How to find: Press “Ctrl + F” in the browser and fill in whatever wording is in the question to find that question/answer. If the question is not here, find it in Questions Bank.
NOTE: If you have the new question on this test, please comment Question and Multiple-Choice list in form below this article. We will update answers for you in the shortest time. Thank you! We truly value your contribution to the website.
CCNA Cybersecurity Operations (Version 1.1) – CyberOps Practice Final Exam
1. A person coming to a cafe for the first time wants to gain wireless access to the Internet using a laptop. What is the first step the wireless client will do in order to communicate over the network using a wireless management frame?
- associate with the AP
- authenticate to the AP
- discover the AP
- agree with the AP on the payload
Explanation: In order for wireless devices to communicate on a wireless network, management frames are used to complete a three-stage process:
Discover the AP
Authenticate with the AP
Associate with the AP
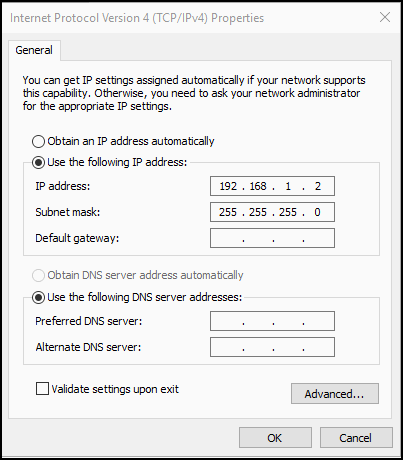
- 192.168.255.1
- 192.168.2.1
- 192.168.1.1
- 192.168.0.1
Explanation: The default gateway setting is the IP address of the router to which the host will send packets in order to reach remote networks. The default gateway address setting must be on the same logical network as the host IP address. In this case, the network of the host is 192.168.1.0 so the default gateway must also be on the 192.168.1.0 network.
- arp -a
- ipconfig /all
- netsat -r
- route print
Explanation: The command arp -a will display the MAC address table on a PC.
- risk management
- vulnerability management
- configuration management
- asset management
Explanation: Asset management involves the implementation of systems that track the location and configuration of networked devices and software across an enterprise.
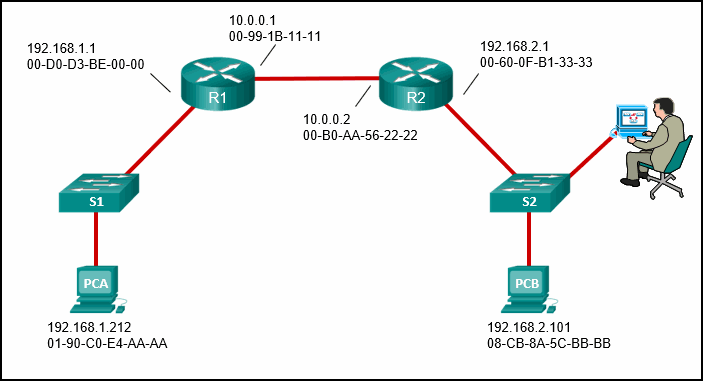
Src IP: 192.168.2.1
Src MAC: 00-60-0F-B1-33-33
Dst IP: 192.168.2.101
Dst MAC: 08-CB-8A-5C-BB-BB
Src IP: 192.168.1.212
Src MAC: 00-60-0F-B1-33-33
Dst IP: 192.168.2.101
Dst MAC: 00-D0-D3-BE-00-00
Src IP: 192.168.1.212
Src MAC: 00-60-0F-B1-33-33
Dst IP: 192.168.2.101
Dst MAC: 08-CB-8A-5C-BB-BB
Src IP: 192.168.1.212
Src MAC: 01-90-C0-E4-AA-AA
Dst IP: 192.168.2.101
Dst MAC: 08-CB-8A-5C-BB-BB
Explanation: When a message sent from PCA to PCB reaches router R2, some frame header fields will be rewritten by R2 before forwarding to switch S2. The frames will contain the source MAC address of router R2 and the destination MAC address of PCB. The frames will retain the original IPv4 addressing applied by PCA which is the IPv4 address of PCA as the source address and the IPv4 address of PCB as the destination.
6. Which tool can be used in a Cisco AVC system to analyze and present the application analysis data into dashboard reports?
