Check answers here: CCNA 2 v7 Practice FINAL Exam Answers
Quiz-summary
0 of 55 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
Information
Switching, Routing, and Wireless Essentials v7.0 – SRWEv7 Practice Final Test Online
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 55 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- Answered
- Review
-
Question 1 of 55
1. Question
1 pointsA network administrator is using the router-on-a-stick method to configure inter-VLAN routing. Switch port Gi1/1 is used to connect to the router. Which command should be entered to prepare this port for the task?Correct
Incorrect
Hint
With the router-on-a-stick method, the switch port that connects to the router must be configured as trunk mode. This can be done with the command Switch(config-if)# switchport mode trunk. The other options do not put the switch port into trunk mode. -
Question 2 of 55
2. Question
1 pointsRefer to the exhibit. The configuration shows commands entered by a network administrator for inter-VLAN routing. However, host H1 cannot communicate with H2. Which part of the inter-VLAN configuration causes the problem?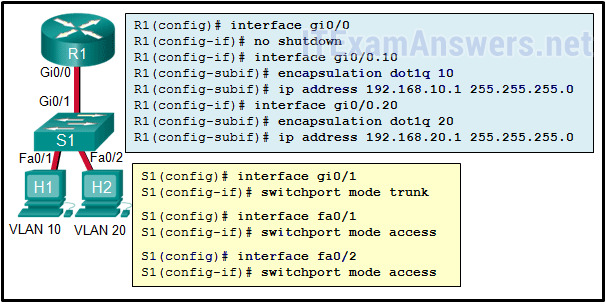 Correct
Correct
Incorrect
Hint
All Cisco switch ports are assigned to VLAN 1 by default. For VLAN implementation, ports Fa0/1 and Fa0/2 should be assigned to VLAN 10 and VLAN 20, respectively. The missing commands on S1 are as follows: switchport access vlan 10 and switchport access vlan 20 . -
Question 3 of 55
3. Question
1 pointsRefer to the exhibit. Inter-VLAN communication between VLAN 10, VLAN 20, and VLAN 30 is not successful. What is the problem?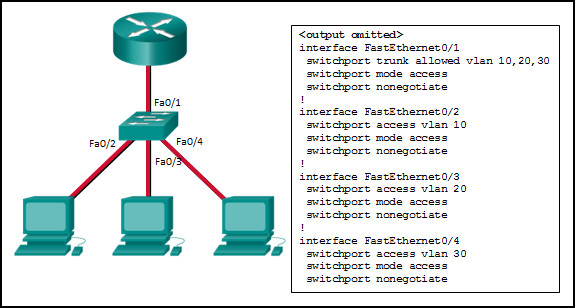 Correct
Correct
Incorrect
Hint
To forward all VLANs to the router, the switch interface Fa0/1 must be configured as a trunk interface with the switchport mode trunk command. -
Question 4 of 55
4. Question
1 pointsAn employee connects wirelessly to the company network using a cell phone. The employee then configures the cell phone to act as a wireless access point that will allow new employees to connect to the company network. Which type of security threat best describes this situation?Correct
Incorrect
Hint
Configuring the cell phone to act as a wireless access point means that the cell phone is now a rogue access point. The employee unknowingly breached the security of the company network by allowing a user to access the network without connecting through the company access point. Cracking is the process of obtaining passwords from data stored or transmitted on a network. Denial of service attacks refer to sending large amounts of data to a networked device, such as a server, to prevent legitimate access to the server. Spoofing refers to access gained to a network or data by an attacker appearing to be a legitimate network device or user. -
Question 5 of 55
5. Question
1 pointsWhich combination of WLAN authentication and encryption is recommended as a best practice for home users?Correct
Incorrect
Hint
WPA2 is the Wi-Fi alliance version of 802.11i, the industry standard for authentication. Neither WEP nor WPA possess the level of authentication provided by WPA2. AES aligns with WPA2 as an encryption standard, and is stronger than TKIP or RC4. PSK refers to pre-shared passwords, an authentication method that can be used by either WPA or WPA2. EAP is intended for use with enterprise networks which use a RADIUS server. -
Question 6 of 55
6. Question
1 pointsWhat are the two methods that a wireless NIC can use to discover an AP? (Choose two.)Correct
Incorrect
Hint
Two methods can be used by a wireless device to discover and register with an access point: passive mode and active mode. In passive mode, the AP sends a broadcast beacon frame that contains the SSID and other wireless settings. In active mode, the wireless device must be manually configured for the SSID, and then the device broadcasts a probe request. -
