1. Refer to the exhibit. Approximately what percentage of the physical memory is still available on this Windows system?
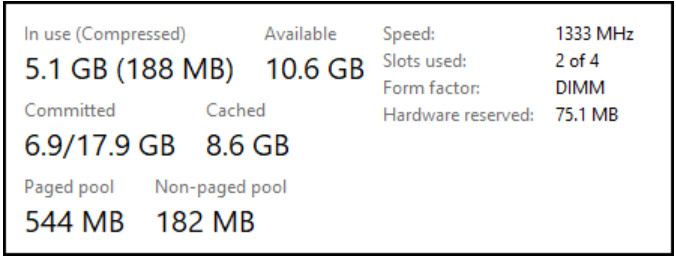
- 32%
- 53%
- 68%
- 90%
2. Which Windows tool can be used by a cybersecurity administrator to secure stand-alone computers that are not part of an active directory domain?
- Local Security Policy
- Windows Defender
- Windows Firewall
- PowerShell
3. Refer to the exhibit. Which technology would contain information similar to the data shown for infrastructure devices within a company?
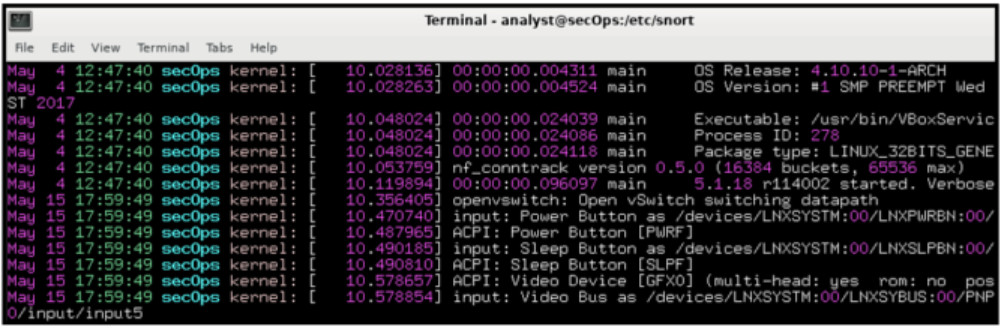
- Apache server
- firewall
- HIDS
- syslog server
4. What are three benefits of using symbolic links over hard links in Linux? (Choose three.)
- Symbolic links can be exported.
- They can be encrypted.
- They can be compressed.
- They can link to a directory.
- They can show the location of the original file.
- They can link to a file in a different file system.
5. Which two protocols are associated with the transport layer? (Choose two.)
- TCP
- IP
- UDP
- PPP
- ICMP
6. Refer to the exhibit. A user reports that resources can no longer be reached on the local 192.168.1.0/24 network nor on the internet. A cybersecurity analyst investigates the issue by reviewing the routing table of the PC in question. What is the reason for the problem reported by the user?
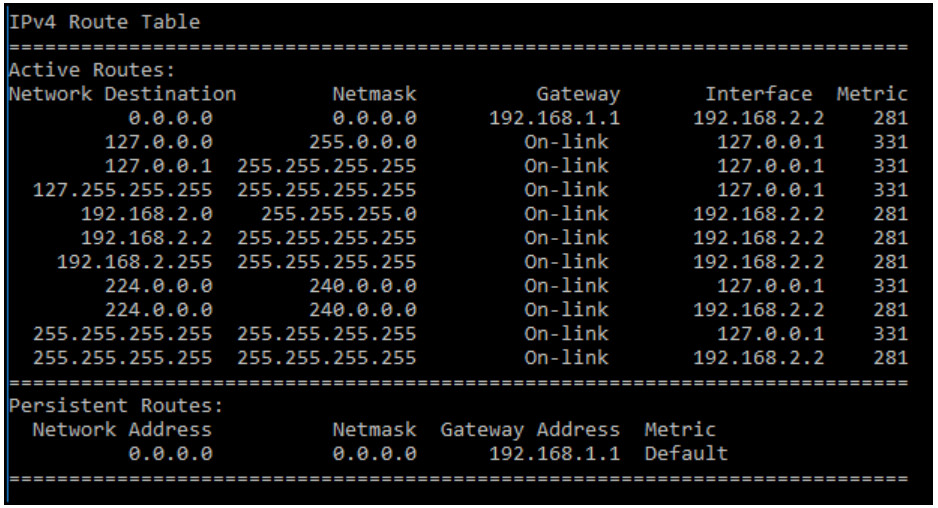
- incorrect host IP address
- incorrect subnet mask
- incorrect default gateway
- incorrect route metric
7. What is the function of ARP?
- resolves domain names to IP addresses
- provides automatic IP address assignments to hosts
- sends error and operational information messages to hosts
- maps IPv4 addresses to MAC addresses
8. A cybersecurity analyst believes an attacker is spoofing the MAC address of the default gateway to perform a man-in-the-middle attack. Which command should the analyst use to view the MAC address a host is using to reach the default gateway?
- ipconfig /all
- route print
- netstat -r
- arp -a
9. Which network service is used by clients to resolve the IP address of a domain name?
- DHCP
- DNS
- ARP
- ICMP
10. Refer to the exhibit. A cybersecurity analyst is viewing captured packets forwarded on switch S1. Which device is the source of the captured packet?