- NetFlow
- NBAR2
- Prime
- IPFIX
Explanation: A management and reporting system, such as Cisco Prime, can be used to analyze and present the application analysis data into dashboard reports for use by network monitoring personnel.
- TCP Wrapper
- Windows Firewall
- nftables
- iptables
Explanation: Windows Firewall uses a profile-based approach to configuring firewall functionality. It uses three profiles, Public, Private, and Domain, to define firewall functions.
- to provide statistics on packets that are flowing through a Cisco device
- to select the type of logging information that is captured
- to specify the destinations of captured messages
- to periodically poll agents for data
- to gather logging information for monitoring and troubleshooting
- to provide traffic analysis
Explanation: There are three primary functions provided by the syslog service:
1. gathering logging information
2. selection of the type of information to be logged
3. selection of the destination of the logged information
- Allow users to re-use old passwords.
- Force periodic password changes.
- Allow USB auto-detection.
- Allow default services to remain enabled.
Explanation: The basic best practices for device hardening are as follows:
Ensure physical security.
Minimize installed packages.
Disable unused services.
Use SSH and disable the root account login over SSH.
Keep the system updated.
Disable USB auto-detection.
Enforce strong passwords.
Force periodic password changes.
Keep users from re-using old passwords.
Review logs regularly.
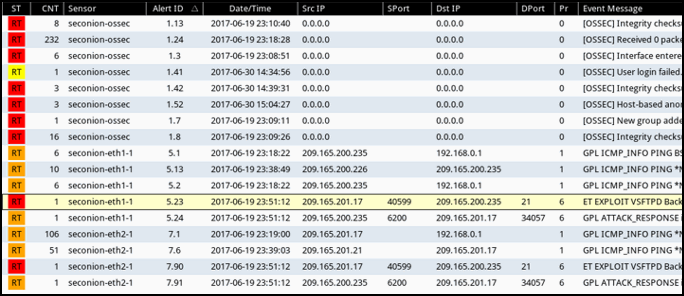
Explanation: The CNT field indicates the number of times an event is detected from the same source and destination IP address. Having a high number of events can indicated a problem with event signatures.
- access
- accounting
- authorization
- authentication
Explanation: The three parts of the AAA process are authentication, authorization, and accounting. The accounting function records information such as who logged in, when the user logged in and out, and what the user did with network resources.
- Coordinate the incident response with other stakeholders and minimize the damage of the incident.
- Review the incident policies, plans, and procedures for local or federal guideline violations.
- Perform actions to minimize the effectiveness of the attack and preserve evidence.
- Perform disciplinary measures if an incident is caused by an employee.
Explanation: IT support best understands the technology used in the organization and can perform the correct actions to minimize the effectiveness of the attack and preserve evidence.
- X Window System
- launcher
- package manager
- penetration tool
Explanation: A package is a specific program and all of the files needed to run that program. A package manager is used to install a package and place all the associated files in the correct location within the operating system.
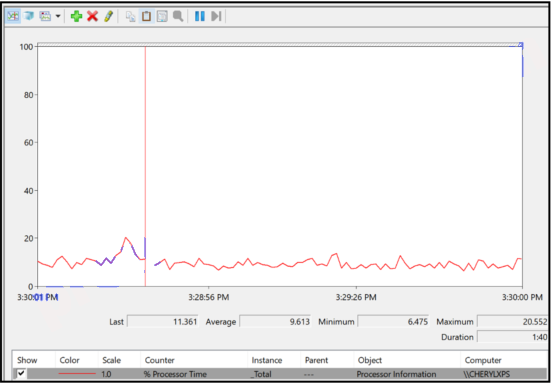
- ARP cache poisoning
- DNS attack
- TCP attack
- malware
Explanation: Windows Performance Monitor is used to evaluate the performance of individual components on a Windows host computer. Commonly monitored components include the processor, hard drive, network, and memory. Windows Task Manager and Performance Monitor are used when malware is suspected and a component is not performing the way it should.
- Use a VPN between a syslog client and the syslog server.
- Use syslog-ng.
- Use a Linux-based server.
- Create an ACL that permits only TCP traffic to the syslog server.
