2.7.2 Lab – Configure Single-Area OSPFv2 (Instructor Version)
Topology
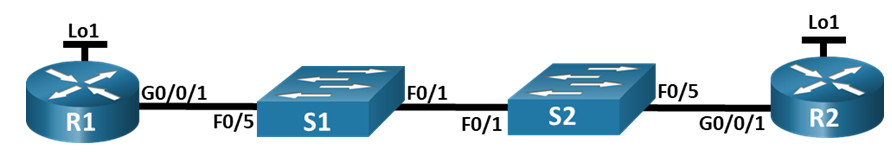
Addressing Table
| Device | Interface | IP Address | Subnet Mask |
|---|---|---|---|
| R1 | G0/0/1 | 10.53.0.1 | 255.255.255.0 |
| Loopback1 | 172.16.1.1 | 255.255.255.0 | |
| R2 | G0/0/1 | 10.53.0.2 | 255.255.255.0 |
| Loopback1 | 192.168.1.1 | 255.255.255.0 |
Objectives
- Part 1: Build the Network and Configure Basic Device Settings
- Part 2: Configure and Verify Single-Area OSPFv2 for basic operation
- Part 3: Optimize and Verify the Single-Area OSPFv2 configuration
Background / Scenario
Instructor Note: This lab has been built to use two routers with no serial interfaces. The switches indicated in the topology are optional. If you have a third router you can introduce into the pod, suggest you add it to one of the switches to create a true multi-access network. You could also directly connect the third router to one of the other routers, creating an additional point-to-point network.
You have been tasked with configuring a small company’s network using OSPFv2. R1 will be hosting an internet connection (simulated by interface Loopback 1) and sharing the default route information to R2. After the initial configuration, the organization has asked for the configuration to be optimized to reduce protocol traffic and ensure that R1 remains in control of routing.
Note: The static routing approach used in this lab is to assess your ability to configure and adjust OSPFv2 in a single-area configuration. This approach used in this lab may not reflect networking best practices.
Note: The routers used with CCNA hands-on labs are Cisco 4221 with Cisco IOS XE Release 16.9.4 (universalk9 image). The switches used in the labs are Cisco Catalyst 2960s with Cisco IOS Release 15.2(2) (lanbasek9 image). Other routers, switches, and Cisco IOS versions can be used. Depending on the model and Cisco IOS version, the commands available and the output produced might vary from what is shown in the labs. Refer to the Router Interface Summary Table at the end of the lab for the correct interface identifiers.
Note: Ensure that the routers and switches have been erased and have no startup configurations. If you are unsure contact your instructor.
Instructor Note: Refer to the Instructor Lab Manual for the procedures to initialize and reload devices.
Required Resources
- 2 Routers (Cisco 4221 with Cisco IOS XE Release 16.9.4 universal image or comparable)
- 2 Switches (Cisco 2960 with Cisco IOS Release 15.2(2) lanbasek9 image or comparable)
- 1 PC (Windows with a terminal emulation program, such as Tera Term)
- Console cables to configure the Cisco IOS devices via the console ports
- Ethernet cables as shown in the topology
Instructions
Part 1: Build the Network and Configure Basic Device Settings.
Step 1: Cable the network as shown in the topology.
Attach the devices as shown in the topology diagram, and cable as necessary.
Step 2: Configure basic settings for each router.
a. Assign a device name to each router.
router(config)# hostname R1 router(config)# hostname R2
b. Disable DNS lookup to prevent the router from attempting to translate incorrectly entered commands as though they were host names.
R1(config)# no ip domain lookup R2(config)# no ip domain lookup
c. Assign class as the privileged EXEC encrypted password.
R1(config)# enable secret class R2(config)# enable secret class
d. Assign cisco as the console password and enable login.
R1(config)# line console 0 R1(config-line)# password cisco R1(config-line)# login R2(config)# line console 0 R2(config-line)# password cisco R2(config-line)# login
e. Assign cisco as the VTY password and enable login.
R1(config)# line vty 0 4 R1(config-line)# password cisco R1(config-line)# login R2(config)# line vty 0 4 R2(config-line)# password cisco R2(config-line)# login
f. Encrypt the plaintext passwords.
R1(config)# service password-encryption R2(config)# service password-encryption
g. Create a banner that warns anyone accessing the device that unauthorized access is prohibited.
R1(config)# banner motd $ Authorized Users Only! $ R2(config)# banner motd $ Authorized Users Only! $
h. Save the running configuration to the startup configuration file.
