1. Which NIST-defined incident response stakeholder is responsible for coordinating incident response with other stakeholders and minimizing the damage of an incident?
- human resources
- IT support
- the legal department
- management
2. What is defined in the policy element of the NIST incident response plan?
- how to handle incidents based on the mission and functions of an organization
- a roadmap for updating the incident response capability
- the metrics used for measuring incident response capability in an organization
- how the incident response team of an organization will communicate with organization stakeholders
3. Which three IPv4 header fields have no equivalent in an IPv6 header? (Choose three.)
- flag
- identification
- TTL
- fragment offset
- version
- protocol
4. What will a threat actor do to create a back door on a compromised target according to the Cyber Kill Chain model?
- Add services and autorun keys.
- Obtain an automated tool to deliver the malware payload.
- Open a two-way communications channel to the CnC infrastructure.
- Collect and exfiltrate data.
5. Refer to the exhibit. A security specialist is checking if files in the directory contain ADS data. Which switch should be used to show that a file has ADS attached?
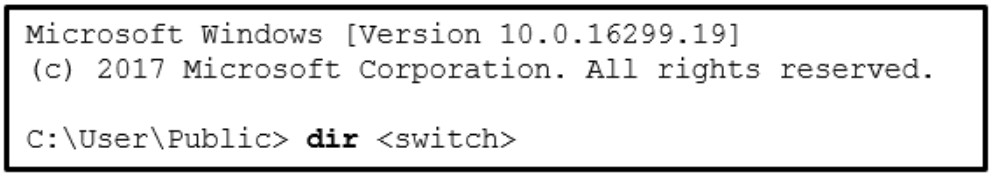
- /a
- /r
- /s
- /d
6. What is the responsibility of the human resources department when handing a security incident as defined by NIST?
- Review the incident policies, plans, and procedures for local or federal guideline violations.
- Perform disciplinary actions if an incident is caused by an employee.
- Coordinate the incident response with other stakeholders and minimize the damage of an incident.
- Perform actions to minimize the effectiveness of the attack and preserve evidence.
7. In which top-level element of the VERIS schema does VERIS use the A4 threat model to describe an incident?
- incident tracking
- incident description
- discovery and response
- impact assessment
8. A company is applying the NIST.SP800-61 r2 incident handling process to security events. What are two examples of incidents that are in the category of precursor? (Choose two.)
- multiple failed logins from an unknown source
- log entries that show a response to a port scan
- an IDS alert message being sent
- a newly-discovered vulnerability in Apache web servers
- a host that has been verified as infected with malware
9. What is a goal of deploying an in-line security device that can analyze data as a normalized stream?
- reduce the amount of event data
- satisfy compliance requirements
- detect and block intrusions
- decrease network latency and jitter
10. What is the VERIS Community Database (VCDB)?
- a collection of research of trend and potential security intrusions
- a central location for the security community to learn from experience and help with decision making before, during, and after a security incident
- a collection of incident data collected and categorized by a selected group of cybersecurity professionals
- an open and free collection of publicly-reported security incidents posted in a variety of data formats
11. According to the Cyber Kill Chain model, after a weapon is delivered to a targeted system, what is the next step that a threat actor would take?
- action on objectives
- exploitation
- weaponization
- installation
12. Which metric in the CVSS Base Metric Group is used with an attack vector?
- the determination whether the initial authority changes to a second authority during the exploit
- the presence or absence of the requirement for user interaction in order for an exploit to be successful
- the proximity of the threat actor to the vulnerability
- the number of components, software, hardware, or networks, that are beyond the control of the attacker and that must be present in order for a vulnerability to be successfully exploited
13.Which statement describes the card verification value (CVV) for a credit card?
- It is the credit card account number.
- It is a security feature of the card.
- It is a PIN number for the card.
- It is the bank account number.
14.Which three fields are found in both the TCP and UDP headers? (Choose three.)