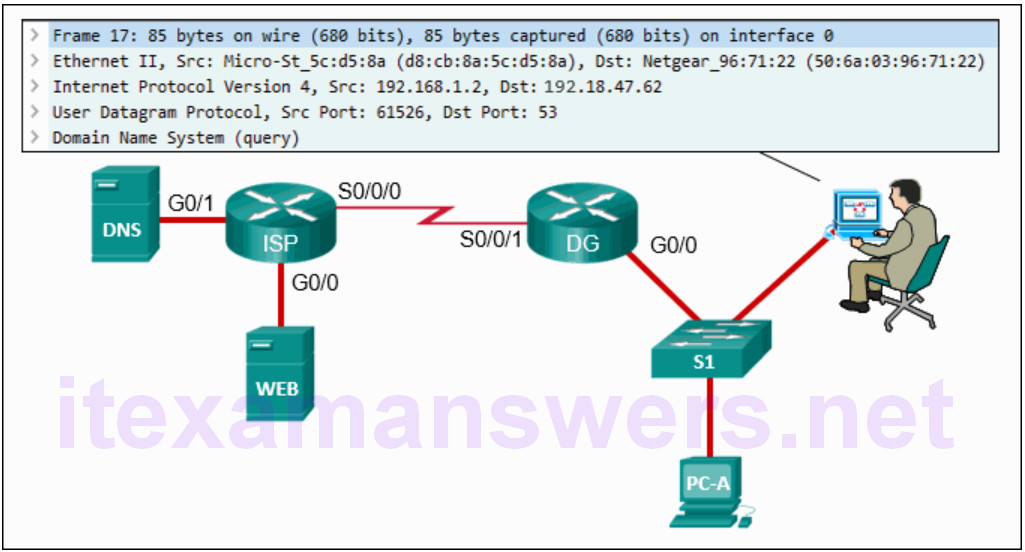
- DNS server
- PC-A
- DG router
- ISP router
- web server
11. What is a purpose of implementing VLANs on a network?
- They can separate user traffic.
- They prevent Layer 2 loops.
- They eliminate network collisions.
- They allow switches to forward Layer 3 packets without a router.
12. Which type of firewall is a combination of various firewall types?
- packet filtering
- stateful
- proxy
- hybrid
13. What is a feature of an IPS?
- It can stop malicious packets.
- It has no impact on latency.
- It is deployed in offline mode.
- It is primarily focused on identifying possible incidents.
14. Refer to the exhibit. A network administrator has written a standard access control list to prevent packets from the 192.168.2.0 LAN from reaching the restricted LAN 192.168.3.0 while permiting traffic from any other LAN. On what interface and in which direction should the access list be implemented on router R1?
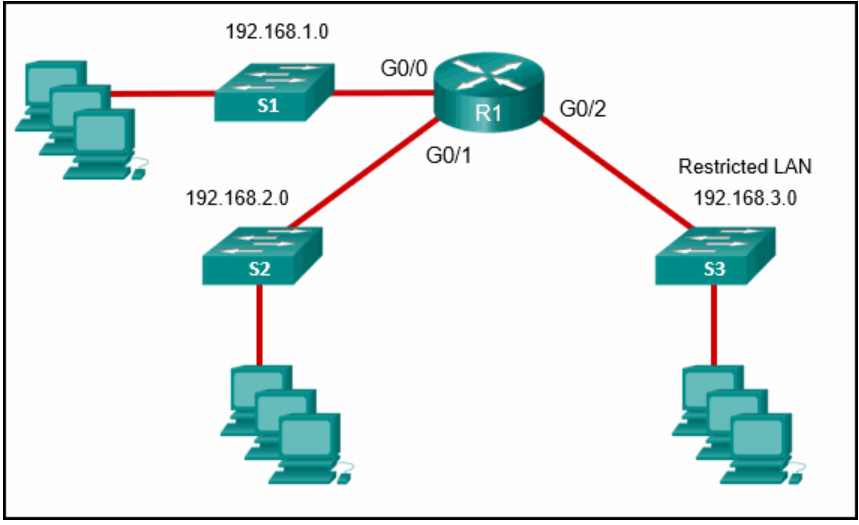
- interface G0/0 inbound
- interface G0/2 inbound
- interface G0/2 outbound
- interface G0/1 outbound
15. What is an example of a local exploit?
- Port scanning is used to determine if the Telnet service is running on a remote server.
- A threat actor performs a brute force attack on an enterprise edge router to gain illegal access.
- A buffer overflow attack is launched against an online shopping website and causes the server crash.
- A threat actor tries to gain the user password of a remote host by using a keyboard capture software installed on it by a Trojan.
16. After complaints from users, a technician identifies that the college web server is running very slowly. A check of the server reveals that there are an unusually large number of TCP requests coming from multiple locations on the Internet. What is the source of the problem?
- A DDoS attack is in progress.
- The server is infected with a virus.
- There is insufficient bandwidth to connect to the server.
- There is a replay attack in progress.
17. A user receives an email requesting verification of the password that is used to access bank files. What type of security threat is this?
- virus
- social engineering
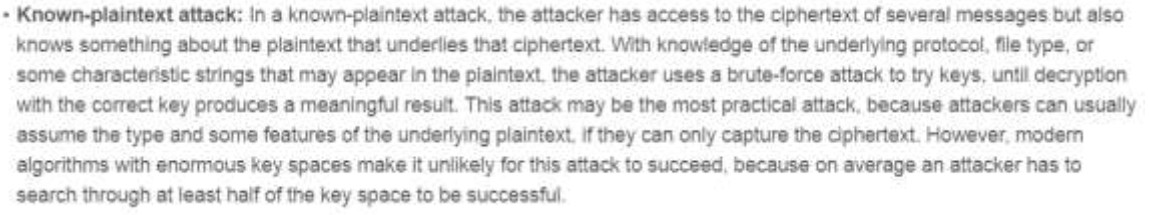
- phishing
- malware
18. To which category of security attacks does man-in-the-middle belong?
- DoS
- access
- reconnaissance
- social engineering
19. What is the main goal of using different evasion techniques by threat actors?
- to launch DDoS attacks on targets
- to identify vulnerabilities of target systems
- to gain the trust of a corporate employee in an effort to obtain credentials
- to prevent detection by network and host defenses
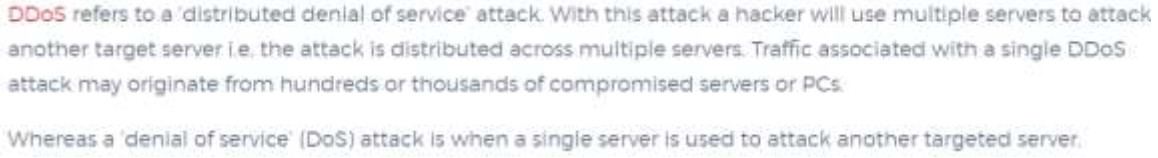
20. What are two examples of DoS attacks? (Choose two.)
- phishing
- ping of death
- SQL injection
- port scanning
- buffer overflow
21. Which attack is integrated with the lowest levels of the operating system of a host and attempts to completely hide the activities of the threat actor on the local system?
- rootkit
- traffic insertion
- traffic substitution
- encryption and tunneling
22. Which evasion method describes the situation that after gaining access to the administrator password on a compromised host, a threat actor is attempting to login to another host using the same credentials?