Question 7 of 55
7. Question
1 pointsWhat address and prefix length is used when configuring an IPv6 default static route?Correct
Incorrect
Hint
The IPv6 address and prefix for a default static route is ::/0. This represents all zeros in the address and a prefix length of zero. -
Question 8 of 55
8. Question
1 pointsRefer to the exhibit. Match the description with the routing table entries. (Not all options are used.)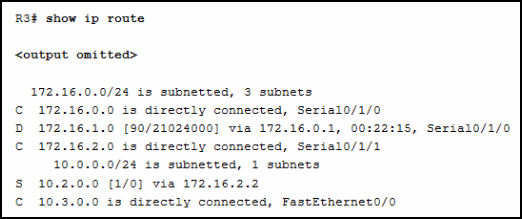 Graphic contains output of show ip route as follows:
Graphic contains output of show ip route as follows:
R3# show ip route 172.16.0.0/24 is subnetted, 3 subnets C 172.16.0.0 is directly connected, Serial0/1/0 D 172.16.1.0 [90/21024000] via 172.16.0.1, 00:22:15, Serial0/1/0 C 172.16.2.0 is directly connected, Serial0/1/0 10.0.0.0/24 is subnetted, 1 subnets S 10.2.0.0/24 [1/0] via 172.16.2.2 C 10.3.0.0 is directly connected, FastEthernet0/0
Sort elements
- D
- 10.3.0.0
- 21024000
- 1
- 172.168.2.2
- 00:22:15
- C
- 3
-
route source protocol
-
destination network
-
metric
-
administrative distance
-
next hop
-
route timestamp
Correct
Incorrect
Hint
route source protocol = D (which is EIGRP) destination network = 10.3.0.0 metric = 21024000 administrative distance = 1 next hop = 172.16.2.2 route timestamp = 00:22:15 -
Question 9 of 55
9. Question
1 pointsRefer to the exhibit. Which interface will be the exit interface to forward a data packet that has the destination IP address 172.18.109.152?Gateway of last resort is not set. 172.18.109.0/26 is variously subnetted, 7 subnets, 3 masks O 172.18.109.0/26 [110/10] via 172.18.32.1, 00:00:24, Serial0/0/0 O 172.18.109.64/26 [110/20] via 172.18.32.6, 00:00:56, Serial 0/0/1 O 172.18.109.128/26 [110/10] via 172.18.32.1, 00:00:24, Serial 0/0/0 C 172.18.109.192/27 is directly connected, GigabitEthernet0/0 L 172.18.109.193/27 is directly connected, GigabitEthernet0/0 C 172.18.109.224/27 is directly connected, GigabitEthernet0/1 L 172.18.109.225/27 is directly connected, GigabitEthernet0/1 172.18.32.0/24 is variably subnetted, 4 subnets, 2 masks C 172.18.32.0/30 is directly connected, Serial0/0/0 L 172.18.32.2/32 is directly connected, Serial0/0/0 C 172.18.32.4/30 is directly connected, Serial0/0/1 L 172.18.32.5/32 is directly connected, Serial0/0/1 S 172.18.33.0/26 [1/0] via 172.18.32.1, 00:00:24, Serial0/0/0 R1#
Correct
Incorrect
-
Question 10 of 55
10. Question
1 pointsMatch the dynamic routing protocol component to the characteristic. (Not all options are used.)Sort elements
- tables or databases that are stored in RAM
- exchanges routing information and maintains accurate information about networks
- a finite list of steps used to determine the best path
- manually implemented routes by an administrator
-
data structures
-
routing protocol messages
-
algorithm
Correct
Incorrect
Hint
data structures tables or databases that are stored in RAM routing protocol messages exchanges routing information and maintains accurate information about networks algorithm a finite list of steps used to determine the best path -
Question 11 of 55
11. Question
1 pointsWhich statement describes the behavior of a switch when the MAC address table is full?Correct
Incorrect
Hint
When the MAC address table is full, the switch treats the frame as an unknown unicast and begins to flood all incoming traffic to all ports only within the local VLAN. -
Question 12 of 55
12. Question
1 pointsWhich term describes the role of a Cisco switch in the 802.1X port-based access control?Correct
Incorrect
Hint
