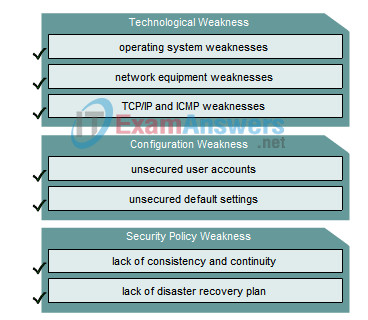
1. Drag the term on the left to the associated description on the right.
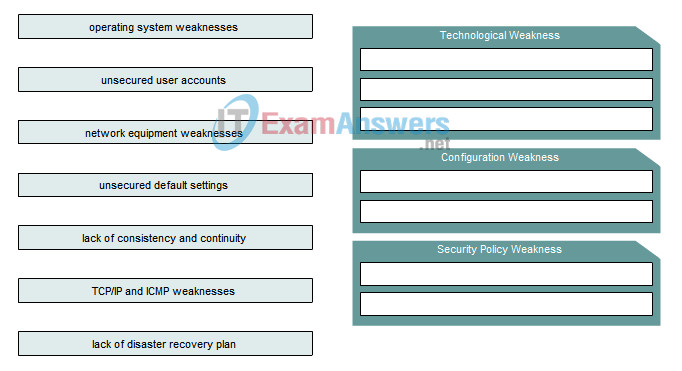
Answer
2. Which two pieces of information can be determined from opening the Cisco SDM homepage of a router? (Choose two.)
- routing table
- CDP neighbors
- snapshot of the router configuration
- interface status
- features supported by the Cisco IOS software
3. A technician has been asked to perform a Cisco SDM one-step lockdown test. Which location should be used to initiate the test?
- diagnostic mode on the Firewall page
- configure mode on the Security Audit page
- test mode on the Security Audit page
- test mode on the Firewall page
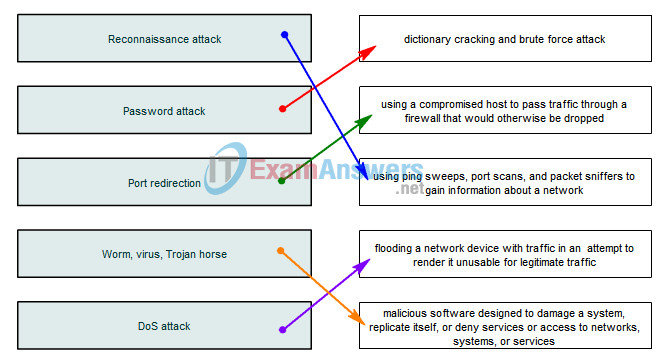
4. Drag the term on the left to the associated description on the right.
5. What is a major advantage of HIPS over HIDS?
- HIPS does not require host-based client software.
- HIPS consumes fewer system resources.
- HIPS can prevent intrusions.
- HIPS prevents the need to update signature files as often.
6. What is the core or “hub” component of the Security Wheel?
- secure
- monitor
- improve
- test
- security policy
7. As part of a network security plan, where does Cisco recommend that administrators send events captured by syslog?
- flash
- NVRAM
- designated log hosts
- designated TFTP clients
- designated SNMP clients
8. Which protocol should be used when strong privacy and session integrity are needed for remote router administration?
- HTTP
- SNMP
- SSH
- Telnet
- TFTP
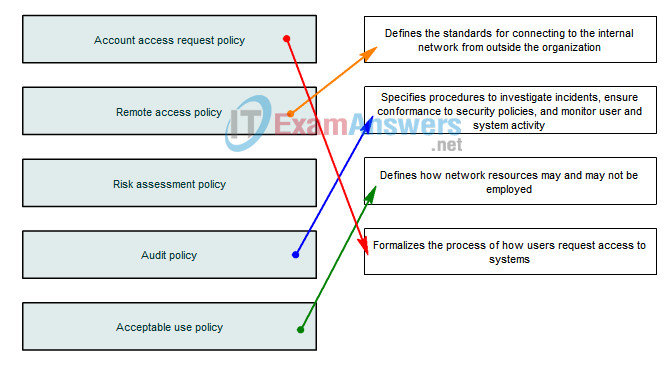
9. Drag the policy on the left to its description on the right. Not all options are used.
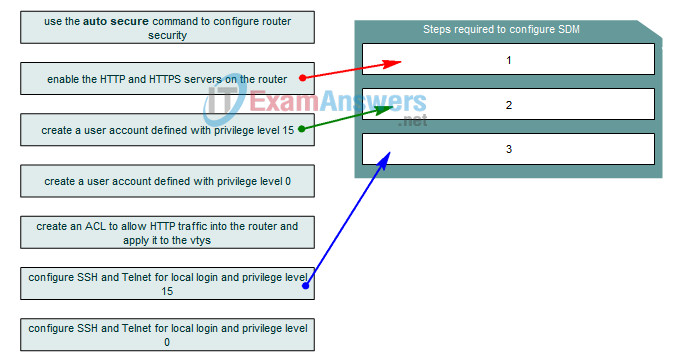
10. Drag the three items required to configure SDM from the left to the steps on the right. Not all options are used.
11. Which three services should be disabled on a router to prevent security vulnerabilities? (Choose three.)
- Network Time Protocol (NTP)
- Domain Name System (DNS)
- Secure Socket Layer (SSL)
- Cisco Express Forwarding (CEF)
- Simple Network Management Protocol (SNMP)
- Secure Shell (SSH)
12. Which feature provides a straightforward “one-touch” device lockdown for configuring the security posture of routers?
- SSH
- SDM
- AutoSecure
- SNMP
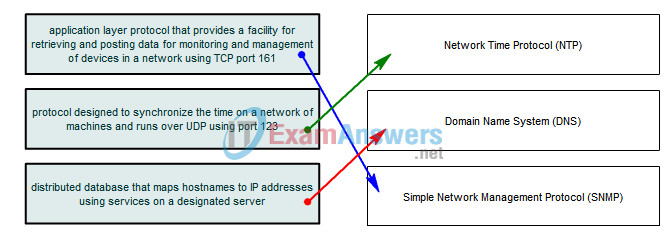
13. Drag the description on the left to the correct network management service on the right.
14. Which feature is a web-based device-management tool for Cisco IOS software-based routers?
- SSH
- SDM
- AutoSecure
- SNMP
15. Which three SDM wizards are available to configure a router? (Choose three.)
- security audit
- firewall
- DHCP
- QoS
- routing
- access list
