CyberOps Associate (Version 1.0) – Modules 3 – 4: Operating System Overview Group Exam
1. Why would a network administrator choose Linux as an operating system in the Security Operations Center (SOC)?
- It is easier to use than other operating systems.
- More network applications are created for this environment.
- It is more secure than other server operating systems.
- The administrator has more control over the operating system.
2. Which two methods can be used to harden a computing device? (Choose two.)
- Allow default services to remain enabled.
- Allow USB auto-detection.
- Enforce the password history mechanism.
- Update patches on a strict annual basis irrespective of release date.
- Ensure physical security.
3. Which Linux command can be used to display the name of the current working directory?
- sudo
- ps
- pwd
- chmod
4. Consider the result of the ls -l command in the Linux output below. What are the file permissions assigned to the sales user for the analyst.txt file?
ls –l analyst.txt -rwxrw-r-- sales staff 1028 May 28 15:50 analyst.txt
- write only
- read, write
- read only
- read, write, execute
5. A Linux system boots into the GUI by default, so which application can a network administrator use in order to access the CLI environment?
- system viewer
- file viewer
- package management tool
- terminal emulator
6. What is the well-known port address number used by DNS to serve requests?
- 25
- 53
- 110
- 60
7. Which user can override file permissions on a Linux computer?
- any user that has ‘group’ permission to the file
- only the creator of the file
- any user that has ‘other’ permission to the file
- root user
8. Match the commonly used ports on a Linux server with the corresponding service.
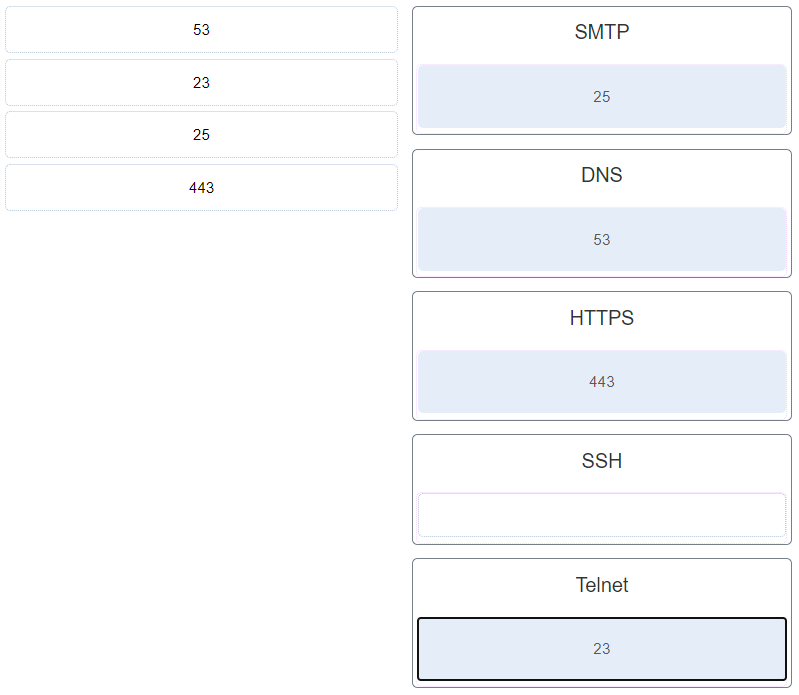
- SMTP: 25
- DNS: 53
- HTTPS: 443
- SSH: 22
- TELNET: 23
9. Match typical Linux log files to the function.
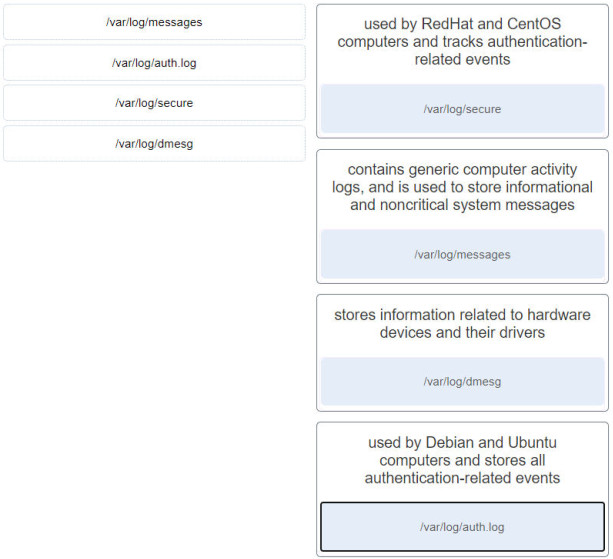
- used by RedHat and CentOS computers and tracks authentication-related events: /var/log/secure
- contains generic computer activity logs, and is used to store informational and noncritical system messages: /var/log/messages
- stores information related to hardware devices and their drivers: /var/log/dmesg
- used by Debian and Ubuntu computers and stores all authentication-related events: /var/log/auth.log
10. Which type of tool allows administrators to observe and understand every detail of a network transaction?
- log manager
- malware analysis tool
- ticketing system
- packet capture software
11. Why is Kali Linux a popular choice in testing the network security of an organization?
- It is a network scanning tool that prioritizes security risks.
- It is an open source Linux security distribution containing many penetration tools.
- It can be used to test weaknesses by using only malicious software.
- It can be used to intercept and log network traffic.
