1. Read each question and indicate if it is open-ended or closed-ended.
- Can you tell me what you were doing when the problem first occurred? – Open-Ended
- Is your computer running Windows 10? – Closed-Ended
- How long have you had this laptop? – Closed-Ended
- What have you already tried to do to fix this problem? – Open-Ended
2. Match the type of document to the respective example.
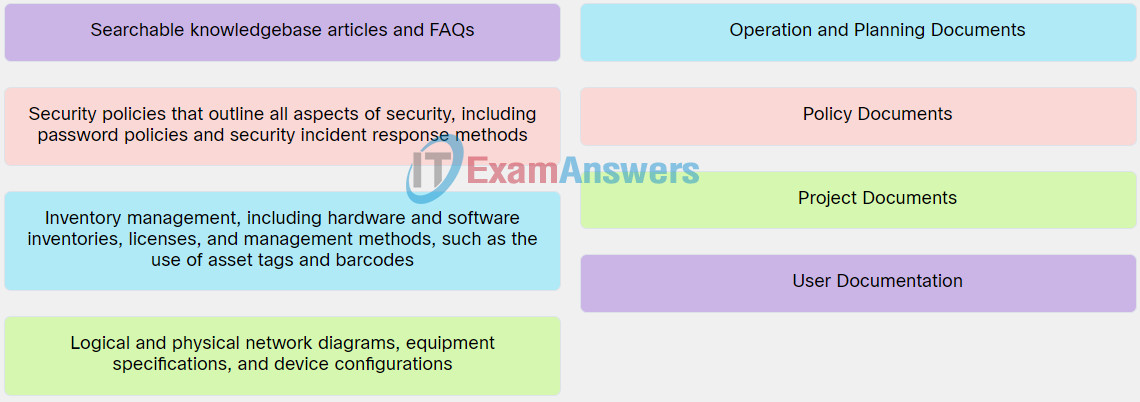
Explanation: Place the options in the following order:
| Security policies that outline all aspects of security, including password policies and security incident response methods. |
Policy Documents |
| Inventory management, including hardware and software inventories, licenses, and management methods, such as the use of asset tags and barcodes. |
Operation and Planning Documents |
| Logical and physical network diagrams, equipment specifications, and device configurations. |
Project Documents |
| Searchable knowledgebase articles and FAQs. |
User Documentation |
3. Match the disaster recovery phase to the corresponding action.
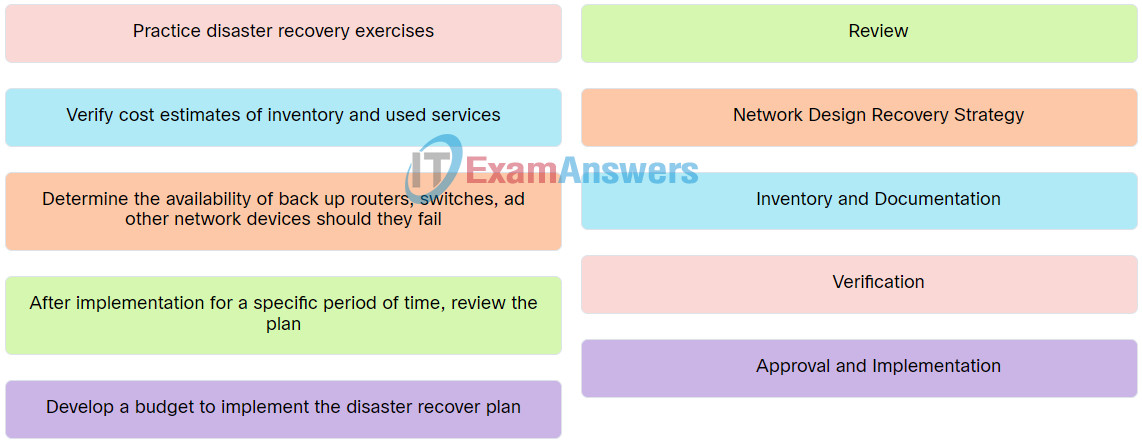
Explanation: Place the options in the following order:
| Practice disaster recovery exercises. |
Verification |
| Verify cost estimates of inventory and used services. |
Inventory and Documentation |
| After implementation for a specific period of time, review the plan. |
Review |
| Develop a budget to implement the disaster recover plan. |
Approval and Implementation |
| Determine the availability of back up routers, switches, ad other network devices should they fail. |
