(IoT Previous Level: Introduction to IoT)
Connecting Things ( Version 2) – IoT Fundamentals: Connecting Things End of Course Assessment Final Exam Answers
1. What is an example of cloud computing?
- an architectural style of the World Wide Web
- a network infrastructure that spans a large geographic area
- a service that offers on-demand access to shared resources
- a continuous interaction between people, processes, data, and things
2. What is used to uniquely identify devices connected to the Internet?
- URL
- device name
- IP address
- gateway address
3. What is the formula used to measure the force that drives current?
- I = V x R
- R = I x V
- P = I x R
- V = I x R
4. What are two examples of fixed costs in business finance? (Choose two.)
- utilities
- advertising
- equipment insurance
- materials
- rent
5. What function is performed by an actuator?
- measuring a physical property by detecting information from the physical world
- receiving a signal from a device and performing a set action
- collecting data and then sending instructions for actions to be taken, or sending information for further analysis
- improving a physical environment by measuring changes
6. What are two functions supported by a data link layer protocol? (Choose two.)
- determining the best path to forward packets
- controlling how data is placed and received on the media
- providing an addressing scheme for reaching destination networks
- accepting Layer 3 packets and packaging them into frames
- encoding and decoding messages
7. What is the key difference between an open-loop control system and a closed-loop control system?
- A closed-loop system uses an IP-enabled controller whereas an open-loop system does not.
- A closed-loop system uses a negative feedback mechanism whereas an open-loop system uses a positive feedback system.
- A closed-loop system uses a feedback mechanism whereas an open-loop system does not.
- A closed-loop system uses a controller whereas an open-loop system does not.
8. What is used by a RESTful system to represent resources to external systems?
- domain names
- IP addresses
- Uniform Resource Identifiers
- Ethernet addresses
9. What are three examples of computer programs? (Choose three.)
- operating system
- memory
- device driver
- storage
- firmware
10. In the Linux shell, which character is used between two commands to instruct the shell to combine and execute these two commands in sequence?
- %
- #
- |
- $
11. Which two technologies are considered 4th generation cellular-based technologies that commonly require monthly payments to connect IoT devices? (Choose two.)
- LOWARAN
- WiMAX
- ZigBee
- Bluetooth
- LTE
12. Which security method can be used to secure the management plane within a network device?
- updating the operating system or firmware
- using strong passwords
- encrypting data
- using a firewall
13. What is the purpose of a sequence diagram?
- It represents the IP addressing scheme for devices within a network
- A sequence diagram represents processes or workflows using different shapes, boxes and connecting arrows.
- It is a graphical representation of an electronic circuit that represents electrical components and their connections through the use of standardized symbols.
- It represents the timeline and sequence of messages exchanged between devices needed to carry out the functionality of processes.
- It represents the portion of components as part of a whole.
14. What is Fog computing?
- It is a type of computing where services are hosted where they are used, such as at the network edge or with end devices.
- It is a type of computing that sends controller data to a sensor.
- It is a type of computing that enhances P2P applications.
- It is a type of computing that disperses servers and services globally in distributed data centers