802.1X port-based authentication defines specific roles for the devices in the network: Client (Supplicant) – The device that requests access to LAN and switch services Switch (Authenticator) – Controls physical access to the network based on the authentication status of the client Authentication server – Performs the actual authentication of the client -
Question 13 of 55
13. Question
1 pointsWhat is a result of connecting two or more switches together?Correct
Incorrect
Hint
When two or more switches are connected together, the size of the broadcast domain is increased and so is the number of collision domains. The number of broadcast domains is increased only when routers are added. -
Question 14 of 55
14. Question
1 pointsA small publishing company has a network design such that when a broadcast is sent on the LAN, 200 devices receive the transmitted broadcast. How can the network administrator reduce the number of devices that receive broadcast traffic?Correct
Incorrect
Hint
By dividing the one big network into two smaller network, the network administrator has created two smaller broadcast domains. When a broadcast is sent on the network now, the broadcast will only be sent to the devices on the same Ethernet LAN. The other LAN will not receive the broadcast. -
Question 15 of 55
15. Question
1 pointsRefer to the exhibit. How is a frame sent from PCA forwarded to PCC if the MAC address table on switch SW1 is empty?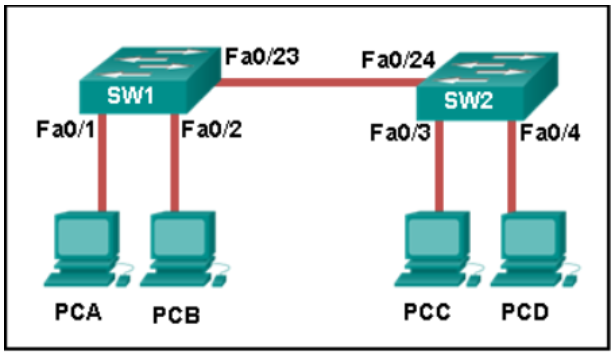 Correct
Correct
Incorrect
Hint
When a switch powers on, the MAC address table is empty. The switch builds the MAC address table by examining the source MAC address of incoming frames. The switch forwards based on the destination MAC address found in the frame header. If a switch has no entries in the MAC address table or if the destination MAC address is not in the switch table, the switch will forward the frame out all ports except the port that brought the frame into the switch. -
Question 16 of 55
16. Question
1 pointsWhat are two switch characteristics that could help alleviate network congestion? (Choose two.)Correct
Incorrect
Hint
Switch characteristics that help alleviate network congestion include fast port speeds, fast internal switching, large frame buffers, and high port density. -
Question 17 of 55
17. Question
1 pointsA network engineer is configuring a LAN with a redundant first hop to make better use of the available network resources. Which protocol should the engineer implement?Correct
Incorrect
Hint
Gateway Load Balancing Protocol (GLBP) provides load sharing between a group of redundant routers while also protecting data traffic from a failed router or circuit. -
Question 18 of 55
18. Question
1 pointsMatch the FHRP protocols to the appropriate description. (Not all options are used.)Sort elements
- A Cisco proprietary FHRP that provides load sharing in addition to redundancy
- A Cisco proprietary FHRP that provides redundancy through use of an active device and standby device
- An open standard FHRP that provides redundancy through use of a virtual routers master and one or more backups
- A legacy open standard FHRP that allows IPv4 hosts to discover gateway routers
-
HSRP
-
VRRP
-
GLBP
Correct
Incorrect
Hint
GLBP, A Cisco proprietary FHRP that provides load sharing in addition to redundancy. HSRP A Cisco proprietary FHRP that provides redundancy through use of an active device and standby device. VRRP, An open standard FHRP that provides redundancy through use of a virtual routers master and one or more backups. Distractor, A legacy open standard FHRP that allows IPv4 hosts to discover gateway routers. -
Question 19 of 55
19. Question
1 pointsAfter sticky learning of MAC addresses is enabled, what action is needed to prevent dynamically learned MAC addresses from being lost in the event that an associated interface goes down?Correct