12. Match the octal value to the file permission description in Linux. (Not all options are used.)
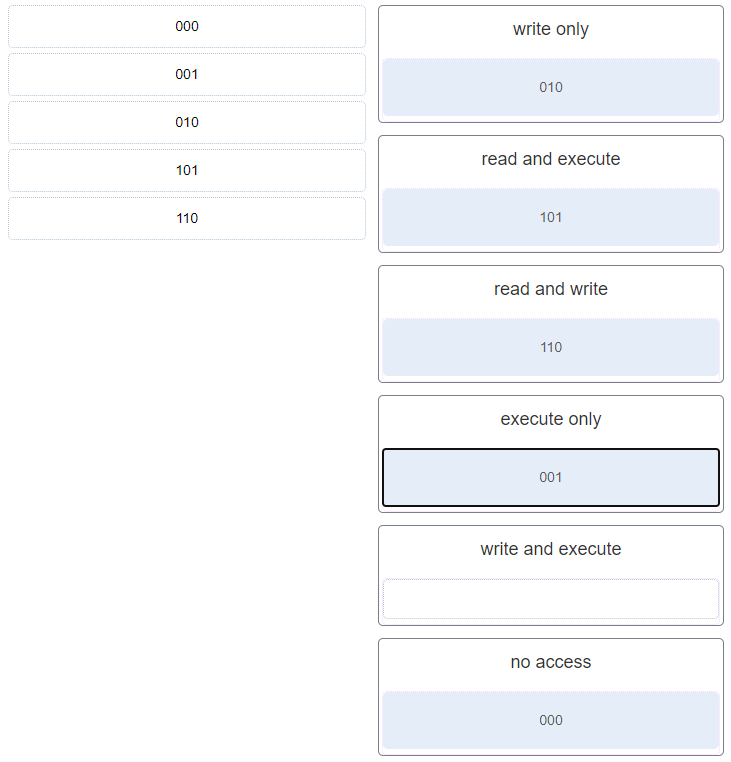
- write only ~~> 010
- read and execute ~~> 101
- read and write ~~> 110
- execute only ~~> 001
- write and execute ~~> NOT SCORED
- no access ~~> 000
13. Match the Linux command to the function. (Not all options are used.)
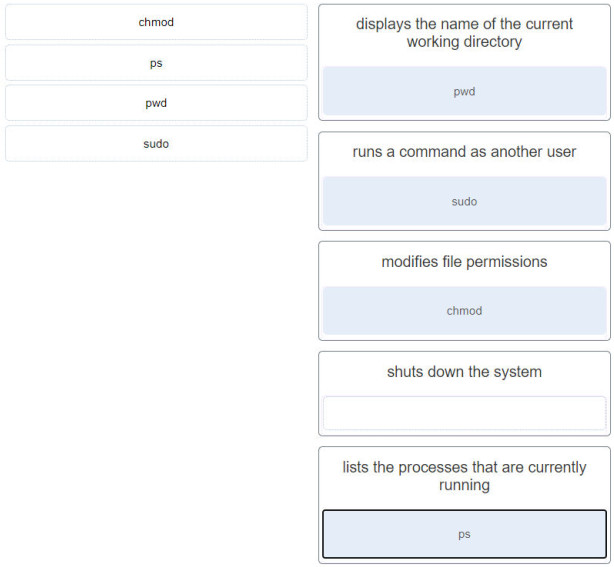
- Displays the name of the current working directory: pwd
- runs a command as another user: sudo
- modifies file permissions: chmod
- shuts down the system: Empty
- lists the processes that are currently running: ps
14. What are two advantages of the NTFS file system compared with FAT32? (Choose two.)
- NTFS is easier to configure.
- NTFS supports larger files.
- NTFS allows faster formatting of drives.
- NTFS allows the automatic detection of bad sectors.
- NTFS allows faster access to external peripherals such as a USB drive.
- NTFS provides more security features.
15. A PC user issues the netstat command without any options. What is displayed as the result of this command?
- a historical list of successful pings that have been sent
- a list of all established active TCP connections
- a network connection and usage report
- a local routing table
16. Which two commands could be used to check if DNS name resolution is working properly on a Windows PC? (Choose two.)