15. What are the three categories of components that make up a network infrastructure? (Choose three.)
- services
- media
- devices
- operating systems
- protocols
- programs
16. Match the cloud computing term with the description.
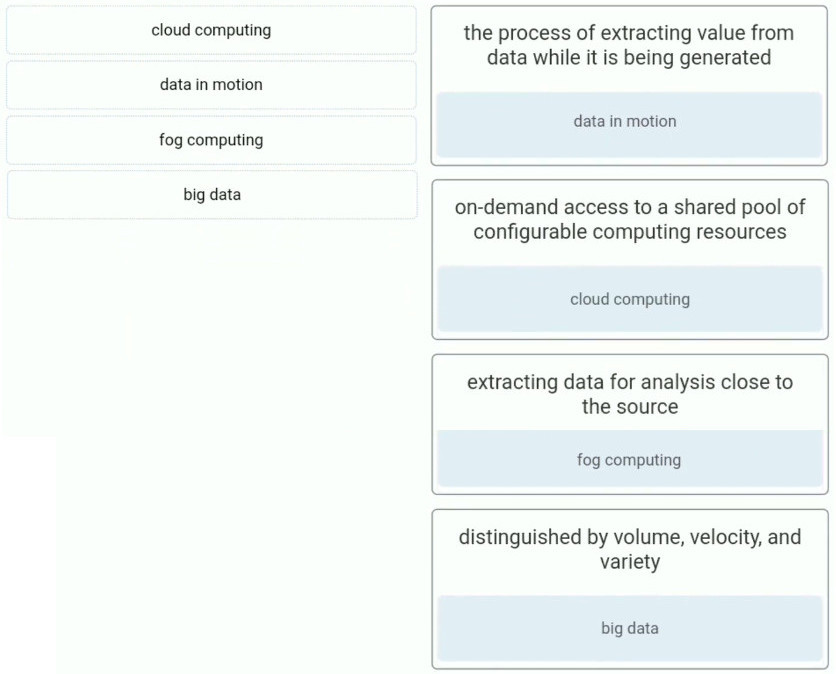
extracting data for analysis close to the source
– fog computing
on-demand access to a shared pool of configurable computing resources
– cloud computing
the process of extracting value from data while it is being generated
– data in motion
distinguished by volume, velocity, and variety
– big data
17. A company plans to add many more devices as part of an IoT solution. What is one of the challenges this company will face because of this rapid growth of digitization?
- integrating the new devices into the existing infrastructure
- increasing the lengths currently defined in network wiring standards
- providing power to the existing devices
- accessing data created by the existing devices
18. What is a recommended security action to take when using off-the-shelf IoT devices?
- Enable UPnP.
- Enable Telnet.
- Disable software updates.
- Disable default user accounts.