Incorrect
Hint
When sticky learning is enabled, dynamically learned MAC addresses are stored in the running configuration in RAM and will be lost if the switch is rebooted or an interface goes down. To prevent the loss of learned MAC addresses, an administrator can save the running configuration into the startup configuration in NVRAM. -
Question 20 of 55
20. Question
1 pointsA small coffee shop is offering free Wi-Fi to customers. The network includes a wireless router and a DSL modem that is connected to the local phone company. What method is typically used to configure the connection to the phone company?Correct
Incorrect
Hint
In a SOHO environment, a wireless router connects to an ISP via a DSL or cable modem. The IP address between the wireless router and ISP site is typically assigned by the ISP through DHCP. The DSL modem does not manage IP address allocation. -
Question 21 of 55
21. Question
1 pointsMatch the purpose with its DHCP message type. (Not all options are used.)Sort elements
- DHCPDISCOVER
- DHCPOFFER
- DHCPREQUEST
- DHCPACK
- DHCPNAK
-
a message that is used to locate any available DHCP server on a network
-
a message that is used to suggest a lease to client
-
a message that is used to identify the explicit server and lease offer to accept
-
a message that is used to acknowledge that the lease is successful
Correct
Incorrect
Hint
The DHCPDISCOVER message is used to identify any DHCP servers on a network. The DHCPOFFER message is used by a server to offer a lease to a client. The DHCPREQUEST message is used to identify both the specific DHCP server and the lease that the client is accepting. The DHCPACK message is used by a server to finalize a successful lease with a client. The DHCPNAK message is used when an offered lease is no longer valid. -
Question 22 of 55
22. Question
1 pointsMatch the spanning-tree feature with the protocol type. (Not all options are used.)Sort elements
- PVST+
- RSTP
- MSTP
- MST
- Rapid PVST+
-
Cisco implementation of IEEE 802.1D
-
Fast converging enhancement of IEEE 802.1D
-
IEEE standard that reduces the number of STP instances
-
Proprietary per VLAN implementation of IEEE 802.1w
Correct
Incorrect
Hint
MST is the Cisco implementation of MSTP (IEEE 802.1s). -
Question 23 of 55
23. Question
1 pointsWhich three components are combined to form a bridge ID?Correct
Incorrect
Hint
The three components that are combined to form a bridge ID are bridge priority, extended system ID, and MAC address. -
Question 24 of 55
24. Question
1 pointsWhat is an advantage of PVST+?Correct
Incorrect
Hint
PVST+ results in optimum load balancing. However, this is accomplished by manually configuring switches to be elected as root bridges for different VLANs on the network. The root bridges are not automatically selected. Furthermore, having spanning-tree instances for each VLAN actually consumes more bandwidth and it increases the CPU cycles for all the switches in the network. -
Question 25 of 55
25. Question
1 pointsWhich problem is evident if the show ip interface command shows that the interface is down and the line protocol is down?Correct
Incorrect
Hint
If an interface has not been brought up with the no shutdown command, the interface status shows administratively down. A duplicate IP address will not bring an interface down. An encapsulation error is normally found using the show interfaces command. -
Question 26 of 55
26. Question
1 pointsA technician is configuring a new Cisco 2960 switch. What is the effect of issuing the BranchSw(config)#interface VLAN88 command?Correct
Incorrect
-
Question 27 of 55
27. Question
1 pointsIn what situation would a Layer 2 switch have an IP address configured?Correct
Incorrect
Hint