Network Design Recovery Strategy |
4. Match the term to the respective description.
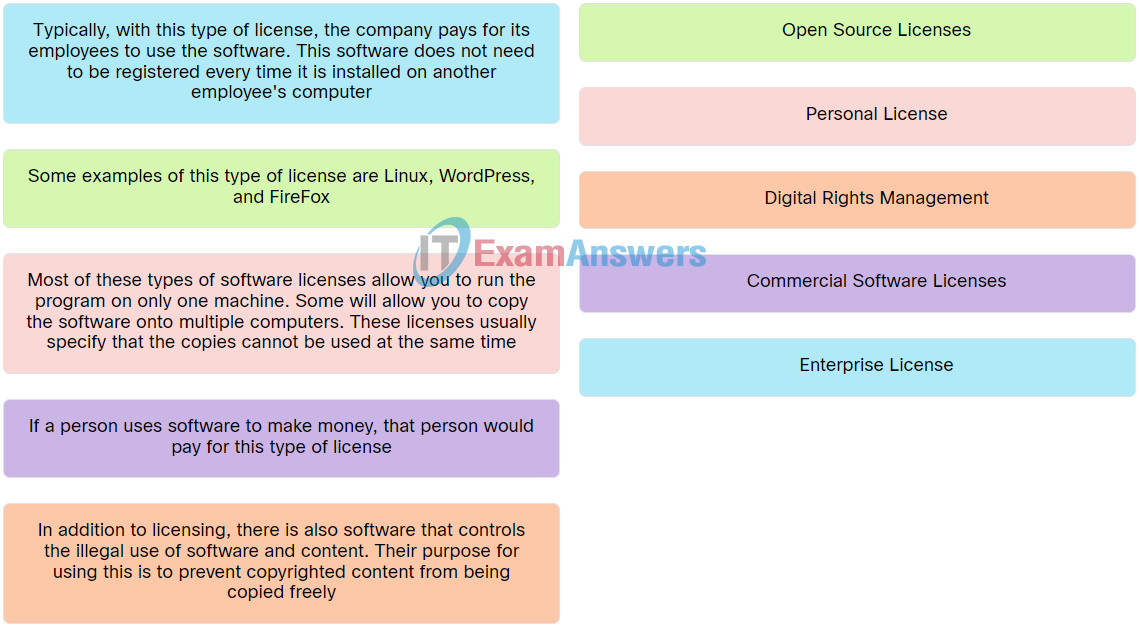
Explanation: Place the options in the following order:
| Most of these types of software licenses allow you to run the program on only one machine. Some will allow you to copy the software onto multiple computers. These licenses usually specify that the copies cannot be used at the same time. |
Personal License |
| Typically, with this type of license, the company pays for its employees to use the software. This software does not need to be registered every time it is installed on another employee’s computer. |
Enterprise License |
| Some examples of this type of license are Linux, WordPress, and FireFox. |
Open Source Licenses |
| If a person uses software to make money, that person would pay for this type of license. |
Commercial Software Licenses |
| In addition to licensing, there is also software that controls the illegal use of software and content. Their purpose for using this is to prevent copyrighted content from being copied freely. |
Digital Rights Management |
5. Match the term to the respective description.
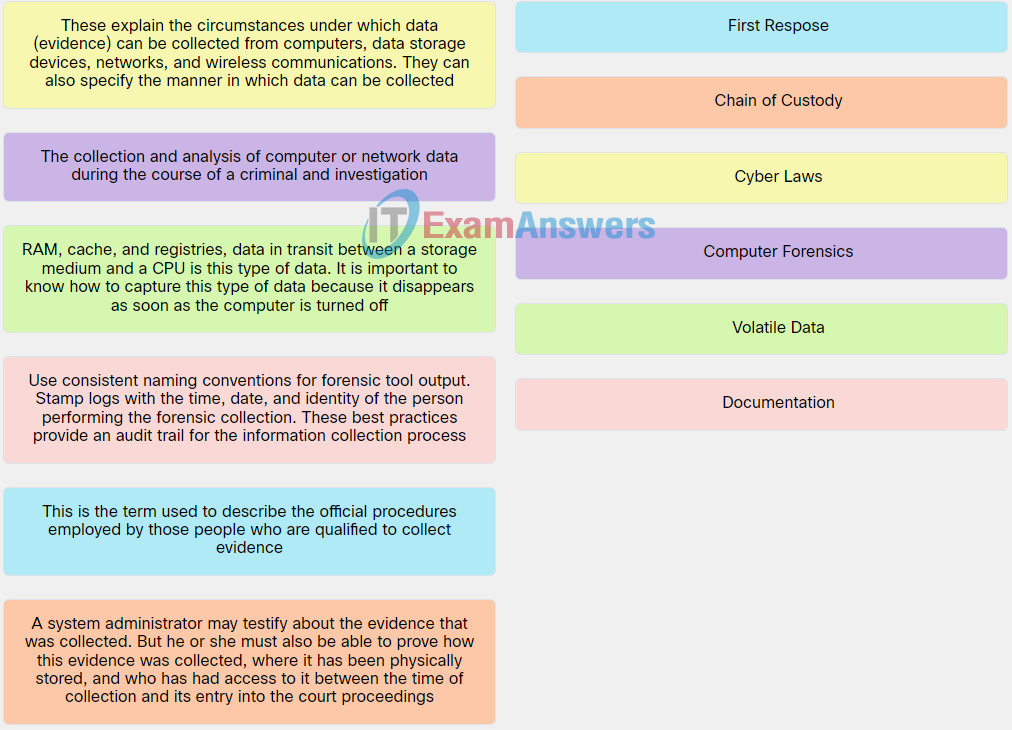
Explanation: Place the options in the following order:
| Use consistent naming conventions for forensic tool output. Stamp logs with the time, date, and identity of the person performing the forensic collection. These best practices provide an audit trail for the information collection process. |
Documentation |
| This is the term used to describe the official procedures employed by those people who are qualified to collect evidence. |
First Respose |
| RAM, cache, and registries, data in transit between a storage medium and a CPU is this type of data. It is important to know how to capture this type of data because it disappears as soon as the computer is turned off. |
Volatile Data |
| The collection and analysis of computer or network data during the course of a criminal and investigation. |
Computer Forensics |
| A system administrator may testify about the evidence that was collected. But he or she must also be able to prove how this evidence was collected, where it has been physically stored, and who has had access to it between the time of collection and its entry into the court proceedings. |
Chain of Custody |
| These explain the circumstances under which data (evidence) can be collected from computers, data storage devices, networks, and wireless communications. They can also specify the manner in which data can be collected. |
Cyber Laws |




