsulation hdlc
R3
interface Serial0/0/0 encapsulation hdlc
Step 2: Restore full connectivity to your network.
R1
interface Serial0/0/0 encapsulation ppp
R2
interface Serial0/0/1 encapsulation ppp
R3
interface Serial0/0/0 encapsulation ppp
Step 3: Verify full connectivity to your network.
R1#show ip route R2#show ip route R3#show ip route username R2 password cisco username R3 password cisco interface serial0/0/0 ppp authentication chap interface serial0/0/1 ppp authentication chap
Task 7: Configure PPP CHAP Authentication
Step 1: Configure PPP CHAP authentication on all serial links.
R1
username R2 password cisco username R3 password cisco interface serial0/0/0 ppp authentication chap interface serial0/0/1 ppp authentication chap
R2
username R1 password cisco username R3 password cisco interface serial0/0/0 ppp authentication chap interface serial0/0/1 ppp authentication chap
R3
username R1 password cisco username R2 password cisco interface serial0/0/0 ppp authentication chap interface serial0/0/1 ppp authentication chap
Step 2: Verify PPP CHAP authentication on all serial links.
R1#show ip interface brief Interface IP-Address OK? Method Status Protocol FastEthernet0/0 unassigned YES manual administratively down down FastEthernet0/1 10.0.0.1 YES manual up up Serial0/0/0 172.16.0.1 YES manual up up Serial0/0/1 172.16.0.9 YES manual up up R2#show ip interface brief Interface IP-Address OK? Method Status Protocol FastEthernet0/0 unassigned YES unset administratively down down FastEthernet0/1 unassigned YES unset administratively down down Serial0/0/0 172.16.0.2 YES manual up up Serial0/0/1 172.16.0.5 YES manual up up Loopback0 209.165.200.161 YES manual up up R3#show ip interface brief Interface IP-Address OK? Method Status Protocol FastEthernet0/0 unassigned YES unset administratively down down FastEthernet0/1 10.0.0.129 YES manual up up Serial0/0/0 172.16.0.10 YES manual up up Serial0/0/1 172.16.0.6 YES manual up up
Task 8: Intentionally Break and Restore PPP CHAP Authentication
Step 1: Choose a way to break PPP CHAP authentication on one or more serial links.
R1#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#interface serial 0/0/0
R1(config-if)#no ppp authentication chap
R1(config-if)#ppp authentication pap
R1(config-if)#interface serial0/0/1
R1(config-if)#no ppp authentication chap
R1(config-if)#ppp authentication pap
R1(config-if)#^Z
R1#copy running-config startup-config
Destination filename [startup-config]?
Building configuration...
[OK]
R1#reload
Step 2: Verify that PPP CHAP authentication is broken.
R1#show ip interface brief
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 unassigned YES NVRAM administratively down down
FastEthernet0/1 10.0.0.1 YES NVRAM up up
Serial0/0/0 172.16.0.1 YES NVRAM up down
Serial0/0/1 172.16.0.9 YES NVRAM up down
Step 3: Restore PPP CHAP authentication on all serial links.
R1#conf t Enter configuration commands, one per line. End with CNTL/Z. R1(config)#interface serial0/0/0 R1(config-if)#ppp authentication chap R1(config-if)#interface serial0/0/1 R1(config-if)#ppp authentication chap R1(config-if)#^Z R1#
Step 4: Verify PPP CHAP authentication on all serial links.
R1#show ip interface brief Interface IP-Address OK? Method Status Protocol FastEthernet0/0 unassigned YES NVRAM administratively down down FastEthernet0/1 10.0.0.1 YES NVRAM up up Serial0/0/0 172.16.0.1 YES NVRAM up up Serial0/0/1 172.16.0.9 YES NVRAM up up
Task 9: Document the Router Configurations
R1
R1#show run !<output omitted> ! hostname R1 ! ! enable secret class ! ! no ip domain lookup ! username R3 password 0 cisco username R2 password 0 cisco ! ! interface FastEthernet0/1 ip address 10.0.0.1 255.255.255.128 no shutdown ! interface Serial0/0/0 ip address 172.16.0.1 255.255.255.252 encapsulation ppp clockrate 64000 ppp authentication chap no shutdown ! interface Serial0/0/1 ip address 172.16.0.9 255.255.255.252 encapsulation ppp ppp authentication chap no shutdown ! ! router ospf 1 network 10.0.0.0 0.0.0.127 area 0 network 172.16.0.0 0.0.0.3 area 0 network 172.16.0.8 0.0.0.3 area 0 ! ! banner motd ^CCUnauthorized access strictly prohibited and prosecuted to the full extent of the law^C ! line con 0 exec-timeout 0 0 password cisco logging synchronous login line aux 0 line vty 0 4 password cisco login ! end
R2
R2#show run !<output omitted> ! hostname R2 ! ! enable secret class ! ! no ip domain lookup ! username R1 password 0 cisco username R3 password 0 cisco ! ! ! interface Loopback0 ip address 209.165.200.161 255.255.255.224 ! ! interface Serial0/0/0 ip address 172.16.0.2 255.255.255.252 encapsulation ppp ppp authentication chap no shutdown ! interface Serial0/0/1 ip address 172.16.0.5 255.255.255.252 encapsulation ppp clockrate 64000 ppp authentication chap no shutdown ! ! router ospf 1 network 172.16.0.0 0.0.0.3 area 0 network 172.16.0.4 0.0.0.3 area 0 network 209.165.200.160 0.0.0.31 area 0 ! ! banner motd ^CCUnauthorized access strictly prohibited and prosecuted to the full extent of the law^C ! line con 0 exec-timeout 0 0 password cisco logging synchronous login line aux 0 line vty 0 4 password cisco login ! end
R3
R3#show run !<output omitted> ! hostname R3 ! ! enable secret class ! ! no ip domain lookup ! username R1 password 0 cisco username R2 password 0 cisco ! ! interface FastEthernet0/1 ip address 10.0.0.129 255.255.255.128 no shutdown ! interface Serial0/0/0 ip address 172.16.0.10 255.255.255.252 encapsulation ppp clockrate 64000 ppp authentication chap no shutdown ! interface Serial0/0/1 ip address 172.16.0.6 255.255.255.252 encapsulation ppp ppp authentication chap no shutdown ! router ospf 1 network 10.0.0.128 0.0.0.127 area 0 network 172.16.0.4 0.0.0.3 area 0 network 172.16.0.8 0.0.0.3 area 0 ! ! banner motd ^CCUnauthorized access strictly prohibited and prosecuted to the full extent of the law^C ! line con 0 exec-timeout 0 0 password cisco logging synchronous login line aux 0 line vty 0 4 password cisco login ! end
Task 10: Clean Up
Erase the configurations and reload the routers. Disconnect and store the cabling. For PC hosts that are normally connected to other networks, such as the school LAN or the Internet, reconnect the appropriate cabling and restore the TCP/IP settings.