Explanation: Hackers may try to block clients from sending data to the syslog server, manipulate or erase logged data, or manipulate the software used to transmit messages between the clients and the server. Syslog-ng is the next generation of syslog and it contains improvements to prevent some of the exploits.
Explanation: SQL is the language used to query a relational database. Cybercriminals use SQL injections to get information, create fake or malicious queries, or to breach the database in some other way.
- Clients receive IP address assignments from a rogue DHCP server.
- Legitimate clients are unable to lease IP addresses.
- The IP addresses assigned to legitimate clients are hijacked.
- The attacker provides incorrect DNS and default gateway information to clients.
Explanation: DCHP starvation attacks are launched by an attacker with the intent to create a DoS for DHCP clients. To accomplish this goal, the attacker uses a tool that sends many DHCPDISCOVER messages to lease the entire pool of available IP addresses, thus denying them to legitimate hosts.
- A DoS attack has been launched against the network.
- The computers are subject to a reconnaissance attack.
- A virus has infected the computers.
- An access attack has occurred.
Explanation: A virus such as this is harmless, but still needs to be removed. Other viruses can be destructive in that they modify or delete files on the local computer and possibly other computers on the network.
- trust exploitation
- port redirection
- reconnaissance
- denial of service
Explanation: Wireshark is a free download that allows network packet inspection. Someone using this tool for malicious intent would be performing a reconnaissance attack. Through the capture of network packets, weak security network connectivity protocols such as Telnet can be caught, inspected, and then analyzed for detailed network information, including passwords.
- Darknet
- Snort
- Bitcoin
- BitTorrent
- Wireshark
Explanation: Bitcoin is used to share a distributed database or ledger. BitTorrent is used for file sharing.
- Header Length
- Differentiated Services
- Time-to-Live
- Fragment Offset
Explanation: When a router receives a packet, the router will decrement the Time-to-Live (TTL) field by one. When the field reaches zero, the receiving router will discard the packet and will send an ICMP Time Exceeded message to the sender.
- facility
- severity
- header
- hostname
- timestamp
Explanation: The PRI in a syslog message consists of two elements, the facility and severity of the message.
- cyber kill chain
- playbook
- rootkit
- chain of custody
Explanation: A playbook is an automated query that can add efficiency to the cyberoperations workflow.
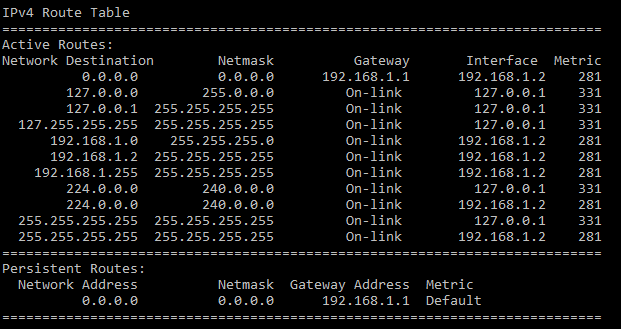
- 127.0.0.1
- 192.168.1.2
- 192.168.1.1
- 192.168.1.255
Explanation: The default gateway setting is the IP address of the router to which the host will send packets that are destined for remote networks. In the routing table of a PC, the gateway address is the default gateway and must be on the same logical network as the host IP address, in this case 192.168.1.0. Thus the gateway address, which must be on the 192.168.1.0 network, is 192.168.1.1.
- Decrease the wireless antenna gain level.
- Only turn on Wi-Fi when using the wireless network.
- Use wireless MAC address filtering.
- Only allow devices that have been approved by the corporate IT team.
- Keep the device OS and software updated.
- Use paint that reflects wireless signals and glass that prevents the signals from going outside the building.
Explanation: Many companies now support employees and visitors attaching and using wireless devices that connect to and use the corporate wireless network. This practice is known as a bring-your-own-device policy or BYOD. Commonly, BYOD security practices are included in the security policy. Some best practices that mitigate BYOD risks include the following:Use unique passwords for each device and account.
Turn off Wi-Fi and Bluetooth connectivity when not being used. Only connect to trusted networks.
Keep the device OS and other software updated.
Backup any data stored on the device.
Subscribe to a device locator service with a remote wipe feature.
Provide antivirus software for approved BYODs.
Use Mobile Device Management (MDM) software that allows IT teams to track the device and implement security settings and software controls.
