ENSA Bridging Exam Answers
Enterprise Networking, Security, and Automation (Version 7.00) – Network Security and Automation Exam
1. Which protocol is attacked when a cybercriminal provides an invalid gateway in order to create a man-in-the-middle attack?
- HTTP or HTTPS
- DHCP
- DNS
- ICMP
Explanation: A cybercriminal could set up a rogue DHCP server that provides one or more of the following:
Wrong default gateway that is used to create a man-in-the-middle attack and allow the attacker to intercept data
Wrong DNS server that results in the user being sent to a malicious website
Invalid default gateway IP address that results in a denial of service attack on the DHCP client
2. In which TCP attack is the cybercriminal attempting to overwhelm a target host with half-open TCP connections?
- reset attack
- port scan attack
- session hijacking attack
- SYN flood attack
Explanation: In a TCP SYN flood attack, the attacker sends to the target host a continuous flood of TCP SYN session requests with a spoofed source IP address. The target host responds with a TCP-SYN-ACK to each of the SYN session requests and waits for a TCP ACK that will never arrive. Eventually the target is overwhelmed with half-open TCP connections.
3. Which statement describes an important characteristic of a site-to-site VPN?
- It requires using a VPN client on the host PC.
- After the initial connection is established, it can dynamically change connection information.
- It is ideally suited for use by mobile workers.
- It must be statically set up.
- It is commonly implemented over dialup and cable modem networks.
Explanation: A site-to-site VPN is created between the network devices of two separate networks. The VPN is static and stays established. The internal hosts of the two networks have no knowledge of the VPN.
4. Which statement describes a VPN?
- VPNs use open source virtualization software to create the tunnel through the Internet.
- VPNs use logical connections to create public networks through the Internet.
- VPNs use dedicated physical connections to transfer data between remote users.
- VPNs use virtual connections to create a private network through a public network.
Explanation: A VPN is a private network that is created over a public network. Instead of using dedicated physical connections, a VPN uses virtual connections routed through a public network between two network devices.
5. How is the YAML data format structure different from JSON?
- It uses brackets and commas.
- It uses indentations.
- It uses end tags.
- It uses hierarchical levels of nesting.
Explanation: The structure in YAML is defined by indentations rather than brackets and commas.
6. What is the most widely used API for web services?
- REST
- JSON-RPC
- XML-RPC
- SOAP
Explanation: REST accounts for more than 80% of all API types used for web services, making it the most widely used web service API.
7. What is the significant characteristic of worm malware?
- A worm can execute independently of the host system.
- Once installed on a host system, a worm does not replicate itself.
- Worm malware disguises itself as legitimate software.
- A worm must be triggered by an event on the host system.
Explanation: Worm malware can execute and copy itself without being triggered by a host program. It is a significant network and Internet security threat.
8. Which statement accurately characterizes the evolution of threats to network security?
- Threats have become less sophisticated while the technical knowledge needed by an attacker has grown.
- Internet architects planned for network security from the beginning.
- Internal threats can cause even greater damage than external threats.
- Early Internet users often engaged in activities that would harm other users.
Explanation: Internal threats can be intentional or accidental and cause greater damage than external threats because the internal user has direct access to the internal corporate network and corporate data.
9. Which requirement of secure communications is ensured by the implementation of MD5 or SHA hash generating algorithms?
- nonrepudiation
- authentication
- integrity
- confidentiality
Explanation: Integrity is ensured by implementing either MD5 or SHA hash generating algorithms. Many modern networks ensure authentication with protocols, such as HMAC. Data confidentiality is ensured through symmetric encryption algorithms, including DES, 3DES, and AES. Data confidentiality can also be ensured using asymmetric algorithms, including RSA and PKI.
10. In what type of attack is a cybercriminal attempting to prevent legitimate users from accessing network services?
- DoS
- address spoofing
- MITM
- session hijacking
Explanation: In a DoS or denial-of-service attack, the goal of the attacker is to prevent legitimate users from accessing network services.
11. What is the best description of Trojan horse malware?
- It appears as useful software but hides malicious code.
- It is malware that can only be distributed over the Internet.
- It is software that causes annoying but not fatal computer problems.
- It is the most easily detected form of malware.
