How to find: Press “Ctrl + F” in the browser and fill in whatever wording is in the question to find that question/answer. If the question is not here, find it in Questions Bank.
NOTE: If you have the new question on this test, please comment Question and Multiple-Choice list in form below this article. We will update answers for you in the shortest time. Thank you! We truly value your contribution to the website.
Checkpoint Exam: Threat Actors and Defenders Group Exam Answers
Modules 13 – 17 of the CyberOps Associate 1.0
1. Which organization is an international nonprofit organization that offers the CISSP certification?
Explanation: (ISC)2 is an international nonprofit organization that offers the CISSP certification.
2. What is a benefit to an organization of using SOAR as part of the SIEM system?
- SOAR was designed to address critical security events and high-end investigation.
- SOAR would benefit smaller organizations because it requires no cybersecurity analyst involvement once installed.
- SOAR automates incident investigation and responds to workflows based on playbooks.
- SOAR automation guarantees an uptime factor of “5 nines”.
Explanation: SIEM systems are used for collecting and filtering data, detecting and classifying threats, and analyzing and investigating threats. SOAR technology does the same as SIEMs but it also includes automation. SOAR integrates threat intelligence and automates incident investigation. SOAR also responds to events using response workflows based on previously developed playbooks.
3. Which personnel in a SOC are assigned the task of hunting for potential threats and implementing threat detection tools?
- Tier 3 SME
- Tier 2 Incident Reporter
- Tier 1 Analyst
- SOC Manager
Explanation: In a SOC, Tier 3 SMEs have expert-level skills in network, endpoint, threat intelligence, and malware reverse engineering (RE). They are deeply involved in hunting for potential security threats and implementing threat detection tools.
4. Which three technologies should be included in a SOC security information and event management system? (Choose three.)
- security monitoring
- threat intelligence
- proxy service
- firewall appliance
- intrusion prevention
- log management
Explanation: Technologies in a SOC should include the following:
Event collection, correlation, and analysis
Security monitoring
Security control
Log management
Vulnerability assessment
Vulnerability tracking
Threat intelligence
Proxy server, VPN, and IPS are security devices deployed in the network infrastructure.
5. The term cyber operations analyst refers to which group of personnel in a SOC?
- Tier 1 personnel
- Tier 3 personnel
- Tier 2 personnel
- SOC managers
Explanation: In a typical SOC, the Tier 1 personnel are called alert analysts, also known as cyberoperations analysts.
6. How does a security information and event management system (SIEM) in a SOC help the personnel fight against security threats?
- by analyzing logging data in real time
- by combining data from multiple technologies
- by integrating all security devices and appliances in an organization
- by dynamically implementing firewall rules
Explanation: A security information and event management system (SIEM) combines data from multiple sources to help SOC personnel collect and filter data, detect and classify threats, analyze and investigate threats, and manage resources to implement preventive measures.
7. An SOC is searching for a professional to fill a job opening. The employee must have expert-level skills in networking, endpoint, threat intelligence, and malware reverse engineering in order to search for cyber threats hidden within the network. Which job within an SOC requires a professional with those skills?
- Incident Responder
- Alert Analyst
- SOC Manager
- Threat Hunter
Explanation: Tier 3 professionals called Threat Hunters must have expert-level skills in networking, endpoint, threat intelligence, and malware reverse engineering. They are experts at tracing the processes of malware to determine the impact of the malware and how it can be removed.
8. Which three are major categories of elements in a security operations center? (Choose three.)
- technologies
- Internet connection
- processes
- data center
- people
- database engine
Explanation: The three major categories of elements of a security operations center are people, processes, and technologies. A database engine, a data center, and an Internet connection are components in the technologies category.