- pivoting
- traffic substitution
- resource exhaustion
- protocol-level misinterpretation
23. Which two attacks target web servers through exploiting possible vulnerabilities of input functions used by an application? (Choose two.)
- SQL injection
- port scanning
- port redirection
- trust exploitation
- cross-site scripting
24. What is the first line of defense when an organization is using a defense-in-depth approach to network security?
- IPS
- edge router
- firewall
- proxy server
25. What is the benefit of a defense-in-depth approach?
- The effectiveness of other security measures is not impacted when a security mechanism fails.
- The need for firewalls is eliminated.
- All network vulnerabilities are mitigated.
- Only a single layer of security at the network core is required.
26. Which access control model allows users to control access to data as an owner of that data?
- mandatory access control
- nondiscretionary access control
- discretionary access control
- attribute-based access control
27. What is the principle behind the nondiscretionary access control model?
- It applies the strictest access control possible.
- It allows access decisions to be based on roles and responsibilities of a user within the organization.
- It allows users to control access to their data as owners of that data.
- It allows access based on attributes of the object be to accessed.
28. What is an example of privilege escalation attack?
- A threat actor sends an email to an IT manager to request the root access.
- A threat actor performs an access attack and gains the administrator password.
- A DDoS attack is launched against a government server and causes the server to crash.
- A port scanning attack finds that the FTP service is running on a server that allows anonymous access.
29. Which access control model applies the strictest access control and is often used in military and mission critical applications?
- discretionary
- mandatory
- nondiscretionary
- attribute-based
30. Which data security component is provided by hashing algorithms?
- key exchange
- confidentiality
- integrity
- authentication
31. Which two algorithms use a hashing function to ensure message integrity? (Choose two.)
- SEAL
- AES
- 3DES
- MD5
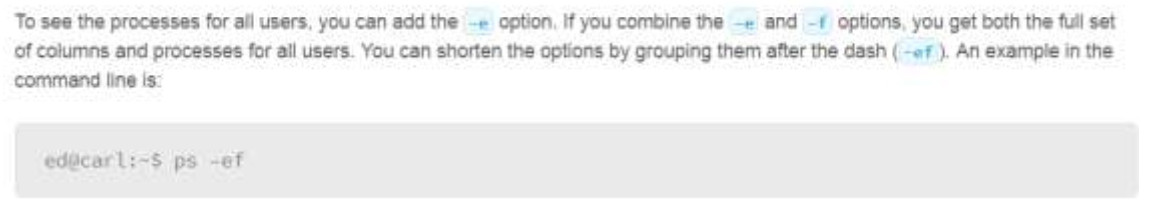
- SHA
32. What is a feature of asymmetrical encryption?
- Different keys are used to encrypt and decrypt data.
- Key lengths are short.
- It encrypts bulk data quickly.
- It requires fewer computations than symmetric encryption requires.
33. What technology supports asymmetric key encryption used in IPsec VPNs?
- 3DES
- IKE
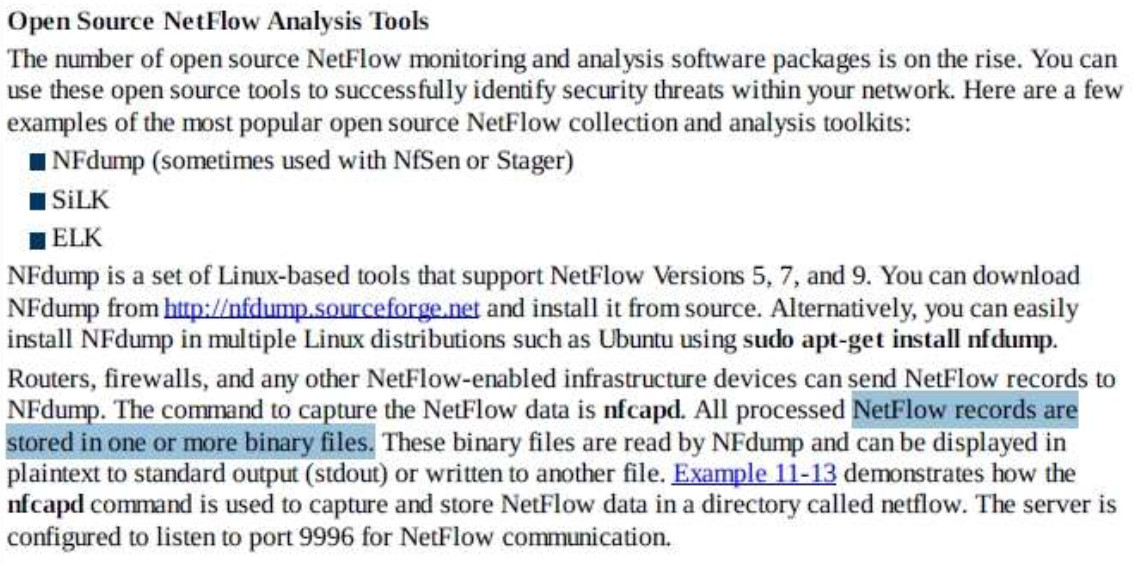
- SEAL
- AES
34. Which security function is provided by encryption algorithms?
- key management
- authorization
- integrity
- confidentiality
35. A security professional is making recommendations to a company for enhancing endpoint security. Which security endpoint technology would be recommended as an agent-based system to protect hosts against malware?
- baselining
- blacklisting
- HIDS
- IPS
36. Which firewall application runs on a Linux host and allows an administrator to configure network access rules as part of the Linux kernel?
- vShield
- nftables
- TCP Wrapper
- iptables
37. Which security endpoint setting would be used by a security analyst to determine if a computer has been configured to prevent a particular application from running?
- services
- block listing
- baselining
- Allow listing
38. Which technique could be used by security personnel to analyze a suspicious file in a safe environment?
- baselining
- blacklisting
- sandboxing
- whitelisting
39. Which attack surface, defined by the SANS Institute, is delivered through the exploitation of vulnerabilities in web, cloud, or host-based applications?
- host
- human
- network
- software
40. What is an action that should be taken in the discovery step of the vulnerability management life cycle?
- assigning business value to assets
- determining a risk profile
- developing a network baseline
- documenting the security plan
41. Which security management plan specifies a component that involves tracking the location and configuration of networked devices and software across an enterprise?