19. Match the Blockly logic blocks to the function.
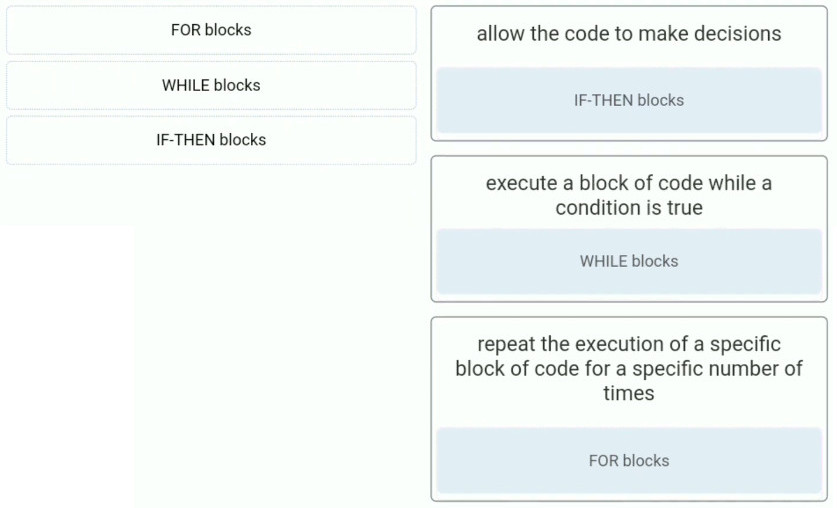
allow the code to make decisions
– IF-THEN blocks
execute a block of code while a condition is true
– WHILE blocks
repeat the execution of a specific block of code for a specific number of times
– FOR blocks
20. Which two blocks in the Business Model Canvas describe business finances? (Choose two.)
- revenue stream
- customer segment
- channels
- cost structure
- key resources
21. Which term is used to describe the rate at which data is generated when referring to big data?
- velocity
- volume
- bandwidth
- variety
22. Which two computer languages are examples of compiled programming languages? (Choose two.)
- Java
- C++
- PHP
- Javascript
- Python
23. Which component in Linux is responsible for interacting directly with the device hardware?
- command interpreter
- command line interface
- shell
- kernel
24. How do cloud services extend IoT functionality?
- move processing and storage functions off the IoT device
- store data in an on-site server
- reduce device network bandwidth requirements
- provide increased security through obscurity
25. Match the description with the apropriate electronics term.
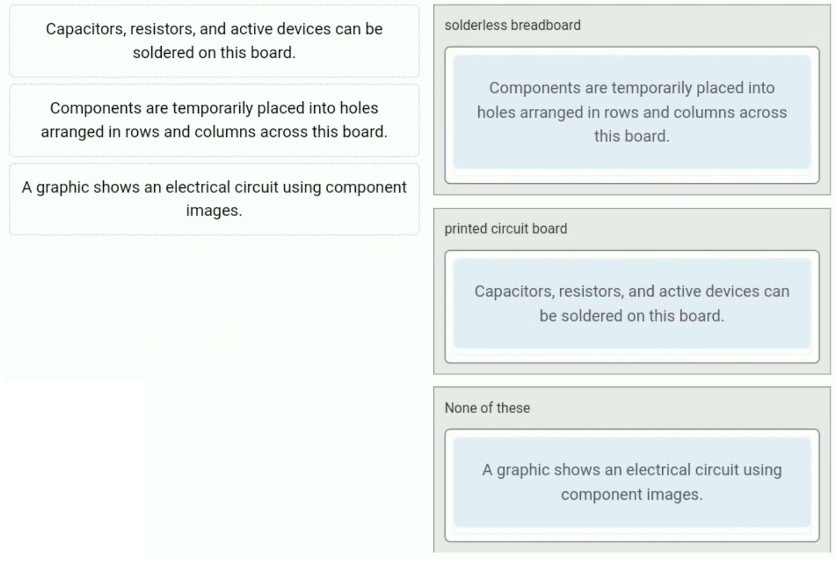
solderless breadboard
– Components are temporarily placed into holes arranged in rows and columns across this board.
printed circuit board
– Capacitors, resistors, and active devices can be soldered on this board.
None of these
– A graphic shows an electrical circuit using component images.
26. What is an example of data in motion?
- hourly weather information being collected in preparation for the next day weather forecast for a specific location
- collecting sales and transaction records in preparation for a monthly sales report from sales consultants as they travel between customers
- recording road traffic volumes and patterns for future highway planning
- medical information being transmitted from an ambulance to emergency department staff as a critically ill patient is being transported to the hospital
27. Which technology type describes a refrigerator that has become part of a botnet that is attacking businesses?
- consumer technology
- industry technology
- operational technology
- information technology
28. A threat actor uses a newly discovered vulnerability to access the home wireless router of a user. The threat actor then changes the password for the wireless network served by the router and causes all wireless devices to lose connectivity. Which factor of smart home security is affected by this attack?
- firmware
- authentication
- WPA2
- encryption
29. Which technology type includes industrial control sytems such as SCADA?
- industry technology
- information technology
- operational technology
- consumer technology
30. What uses a solenoid to actuate electric devices?
- passive circuit
- linear circuit
- relay
- armature
31. What is an electronic circuit?
- a device used to control a large amount of current or voltage with a small electrical signal
- a specialized device used to control current
- a closed conductive path that allows electrons to flow and create an electric current
- a device that detects an event from the physical environment and responds with an optical signal
32. A company plans to develop IoT solutions for both horizontal and vertical markets. What is the major difference in designing solutions for different industries?
- Solutions for a horizontal market industry should be usable for a longer time, whereas solutions for a vertical industry would have a short limited time usage.
- Control software for a horizontal market industry should be coded with C, whereas control software for a vertical market industry should be coded with Python
- Solutions for a horizontal market industry will deal with many general network devices, whereas solutions for a vertical market industry will deal with only specialized equipment
- Solutions for a horizontal market industry should meet general needs across the industry, whereas solutions for a vertical market industry should meet specialized needs for the industry.
The IoT solutions suitable for a horizontal market should meet similar needs for a wide variety of industries that have different products and customers. They tend to be less specialized than a product designed for a certain type of industry with specific needs. On the other hand, the IoT solutions suitable for a vertical market should meet specialized needs for companies with products for a set of customers.