Explanation: The best description of Trojan horse malware, and what distinguishes it from viruses and worms, is that it appears as useful software but hides malicious code. Trojan horse malware may cause annoying computer problems, but can also cause fatal problems. Some Trojan horses may be distributed over the Internet, but they can also be distributed by USB memory sticks and other means. Specifically targeted Trojan horse malware can be some of the most difficult malware to detect.
12. What is a feature of an IPS?
- It is primarily focused on identifying possible incidents.
- It can stop malicious packets.
- It has no impact on latency.
- It is deployed in offline mode.
Explanation: An advantage of an intrusion prevention systems (IPS) is that it can identify and stop malicious packets. However, because an IPS is deployed inline, it can add latency to the network.
13. Which type of hacker is motivated to protest against political and social issues?
- script kiddie
- vulnerability broker
- hacktivist
- cybercriminal
Explanation: Hackers are categorized by motivating factors. Hacktivists are motivated by protesting political and social issues.
14. In which type of attack is falsified information used to redirect users to malicious Internet sites?
- DNS cache poisoning
- ARP cache poisoning
- DNS amplification and reflection
- domain generation
Explanation: In a DNS cache poisoning attack, falsified information is used to redirect users from legitimate to malicious internet sites.
15. Which attack involves threat actors positioning themselves between a source and destination with the intent of transparently monitoring, capturing, and controlling the communication?
- ICMP attack
- man-in-the-middle attack
- SYN flood attack
- DoS attack
Explanation: The man-in-the-middle attack is a common IP-related attack where threat actors position themselves between a source and destination to transparently monitor, capture, and control the communication.
16. What is the function of the Diffie-Hellman algorithm within the IPsec framework?
- provides authentication
- allows peers to exchange shared keys
- guarantees message integrity
- provides strong data encryption
Explanation: The IPsec framework uses various protocols and algorithms to provide data confidentiality, data integrity, authentication, and secure key exchange. DH (Diffie-Hellman) is an algorithm used for key exchange. DH is a public key exchange method that allows two IPsec peers to establish a shared secret key over an insecure channel.
17. What is the function of the Hashed Message Authentication Code (HMAC) algorithm in setting up an IPsec VPN?
- authenticates the IPsec peers
- protects IPsec keys during session negotiation
- creates a secure channel for key negotiation
- guarantees message integrity
Explanation: The IPsec framework uses various protocols and algorithms to provide data confidentiality, data integrity, authentication, and secure key exchange. The Hashed Message Authentication Code (HMAC) is a data integrity algorithm that uses a hash value to guarantee the integrity of a message.
18. What algorithm is used with IPsec to provide data confidentiality?
- MD5
- Diffie-Hellman
- SHA
- RSA
- AES
Explanation: The IPsec framework uses various protocols and algorithms to provide data confidentiality, data integrity, authentication, and secure key exchange. Two popular algorithms that are used to ensure that data is not intercepted and modified (data integrity) are MD5 and SHA. AES is an encryption protocol and provides data confidentiality. DH (Diffie-Hellman) is an algorithm that is used for key exchange. RSA is an algorithm that is used for authentication.
19. What are two hashing algorithms used with IPsec AH to guarantee authenticity? (Choose two.)
Explanation: The IPsec framework uses various protocols and algorithms to provide data confidentiality, data integrity, authentication, and secure key exchange. Two popular algorithms used to ensure that data is not intercepted and modified (data integrity and authenticity) are MD5 and SHA.
20. What two algorithms can be part of an IPsec policy to provide encryption and hashing to protect interesting traffic? (Choose two.)
Explanation: The IPsec framework uses various protocols and algorithms to provide data confidentiality, data integrity, authentication, and secure key exchange. Two algorithms that can be used within an IPsec policy to protect interesting traffic are AES, which is an encryption protocol, and SHA, which is a hashing algorithm.
21. Which protocol creates a virtual point-to-point connection to tunnel unencrypted traffic between Cisco routers from a variety of protocols?
Explanation: Generic Routing Encapsulation (GRE) is a tunneling protocol developed by Cisco that encapsulates multiprotocol traffic between remote Cisco routers. GRE does not encrypt data. OSPF is a open source routing protocol. IPsec is a suite of protocols that allow for the exchange of information that can be encrypted and verified. Internet Key Exchange (IKE) is a key management standard used with IPsec.
22. Which two end points can be on the other side of an ASA site-to-site VPN configured using ASDM? (Choose two.)
- multilayer switch
- ISR router
- DSL switch
- Frame Relay switch
- another ASA
Explanation: ASDM supports creating an ASA site-to-site VPN between two ASAs or between an ASA and an ISR router.