9. Which KPI metric does SOAR use to measure the time required to stop the spread of malware in the network?
- MITR
- Time to Control
- MITC
- MTTD
Explanation:
The common key performance indicator (KPI) metrics compiled by SOC managers are as follows:
• Dwell Time: the length of time that threat actors have access to a network before they are detected and the access of the threat actors stopped
• Mean Time to Detect (MTTD): the average time that it takes for the SOC personnel to identify that valid security incidents have occurred in the network
• Mean Time to Respond (MTTR): the average time that it takes to stop and remediate a security incident
• Mean Time to contain (MTTC): the time required to stop the incident from causing further damage to systems or data
• Time to Control the time required to stop the spread of malware in the network
10. What job would require verification that an alert represents a true security incident or a false positive?
- Alert Analyst
- Threat Hunter
- SOC Manager
- Incident Reporter
Explanation: A Cybersecurity Analyst monitors security alert queues and uses a ticketing system to assign alerts to a queue for an analyst to investigate. Because the software that generates alerts can trigger false alarms, one job of the Cybersecurity Analyst would be to verify that an alert represents a true security incident.
11. When a user turns on the PC on Wednesday, the PC displays a message indicating that all of the user files have been locked. In order to get the files unencrypted, the user is supposed to send an email and include a specific ID in the email title. The message also includes ways to buy and submit bitcoins as payment for the file decryption. After inspecting the message, the technician suspects a security breach occurred. What type of malware could be responsible?
- Trojan
- spyware
- adware
- ransomware
Explanation: Ransomware requires payment for access to the computer or files. Bitcoin is a type of digital currency that does not go through a particular bank.
12. An employee connects wirelessly to the company network using a cell phone. The employee then configures the cell phone to act as a wireless access point that will allow new employees to connect to the company network. Which type of security threat best describes this situation?
- rogue access point
- cracking
- spoofing
- denial of service
Explanation: Configuring the cell phone to act as a wireless access point means that the cell phone is now a rogue access point. The employee unknowingly breached the security of the company network by allowing a user to access the network without connecting through the company access point. Cracking is the process of obtaining passwords from data stored or transmitted on a network. Denial of service attacks refer to sending large amounts of data to a networked device, such as a server, to prevent legitimate access to the server. Spoofing refers to access gained to a network or data by an attacker appearing to be a legitimate network device or user.
13. What are two examples of personally identifiable information (PII)? (Choose two.)
- first name
- IP address
- language preference
- street address
- credit card number
Explanation: Personally identifiable information (PII) is any data that could potentially identify and track a specific individual. A credit card number and street address are the best examples of PII.
14. What is the dark web?
- It is a website that reports the most recent activities of cybercriminals all over the world.
- It is a website that sells stolen credit cards.
- It is part of the internet where a person can obtain personally identifiable information from anyone for free
- It is part of the internet that can only be accessed with special software.
Explanation: One of the more lucrative goals of cybercriminals is obtaining lists of personally identifiable information that can then be sold on the dark web. The dark web can only be accessed with special software and is used by cybercriminals to shield their activities. Stolen PII can be used to create fake accounts, such as credit cards and short-term loans.
15. A company has just had a cybersecurity incident. The threat actor appeared to have a goal of network disruption and appeared to use a common security hack tool that overwhelmed a particular server with a large amount of traffic. This traffic rendered the server inoperable. How would a certified cybersecurity analyst classify this type of threat actor?
- terrorist
- hacktivist
- state-sponsored
- amateur
Explanation:Amateurs or script kiddies use common, existing tools found on the internet to launch attacks. Hacktivists disrupt services in protest against organizations or governments for a particular political or social idea. State-sponsored threat actors use cyberspace for industrial espionage or interfering with another country in some way. Terrorist groups attack for a specific cause.
16. A user calls the help desk complaining that the password to access the wireless network has changed without warning. The user is allowed to change the password, but an hour later, the same thing occurs. What might be happening in this situation?
- rogue access point
- password policy
- weak password
- user error
- user laptop
Explanation:Man-in-the-middle attacks are a threat that results in lost credentials and data. These type of attacks can occur for different reasons including traffic sniffing.