R1# copy running-config startup-config R2# copy running-config startup-config
Step 3: Configure basic settings for each switch.
a. Assign a device name to each switch.
switch(config)# hostname S1 switch(config)# hostname S2
b. Disable DNS lookup to prevent the router from attempting to translate incorrectly entered commands as though they were host names.
S1(config)# no ip domain lookup S2(config)# no ip domain lookup
c. Assign class as the privileged EXEC encrypted password.
S1(config)# enable secret class S2(config)# enable secret class
d. Assign cisco as the console password and enable login.
S1(config)# line console 0 S1(config-line)# password cisco S1(config-line)# login S2(config)# line console 0 S2(config-line)# password cisco S2(config-line)# login
e. Assign cisco as the VTY password and enable login.
S1(config)# line vty 0 15 S1(config-line)# password cisco S1(config-line)# login S2(config)# line vty 0 15 S2(config-line)# password cisco S2(config-line)# login
f. Encrypt the plaintext passwords.
S1(config)# service password-encryption S2(config)# service password-encryption
g. Create a banner that warns anyone accessing the device that unauthorized access is prohibited.
S1(config)# banner motd $ Authorized Users Only! $ S2(config)# banner motd $ Authorized Users Only! $
h. Save the running configuration to the startup configuration file.
S1# copy running-config startup-config S2# copy running-config startup-config
Part 2: Configure and Verify Single-Area OSPFv2 for basic operation.
Step 1: Configure interface addresses and basic OSPFv2 on each router.
a. Configure interface addresses on each router as shown in the Addressing Table above.
R1(config)# interface g0/0/1 R1(config-if)# ip address 10.53.0.1 255.255.255.0 R1(config-if)# no shut R1(config-if)# exit R1(config)# interface loopback 1 R1(config-if)# ip address 172.16.1.1 255.255.255.0 R1(config-if)# exit R2(config)# interface g0/0/1 R2(config-if)# ip address 10.53.0.2 255.255.255.0 R2(config-if)# no shut R2(config-if)# exit R2(config)# interface loopback 1 R2(config-if)# ip address 192.168.1.1 255.255.255.0 R2(config-if)# exit
b. Enter OSPF router configuration mode using process ID 56.
R1(config)# router ospf 56 R2(config)# router ospf 56
c. Configure a static router ID for each router (1.1.1.1 for R1, 2.2.2.2 for R2).
R1(config-router)# router-id 1.1.1.1 R2(config-router)# router-id 2.2.2.2
d. Configure a network statement for the network between R1 and R2 placing it in area 0.
R1(config-router)# network 10.53.0.0 0.0.0.255 area 0 R2(config-router)# network 10.53.0.0 0.0.0.255 area 0
e. On R2 only, add the configuration necessary to advertise the Loopback 1 network into OSPF area 0.
R2(config-router)# network 192.168.1.0 0.0.0.255 area 0
OR
R2(config)# interface loopback1 R2(config-if)# ip ospf 56 area 0
f. Verify OSPFv2 is operational between the routers. Issue the command to verify R1 and R2 have formed an adjacency.
R1# show ip ospf neighbor Neighbor ID Pri State Dead Time Address Interface 2.2.2.2 1 FULL/DR 00:00:33 10.53.0.2 GigabitEthernet0/0/1 R2# show ip ospf neighbor Neighbor ID Pri State Dead Time Address Interface 1.1.1.1 1 FULL/BDR 00:00:37 10.53.0.1 GigabitEthernet0/0/1
Which router is identified as the DR? Which is the BDR? What was the selection criteria?
Answers will vary. In this example R1 was configured first and was speaking OSPF before R2. So during the OSPF election only R1 was configured for OSPF and became the DR. After R2 was configured for OSPF it became the BDR on the Gigabit segment. The router with the highest router ID is used in the selection of DR and BDR.
g. On R1, issue the show ip route ospf command to verify that the R2 Loopback1 network is present in the routing table. Notice the default behavior of OSPF is to advertise a loopback interface as a host route using a 32 bit mask.
R1# show ip route ospf
<output omitted>
Gateway of last resort is not set
192.168.1.0/32 is subnetted, 1 subnets
O 192.168.1.1 [110/2] via 10.53.0.2, 00:03:12, GigabitEthernet0/0/1
h. Ping the R2 Loopback 1 interface address from R1. The ping should succeed.
R1# ping 192.168.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
Part 3: Optimize the Single-Area OSPFv2 configuration
Step 1: Implement various optimizations on each router.
a. On R1, configure the interface G0/0/1 OSPF priority to 50 to ensure R1 is the Designated Router.