- window
- checksum
- options
- sequence number
- destination port
- source port
15. Which specification provides a common language for describing security incidents in a structured and repeatable way?
- VERIS schema
- Cyber Kill Chain
- NIST Incident Response Life Cycle
- Diamond model
16. What is the responsibility of the IT support group when handing an incident as defined by NIST?
- reviews the incident policies, plans, and procedures for local or federal guideline violations
- performs actions to minimize the effectiveness of the attack and preserve evidence
- coordinates the incident response with other stakeholders and minimizes the damage of an incident
- performs disciplinary measures if an incident is caused by an employee
17. During the detection and analysis phase of the NIST incident response process life cycle, which sign category is used to describe that an incident might occur in the future?
- attrition
- impersonation
- precursor
- indicator
18. After a security monitoring tool identifies a malware attachment entering the network, what is the benefit of performing a retrospective analysis?
- It can calculate the probability of a future incident.
- It can identify how the malware originally entered the network.
- It can determine which network host was first affected.
- A retrospective analysis can help in tracking the behavior of the malware from the identification point forward.
19. Which field in the IPv6 header points to optional network layer information that is carried in the IPv6 packet?
- flow label
- version
- traffic class
- next header
20. Refer to the exhibit. A security analyst issues the cat command to review the content of the file confidential2. Which encoding method was used to encode the file?
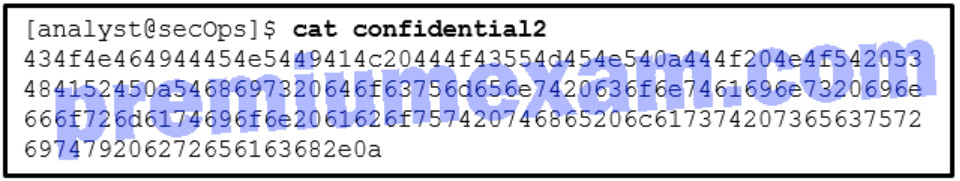
- 8-bit binary
- ASCII
- Hex
- Base64
21. How much overhead does the TCP header add to data from the application layer?
- 8 bytes
- 16 bytes
- 20 bytes
- 40 bytes
22. In which step of the NIST incident response process does the CSIRT perform an analysis to determine which networks, systems, or applications are affected; who or what originated the incident; and how the incident is occurring?
- incident notification
- scoping
- attacker identification
- detection
23. Refer to the exhibit. Which techology generated the event log?

- web proxy
- NetFlow
- syslog
- Wireshark
24. When a server profile for an organization is being established, which element describes the TCP and UDP daemons and ports that are allowed to be open on the server?
- listening ports
- service accounts
- critical asset address space
- software environment
25. Refer to the exhibit. A network administrator is examining a NetFlow record. Why would the record indicate that both TRNS SOURCE PORT and TRNS DESTINATION PORT are 0?
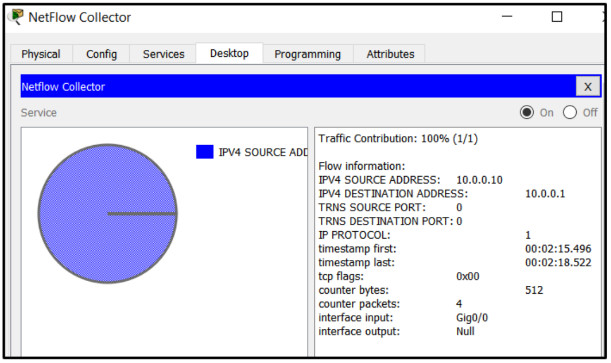
- The flow contains four packets and they use varying port numbers.
- The flow does not include transport layer protocols.
- The Gig0/0 interface has not transmitted any packets.
- The source host uses a different transport layer protocol from the one used by the destination host.
26. When establishing a server profile for an organization, which element describes the type of service that an application is allowed to run on the server?
- listening port
- user account
- software environment
- service account
27. Refer to the exhibit. A security specialist is using Wireshark to review a PCAP file generated by tcpdump . When the client initiated a file download request, which source socket pair was used?