- nslookup cisco.com
- net cisco.com
- ipconfig /flushdns
- nbtstat cisco.com
- ping cisco.com
17. What is the purpose of using the net accounts command in Windows?
- to display information about shared network resources
- to show a list of computers and network devices on the network
- to start a network service
- to review the settings of password and logon requirements for users
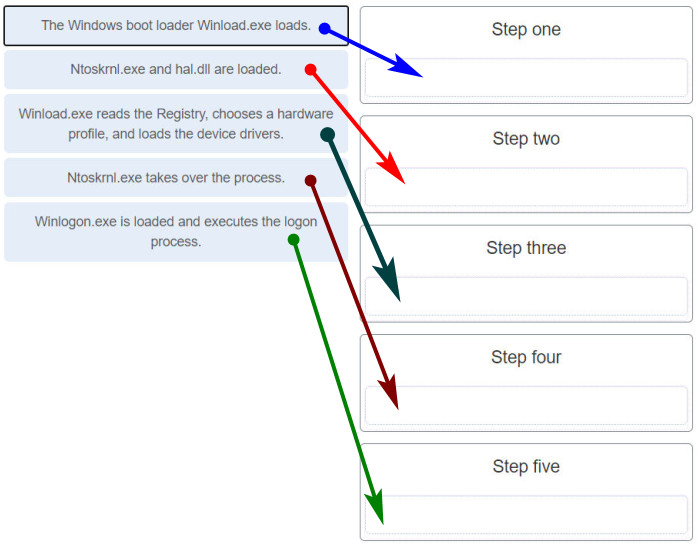
18. Match the Windows 10 boot sequence after the boot manager (bootmgr.exe) loads.
19. A technician has installed a third party utility that is used to manage a Windows 7 computer. However, the utility does not automatically start whenever the computer is started. What can the technician do to resolve this problem?
- Set the application registry key value to one.
- Use the Add or Remove Programs utility to set program access and defaults.
- Change the startup type for the utility to Automatic in Services .
- Uninstall the program and then choose Add New Programs in the Add or Remove Programs utility to install the application.
20. Which statement describes the function of the Server Message Block (SMB) protocol?
- It is used to stream media contents.
- It is used to manage remote PCs.
- It is used to compress files stored on a disk.
- It is used to share network resources.
