1. What are three features of the iOS mobile device operating system? (Choose three.)
- Linux based operating system
- closed source operating system
- developed by Open Handset Alliance
- source code not released to the public
- uses walled garden model for apps
- third-party apps are installed directly using an .apk file
2. For each scenario, select the screen lock method that is described.
- This screen lock requires that a four or six-digit numeric code be entered to unlock the mobile device. The best choice is a passcode lock.
– This is the most common method to lock mobile devices. Passcode options can also include setting a custom numeric code or alphanumeric password. - This screen lock requires the user simply swipe the device screen in a pre-defined direction to unlock the device. The best choice is a swipe lock.
– Also called Slide to unlock on many Android devices. Although convenient, this less secure method should only be used if security is unimportant. - This screen lock requires the user to join four or more dots in a specific pattern to unlock the device. The best choice is a pattern lock.
– Available on many Android devices. The screen unlocks using a pattern you draw with your finger. - This biometric screen lock can unlock a device by scanning the user’s fingerprint. The best choice is a fingerprint lock.
– This iOS and Android feature converts the user’s fingerprint scan into a unique hash. When a user touches the fingerprint sensor, the device re-computes the hash. The device unlocks if the hash values match. - This biometric screen lock can unlock a device by simply looking at it. The best choice is a face lock.
– This iOS and Android feature computes a hash using a picture of the user’s face. Nice try, but that’s not the correct answer.
3. Which two mobile device screen lock security features use biometric data? (Choose two.)
- face lock
- fingerprint lock
- pattern lock
- swipe lock
- passcode lock
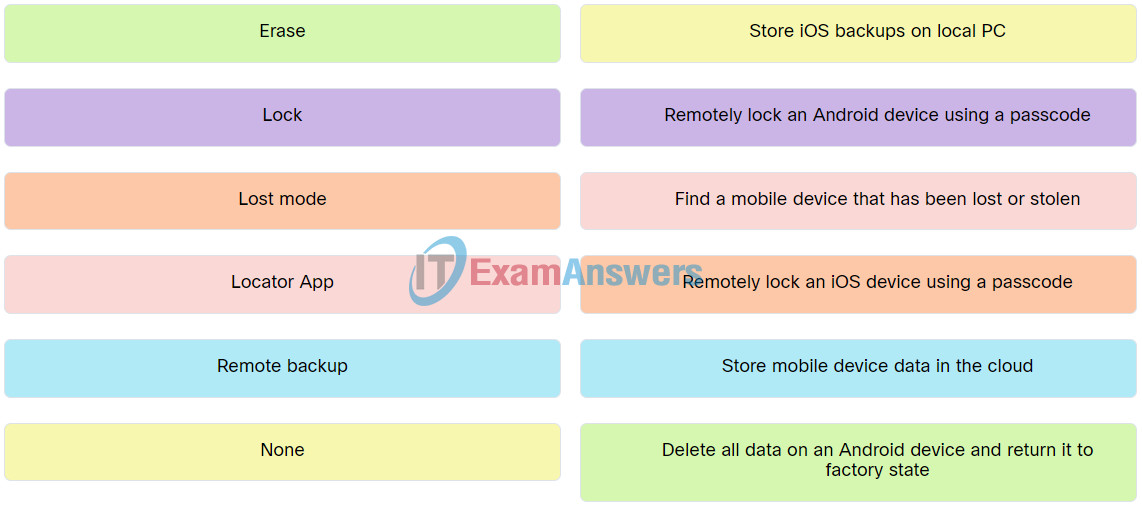
4. Match the action with the mobile device security feature.
5. Which statement is correct regarding mobile device security?
- Running apps in a sandbox helps mitigate damage to mobile devices by malicious software.
- Rooting is a method of removing restrictions on modifying code on an iOS device.
- Jailbreaking exploits vulnerabilities on Android devices.
- Updates and patches for Android devices are released as one package for all devices.
- Jailbreaking exploits vulnerabilities on iOS devices.
6. What are two features of the Linux and macOS operating systems? (Choose two.)
- Linux and macOS are open-source and independently developed operating systems.
- Linux can be customized by the user installing and removing software components.
- macOS includes a Disk Utility to backup and perform image recovery.