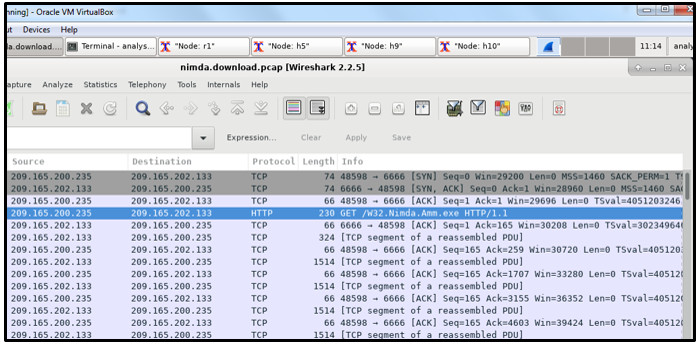
- 209.165.202.133:6666
- 209.165.200.235:6666
- 209.165.202.133:48598
- 209.165.200.235:48598
28. A cybersecurity analyst is performing a CVSS assessment on an attack where a web link was sent to several employees. Once clicked, an internal attack was launched. Which CVSS Base Metric Group Exploitability metric is used to document that the user had to click on the link in order for the attack to occur?
- integrity requirement
- availability requirement
- user interaction
- scope
29. What is the benefit of converting log file data into a common schema?
- creates a data model based on fields of data from a source
- allows the implementation of partial normalization and inspection
- allows easy processing and analysis of datasets
- creates a set of regex-based field extractions
30. What are the three impact metrics contained in the CVSS 3.0 Base Metric Group? (Choose three.)
- integrity
- remediation level
- confidentiality
- exploit
- attack vector
- availability
31. Which type of analysis relies on different methods to establish the likelihood that a security event has happened or will happen?
- deterministic
- statistical
- log
- probabilistic
32. When establishing a network profile for an organization, which element describes the time between the establishment of a data flow and its termination?
- routing protocol convergence
- session duration
- bandwidth of the Internet connection
- total throughput
33. When attempting to improve system performance for Linux computers with a limited amount of memory, why is increasing the size of the swap file system not considered the best solution?
- A swap file system cannot be mounted on an MBR partition.
- A swap file system only supports the ex2 file system.
- A swap file system does not have a specific file system.
- A swap file system uses hard disk space to store inactive RAM content.
34. What will match the regular expression ^83?
- any string that includes 83
- any string that begins with 83
- any string with values greater than 83
- any string that ends with 83
35. Which type of evidence cannot prove an IT security fact on its own?
- best
- corroborative
- indirect
- hearsay
36. Which type of computer security incident response team is responsible for determining trends to help predict and provide warning of future security incidents?
- coordination centers
- analysis centers
- vendor teams
- national CSIRT
37. Which two actions should be taken during the preparation phase of the incident response life cycle defined by NIST? (Choose two.)
- Fully analyze the incident.
- Meet with all involved parties to discuss the incident that took place.
- Detect all the incidents that occurred.
- Acquire and deploy the tools that are needed to investigate incidents.
- Create and train the CSIRT
38. Which technology is used by Cisco Advanced Malware Protection (AMP) in defending and protecting against known and emerging threats?
- threat intelligence
- network admission control
- network profiling
- website filtering and blacklisting
39. Which two actions can help identify an attacking host during a security incident? (Choose two.)
- Use an Internet search engine to gain additional information about the attack.
- Log the time and date that the evidence was collected and the incident remediated.
- Determine the location of the recovery and storage of all evidence.
- Validate the IP address of the threat actor to determine if it is viable.
- Develop identifying criteria for all evidence such as serial number, hostname, and IP address
40. What classification is used for an alert that correctly identifies that an exploit has occurred?
- false negative
- false positive
- true positive
- true negative
41. Which type of analysis relies on predefined conditions and can analyze applications that only use well-known fixed ports?
- statistical
- deterministic
- log
- probabilistic
42. What are security event logs commonly based on when sourced by traditional firewalls?
- application analysis
- static filtering
- signatures
- 5-tuples
43. Using Tcpdump and Wireshark, a security analyst extracts a downloaded file from a pcap file. The analyst suspects that the file is a virus and wants to know the file type for further examination. Which Linux command can be used to determine the file type?
- file
- tail
- nano
- ls -l
44. Which three things will a threat actor do to prepare a DDoS attack against a target system on the Internet? (Choose three.)
- Install a black door on the target system.