Layer 2 switches can be configured with an IP address so that they can be remotely managed by an administrator. Layer 3 switches can use an IP address on routed ports. Layer 2 switches do not need a configured IP address to forward user traffic or act as a default gateway. -
Question 28 of 55
28. Question
1 pointsWhich command would create a valid IPv6 default route?Correct
Incorrect
Hint
The correct prefix and prefix length for a default route is ::/0, which matches any address. ::/128 matches only the specific address of all zeros. When creating a static route that uses a link-local address as the next hop, an exit interface must also be specified for the route to be valid. -
Question 29 of 55
29. Question
1 pointsRefer to the exhibit. The routing table for R2 is as follows: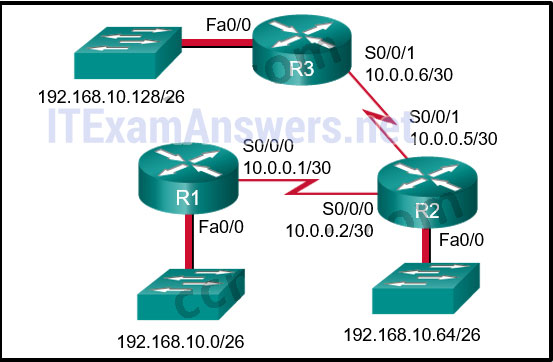
Gateway of last resort is not set 10.0.0.0/30 is subnetted, 2 subnets C 10.0.0.0 is directly connected, Serial0/0/0 C 10.0.0.4 is directly connected, Serial0/0/1 192.168.10.0/26 is subnetted, 3 subnets S 192.168.10.0 is directly connected, Serial0/0/0 C 192.168.10.64 is directly connected, FastEthernet0/0 S 192.168.10.128 [1/0] via 10.0.0.6
What will router R2 do with a packet destined for 192.168.10.129?Correct
Incorrect
Hint
When a static route is configured with the next hop address (as in the case of the 192.168.10.128 network), the output of the show ip route command lists the route as “via” a particular IP address. The router has to look up that IP address to determine which interface to send the packet out. Because the IP address of 10.0.0.6 is part of network 10.0.0.4, the router sends the packet out interface Serial0/0/1. -
Question 30 of 55
30. Question
1 pointsRefer to the exhibit. Router R1 has an OSPF neighbor relationship with the ISP router over the 192.168.0.32 network. The 192.168.0.36 network link should serve as a backup when the OSPF link goes down. The floating static route command ip route 0.0.0.0 0.0.0.0 S0/0/1 100 was issued on R1 and now traffic is using the backup link even when the OSPF link is up and functioning. Which change should be made to the static route command so that traffic will only use the OSPF link when it is up?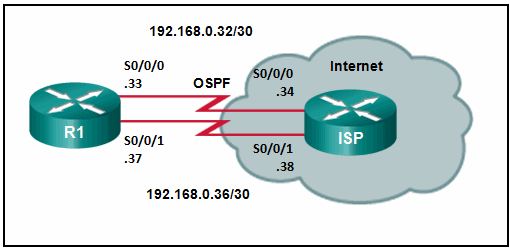 Correct
Correct
Incorrect
Hint
The problem with the current floating static route is that the administrative distance is set too low. The administrative distance will need to be higher than that of OSPF, which is 110, so that the router will only use the OSPF link when it is up. -
Question 31 of 55
31. Question
1 pointsA junior technician was adding a route to a LAN router. A traceroute to a device on the new network revealed a wrong path and unreachable status. What should be done or checked?Correct
Incorrect
-
Question 32 of 55
32. Question
1 pointsRefer to the exhibit. When a packet arrives on interface Serial0/0/0 on R1, with a destination IP address of PC1, which two events occur? (Choose two)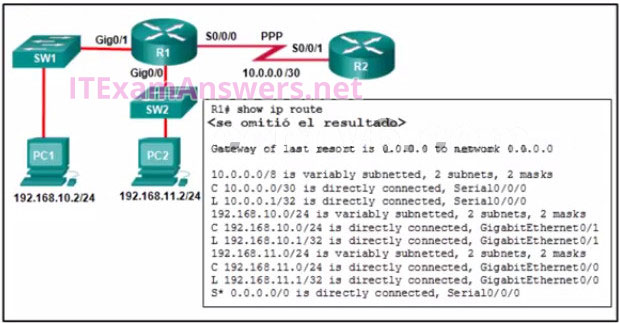 Correct
Correct
Incorrect
Hint
Routing and Switching Essentials 1.1.1 Router Functions 1.2.2 Path Determination A router will look in the routing table for a destination network and locate an exit interface to forward a packet to a destination. After the exit interface is determined, the router will encapsulate a packet into the correct frame type. (PPP) is a data link (layer 2) protocol used to establish a direct connection between two nodes. (from wikipedia) -
Question 33 of 55
33. Question
1 pointsRefer to the exhibit. How was the host route 2001:DB8:CAFE:4::1/128 installed in the routing table?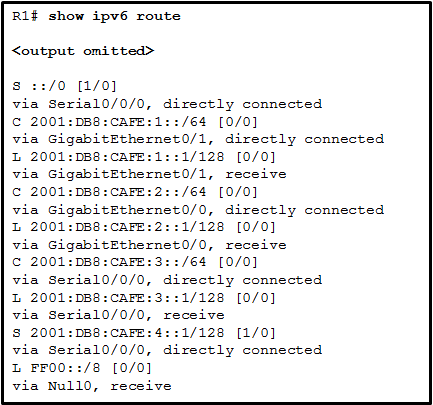 Correct
Correct
Incorrect
Hint
A host route is an IPv6 route with a 128-bit mask. A host route can be installed in a routing table automatically when an IP address is configured on a router interface or manually if a static route is created. -