23. Which two types of VPNs are examples of enterprise-managed remote access VPNs? (Choose two.)
- client-based IPsec VPN
- IPsec VPN
- clientless SSL VPN
- IPsec Virtual Tunnel Interface VPN
- GRE over IPsec VPN
Explanation: Enterprise managed VPNs can be deployed in two configurations:
Remote Access VPN – This VPN is created dynamically when required to establish a secure connection between a client and a VPN server. Remote access VPNs include client-based IPsec VPNs and clientless SSL VPNs.
Site-to-site VPN – This VPN is created when interconnecting devices are preconfigured with information to establish a secure tunnel. VPN traffic is encrypted only between the interconnecting devices, and internal hosts have no knowledge that a VPN is used. Site-to-site VPNs include IPsec, GRE over IPsec, Cisco Dynamic Multipoint (DMVPN), and IPsec Virtual Tunnel Interface (VTI) VPNs.
24. Which two technologies provide enterprise-managed VPN solutions? (Choose two.)
- Layer 3 MPLS VPN
- site-to-site VPN
- Layer 2 MPLS VPN
- remote access VPN
- Frame Relay
Explanation: VPNs can be managed and deployed as either of two types:
Enterprise VPNs – Enterprise-managed VPNs are a common solution for securing enterprise traffic across the internet. Site-to-site and remote access VPNs are examples of enterprise managed VPNs.
Service Provider VPNs – Service provider managed VPNs are created and managed over the provider network. Layer 2 and Layer 3 MPLS are examples of service provider managed VPNs. Other legacy WAN solutions include Frame Relay and ATM VPNs.
25. Which action takes place in the assurance element of the IBN model?
- integrity checks
- translation of policies
- verification and corrective action
- configuring systems
Explanation: The assurance element of the IBN model is concerned with end-to-end verification of network-wide behavior.
26. Which RESTFul operation corresponds to the HTTP GET method?
Explanation: RESTful operations correspond to the following HTTP methods (shown to the left with the RESTful operation on the right):
POST > Create
GET > Read
PUT/PATCH > Update
DELETE > Delete
27. What is REST?
- It is an architecture style for designing web service applications.
- It is a way to store and interchange data in a structured format.
- It is a protocol that allows administrators to manage nodes on an IP network.
- It is a human readable data structure that is used by applications for storing, transforming, and reading data.
Explanation: REST is not a protocol or service, but rather a style of software architecture for designing web service applications.
28. What is a difference between the XML and HTML data formats?
- XML does not use predefined tags whereas HTML does use predefined tags.
- XML encloses data within a pair of tags whereas HTML uses a pair of quotation makes to enclose data.
- XML does not require indentation for each key/value pair but HTML does require indentation.
- XML formats data in binary whereas HTML formats data in plain text.
Explanation: XML is a human readable data structure used to store, transfer, and read data by applications. Like HTML, XML uses a related set of tags to enclose data. However, unlike HTML, XML uses no predefined tags or document structure.
29. Refer to the exhibit. Which data format is used to represent the data for network automation applications?

Explanation: The common data formats that are used in many applications including network automation and programmability are as follows:
JavaScript Object Notation (JSON) – In JSON, the data known as an object is one or more key/value pairs enclosed in braces { }. Keys must be strings within double quotation marks ” “. Keys and values are separated by a colon.
eXtensible Markup Language (XML) – In XML, the data is enclosed within a related set of tags <tag>data</tag>.
YAML Ain’t Markup Language (YAML) – In YAML, the data known as an object is one or more key value pairs. Key value pairs are separated by a colon without the use of quotation marks. YAML uses indentation to define its structure, without the use of brackets or commas.
30. What is the function of the key contained in most RESTful APIs?
- It is the top-level object of the API query.
- It is used to authenticate the requesting source.
- It is used in the encryption of the message by an API request.
- It represents the main query components in the API request.
Explanation: Many RESTful APIs, including public APIs, require a key. The key is used to identify the source of the request through authentication.
31. Match the term to the RESTful API request http://www.mapquestapi.com/directions/v2/route?outFormat=json&key=KEY&from=San+Jose,Ca&to=Monterey,Ca component. (Not all options are used.)