21. A user creates a file with .ps1 extension in Windows. What type of file is it?
- PowerShell function
- PowerShell cmdlet
- PowerShell documentation
- PowerShell script
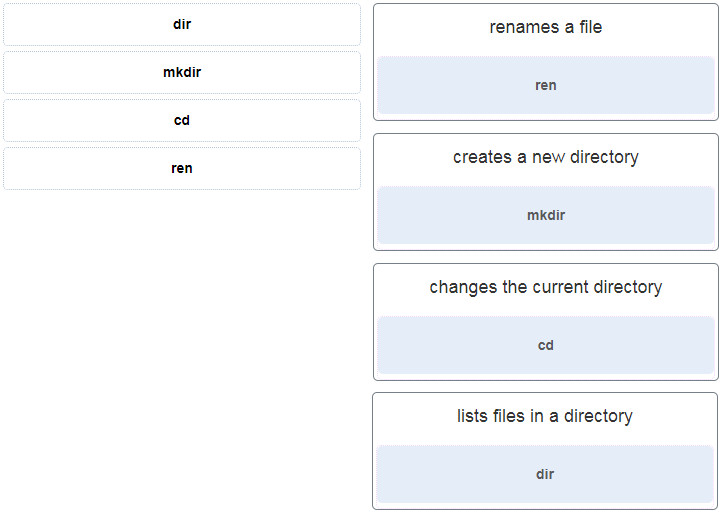
22. Match the Windows command to the description.
Modules 3 – 4: Operating System Overview Group Exam
- renames a file ~~> ren
- creates a new directory ~~> mkdir
- changes the current directory ~~> cd
- lists files in a directory ~~> dir
23. A user logs in to Windows with a regular user account and attempts to use an application that requires administrative privileges. What can the user do to successfully use the application?
- Right-click the application and choose Run as Priviledge .
- Right-click the application and choose Run as Superuser .
- Right-click the application and choose Run as Administrator .
- Right-click the application and choose Run as root .
24. An IT technician wants to create a rule on two Windows 10 computers to prevent an installed application from accessing the public Internet. Which tool would the technician use to accomplish this task?
- Local Security Policy
- Computer Management
- Windows Defender Firewall with Advanced Security
- DMZ
25. What technology was created to replace the BIOS program on modern personal computer motherboards?
- UEFI
- MBR
- CMOS
- RAM
26. Match the Linux system component with the description. (Not all options are used.)
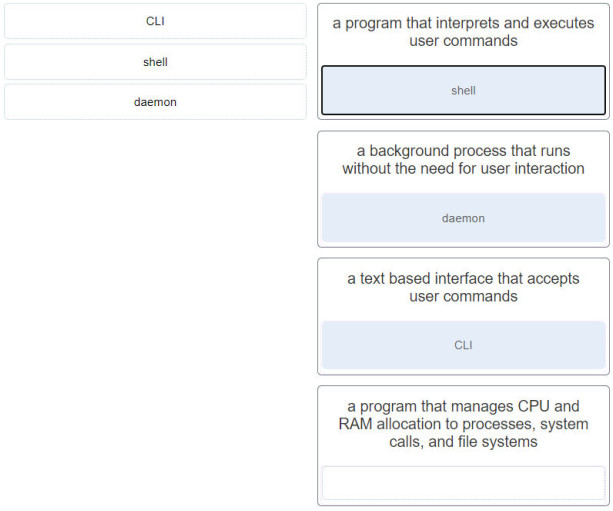
- CLI : a text based interface that accepts user commands
- shell : a program that interprets and executes user commands
- daemon : a background process that runs without the need for user interaction
- (Empty) : a program that manages CPU and RAM allocation to processes, system calls, and file systems
27. What is the outcome when a Linux administrator enters the man man command?
- The man man command configures the network interface with a manual address
- The man man command opens the most recent log file
- The man man command provides a list of commands available at the current prompt