- macOS supports the Gnome-terminal terminal emulator.
- Linux and macOS use the Grub boot manager.
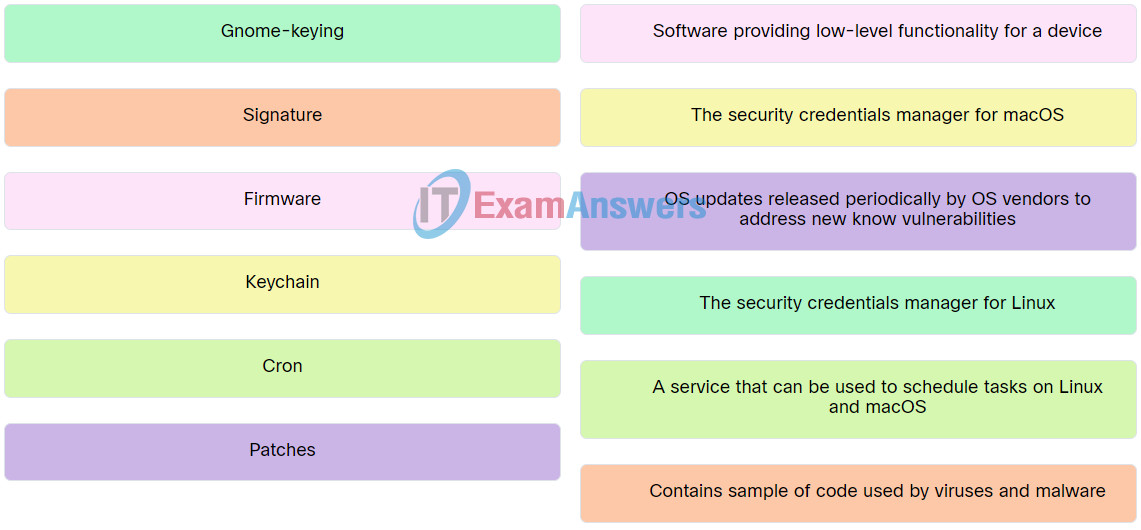
7. Match the Linux or macOS feature to the description.
8. Which four Linux commands would be used to create a new directory under the current directory, copy files to that new directory, make that directory the current directory, and displays the files in that directory? (Choose four.)
- mkdir
- cp
- cd
- ls
- mv
- rm
- pwd
9. Which Linux file permission should be applied to a file that only the file owner can read, change, and execute, but allows all other users to read and execute the file?
- rwxr-xr-x
- rwxtwxrwx
- rw-r–r–
- rw-rw-rw
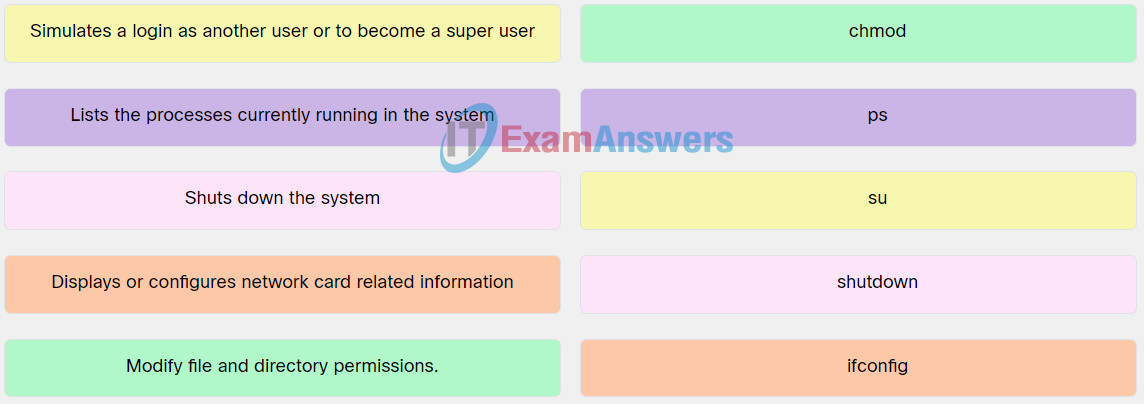
10. Match the file or administrative Linux command to the description.