Question 34 of 55
34. Question
1 pointsWhich command will start the process to bundle two physical interfaces to create an EtherChannel group via LACP?Correct
Incorrect
Hint
To specify the interfaces in an EtherChannel group, use the interface range interface global configuration command for the range of interfaces used. The interface range GigabitEthernet 0/4 – 5 command is the correct option because it specifies two interfaces for the EtherChannel group. -
Question 35 of 55
35. Question
1 pointsRefer to the exhibit. Based on the command output shown, what is the status of the EtherChannel?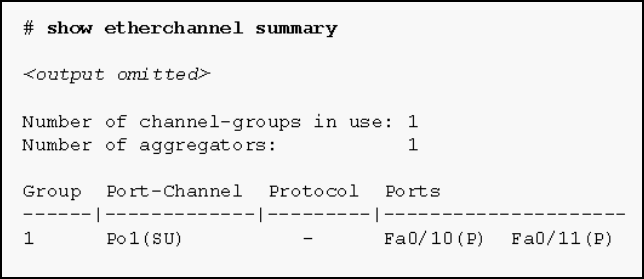 Correct
Correct
Incorrect
Hint
The command output shows the port channel as SU, which means Layer 2 and in use; and the FastEthernet 0/10 and 0/11 interfaces are bundled in port-channel as indicated by the P flag. Configuring the EtherChannel using the channel-group 1 mode on command will cause the Protocol field in the command output to be empty. -
Question 36 of 55
36. Question
1 pointsRefer to the exhibit. DLS1 is connected to another switch, DLS2, via a trunk link. A host that is connected to DLS1 is not able to communicate to a host that is connected to DLS2, even though they are both in VLAN 99. Which command should be added to Fa0/1 on DLS1 to correct the problem?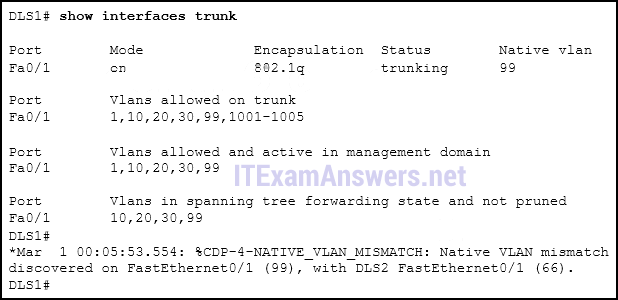 Correct
Correct
Incorrect
Hint
When configuring 802.1Q trunk links, the native VLAN must match on both sides of the link, or else CDP error messages will be generated, and traffic that is coming from or going to the native VLAN will not be handled correctly. -
Question 37 of 55
37. Question
1 pointsWhich type of traffic is designed for a native VLAN?Correct
Incorrect
Hint
A native VLAN carries untagged traffic, which is traffic that does not come from a VLAN. A data VLAN carries user-generated traffic. A management VLAN carries management traffic. -
Question 38 of 55
38. Question
1 pointsRefer to the exhibit. PC-A and PC-B are both in VLAN 60. PC-A is unable to communicate with PC-B. What is the problem?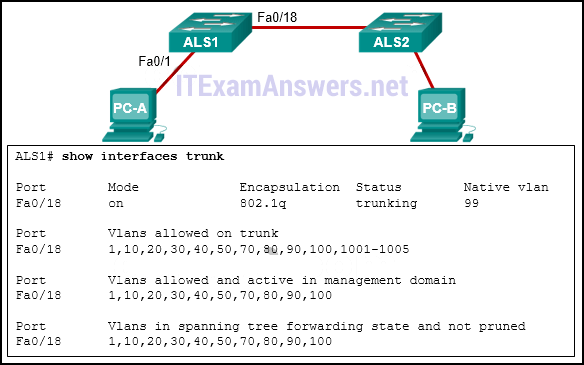 Correct
Correct
Incorrect
Hint
Because PC-A and PC-B are connected to different switches, traffic between them must flow over the trunk link. Trunks can be configured so that they only allow traffic for particular VLANs to cross the link. In this scenario, VLAN 60, the VLAN that is associated with PC-A and PC-B, has not been allowed across the link, as shown by the output of show interfaces trunk. -
Question 39 of 55
39. Question
1 pointsQuestion as presented: Match the DTP mode with its function. (Not all options are used.)Sort elements
- actively attempt to convert the link to a trunk
- passively waits for the neighbor to initiate trunking
- requires manual configuration of trunking or nontrunking
- permanent trunking mode
- permanent nontrunking mode
-
dynamic desirable
-
dynamic auto
-
nonegotiate
-
trunk
Correct
Incorrect
Hint
The dynamic auto mode makes the interface become a trunk interface if the neighboring interface is set to trunk or desirable mode. The dynamic desirable mode makes the interface actively attempt to convert the link to a trunk link. The trunk mode puts the interface into permanent trunking mode and negotiates to convert the neighboring link into a trunk link. The nonegotiate mode prevents the interface from generating DTP frames. -
Question 40 of 55
40. Question
1 pointsWhat type of VLAN is configured specifically for network traffic such as SSH, Telnet, HTTPS, HTTP, and SNMP?Correct
Incorrect
-
Question 41 of 55
41. Question