- The
man mancommand provides documentation about the man command
28. Match the description to the Linux term. (Not all options are used.)
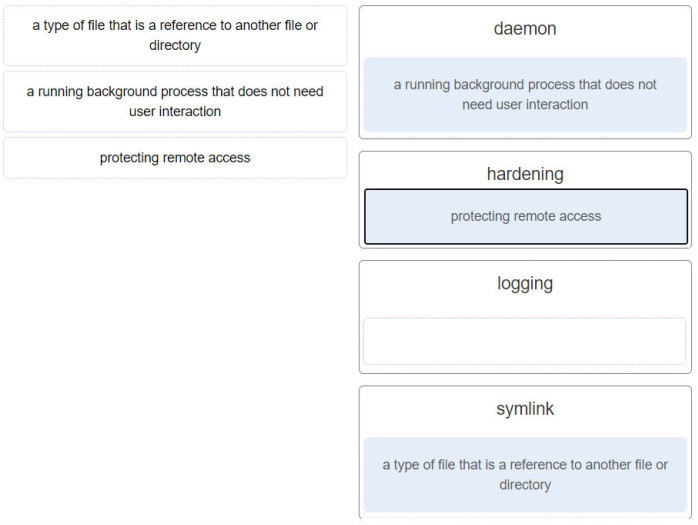
- a type of file that is a reference to another file or directory ~~> symlink
- a running background process that does not need user interaction ~~> daemon
- protecting remote access ~~> hardening
- (Empty) ~~>logging
29. What are two benefits of using an ext4 partition instead of ext3? (Choose two.)
- an increase in the number of supported devices
- improved performance
- compatibility with NTFS
- increase in the size of supported files
- decreased load time
- compatibility with CDFS
30. Consider the result of the ls -l command in the Linux output below. What are the file permissions assigned to the sales user for the analyst.txt file?
ls -l analyst.txt -rwxrw-r-- sales staff 1028 May 28 15:50 analyst.txt
- read, write, execute
- write only
- read only
- read, write
31. What is the purpose of entering the netsh command on a Windows PC?
- to configure networking parameters for the PC
- to change the computer name for the PC
- to create user accounts
- to test the hardware devices on the PC
32. Which type of Windows PowerShell command performs an action and returns an output or object to the next command that will be executed?
- cmdlets
- functions
- routines
- scripts
33. A user creates a file with
.ps1 extension in Windows. What type of file is it?
- PowerShell documentation
- PowerShell cmdlet
- PowerShell script
- PowerShell function
34. Match the Windows system tool with the description. (Not all options are used.)
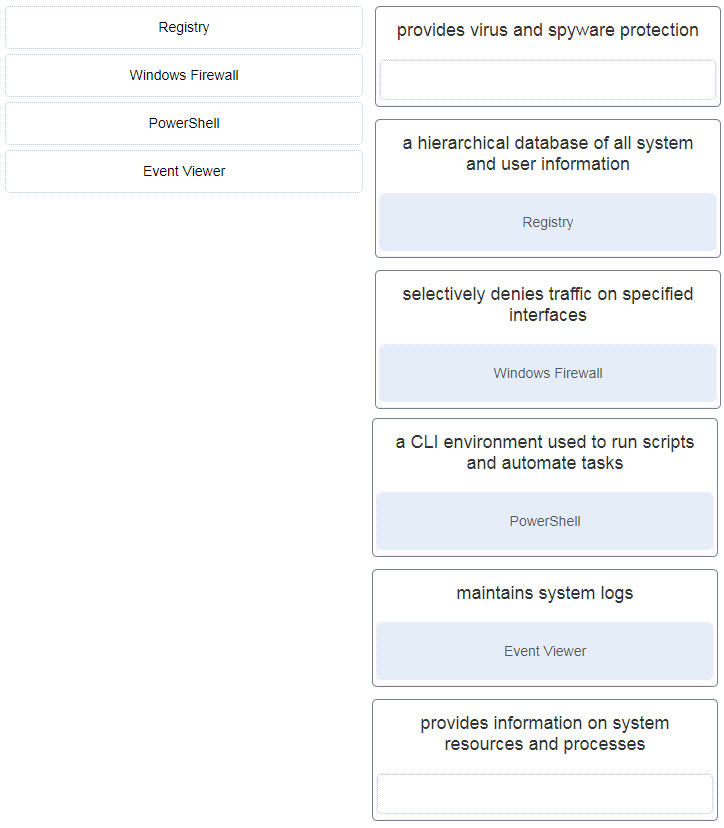
- Registry : a hierarchical database of all system and user information
- Windows Firewall : selectively denies traffic on specified interfaces
- PowerShell : a CLI environment used to run scripts and automate tasks
- Event Viewer : maintains system logs
- (Empty) : provides information on system resources and processes
- (Empty) : provides virus and spyware protection
35. In the Linux shell, which character is used between two commands to instruct the shell to combine and execute these two commands in sequence?