33. What is represented by a diamond symbol in a flowchart?
- a decision
- a start or an end
- an input or output
- a processing step
34. What are three of the six core components in the Cisco IoT system? (Choose three.)
- fog computing
- wearable technologies
- data analytics
- robot guides
- cyber and physical security
- smart bandages
35. How do cloud services extend IoT functionality?
- reduce device network bandwidth requirements
- provide increased security through obscurity
- store data in an on-site server
- move processing and storage functions off the IoT device
36. What are two emerging data protocols used within IoT networks? (Choose two.)
- CoAP
- VPN
- HTTP
- HTTPS
- MQTT
37. What are two challenges that are associated with the rapid growth of IoT? (Choose two.)
- assure interoperability among different device vendors
- adding more switching ports for new things
- improving Internet connections for organizations
- securing new devices that require different levels of security
- developing new programming languages specifically for IoT
38. A company plans to develop IoT solutions for both horizontal and vertical markets. What is the major difference in designing solutions for different industries?
- Solutions for a horizontal market industry should be usable for a longer time, whereas solutions for a vertical industry would have a short limited time usage.
- Control software for a horizontal market industry should be coded with C, whereas control software for a vertical market industry should be coded with Python.
- Solutions for a horizontal market industry will deal with many general network devices, whereas solutions for a vertical market industry will deal with only specialized equipment.
- Solutions for a horizontal market industry should meet general needs across the industry, whereas solutions for a vertical market industry should meet specialized needs for the industry.
39. What are three potential vulnerabilities related to attacks toward the memory of an IoT device? (Choose three.)
- privilege escalation
- sensitive data
- clear-text authentication credential
- removal of storage media
- encryption key
- damage
40. What are three variables used by DREAD? (Choose three.)
- privacy
- damage
- reputation
- exploitability
- denial of service
- affected users
41. What are three items that should be included in the documentation describing the components of the IoT system at each layer? (Choose three.)
- applications
- devices
- protocols
- technologies
- communications network
- the flow of data between components and layers
42. A manufacturing organization is generating a large amount of data via their IoT sensors. At which location should the data be processed if it is to be processed close to the ground where the IoT sensors are connected to the network?
- cloud
- fog
- mist
- device
43. In the context of the importance of security in IoT networks, which model provides a common framework for understanding the placement of various standards and protocols in an IoT system?
- TCPAP
- IoT-A
- OSI
- ETSI

37. What are two challenges that are associated with the rapid growth of IoT? (Choose two.)
“assure interoperability among different device vendors” is wrong. the right answer is “developing new progranning language specifically for IoT“
32. A company plans to develop loT solutions for both horizontal and vertical markets. What is the major difference in designing solutions for different industries?
This has the wrong answer. The correct answer is “Solutions for a horizontal market industry should meet general needs across the industry, whereas solutions for a vertical market industry should meet specialized needs for the industry.”
42. A manufacturing organization is generating a large amount of data via their IoT sensors. At which location should the data be processed if it is to be processed close to the ground where the IoT sensors are connected to the network?
This one is wrong as well. The correct answer is “Fog”.
What are three potential vulnerabilities related to attacks toward the memory of an IoT device? (Choose three.)sensitive data
encryption key
privilege escalation
clear-text authentication credential
damage
removal of storage media
Added all, thanks for your sharing!!
What are three variables used by DREAD? (Choose three.)exploitability
privacy
reputation
damage
affected users
denial of service
What are three items that should be included in the documentation describing the components of the IoT system at each layer? (Choose three.)protocols
the flow of data between components and layers
devices
applications
technologies
communications network
A manufacturing organization is generating a large amount of data via their IoT sensors. At which location should the data be processed if it is to be processed close to the ground where the IoT sensors are connected to the network?cloud
mist
device
fog
In the context of the importance of security in IoT networks, which model provides a common framework for understanding the placement of various standards and protocols in an IoT system?OSI
TCP/IP
IoT-A
ETSI
A threat actor uses a newly discovered vulnerability to access the home wireless router of a user. The threat actor then changes the password for the wireless network served by the router and causes all wireless devices to lose connectivity. Which factor of smart home security is affected by this attack?authentication
firmware
encryption
WPA2
Which technology type includes industrial control sytems such as SCADA?operational technology
consumer technology
industry technology
information technology
Which technology type describes a refrigerator that has become part of a botnet that is attacking businesses?consumer technology
industry technology
operational technology
information technology