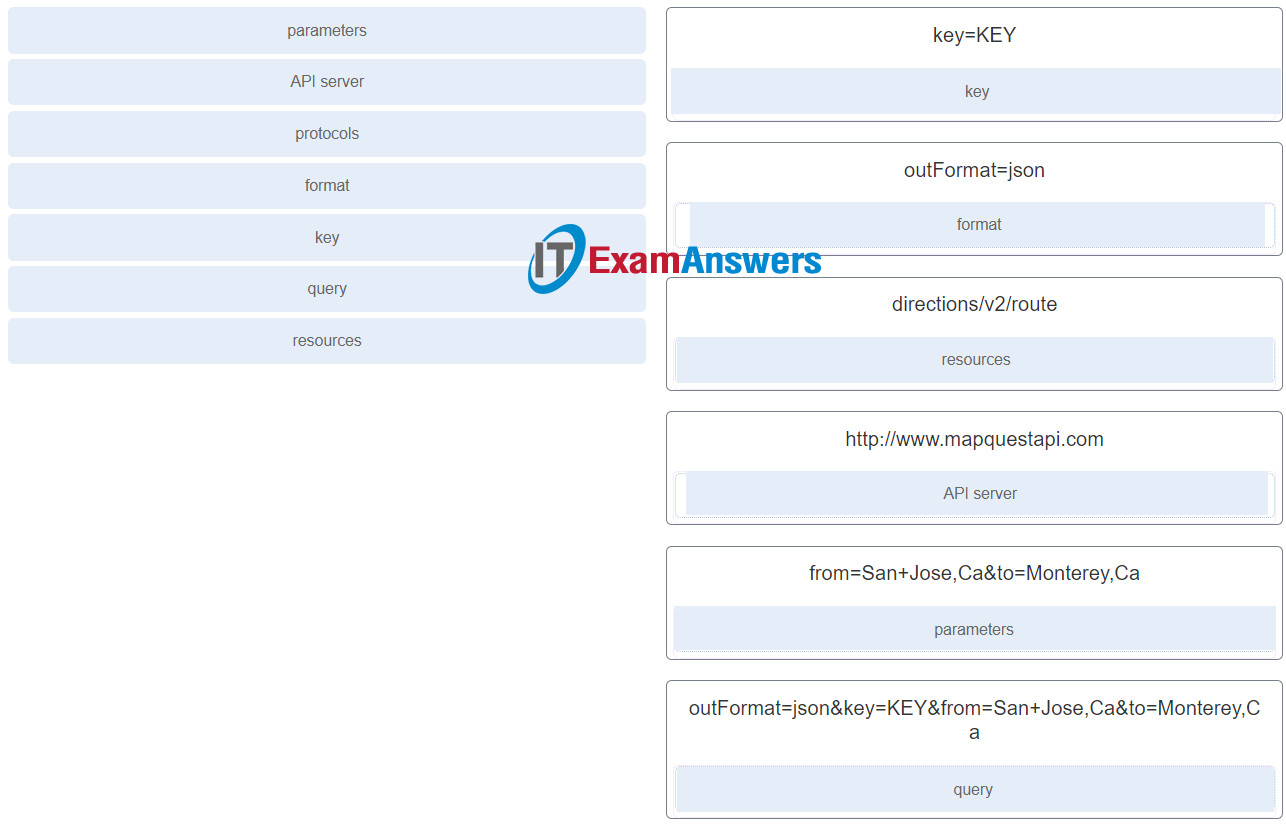
Match the term to the RESTful API request http://www.mapquestapi.com/directions/v2/route?outFormat=json&key=KEY&from=San+Jose,Ca&to=Monterey,Ca component. (Not all options are used.)
32. Which two configuration management tools are developed using Ruby? (Choose two.)
- Puppet
- Ansible
- SaltStack
- RESTCONF
- Chef
Explanation: Chef and Puppet are configuration management tools developed using Ruby. Ansible and SaltStack are configuration management tools developed using Python. Ruby is typically considered a more difficult language to learn than Python. RESTCONF is a network management protocol.
33. In which situation would a partner API be appropriate?
- a vacation service site interacting with hotel databases to display information from all the hotels on its web site
- an internet search engine allowing developers to integrate the search engine into their own software applications
- company sales staff accessing internal sales data from their mobile devices
- someone creating an account on an external app or website by using his or her social media credentials
Explanation: Partner API programs incorporate collaboration with other business. They facilitate communication and integration of software between a company and its business partners.