- forwarding traffic and physical layer errors to an analysis device
- providing 24×7 statistics on packets flowing through a Cisco router or multilayer switch
- monitoring traffic and comparing it against the configured rules
- providing reporting and analysis of security events
Explanation: SIEM provides real-time reporting and analysis of security events. SIEM provides administrators with details on sources of suspicious activity such as user information, device location, and compliance with security policies.
- If a public key is used to encrypt the data, a public key must be used to decrypt the data.
- If a private key is used to encrypt the data, a private key must be used to decrypt the data.
- Public and private keys may be used interchangeably.
- If a private key is used to encrypt the data, a public key must be used to decrypt the data.
- If a public key is used to encrypt the data, a private key must be used to decrypt the data.
Explanation: Asymmetric algorithms use two keys: a public key and a private key. Both keys are capable of the encryption process, but the complementary matched key is required for decryption. If a public key encrypts the data, the matching private key decrypts the data. The opposite is also true. If a private key encrypts the data, the corresponding public key decrypts the data.
- It identifies the steps that adversaries must complete to accomplish their goals.
- It specifies common TCP/IP protocols used to fight against cyberattacks.
- It is a set of metrics designed to create a way to describe security incidents in a structured and repeatable way.
- It uses the OSI model to describe cyberattacks at each of the seven layers.
Explanation: The Cyber Kill Chain was developed to identify and prevent cyber intrusions by specifying what threat actors must complete to accomplish their goals.
- Worms are more network-based than viruses are.
- Worms are not detected by antivirus programs.
- Worms run within a host program.
- Worms directly attack the network devices.
Explanation: One major component of a worm is the propagation mechanism which replicates the worm and targets unprotected network devices. A virus requires a host program, but worms do not.
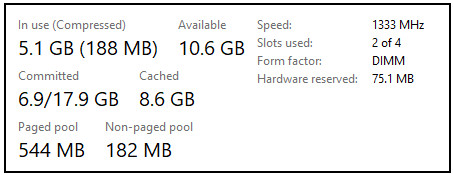
Explanation: The graphic shows that there is 5.0 GB (187 MB) of memory in use with 10.7 GB still available. Together this adds up to 16 GB of total physical memory. 5 GB is approximately 33% of 16 GB.

Explanation: For the Linux tail command, the option -f is used to monitor a file for changes. The -c option is used to limit the number of bytes shown. The -n option is used to set the number of lines to display. The -q option is used to suppress the header line.
- nonrepudiation of the transaction
- confidentiality of the public key
- integrity of digitally signed data
- authenticity of digitally signed data
Explanation: Digital signatures provide three basic security services:Authenticity of digitally signed data – Digital signatures authenticate a source, proving that a certain party has seen and signed the data in question.
Integrity of digitally signed data – Digital signatures guarantee that the data has not changed from the time it was signed.
Nonrepudiation of the transaction – The recipient can take the data to a third party, and the third party accepts the digital signature as a proof that this data exchange did take place. The signing party cannot repudiate that it has signed the data.
- origin authentication
- data integrity
- nonrepudiation
- data confidentiality
Explanation: Secure communications consists of four elements:
Data confidentiality – guarantees that only authorized users can read the message
Data integrity – guarantees that the message was not altered
Origin authentication – guarantees that the message is not a forgery and does actually come from whom it states
Data nonrepudiation – guarantees that the sender cannot repudiate, or refute, the validity of a message sent
- to secure the exchange of keys used to encrypt data
- to create password hashes for secure authentication
- to encrypt data for secure e-commerce communications
- to provide routing protocol authentication between routers
Explanation: Diffie-Helman is not an encryption mechanism and is not typically used to encrypt data. Instead, it is a method to securely exchange the keys used to encrypt the data.
- Trusted automated exchange of indicator information (TAXII)
- Structured threat information expression (STIX)
- Common vulnerabilities and exposures (CVE)
- Automated indicator sharing (AIS)
Explanation: The two common threat intelligence sharing standards are as follows:
Structured Threat Information Expression (STIX) – This is a set of specifications for exchanging cyberthreat information between organizations. The Cyber Observable Expression (CybOX) standard has been incorporated into STIX.