R1(config)# interface g0/0/1 R1(config-if)# ip ospf priority 50
b. Configure the OSPF timers on the G0/0/1 of each router for a hello timer of 30 seconds.
R1(config)# interface g0/0/1 R1(config-if)# ip ospf hello-interval 30 R2(config)# interface g0/0/1 R1(config-if)# ip ospf hello-interval 30
c. On R1, configure a default static route that uses interface Loopback 1 as the exit interface. Then, propagate the default route into OSPF. Note the console message after setting the default route.
R1(config)# ip route 0.0.0.0 0.0.0.0 loopack 1 %Default route without gateway, if not a point-to-point interface, may impact performance R1(config)# router ospf 56 R1(config-router)# default-information originate
d. On R2 only, add the configuration necessary for OSPF to treat R2 Loopback 1 like a point-to-point network. This results in OSPF advertising Loopback 1 using the interface subnet mask.
R2(config)# interface loopback 1 R2(config-if)# ip ospf network point-to-point R2(config-if)# exit
e. On R2 only, add the configuration necessary to prevent OSPF advertisements from being sent to the Loopback 1 network.
R2(config)# router ospf 56 R2(config-router)# passive-interface loopback 1 R2(config-router)# exit
f. Change the reference bandwidth on each router to 1Gbs. After this configuration, restart OSPF using the clear ip ospf process command. Note the console message after setting the new reference bandwidth.
R1(config)# router ospf 56 R1(config-router)# auto-cost reference-bandwidth 1000 %OSPF: Reference bandwidth is changed. Please ensure reference bandwidth is consistent across all routers. R1(config-router)# end R1# clear ip ospf process Reset ALL OSPF processes? [no]: yes R2(config)# router ospf 56 R2(config-router)# auto-cost reference-bandwidth 1000 %OSPF: Reference bandwidth is changed. Please ensure reference bandwidth is consistent across all routers. R2(config-router)# end R2# clear ip ospf process Reset ALL OSPF processes? [no]: yes
Step 2: Verify OSPFv2 optimizations are in place.
a. Issue the show ip ospf interface g0/0/1 command on R1 and verify that the interface priority has been set to 50 and that the time intervals are Hello 30, Dead 120, and the default Network Type is Broadcast
R1# show ip ospf interface g0/0/1
GigabitEthernet0/0/1 is up, line protocol is up
Internet Address 10.53.0.1/24, Interface ID 7, Area 0
Attached via Network Statement
Process ID 56, Router ID 1.1.1.1, Network Type BROADCAST, Cost: 10
Topology-MTID Cost Disabled Shutdown Topology Name
0 10 no no Base
Transmit Delay is 1 sec, State DR, Priority 50
Designated Router (ID) 1.1.1.1, Interface address 10.53.0.1
Backup Designated router (ID) 2.2.2.2, Interface address 10.53.0.2
Timer intervals configured, Hello 30, Dead 120, Wait 120, Retransmit 5
oob-resync timeout 120
Hello due in 00:00:09
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Index 1/1/1, flood queue length 0
Next 0x0(0)/0x0(0)/0x0(0)
Last flood scan length is 1, maximum is 1
Last flood scan time is 0 msec, maximum is 0 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 2.2.2.2 (Backup Designated Router)
Suppress hello for 0 neighbor(s)
b. On R1, issue the show ip route ospf command to verify that the R2 Loopback1 network is present in the routing table. Note the difference in the metric between this output and the previous output. Also note the mask is now 24 bits as opposed to the 32 bits previously advertised.
R1# show ip route ospf <output omitted> Gateway of last resort is 0.0.0.0 to network 0.0.0.0 O 192.168.1.0/24 [110/11] via 10.53.0.2, 00:03:11, GigabitEthernet0/0/1
c. On R2, issue the show ip route ospf command. The only OSPF route information should be the default route R1 is propagating.
R2# show ip route ospf
d. Ping the R1 Loopback 1 interface address from R2. The ping should succeed.
R2# ping 172.16.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 172.16.1.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
Why is the OSPF cost for the default route different than the OSPF cost at R1 for the 192.168.1.0/24 network?
A default static route imported into OSPF is given the metric type of “E2” or External Type 2 by default. An “E2” by default, keeps the same OSPF cost across the entire OSPF network. In this case, the metric for the default route was 1, so it has a metric of 1 everywhere in the OSPF 56 network. The 192.168.1.0 /24 network is an internal OSPF route whose metric is cumulative.