- $
- #
- %
- |
36. Why is Linux considered to be better protected against malware than other operating systems?
- customizable penetration and protection tools
- fewer deployments
- file system structure, file permissions, and user account restrictions
- integrated firewall
37. Match the commonly used ports on a Linux server with the corresponding service. (Not all options are used.)
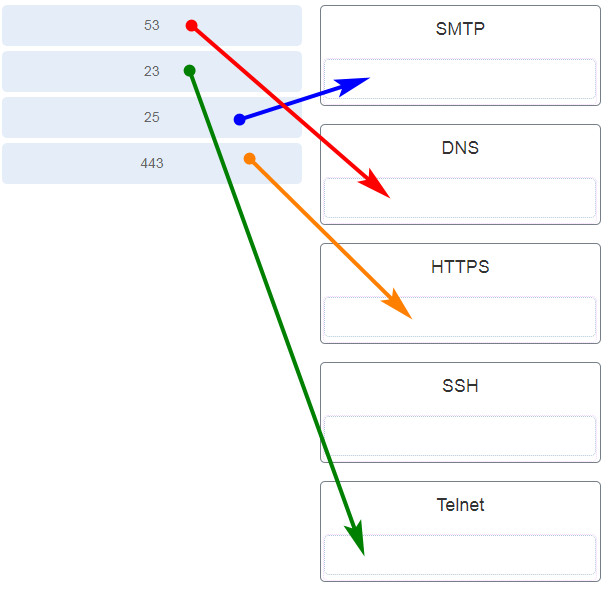
38. Which Windows tool can be used by a cybersecurity administrator to secure stand-alone computers that are not part of an active directory domain?
- PowerShell
- Windows Defender
- Windows Firewall
- Local Security Policy

Questions and Mutiple-Choice
Great job. I am very thankful for the help offered. The explanation makes sense for us to understand the concepts.
Great job. I am very thankful for the help offered. The explanation makes sense for us to understand the comncepts.
Q4 and Q30 are the same
I hope you let us add pictures for the illustrations of the questions, Thanks for your amazing site.
OK, I have enable it, you can attach picture in your comments. Thank you for sharing, I will update it in this post.
25- Why would a network administrator choose Linux as an operating system in the Security Operations Center (SOC)?
+ It is easier to use than other operating systems.
+ More network applications are created for this environment.
+ It is more secure than other server operating systems.
+ The administrator has more control over the operating system.
24- Which two methods can be used to harden a computing device? (Choose two.)
Allow default services to remain enabled.
Allow USB auto-detection.
Enforce the password history mechanism.
Update patches on a strict annual basis irrespective of release date.
Ensure physical security.
23- Which Linux command can be used to display the name of the current working directory?
sudo
ps
pwd
chmod
22- Consider the result of the ls -l command in the Linux output below. What are the file permissions assigned to the sales user for the analyst.txt file?
write only
read, write
read only
read, write, execute
21- A Linux system boots into the GUI by default, so which application can a network administrator use in order to access the CLI environment?
system viewer
file viewer
package management tool
terminal emulator
20- What is the well-known port address number used by DNS to serve requests?
25
53
110
60
19- Which user can override file permissions on a Linux computer?