Trusted Automated Exchange of Indicator Information (TAXII) – This is the specification for an application layer protocol that allows the communication of CTI over HTTPS. TAXII is designed to support STIX.
- Diamond
- Cyber Kill Chain
- CSIRT
- VERIS
Explanation: Vocabulary for Event Recording and Incident Sharing (VERIS) is a set of metrics designed to create a way to describe security incidents in a structured or repeatable way. A Computer Security Incident response Team (CSIRT) is an internal organizational group that provides services and functions to secure assets. Cyber Kill Chain contains seven steps which help analysts understand the techniques, tools, and procedures of threat actors. The Diamond Model of intrusion has four parts that represent a security incident.
- shell
- command interpreter
- kernel
- command line interface
Explanation: A Linux OS can be divided into kernel and shell. The shell, also called the command line interface, is a command interpreter that parses the inputs (or commands) from a user and interacts with the kernel. The kernel, in turn, interacts with the hardware components of a device.
Explanation: Port numbers are used in TCP and UDP communications to differentiate between the various services running on a device. The well-known port number used by HTTPs is port 443.
- a historical list of successful pings that have been sent
- a local routing table
- a network connection and usage report
- a list of all established active TCP connections
Explanation: When used by itself (without any options), the netstat command will display all the active TCP connections that are available.
- by listing results of user web surfing activities
- by displaying alert messages that are generated by Snort
- by comparing normal network behavior to current network behavior
- by recording conversations between network endpoints
Explanation: Statistical data is created through the analysis of other forms of network data. Statistical characteristics of normal network behavior can be compared to current network traffic in an effort to detect anomalies. Conclusions resulting from analysis can be used to describe or predict network behavior.
- INTERNET
- INPUT
- OUTPUT
- FORWARD
Explanation: The firewall iptables uses the concepts of chains and rules to filter traffic:
INPUT chain – handles traffic entering the firewall and destined to the firewall device itself
OUTPUT chain – handles traffic originating within the firewall device itself and destined to somewhere else
FORWARD chain – handles traffic originated somewhere else and passing through the firewall device
- to develop advanced network devices
- to protect cloud-based data centers
- to gain advantage over adversaries
- to simulate possible war scenarios among nations
Explanation: Cyberwarfare is Internet-based conflict that involves the penetration of the networks and computer systems of other nations. The main purpose of cyberwarfare is to gain advantage over adversaries, whether they are nations or competitors.
- to check the length of key used for the digital certificate
- to negotiate the best encryption to use
- to verify the validity of the digital certificate
- to request the CA self-signed digital certificate
Explanation: A digital certificate must be revoked if it is invalid. CAs maintain a certificate revocation list (CRL), a list of revoked certificate serial numbers that have been invalidated. The user browser will query the CRL to verify the validity of a certificate.
- By default, both the administrator and guest accounts are enabled.
- By default, both the administrator and guest accounts are disabled.
- By default, the administrator account is enabled but the guest account is disabled.
- By default, the guest account is enabled but the administrator account is disabled.
Explanation: When a user installs Windows desktop version, two local user accounts are created automatically during the process, administrator and guest. Both accounts are disabled by default.
- Malware that executes arbitrary code and installs copies of itself in memory.
- A self-replicating attack that is independently launched.
- Malware that relies on the action of a user or a program to activate.
- Program code specifically designed to corrupt memory in network devices.
- Malicious code that can remain dormant before executing an unwanted action.
Explanation: A virus is malicious code that is attached to legitimate programs or executable files. Most viruses require end user activation, can lie dormant for an extended period, and then activate at a specific time or date. In contrast, a worm executes arbitrary code and installs copies of itself in the memory of the infected computer. The main purpose of a worm is automatic replication to spread quickly across a network. A worm does not require a host program to run.
- Use the Add or Remove Programs utility to set program access and defaults.
- Uninstall the program and then choose Add New Programs in the Add or Remove Programs utility to install the application.
- Set the application registry key value to one.
- Change the startup type for the utility to Automatic in Services.
Explanation: The Services console in Windows OS allows for the management of all the services on the local and remote computers. The setting of Automatic in the Services console enables the chosen service to start when the computer is started.