1 pointsRefer to the exhibit. The users on the LAN network of R1 cannot receive an IPv6 address from the configured stateful DHCPv6 server. What is missing from the stateful DHCPv6 configuration on router R1?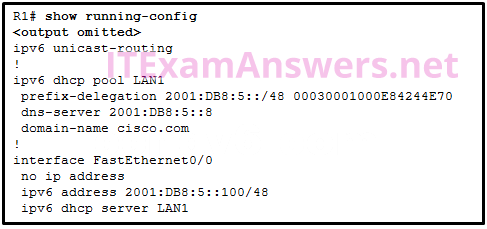 Correct
Correct
Incorrect
Hint
When configuring a router interface for stateful DHCPv6, the router must be able to inform the host PC’s to receive IPv6 addressing from a stateful DHCPv6 server. The interface command is ipv6 nd managed-config-flag -
Question 42 of 55
42. Question
1 pointsA network administrator is implementing DHCPv6 for the company. The administrator configures a router to send RA messages with M flag as 1 by using the interface command ipv6 nd managed-config-flag . What effect will this configuration have on the operation of the clients?Correct
Incorrect
Hint
Under stateful DHCPv6 configuration, which is indicated by setting M flag as 1 (through the interface command ipv6 nd managed-config-flag ), the dynamic IPv6 address assignments are managed by the DHCPv6 server. Clients must obtain all configuration information from a DHCPv6 server. -
Question 43 of 55
43. Question
1 pointsRefer to the exhibit. A network administrator is troubleshooting a problem with EtherChannel. What command was used to produce the exhibited output?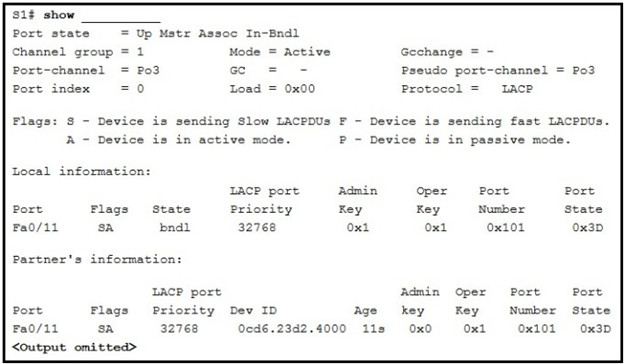 Correct
Correct
Incorrect
Hint
The show interfaces fastethernet 0/11 etherchannel command will show the EtherChannel information for the FastEthernet 0/11 interface. The displayed information includes the port channel it belongs to, the current mode, and the channel group, among other information. -
Question 44 of 55
44. Question
1 pointsRefer to the exhibit. The administrator wants to enable port security on an interface on switch S1, but the command was rejected. Which conclusion can be drawn?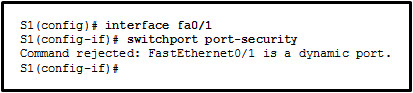 Correct
Correct
Incorrect
Hint
To enable port security, use the switchport port-security interface configuration command on an access port. By default, Layer 2 switch ports are set to dynamic auto (trunking on); therefore, the port must be initially configured as an access port before port security can be enabled. -
Question 45 of 55
45. Question
1 pointsOn which port should Dynamic ARP Inspection (DAI) be configured on a switch?Correct
Incorrect
Hint
DHCP snooping must be enabled on a port where DAI is configured, because DAI requires the DHCP snooping table to operate. Only a trusted interface, such as an uplink port between switches, is configured to implement DAI. All access ports are untrusted. -
Question 46 of 55
46. Question
1 pointsRefer to the exhibit. A network administrator is configuring DAI on switch SW1. What is the result of entering the exhibited commands? Correct
Correct
Incorrect
Hint
DAI can be configured to check for destination MAC, source MAC, and IP addresses. However, only one ip arp inspection validate command can be configured. Entering multiple ip arp inspection validate commands overwrites the previous command. -
Question 47 of 55
47. Question
1 pointsWhich Cisco solution helps prevent ARP spoofing and ARP poisoning attacks?Correct
Incorrect
Hint
Cisco provides solutions to help mitigate Layer 2 attacks. The solutions include the following: IP Source Guard (IPSG) – prevents MAC and IP address spoofing attacks Dynamic ARP Inspection (DAI) – prevents ARP spoofing and ARP poisoning attacks DHCP Snooping – prevents DHCP starvation and SHCP spoofing attacks Port Security – prevents many types of attacks including MAC table overflow attacks and DHCP starvation attacks -
Question 48 of 55
48. Question
1 pointsWhat is the reason for disabling SSID broadcasting and changing the default SSID on a wireless access point?Correct
Incorrect
Hint