17. Which regulatory law regulates the identification, storage, and transmission of patient personal healthcare information?
Explanation: The Health Insurance Portability and Accountability Act (HIPAA) requires that all patient personally identifiable healthcare information be stored, maintained, and transmitted in ways that ensure patient privacy and confidentiality.
18. A worker in the records department of a hospital accidentally sends a medical record of a patient to a printer in another department. When the worker arrives at the printer, the patient record printout is missing. What breach of confidentiality does this situation describe?
Explanation: Protected Health Information (PHI) includes patient name, addresses, visiting dates and more. The Health Insurance Portability and Accountability Act (HIPAA) regulates and provides severe penalties for breaches of PHI. EMRs (Electronic Medical Records) are documents created and maintained by the medical community that contain PHI. Personally identifiable information (PII) is any information that can be used to positively identify an individual, such as name and social security number. Personal Security Information (PSI) is related to information about an individual such as passwords, access keys, and account details.
19. What type of cyberwarfare weapon was Stuxnet?
- botnet
- virus
- worm
- ransomware
Explanation:The Stuxnet worm was an excellent example of a sophisticated cyberwarfare weapon. In 2010, it was used to attack programmable logic controllers that operated uranium enrichment centrifuges in Iran.
20. Which example illustrates how malware might be concealed?

- A hacker uses techniques to improve the ranking of a website so that users are redirected to a malicious site.
- An attack is launched against the public website of an online retailer with the objective of blocking its response to visitors.
- A botnet of zombies carry personal information back to the hacker.
- An email is sent to the employees of an organization with an attachment that looks like an antivirus update, but the attachment actually consists of spyware.
Explanation: An email attachment that appears as valid software but actually contains spyware shows how malware might be concealed. An attack to block access to a website is a DoS attack. A hacker uses search engine optimization (SEO) poisoning to improve the ranking of a website so that users are directed to a malicious site that hosts malware or uses social engineering methods to obtain information. A botnet of zombie computers is used to launch a DDoS attack.
- websites to check account fees
- websites to check product details
- websites to check stock prices
- websites to make purchases
Explanation: Many free and open wireless hotspots operate with no authentication or weak authentication mechanisms. Attackers could easily capture the network traffic in and out of such a hotspot and steal user information. Therefore, users who use free and open wireless hotspots to connect to websites should avoid giving any personal information to the websites.
22. In a smart home, an owner has connected many home devices to the Internet, such as the refrigerator and the coffee maker. The owner is concerned that these devices will make the wireless network vulnerable to attacks. What action could be taken to address this issue?
- Configure mixed mode wireless operation.
- Install the latest firmware versions for the devices.
- Assign static IP addresses to the wireless devices.
- Disable the SSID broadcast.
Explanation: The Internet of Things (IoT) is facilitating the connection of different kinds of devices to the internet, like home devices such as coffee makers and refrigerators, and also wearable devices. In order to make these devices secure and not vulnerable to attacks, they have to be updated with the latest firmware.
23. Match the SOC metric to the description. (Not all options are used.)
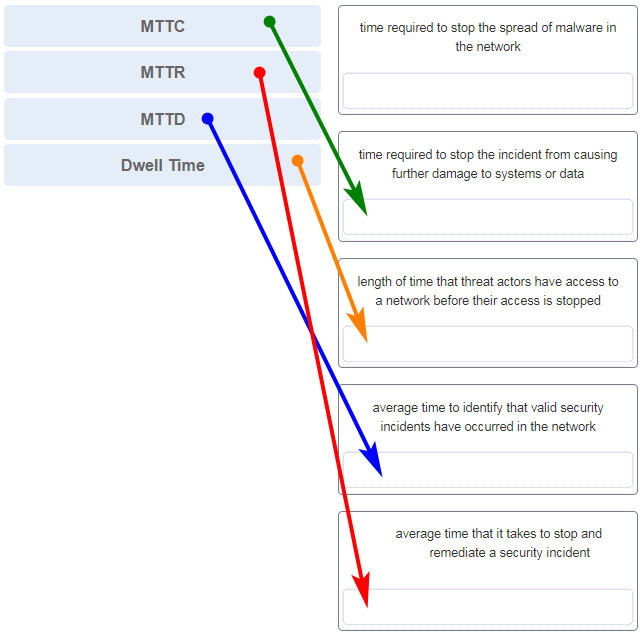
Explanation: SOCs use many metrics as performance indicators of how long it takes personnel to locate, stop, and remediate security incidents.