- asset management
- risk management
- vulnerability management
- patch management
42. Which risk management plan involves discontinuing an activity that creates a risk?
- risk reduction
- risk retention
- risk avoidance
- risk sharing
43. A piece of malware has gained access to a workstation and issued a DNS lookup query to a CnC server. What is the purpose of this attack?
- to request a change of the IP address
- to send stolen sensitive data with encoding
- to check the domain name of the workstation
- to masquerade the IP address of the workstation
44. Why does HTTPS technology add complexity to network security monitoring?
- HTTPS uses tunneling technology for confidentiality.
- HTTPS hides the true source IP address using NAT/PAT.
- HTTPS conceals data traffic through end-to-end encryption.
- HTTPS dynamically changes the port number on the web server.
45. Which type of attack is carried out by threat actors against a network to determine which IP addresses, protocols, and ports are allowed by ACLs?
- phishing
- reconnaissance
- denial of service
- social engineering
46. How can NAT/PAT complicate network security monitoring if NetFlow is being used?
- It changes the source and destination MAC addresses.
- It conceals the contents of a packet by encrypting the data payload.
- It disguises the application initiated by a user by manipulating port numbers.
- It hides internal IP addresses by allowing them to share one or a few outside IP addresses.
47. Which statement describes the function provided by the Tor network?
- It distributes user packets through load balancing.
- It allows users to browse the Internet anonymously.
- It conceals packet contents by establishing end-to-end tunnels.
- It manipulates packets by mapping IP addresses between two networks.
48. Refer to the exhibit. A security analyst is reviewing an alert message generated by Snort. What does the number 2100498 in the message indicate?

- the message length in bits
- the Snort rule that is triggered
- the session number of the message
- the id of the user that triggers the alert
49. Which type of data is used by Cisco Cognitive Threat Analytics to find malicious activity that has bypassed security controls, or entered through unmonitored channels, and is operating inside an enterprise network?
- alert
- session
- statistical
- transaction
50. Refer to the exhibit. A security analyst is reviewing the logs of an Apache web server. Which action should the analyst take based on the output shown?
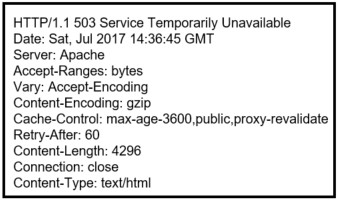
- Ignore the message.
- Notify the server administrator.
- Restart the server.
- Notify the appropriate security administration for the country.
51. Which Windows application is commonly used by a cybersecurity analyst to view Microsoft IIS access logs?
- Event Viewer
- Notepad
- SIEM
- Word
52. Which tool captures full data packets with a command-line interface only?
- nfdump
- NBAR2
- tcpdump
- Wireshark
53. What is a key difference between the data captured by NetFlow and data captured by Wireshark?
- NetFlow provides transaction data whereas Wireshark provides session data.
- NetFlow data is analyzed by tcpdump whereas Wireshark data is analyzed by nfdump.
- NetFlow collects metadata from a network flow whereas Wireshark captures full data packets.
- NetFlow data shows network flow contents whereas Wireshark data shows network flow statistics.
54. Which Cisco appliance can be used to filter network traffic contents to report and deny traffic based on the web server reputation?
- ASA
- AVC
- ESA
- WSA
55. Which type of event is logged in Cisco Next-Generation IPS devices (NGIPS) using FirePOWER Services when changes have been detected in the monitored network?
- intrusion
- connection
- host or endpoint
- network discovery
New Questions for 210-250 Exam (Dump)
61. Which definition of a process in Windows is true?
- running program
- unit of execution that must be manually scheduled by the application
- database that stores low-level settings for the OS and for certain applications
- basic unit to which the operating system allocates processor time
62. Which definition of permissions in Linux is true?
- rules that allow network traffic to go in and out
- table maintenance program
- written affidavit that you have to sign before using the system
- attributes of ownership and control of an objec
63. Which hashing algorithm is the least secure?
- MD5
- RC4
- SHA-3
- SHA-2
64. Which protocol is expected to have NTP a user agent, host, and referrer headers in a packet capture?
- NTP
- HTTP
- DNS
- SSH
65. Which definition of a daemon on Linux is true?
- error check right after the call to fork a process
- new process created by duplicating the calling process
- program that runs unobtrusively in the background
- set of basic CPU instructions
66. Which definition of vulnerability is true?
- an exploitable unpatched and unmitigated weakness in software
- an incompatible piece of software
- software that does not have the most current patch applied
- software that was not approved for installation
67. Which option is an advantage to using network-based anti-virus versus host-based anti- virus?
- Network-based has the ability to protect unmanaged devices and unsupported operating systems.
- There are no advantages compared to host-based antivirus.
- Host-based antivirus does not have the ability to collect newly created signatures.
- Network-based can protect against infection from malicious files at rest.
68. Which evasion method involves performing actions slower than normal to prevent detection?
- traffic fragmentation
- tunneling
- timing attack
- resource exhaustion
69. Which event occurs when a signature-based IDS encounters network traffic that triggers an alert?
- A. connection event
- B. endpoint event
- C. NetFlow event
- D. intrusion event
70. Which data can be obtained using NetFlow?
- session data
- application logs
- network downtime
- report full packet capture
71. Which term describes the act of a user, without authority or permission, obtaining rights on a system, beyond what were assigned?
- authentication tunneling
- administrative abuse
- rights exploitation
- privilege escalation
72. Refer to the exhibit. A TFTP server has recently been installed in the Atlanta office. The network administrator is located in the NY office and has attempted to make a connection to the TFTP server. They are unable to backup the configuration file and Cisco IOS of the NY router to the TFTP server Which cause of this problem is true?