The SSID is the name of the wireless network. Changing the default SSID forces device users to manually enter the SSID in order to gain access to the network. Broadcasting the SSID does not allow other devices to access the configuration, or to discover the MAC address of the device. SSID broadcasts do not affect radio frequency bandwidth. -
Question 49 of 55
49. Question
1 pointsWhat are two characteristics of Cisco Express Forwarding (CEF)? (Choose two.)Correct
Incorrect
Hint
Cisco Express Forwarding (CEF) builds a forwarding information base (FIB) and an adjacency table to be able to route packets quicker than traditional packet forwarding methods can. -
Question 50 of 55
50. Question
1 pointsA network administrator of a college is configuring WLAN security with WPA2 Enterprise authentication. Which server is required when deploying this type of authentication?Correct
Incorrect
Hint
WAP2 Enterprise provides stronger secure user authentication than WPA2 PSK does. Instead of using a pre-shared key for all users to access a WLAN, WPA2 Enterprise requires that users enter their own username and password credentials to be authenticated before they can access the WLAN. The RADIUS server is required for deploying WPA2 Enterprise authentication. -
Question 51 of 55
51. Question
1 pointsWhat is a potential issue when using the WLC to upgrade and deploy the latest firmware image to all APs?Correct
Incorrect
Hint
When APs are performing a firmware upgrade, users will be disconnected from the WLAN and the internet until the upgrade finishes. The wireless router may need to reboot several times before normal network operations are restored. -
Question 52 of 55
52. Question
1 pointsA network administrator is configuring a WLC to provide WLAN access to users in an office building. When testing the newly created WLAN, the administrator does not see the SSID from a wireless device. What is a possible cause?Correct
Incorrect
Hint
After a new WLAN is created and configured on a WLC, it should be enabled before it can be accessed by users. -
Question 53 of 55
53. Question
1 pointsWhat is the best way to prevent a VLAN hopping attack?Correct
Incorrect
Hint
VLAN hopping attacks rely on the attacker being able to create a trunk link with a switch. Disabling DTP and configuring user-facing ports as static access ports can help prevent these types of attacks. Disabling the Spanning Tree Protocol (STP) will not eliminate VLAN hopping attacks. -
Question 54 of 55
54. Question
1 pointsAn administrator has configured a DHCPv4 relay router and issued these commands:Router(config)# interface g0/0 Router(config-if)# ip address 10.0.1.1 255.255.255.0 Router(config-if)# no shutdown Router(config-if)# exit Router(config)# ip dhcp pool RELAY Router(dhcp-config)# end
The clients are not receiving IP parameters from the DHCPv4 server. What is a possible cause?Correct
Incorrect
Hint
This router should be configured with the ip helper-address command, followed with the IP address of the DHCPv4 server, because the router is meant to be used as a relay agent. The ip dhcp pool RELAY command just names the DHCPv4 pool, and it does not enable the relay function. -
Question 55 of 55
55. Question
1 pointsConsider the following command:ip route 192.168.10.0 255.255.255.0 10.10.10.2 5
What does the 5 at the end of the command signify?Correct
Incorrect
Hint
The 5 at the end of the command signifies administrative distance. This value is added to floating static routes or routes that only appear in the routing table when the preferred route has gone down. The 5 at the end of the command signifies administrative distance configured for the static route. This value indicates that the floating static route will appear in the routing table when the preferred route (with an administrative distance less than 5) is down.