- Task Manager
- Event Viewer
- PowerShell
- Performance Monitor
Explanation: Event Viewer is used to investigate the history of application, security, and system events. Events show the date and time that the event occurred along with the source of the event. If a cybersecurity analyst has the address of the Windows computer targeted or the date and time that a security breach occurred, the analyst could use Event Viewer to document and prove what occurred on the computer.
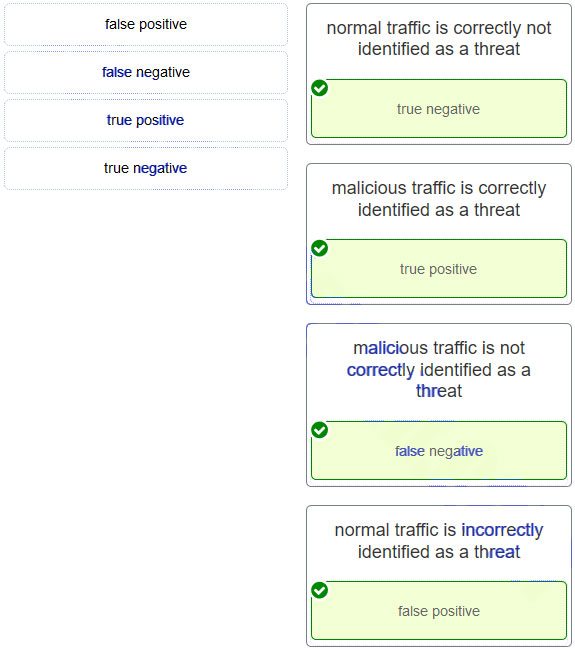
- true positive
- false positive
- true negative
- false negative
Explanation: Sguil includes seven pre-built categories that can be assigned to events that have been identified as true positives.
- destination MAC address
- destination IP address
- source MAC address
- source IP address
Explanation: A switch is a Layer 2 device that uses source MAC addresses to build a MAC address table (a CAM table) and destination MAC addresses to forward frames.
- Trusted automated exchange of indicator information (TAXII)
- Structured threat information expression (STIX)
- Common vulnerabilities and exposures (CVE)
- Automated indicator sharing (AIS)
Explanation: The two common threat intelligence sharing standards are as follows:
Structured Threat Information Expression (STIX) – This is a set of specifications for exchanging cyberthreat information between organizations. The Cyber Observable Expression (CybOX) standard has been incorporated into STIX.
Trusted Automated Exchange of Indicator Information (TAXII) – This is the specification for an application layer protocol that allows the communication of CTI over HTTPS. TAXII is designed to support STIX.
51. Refer to the exhibit. A network security analyst is examining captured data using Wireshark. What is represented by the first three frames?
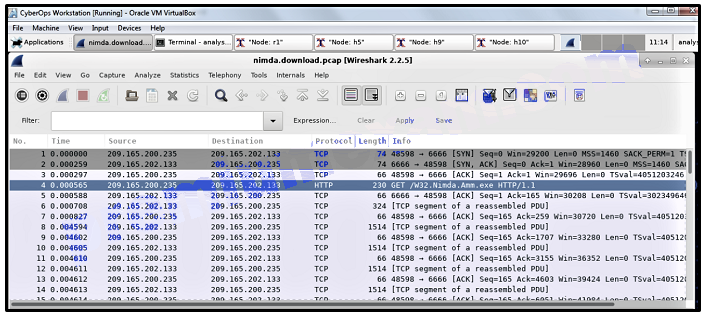
- request of a file from the client
- TCP three-way handshake
- UDP DNS request
- connectivity test between two hosts
Explanation: The first three frames consist of the SYN, SYN/ACK, and ACK exchanges that constitute the TCP three-way handshake between the two hosts.
- social engineering
- adware
- phishing
- DDoS
- spyware
Explanation: Phishing, spyware, and social engineering are security attacks that collect network and user information. Adware consists, typically, of annoying popup windows. Unlike a DDoS attack, none of these attacks generate large amounts of data traffic that can restrict access to network services.
Explanation: A /26 prefix gives 6 host bits, which provides a total of 64 addresses, because 26 = 64. Subtracting the network and broadcast addresses leaves 62 usable host addresses.