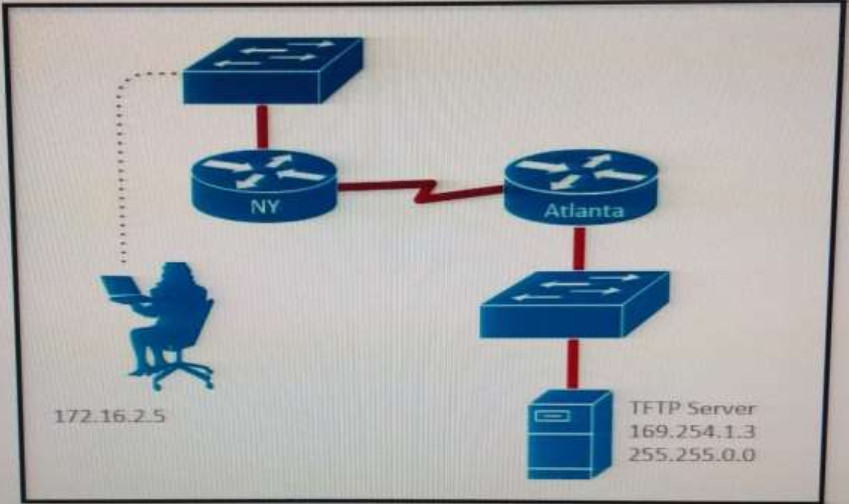
- The TFTP server cannot obtain an address from a DHCP Server.
- The TFTP server has an incorrect IP address.
- The network administrator computer has an incorrect IP address
- The TFTP server has an incorrect subnet mask.
73. Which term represents a potential danger that could take advantage of a weakness in a system?
- vulnerability
- risk
- threat
- Dexploit
74. Which security principle states that more than one person is required to perform a critical task?
- due diligence
- separation of duties
- need to know
- least privilege
75. You must create a vulnerability management framework. Which main purpose of this framework is true?
- Conduct vulnerability scans on the network.
- Manage a list of reported vulnerabilities.
- Identify remove and mitigate system vulnerabilities.
- Detect and remove vulnerabilities in source code.
76. In computer security, which information is the term PHI used to describe?
- private host information
- protected health information
- personal health information
- protected host information
77. Which security monitoring data type requires the most storage space?
- full packet capture
- transaction data
- statistical data
- session data
78. Which type of exploit normally requires the culprit to have prior access to the target system?
- local exploit
- denial of service
- system vulnerability
- remote exploit
79. Which identifier is used to describe the application or process that submitted a log message?
- action
- selector
- priority
- facility
80. Which concern is important when monitoring NTP servers for abnormal levels of traffic?
- Being the cause of a distributed reflection denial of service attack.
- Users changing the time settings on their systems.
- A critical server may not have the correct time synchronized.
- Watching for rogue devices that have been added to the network.
81. Which protocol is primarily supported by the third layer of the Open Systems Interconnection reference model?
- HTTP/TLS
- IPv4/IPv6
- TCP/UDP
- ATM/ MPLS
82. A firewall requires deep packet inspection to evaluate which layer?
- application
- Internet
- link
- transport
83. Which two protocols are used for email (Choose two )
- NTP
- DNS
- HTTP
- IMAP
- SMTP
84. Which two options are recognized forms of phishing? (Choose two )
- spear
- whaling
- mailbomb
- hooking
- mailnet
85. While viewing packet capture data, you notice that one IP is sending and receiving traffic for multiple devices by modifying the IP header, Which option is making this behavior possible?
- TOR
- NAT
- encapsulation
- tunneling
86. Which definition of an antivirus program is true?
- program used to detect and remove unwanted malicious software from the system
- program that provides real time analysis of security alerts generated by network hardware and application
- program that scans a running application for vulnerabilities
- rules that allow network traffic to go in and out
87. Which type of attack occurs when an attacker is successful in eavesdropping on a conversation between two IPS phones?
- replay
- man-in-the-middle
- dictionary
- known-plaintext
88. An intrusion detection system begins receiving an abnormally high volume of scanning from numerous sources. Which evasion technique does this attempt indicate?
- traffic fragmentation
- resource exhaustion
- timing attack
- tunneling
89. Which type of attack occurs when an attacker utilizes a botnet to reflect requests off an NTP server to overwhelm their target?
- man in the middle
- denial of service
- distributed denial of service
- replay
90. In NetFlow records, which flags indicate that an HTTP connection was stopped by a security appliance, like a firewall, before it could be built fully?
- ACK
- SYN ACK
- RST
- PSH, ACK
91. Which definition of a fork in Linux is true?
- daemon to execute scheduled commands
- parent directory name of a file pathname
- macros for manipulating CPU sets
- new process created by a parent process
92. Which two actions are valid uses of public key infrastructure?(Choose two )
- ensuring the privacy of a certificate
- revoking the validation of a certificate
- validating the authenticity of a certificate
- creating duplicate copies of a certificate
- changing ownership of a certificate
93. Which two terms are types of cross site scripting attacks? (Choose two )
- directed
- encoded
- stored
- reflected
- cascaded
94. Which network device is used to separate broadcast domains?
- router
- repeater
- switch
- bridge
95. Based on which statement does the discretionary access control security model grant or restrict access ?
- discretion of the system administrator
- security policy defined by the owner of an object
- security policy defined by the system administrator
- role of a user within an organization
96. Which cryptographic key is contained in an X.509 certificate?
- symmetric
- public
- private
- asymmetric
97. Which two activities are examples of social engineering? (Choose two)
- receiving call from the IT department asking you to verify your username/password to maintain the account
- receiving an invite to your department’s weekly WebEx meeting
- sending a verbal request to an administrator to change the password to the account of a user the administrator does know
- receiving an email from MR requesting that you visit the secure HR website and update your contract information
- receiving an unexpected email from an unknown person with an uncharacteristic attachment from someone in the same company
98. Which hash algorithm is the weakest?
- SHA-512
- RSA 4096
- SHA-1
- SHA-256
99. A user reports difficulties accessing certain external web pages, When examining traffic to and from the external domain in full packet captures, you notice many SYNs that have the same sequence number, source, and destination IP address, but have different payloads. Which problem is a possible explanation of this situation?
- insufficient network resources
- failure of full packet capture solution
- misconfiguration of web filter
- TCP injection
100. Which tool is commonly used by threat actors on a webpage to take advantage of the softwarevulnerabilitiesof a system to spread malware?
- exploit kit
- root kit
- vulnerability kit
- script kiddie kit
101. Refer to the exhibit. During an analysis this list of email attachments is found. Which files contain the same content?