Router Interface Summary Table
| Router Model | Ethernet Interface #1 | Ethernet Interface #2 | Serial Interface #1 | Serial Interface #2 |
|---|---|---|---|---|
| 1800 | Fast Ethernet 0/0 (F0/0) | Fast Ethernet 0/1 (F0/1) | Serial 0/0/0 (S0/0/0) | Serial 0/0/1 (S0/0/1) |
| 1900 | Gigabit Ethernet 0/0 (G0/0) | Gigabit Ethernet 0/1 (G0/1) | Serial 0/0/0 (S0/0/0) | Serial 0/0/1 (S0/0/1) |
| 2801 | Fast Ethernet 0/0 (F0/0) | Fast Ethernet 0/1 (F0/1) | Serial 0/1/0 (S0/1/0) | Serial 0/1/1 (S0/1/1) |
| 2811 | Fast Ethernet 0/0 (F0/0) | Fast Ethernet 0/1 (F0/1) | Serial 0/0/0 (S0/0/0) | Serial 0/0/1 (S0/0/1) |
| 2900 | Gigabit Ethernet 0/0 (G0/0) | Gigabit Ethernet 0/1 (G0/1) | Serial 0/0/0 (S0/0/0) | Serial 0/0/1 (S0/0/1) |
| 4221 | Gigabit Ethernet 0/0/0 (G0/0/0) | Gigabit Ethernet 0/0/1 (G0/0/1) | Serial 0/1/0 (S0/1/0) | Serial 0/1/1 (S0/1/1) |
| 4300 | Gigabit Ethernet 0/0/0 (G0/0/0) | Gigabit Ethernet 0/0/1 (G0/0/1) | Serial 0/1/0 (S0/1/0) | Serial 0/1/1 (S0/1/1) |
Note: To find out how the router is configured, look at the interfaces to identify the type of router and how many interfaces the router has. There is no way to effectively list all the combinations of configurations for each router class. This table includes identifiers for the possible combinations of Ethernet and Serial interfaces in the device. The table does not include any other type of interface, even though a specific router may contain one. An example of this might be an ISDN BRI interface. The string in parenthesis is the legal abbreviation that can be used in Cisco IOS commands to represent the interface.
Device Configs
Router R1
R1# show run Building configuration... Current configuration : 4138 bytes ! version 16.9 service timestamps debug datetime msec service timestamps log datetime msec service password-encryption platform qfp utilization monitor load 80 no platform punt-keepalive disable-kernel-core ! hostname R1 ! boot-start-marker boot-end-marker ! ! vrf definition Mgmt-intf ! address-family ipv4 exit-address-family ! address-family ipv6 exit-address-family ! enable secret 5 $1$uly4$WMyry1cgARCNOP6IOy9TX/ ! no aaa new-model ! no ip domain lookup ! login on-success log ! subscriber templating ! multilink bundle-name authenticated ! spanning-tree extend system-id ! redundancy mode none ! interface Loopback1 ip address 172.16.1.1 255.255.255.0 ! interface GigabitEthernet0/0/0 no ip address shutdown negotiation auto ! interface GigabitEthernet0/0/1 ip address 10.53.0.1 255.255.255.0 ip ospf hello-interval 30 ip ospf priority 50 negotiation auto ! interface Serial0/1/0 no ip address shutdown ! interface Serial0/1/1 no ip address shutdown ! router ospf 56 router-id 1.1.1.1 auto-cost reference-bandwidth 1000 network 10.53.0.0 0.0.0.255 area 0 default-information originate ! ip forward-protocol nd ip http server ip http authentication local ip http secure-server ip tftp source-interface GigabitEthernet0 ip route 0.0.0.0 0.0.0.0 Loopback1 ! control-plane ! banner motd ^C Authorized Users Only! ^C ! line con 0 password 7 121A0C041104 login transport input none stopbits 1 line aux 0 stopbits 1 line vty 0 4 password 7 05080F1C2243 login ! end
Router R2
R2# show run Building configuration... Current configuration : 4131 bytes ! version 16.9 service timestamps debug datetime msec service timestamps log datetime msec service password-encryption platform qfp utilization monitor load 80 no platform punt-keepalive disable-kernel-core ! hostname R2 ! boot-start-marker boot-end-marker ! ! vrf definition Mgmt-intf ! address-family ipv4 exit-address-family ! address-family ipv6 exit-address-family ! enable secret 5 $1$8xdp$AQl.kiynNnTKeEuMu0R8l. ! no aaa new-model ! no ip domain lookup ! ! login on-success log ! ! subscriber templating ! ! multilink bundle-name authenticated ! spanning-tree extend system-id ! ! redundancy mode none ! ! interface Loopback1 ip address 192.168.1.1 255.255.255.0 ip ospf