+any user that has ‘group’ permission to the file
+only the creator of the file
+any user that has ‘other’ permission to the file
+root user
18- Match the commonly used ports on a Linux server with the corresponding service.
SMTP 25
DNS 53
HTTPS 443
SSH 22
TELNET 23
Match the commonly used ports on a Linux server with the corresponding service. (Not all options are used.)
SSH “22” IS NOT FOUND BUT I ADDED IT JUST TO KNOW ITS PORT NUMBER.
17- Match typical Linux log files to the function.
used by RedHat and CentOS computers and tracks authentication-related events:/var/log/secure
contains generic computer activity logs, and is used to store informational and noncritical system messages:/var/log/messages
stores information related to hardware devices and their drivers:/var/log/dmesg
used by Debian and Ubuntu computers and stores all authentication-related events:/var/log/auth.log
16- Which type of tool allows administrators to observe and understand every detail of a network transaction?
15- Why is Kali Linux a popular choice in testing the network security of an organization?
THE CORRECT ANSWER IS;
It is an open source Linux security distribution containing many penetration tools.
14- Match the octal value to the file permission description in Linux. (Not all options are used.)
write onlyread and executeread and writeexecute onlywrite and executeno access
000
001
010
101
110
write only – read and execute – read and write – execute only – write and execute – no access.
I don’t know the answer
write only – read and execute – read and write – execute only – write and execute – no access.
THE CORRECT ANSWERES:
010
101
110
001
NOT SCORED
000
13- Match the Linux command to the function. (Not all options are used.)
hmodudodisplays the name of the current working directory: pwd
runs a command as another user: sudo
modifies file permissions:
chmod
shuts down the system:
lists the processes that are currently running: ps
THE ANSWERS ARE CORRECT:
Displays the name of the current working directory: pwd
runs a command as another user: sudo
modifies file permissions: chmod
shuts down the system:
lists the processes that are currently running: ps
12- What are two advantages of the NTFS file system compared with FAT32? (Choose two.)
11- A PC user issues the netstat command without any options. What is displayed as the result of this command?
The correct answer is:
a list of all established active TCP connections
10- Which two commands could be used to check if DNS name resolution is working properly on a Windows PC? (Choose two.)
9- What is the purpose of using the net accounts command in Windows?
8- Match the Windows 10 boot sequence after the boot manager (bootmgr.exe) loads.
Step one: The Windows boot loader Winload.exe loads
Step two: Ntosknl.exe and hal.dll are loaded
Step three: Winload.exe reads the registry, chooses a hardware profile, and loads the device drivers.
Step four: Ntoskrnl.exe takes over the process.
Step five: Winlogon.exe is loaded and excutes the logon process.
Step one: The Windows boot loader Winload.exe loads
Step two: Winload.exe reads the registry, chooses a hardware profile, and loads the device drivers.
Step three: Ntosknl.exe and hal.dll are loaded
Step four: Ntoskrnl.exe takes over the process.
Step five: Winlogon.exe is loaded and excutes the logon process.
Yei is incorrect.
7- A technician has installed a third party utility that is used to manage a Windows 7 computer. However, the utility does not automatically start whenever the computer is started. What can the technician do to resolve this problem?
iS THE CORRECT ANSWER
6- Which statement describes the function of the Server Message Block (SMB) protocol?
The correct answer is;
It is used to share network resources.
5- A user creates a file with .ps1 extension in Windows. What type of file is it?
PowerShell script
iS THE CORRECT ANSWER
4- Match the Windows command to the description.
renames a file: ren
creates a new directory: mkdir
changes the current directory: cd
lists files in a directory: dir
3- A user logs in to Windows with a regular user account and attempts to use an application that requires administrative privileges. What can the user do to successfully use the application?
2- An IT technician wants to create a rule on two Windows 10 computers to prevent an installed application from accessing the public Internet. Which tool would the technician use to accomplish this task?
The correct answer is;
Windows Defender Firewall with Advanced Security
1- What technology was created to replace the BIOS program on modern personal computer motherboards?