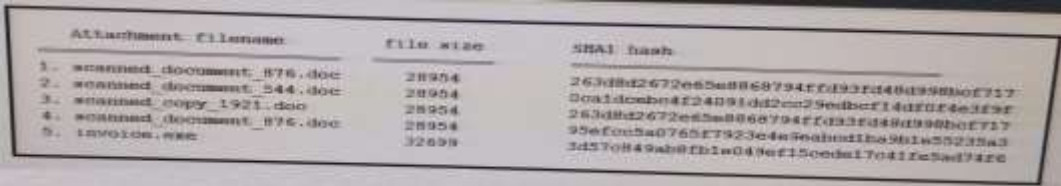
- 1 and 4
- 3 and 4
- 1 and 3
- 1 and 2
102. Which term represents the practice of giving employees only those permissions necessary to perform their specific role within an organization?
- integrity validation
- due diligence
- need to know
- least privilege
103. Which term represents the chronological record of how evidence was collected- analyzed, preserved, and transferred?
- chain of evidence
- evidence chronology
- chain of custody
- record of safekeeping
104. Which two tasks can be performed by analyzing the logs of a traditional stateful firewall? (Choose two.)
- Confirm the timing of network connections differentiated by the TCP 5-tuple
- Audit the applications used within a social networking web site.
- Determine the user IDs involved in an instant messaging exchange.
- Map internal private IP addresses to dynamically translated external public IP addresses
- Identify the malware variant carried by ^n SMTP connection
105. Which security monitoring data type is associated with application server logs?
- alert data
- statistical data
- session data
- transaction data
106. Where is a host-based intrusion detection system located?
- on a particular end-point as an agent or a desktop application
- on a dedicated proxy server monitoring egress traffic
- on a span switch port
- on a tap switch port
107. One of the objectives of information security is to protect the CIA of information and systems. What does CIA mean in this context?
- Confidentiality, Integrity, and Availability
- Confidentiality, Identity, and Availability
- Confidentiality, Integrity, and Authorization
- Confidentiality, Identity, and Authorization
108. According to RFC 1035 which transport protocol is recommended for use with DNS queries?
- Transmission Control Protocol
- Reliable Data Protocol
- Hypertext Transfer Protocol
- User Datagram Protocol
109. Which definition describes the main purpose of a Security Information and Event Management solution ?
- a database that collects and categorizes indicators of compromise to evaluate and search for potential security threats
- a monitoring interface that manages firewall access control lists for duplicate firewall filtering
- a relay server or device that collects then forwards event logs to another log collection device
- a security product that collects, normalizes, and correlates event log data to provide holistic views of the security posture
110. Which option is a purpose of port scanning?
- Identify the Internet Protocol of the target system.
- Determine if the network is up or down
- Identify which ports and services are open on the target host.
- Identify legitimate users of a system.
111. Which definition of the virtual address space for a Windows process is true?
- actual physical location of an object in memory
- set of virtual memory addresses that it can use
- set of pages that are currently resident in physical memory
- system-level memory protection feature that is built into the operating system
112. Which information security property is supported by encryption?
- sustainability
- integrity
- confidentiality
- availability
113. Which situation indicates application-level white listing?
- Allow everything and deny specific executable files.
- Allow specific executable files and deny specific executable files.
- Writing current application attacks on a whiteboard daily.
- Allow specific files and deny everything else.
114. If a web server accepts input from the user and passes it to a bash shell, to which attack method is it vulnerable?
- input validation
- hash collision
- command injection
- integer overflow
115. Which encryption algorithm is the strongest?
- AES
- CES
- DES
- 3DES
116. Which protocol maps IP network addresses to MAC hardware addresses so that IP packets can be sent across networks?
- Internet Control Message Protocol
- Address Resolution Protocol
- Session Initiation Protocol
- Transmission Control Protocol/Internet Protocol
117. Which statement about digitally signing a document is true?
- The document is hashed and then the document is encrypted with the private key.
- The document is hashed and then the hash is encrypted with the private key.
- The document is encrypted and then the document is hashed with the public key
- The document is hashed and then the document is encrypted with the public key.
118. For which reason can HTTPS traffic make security monitoring difficult?
- encryption
- large packet headers
- Signature detection takes longer.
- SSL interception
119. Which directory is commonly used on Linux systems to store log files, including syslog and apache access logs?
- /etc/log
- /root/log
- /lib/log
- /var/log
120. Drag and Drop.
Drag the technology on the left to the data type the technology provides on the right.
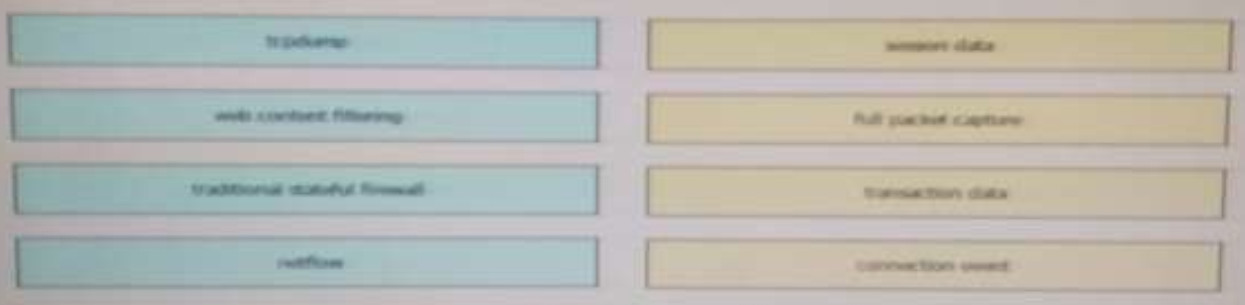
Answer:

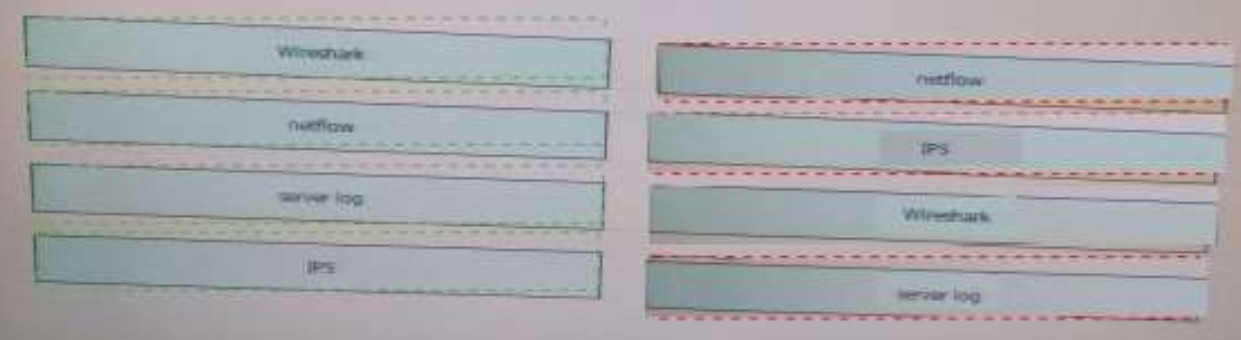
121. Drag and Drop.
Drag the data source on the left to the left to the correct data type on the right.