network point-to-point ! interface GigabitEthernet0/0/0 no ip address shutdown negotiation auto ! interface GigabitEthernet0/0/1 ip address 10.53.0.2 255.255.255.0 ip ospf hello-interval 30 negotiation auto ! interface Serial0/1/0 no ip address ! interface Serial0/1/1 no ip address ! router ospf 56 router-id 2.2.2.2 auto-cost reference-bandwidth 1000 passive-interface Loopback1 network 10.53.0.0 0.0.0.255 area 0 network 192.168.1.0 0.0.0.255 area 0 ! ip forward-protocol nd ip http server ip http authentication local ip http secure-server ip tftp source-interface GigabitEthernet0 ! ! control-plane ! banner motd ^C Authorized Users Only! ^C ! line con 0 password 7 110A1016141D login transport input none stopbits 1 line aux 0 stopbits 1 line vty 0 4 password 7 030752180500 login ! ! end
Switch S1
S1# show run Building configuration... Current configuration : 1498 bytes ! version 15.0 no service pad service timestamps debug datetime msec service timestamps log datetime msec service password-encryption ! hostname S1 ! boot-start-marker boot-end-marker ! ! enable secret 5 $1$E30k$.XhXXGLUB0hquHfF.J5Fi/ ! no aaa new-model system mtu routing 1500 no ip domain-lookup ! ! spanning-tree mode pvst spanning-tree extend system-id ! vlan internal allocation policy ascending ! ! interface FastEthernet0/1 ! interface FastEthernet0/2 ! interface FastEthernet0/3 ! interface FastEthernet0/4 ! interface FastEthernet0/5 ! interface FastEthernet0/6 ! interface FastEthernet0/7 ! interface FastEthernet0/8 ! interface FastEthernet0/9 ! interface FastEthernet0/10 ! interface FastEthernet0/11 ! interface FastEthernet0/12 ! interface FastEthernet0/13 ! interface FastEthernet0/14 ! interface FastEthernet0/15 ! interface FastEthernet0/16 ! interface FastEthernet0/17 ! interface FastEthernet0/18 ! interface FastEthernet0/19 ! interface FastEthernet0/20 ! interface FastEthernet0/21 ! interface FastEthernet0/22 ! interface FastEthernet0/23 ! interface FastEthernet0/24 ! interface GigabitEthernet0/1 ! interface GigabitEthernet0/2 ! interface Vlan1 no ip address ! ip http server ip http secure-server ! ! banner motd ^C Authorized Users Only! ^C ! line con 0 password 7 00071A150754 login line vty 0 4 password 7 00071A150754 login line vty 5 15 password 7 00071A150754 login ! end
Switch S2
S2# show run Building configuration... Current configuration : 1519 bytes version 15.0 no service pad service timestamps debug datetime msec service timestamps log datetime msec service password-encryption ! hostname S2 ! boot-start-marker boot-end-marker ! ! enable secret 5 $1$bSBB$YGAFIJdPk0y2TzyBNVEVs. ! no aaa new-model system mtu routing 1500 no ip domain-lookup ! ! spanning-tree mode pvst spanning-tree extend system-id ! vlan internal allocation policy ascending ! ! interface FastEthernet0/1 ! interface FastEthernet0/2 ! interface FastEthernet0/3 ! interface FastEthernet0/4 ! interface FastEthernet0/5 ! interface FastEthernet0/6 ! interface FastEthernet0/7 ! interface FastEthernet0/8 ! interface FastEthernet0/9 ! interface FastEthernet0/10 ! interface FastEthernet0/11 ! interface FastEthernet0/12 ! interface FastEthernet0/13 ! interface FastEthernet0/14 ! interface FastEthernet0/15 ! interface FastEthernet0/16 ! interface FastEthernet0/17 ! interface FastEthernet0/18 ! interface FastEthernet0/19 ! interface FastEthernet0/20 ! interface FastEthernet0/21 ! interface FastEthernet0/22 ! interface FastEthernet0/23 ! interface FastEthernet0/24 ! interface GigabitEthernet0/1 ! interface GigabitEthernet0/2 ! interface Vlan1 no ip address ! ip http server ip http secure-server ! ! banner motd ^C Authorized Users Only! ^C ! line con 0 password 7 00071A150754 logging synchronous login line vty 0 4 password 7 00071A150754 login line vty 5 15 password 7 00071A150754 login ! end

Thanks fir this post to solve my issues.
They’ve updated this with a physical mode version.
some of it still useful but yeah they should update it.