- Dwell Time
- Mean Time to Detect (MTTD)
- Mean Time to Respond (MTTR)
- Mean Time to Contain (MTTC)
- Time to Control
24. A group of users on the same network are all complaining about their computers running slowly. After investigating, the technician determines that these computers are part of a zombie network. Which type of malware is used to control these computers?
- botnet
- spyware
- virus
- rootkit
Explanation: A botnet is a network of infected computers called a zombie network. The computers are controlled by a hacker and are used to attack other computers or to steal data.
25. Which statement describes cyberwarfare?
- It is Internet-based conflict that involves the penetration of information systems of other nations.
- It is simulation software for Air Force pilots that allows them to practice under a simulated war scenario.
- Cyberwarfare is an attack carried out by a group of script kiddies.
- It is a series of personal protective equipment developed for soldiers involved in nuclear war
Explanation: Cyberwarfare is Internet-based conflict that involves the penetration of the networks and computer systems of other nations. Organized hackers are typically involved in such an attack.
26. Why do IoT devices pose a greater risk than other computing devices on a network?
- Most IoT devices do not receive frequent firmware updates.
- Most IoT devices do not require an Internet connection and are unable to receive new updates.
- IoT devices cannot function on an isolated network with only an Internet connection.
- IoT devices require unencrypted wireless connections.
Explanation: IoT devices commonly operate using their original firmware and do not receive updates as frequently as laptops, desktops, and mobile platforms.
27. Which cyber attack involves a coordinated attack from a botnet of zombie computers?
- DDoS
- MITM
- address spoofing
- ICMP redirect
Explanation: DDoS is a distributed denial-of-services attack. A DDoS attack is launched from multiple coordinated sources. The sources of the attack are zombie hosts that the cybercriminal has built into a botnet. When ready, the cybercriminal instructs the botnet of zombies to attack the chosen target.
28. What is the main purpose of cyberwarfare?
- to protect cloud-based data centers
- to develop advanced network devices
- to gain advantage over adversaries
- to simulate possible war scenarios among nations
Explanation: Cyberwarfare is Internet-based conflict that involves the penetration of the networks and computer systems of other nations. The main purpose of cyberwarfare is to gain advantage over adversaries, whether they are nations or competitors.



Thank you realy, i m stupid, so this helped me, really thank yu
Great job
In a smart home, an owner has connected many home devices to the Internet, such as the refrigerator and the coffee maker. The owner is concerned that these devices will make the wireless network vulnerable to attacks. What action could be taken to address this issue?
install the latest firmware version for the devices
Great job. I am very thankful for the help offered.
Thanks for the answer.. this is great job
3 New
11 A group of users on the same network are all complaining about their computers running slowly. After investigating, the technician determines that these computers are part of a zombie network. Which type of malware is used to control these computers?
16 An employee connects wirelessly to the company network using a cell phone. The employee then configures the cell phone to act as a wireless access point that will allow new employees to connect to the company network. Which type of security threat best describes this situation?
20 Which statement describes cyberwarfare?
It is a series of personal protective equipment developed for soldiers involved in nuclear war
many thank!!!!
3. Which personnel in a SOC are assigned the task of hunting for potential threats and implementing threat detection tools?
The correct answer is Tier 3 SME