Answer:
122. Which technology allows a large number of private IP addresses to be represented by a smaller number of public IP addresses?
- NAT
- NTP
- RFC 1631
- RFC 1918
123. Which NTP command configures the local device as an NTP reference clock source?
- ntp peer
- ntp broadcast
- ntp master
- ntp server
124. Which three options are types of Layer 2 network attack? (Choose three.)
- ARP attacks
- brute force attacks
- spoofing attacks
- DDOS attacks
- VLAN hopping
- botnet attacks
125. If a router has four interfaces and each interface is connected to four switches, how many broadcast domains are present on the router?
- 1
- 2
- 4
- 8
126. Where does routing occur within the DoD TCP/IP reference model?
- application
- internet
- network
- transport
127. Which two features must a next generation firewall include? (Choose two.)
- data mining
- host-based antivirus
- application visibility and control
- Security Information and Event Management
- intrusion detection system
128. Which term represents a weakness in a system that could lead to the system being compromised?
- vulnerability
- threat
- exploit
- risk
129. Which definition of Windows Registry is true?
- set of pages that are currently resident m physical memory
- basic unit to which the operating system allocates processor time
- set of virtual memory addresses
- database that stores low-level settings for the operating system
130. Which definition of the IIS Log Parser tool is true?
- a logging module for IIS that allows you to log to a database
- a data source control to connect to your data source
- a powerful, versatile tool that makes it possible to run SQL-like queries against log flies
- a powerful versatile tool that verifies the integrity of the log files
131. What is PHI?
- Protected HIPAA information
- Protected health information
- Personal health information
- Personal human information
132. Which of the following are Cisco cloud security solutions?
- CloudDLP
- OpenDNS
- CloudLock
- CloudSLS
133. What is a trunk link used for?
- To pass multiple virtual LANs
- To connect more than two switches
- To enable Spanning Tree Protocol
- To encapsulate Layer 2 frames
134. At which OSI layer does a router typically operate?
- Transport
- Network
- Data link
- Application
135. Cisco pxGrid has a unified framework with an open API designed in a hub-and-spoke architecture. pxGrid is used to enable the sharing of contextual-based information from which devices?
- From a Cisco ASA to the Cisco OpenDNS service
- From a Cisco ASA to the Cisco WSA
- From a Cisco ASA to the Cisco FMC
- From a Cisco ISE session directory to other policy network systems, such as Cisco IOS devices and the Cisco ASA
136. What are the advantages of a full-duplex transmission mode compared to half-duplex mode? (Select all that apply.)
- Each station can transmit and receive at the same time.
- It avoids collisions.
- It makes use of backoff time.
- It uses a collision avoidance algorithm to transmit.
137. Stateful and traditional firewalls can analyze packets and judge them against a set of predetermined rules called access control lists (ACLs). They inspect which of the following elements within a packet? (Choose Two)
- Session headers
- NetFlow flow information
- Source and destination ports and source and destination IP addresses
- Protocol information
138. In which case should an employee return his laptop to the organization?
- When moving to a different role
- Upon termination of the employment
- As described in the asset return policy
- When the laptop is end of lease
139. Which of the following are metrics that can measure the effectiveness of a runbook?
- Mean time to repair (MTTR)
- Mean time between failures (MTBF)
- Mean time to discover a security incident
- All of the above
140. Which of the following access control models use security labels to make access decisions?
- Mandatory access control (MAC)
- Role-based access control (RBAC)
- Identity-based access control (IBAC)
- Discretionary access control (DAC)
141. Where are configuration records stored?
- In a CMDB
- In a MySQL DB
- In a XLS file
- There is no need to store them
142. Which of the following is true about heuristic-based algorithms?
- Heuristic-based algorithms may require fine tuning to adapt to network traffic and minimize the possibility of false positives.
- Heuristic-based algorithms do not require fine tuning.
- Heuristic-based algorithms support advanced malware protection.
- Heuristic-based algorithms provide capabilities for the automation of IPS signature creation and tuning.
143. How many broadcast domains are created if three hosts are connected to a Layer 2 switch in full- duplex mode?
- 4
- 3
- None
- 1
144. What is one of the advantages of the mandatory access control (MAC) model?
- Stricter control over the information access.
- Easy and scalable.
- The owner can decide whom to grant access to.
- Complex to administer.
145. According to the attribute-based access control (ABAC) model, what is the subject location considered?
- Part of the environmental attributes
- Part of the object attributes
- Part of the access control attributes
- None of the above
146. What type of algorithm uses the same key to encryp and decrypt data?
- symmetric algorithm
- an asymetric algorithm
- a Public Key infrastructure algorithm
- an IP Security algorithm
147. Which actions can a promiscuous IPS take to mitigate an attack?
- modifying packets
- requesting connection blocking
- denying packets
- resetting the TCP connection
- requesting host blocking
- denying frames
148. Which Statement about personal firewalls is true?
- They are resilient against kernal attacks
- They can protect email messages and private documents in a similar way to a VPN
- They can protect the network against attacks
- They can protect a system by denying probing requests
149. Which three statements about host-based IPS are true? (Choose three)
- It can view encrypted files
- It can be deployed at the perimeter
- It uses signature-based policies
- It can have more restrictive policies than network-based IPS
- It works with deployed firewalls
- It can generate alerts based on behavior at the desktop level.
150. An attacker installs a rogue switch that sends superior BPDUs on your network. What is a possible result of this activity?
- The switch could offer fake DHCP addresses.
- The switch could become the root bridge.
- The switch could be allowed to join the VTP domain
- The switch could become a transparent bridge.