34. A user receives a phone call from a person who claims to represent IT services and then asks that user for confirmation of username and password for auditing purposes. Which security threat does this phone call represent?
- anonymous keylogging
- social engineering
- DDoS
- spam
Explanation: Social engineering attempts to gain the confidence of an employee and convince that person to divulge confidential and sensitive information, such as usernames and passwords. DDoS attacks, spam, and keylogging are all examples of software based security threats, not social engineering.
35. If an asymmetric algorithm uses a public key to encrypt data, what is used to decrypt it?
- DH
- a digital certificate
- a private key
- a different public key
Explanation: When an asymmetric algorithm is used, public and private keys are used for the encryption. Either key can be used for encryption, but the complementary matched key must be used for the decryption. For example if the public key is used for encryption, then the private key must be used for the decryption.
36. What is a ping sweep?
- a scanning technique that examines a range of TCP or UDP port numbers on a host to detect listening services.
- a query and response protocol that identifies information about a domain, including the addresses that are assigned to that domain.
- a network scanning technique that indicates the live hosts in a range of IP addresses.
- a software application that enables the capture of all network packets that are sent across a LAN.
Explanation: A ping sweep is a tool that is used during a reconnaissance attack. Other tools that might be used during this type of attack include a ping sweep, port scan, or Internet information query. A reconnaissance attack is used to gather information about a particular network, usually in preparation for another type of network attack.
37. In what way are zombies used in security attacks?
- They are infected machines that carry out a DDoS attack.
- They target specific individuals to gain corporate or personal information.
- They probe a group of machines for open ports to learn which services are running.
- They are maliciously formed code segments used to replace legitimate applications.
Explanation: Zombies are infected computers that make up a botnet. The zombies are used to deploy a distributed denial of service (DDoS) attack.
38. Which VPN solution allows the use of a web browser to establish a secure, remote-access VPN tunnel to the ASA?
- site-to-site using an ACL
- clientless SSL
- site-to-site using a preshared key
- client-based SSL
Explanation: When a web browser is used to securely access the corporate network, the browser must use a secure version of HTTP to provide SSL encryption. A VPN client is not required to be installed on the remote host, so a clientless SSL connection is used.
39. What is YAML?
- It is a scripting language.
- It is a data format and superset of JSON.
- It is a compiled programming language.
- It is a web application.
Explanation: Like JSON, YAML Ain’t Markup Language (YAML) is a data format used by applications to store and transport data. YAML is considered a superset of JSON.
40. Which term is used to describe a set of instructions for execution by the configuration management tool Puppet?
- Manifest
- Playbook
- Pillar
- Cookbook
Explanation: The configuration management tool Puppet uses the name Manifest to describe the set of instructions to be executed.
41. Which term is used to describe a set of instructions for execution by the configuration management tool SaltStack?
- Cookbook
- Pillar
- Playbook
- Manifest
Explanation: The configuration management tool SaltStack uses the name Pillar to describe the set of instructions to be executed.
42. Which scenario describes the use of a public API?
- It is used only within an organization.
- It can be used with no restrictions.
- It is used between a company and its business partners.
- It requires a license.
Explanation: Public, or open, APIs have no restrictions and are available to the public. Some API providers do require a user to obtain a free key or token prior to using the API in order to control the volume of API requests received and processed.
43. Which IPsec security function provides assurance that the data received via a VPN has not been modified in transit?
- confidentiality
- secure key exchange
- authentication
- integrity
Explanation: Integrity is a function of IPsec and ensures data arrives unchanged at the destination through the use of a hash algorithm. Confidentiality is a function of IPsec and utilizes encryption to protect data transfers with a key. Authentication is a function of IPsec and provides specific access to users and devices with valid authentication factors. Secure key exchange is a function of IPsec and allows two peers to maintain their private key confidentiality while sharing their public key.
44. Which is a requirement of a site-to-site VPN?
- It requires the placement of a VPN server at the edge of the company network.
- It requires hosts to use VPN client software to encapsulate traffic.
- It requires a client/server architecture.
- It requires a VPN gateway at each end of the tunnel to encrypt and decrypt traffic.
Explanation: Site-to-site VPNs are static and are used to connect entire networks. Hosts have no knowledge of the VPN and send TCP/IP traffic to VPN gateways. The VPN gateway is responsible for encapsulating the traffic and forwarding it through the VPN tunnel to a peer gateway at the other end which decapsulates the traffic.