- fast flux
- ARP poisoning
- resource utilization
- cushioning
- amplification and reflection
Explanation: Three types of attacks used on DNS open resolvers are as follows:DNS cache poisoning – attacker sends spoofed falsified information to redirect users from legitimate sites to malicious sites
DNS amplification and reflection attacks – attacker sends an increased volume of attacks to mask the true source of the attack
DNS resource utilization attacks – a denial of service (DoS) attack that consumes server resources
- authentication
- repudiation
- availability
- accounting
- authorization
- access
Explanation: This question refers to AAA authentication, authorization, and accountability.
- Audit endpoints to discover abnormal file creations.
- Establish an incident response playbook.
- Use HIPS to alert or place a block on common installation paths.
- Consolidate the number of Internet points of presence.
- Conduct damage assessment.
Explanation: In the installation phase of the Cyber Kill Chain, the threat actor establishes a back door into the system to allow for continued access to the target. Among other measures, using HIPS to alert or block on common installation paths and auditing endpoints to discover abnormal file creations can help block a potential back door creation.
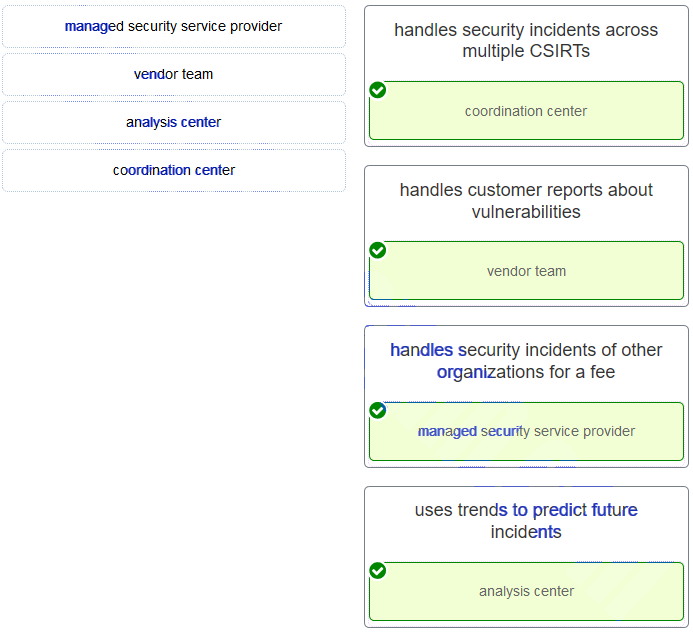
57. Match the type of CSIRT with the description.
58. Match the IPS alarm with the description.
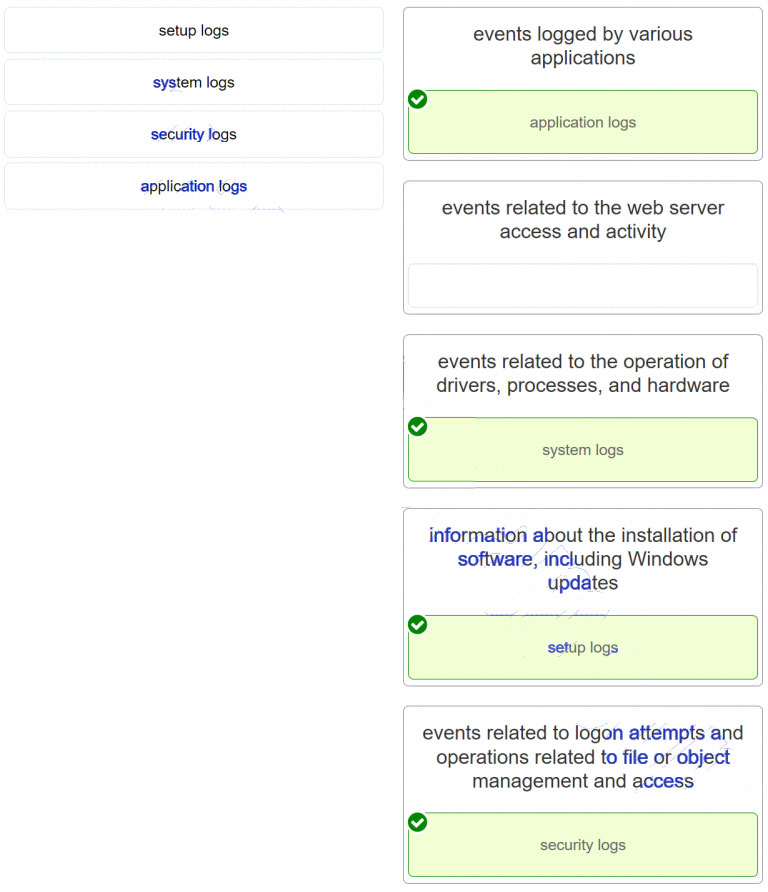
59. Match the Windows host log to the messages contained in it. (Not all options are used.)
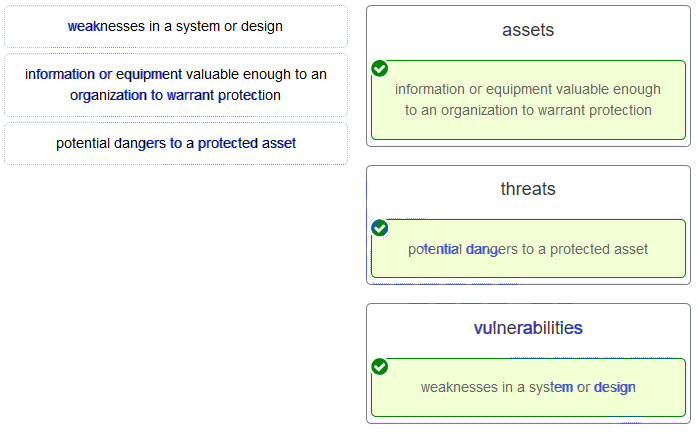
60. Match the term to the description.
61. Match the server profile element to the description. (Not all options are used.)
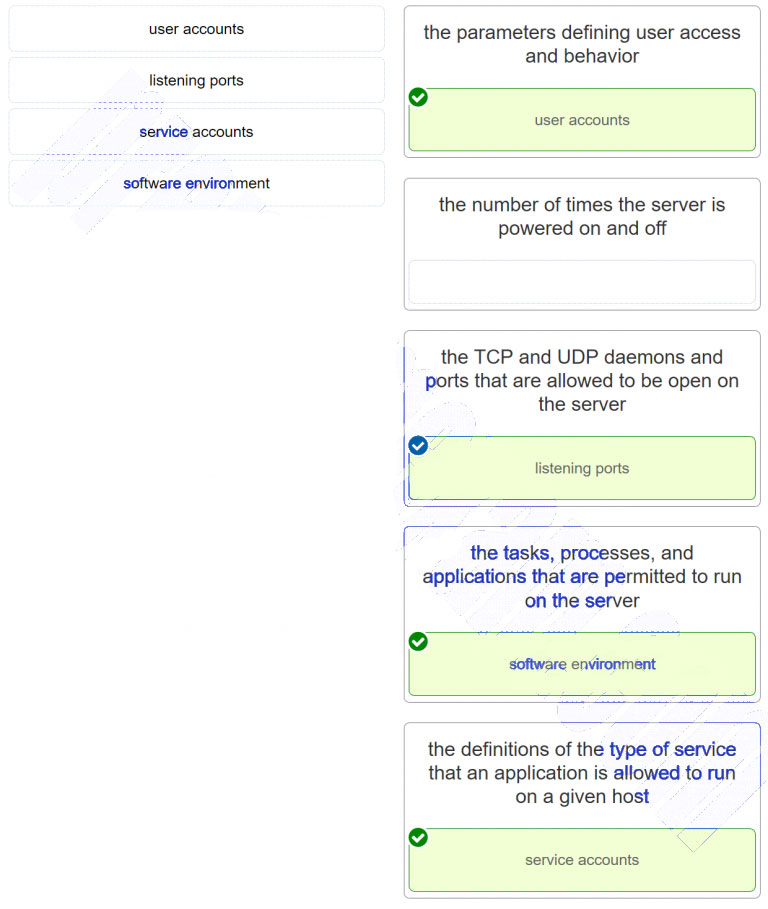
Explanation: The elements of a server profile include the following:Listening ports – the TCP and UDP daemons and ports that are allowed to be open on the server
User accounts – the parameters defining user access and behavior
Service accounts – the definitions of the type of service that an application is allowed to run on a given host
Software environment – the tasks, processes, and applications that are permitted to run on the server