151. The FMC can share HTML, Pdf and csv data type that relate to a specific event type which event type:
- connection
- Host
- Netflow
- Intrusion
152. For which purpose can Windows management instrumentation be used?
- Remote viewing of a computer
- Remote blocking of malware on a computer
- Remote reboot of a computer
- Remote start of a computer
153. Which international standard is for general risk management, including the principles and guideline for managing risk?
- ISO 31000
- ISO 27001
- ISO 27005
- ISO 27002
154. Which statement about the difference between a denial-of-service attack and a distributed denial of service attack is true?
- Dos attack are launched from one host, and DDoS attack are launched from multiple host.
- DoS attack and DDOS attack have no differences
- DDoS attacks are launched from one host, and DoS attacks are launched from multiple host.
- Dos attack only use flooding to compromise a network, and DDoS attacks only use other methods
155. You discover that a foreign government hacked one of the defense contractors in your country and stole intellectual property. In this situation, which option is considered the threat agent?
- method in which the hack occurred.
- defense contractor that stored the intellectual property.
- intellectual property that was stolen.
- foreign government that conducted the attack.
156. After a large influx of network traffic to externally facing devices, you begin investigating what appear to be a denial of service attack. When you review packets capture data, you notice that the traffic is a single SYN packet to each port. Which kind of attack is this?
- SYN flood.
- Host profiling.
- traffic fragmentation.
- port scanning.
157. Which definition of common event format is terms of a security information and event management solution is true?
- a type of event log used to identify a successful user login.
- a TCP network media protocol.
- Event log analysis certificate that stands for certified event forensics.
- a standard log event format that is used for log collection.
158. Which definition of a Linux daemon is true?
- Process that is causing harm to the system by either using up system resources or causing a critical crash.
- Long – running process that is the child at the init process
- process that has no parent process
- process that is starved at the CPU.
159. Which term describes reasonable effort that must be made to obtain relevant information to facilitate appropriate courses of action?
- Due diligence
- ethical behavior
- decision making
- data mining.
160. According to the common vulnerability scoring system, which term is associated with scoring multiple vulnerabilities that are exploit in the course of a single attack?
- chained score
- risk analysis
- Vulnerability chaining
- confidentiality
161. Which Linux terminal command can be used to display all the processes?
- ps -m
- ps -u
- ps -d
- ps -ef
162. Which statement about an attack surface is true?
- It is the sum of all paths for data/commands into and out of the application
- It is an exploitable weakness in a system or design
- It is the individual who perform an attack.
- It is any potential danger to an asset.
163. You get an alert on your desktop computer showing that an attack was successful on the host but up on investigation you see that occurred duration the attack. Which reason is true?
- The computer has HIDS installed on it
- The computer has NIDS installed on it
- The computer has HIPS installed on it
- The computer has NIPS installed on it
164. Which process continues to be recorded in the process table after it has ended and the status is returned to the parent?
- daemon
- zombie
- orphan
- child
165. For which kind of attack does an attacker use known information in encrypted files to break the encryption scheme for the rest of
- known-plaintext
- known-ciphertext
- unknown key
- man in the middle
166. In which technology is network level encrypted not natively incorporated?
- Kerberos
- ssl
- tls
- IPsec
167. Which purpose of command and control for network aware malware is true?
- It helps the malware to profile the host
- It takes over the user account
- It contacts a remote server for command and updates
- It controls and down services on the infected host
168. Which action is an attacker taking when they attempt to gain root access on the victims system?
- privilege escalation
- command injections
- root kit
- command and control
169. Which vulnerability is an example of Shellshock?
- SQL injection
- heap Overflow
- cross site scripting
- command injection
170. In which format are NetFlow records stored?
- base 10
- ASCII
- Binary
- Hexadecimal
171. A zombie process occurs when which of the following happens?
- A process holds its associated memory and resources but is released from the entry table.
- A process continues to run on its own.
- A process holds on to associate memory but releases resources.
- A process releases the associated memory and resources but remains in the entry table.
172. Early versions of the Microsoft PPTP virtual private network software used the same RC4 key for the sender and the receiver. Which attack is the network vulnerable to when a stream cipher like RC4 is used twice with the same key?
- forgery attack
- meet-in-the-middle attack
- ciphertext-only attack
- plaintext-only attack
173. How does NTP help with security monitoring?
- It synchronizes the time of day so that you can correlate events when you receive system logs.
- It enables you to look up the IP addresses a browser navigated to using the FQON.
- It allows you receive system-generated email traffic from log servers.
- It uses TCP, which allows you to see the HTTP conversations between servers and clients.
174. Which hash algorithm is cryptography used in certificate generation?
- SHA-256
- MD5
- RSA 4096
- SHA-512
175. Which description is an example of whaling?
- when attackers use fraudulent websites that look like legitimate ones
- when attackers go after the CEO
- when attackers target specific individuals
- when attackers target a group of individuals
176. Which tool provides universal query access to text based data such as event logs and file system?
- service viewer
- log parser
- handles
- Windows Management Instrumentation
177. You have deployed an enterprise-wide host/endpoint technology for all of the company corporate PCs. Management asks you to block a selected set of applications on all corporate PCs. Which technology is the best option?
- antivirus/antispyware software
- application whitelisting/blacklisting
- host-based IDS
- network NGFW
178. What does the sum of the risks presented by an application represent for that application?
- application attack surface
- security violation
- vulnerability
- HIPPA violation
179. The FMC can share HTML, PDF and CSV data types that relate to a specific event type. Which event type?
- host
- connection
- intrusion
- NetFlow














Hi, This dump are still valid?
Dear Sir, Kindly advice if there are any new questions for exams being taken before 28th May dateline.
If there are new questions kindly update.
okay! kindly tell me these dumps are still valid? if i prepare only these dumps enough to pass the Exam ?
Can you share your experience with the exam and the questions posted here? Thank you.
Dear sir, kindly update the Questions as soon as possible, because my voucher will be expired on 5th march 2020. i am waiting your response. i shall be very thankful to you in this regard.
Sorry, we don’t have many questions for this exam
Dear naeem, could you take the examen 210-250 ? these question serverd you?
sir please upload DRAG and DROP files and lab activity files as well so i prepare it as soon as possible
thank you .
Hello hassii!
210-250 exam includes only theoretical questions, no labs. DRAG and DROP question: Q120-121