- Collect and exfiltrate data.
- Compromise many hosts on the Internet.
- Obtain an automated tool to deliver the malware payload.
- Establish two-way communications channels to the CnC infrastructure with zombies.
- Install attack software on zombies.
45. After containing an incident that infected user workstations with malware, what are three effective remediation procedures that an organization can take for eradication? (Choose three.)
- Change assigned names and passwords for all devices.
- Update and patch the operating system and installed software of all hosts.
- Rebuild hosts with installation media if no backups are available.
- Rebuild DHCP servers using clean installation media.
- Disconnect or disable all wired and wireless network adapters until the remediation is complete.
- Use clean and recent backups to recover hosts.
46. A cybersecurity analyst has been called to a crime scene that contains several technology items including a computer. Which technique will be used so that the information found on the computer can be used in court?
- rootkit
- log collection
- unaltered disk image
- Tor
47. What is specified in the plan element of the NIST incident response plan?
- incident handling based on the mission of the organization
- organizational structure and the definition of roles, responsibilities, and levels of authority
- priority and severity ratings of incidents
- metrics for measuring the incident response capability and effectiveness
48. A network administrator is creating a network profile to generate a network baseline. What is included in the critical asset address space element?
- the TCP and UDP daemons and ports that are allowed to be open on the server
- the IP addresses or the logical location of essential systems or data
- the list of TCP or UDP processes that are available to accept data
- the time between the establishment of a data flow and its termination
49. What are two sources of data in the operation of a security information and event management (SIEM) system? (Choose two.)
- firewalls
- dashboards and reports
- antimalware devices
- automation and alerts
- incident management systems
50. What are two of the 5-tuples? (Choose two.)
- IPS
- source port
- IDS
- ACL
- protocol
51. Refer to the exhibit. A network administrator is examining a NetFlow record. Which protocol is in use in the flow shown?
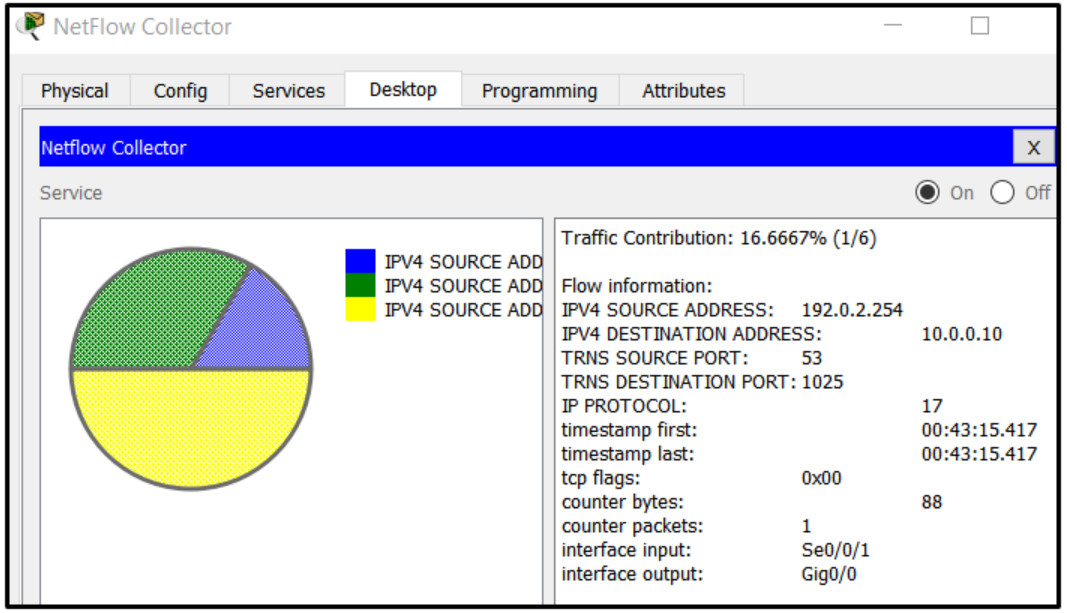
- UDP
- ICMP
- TCP
- HTTP
52. When real-time reporting of security events from multiple sources is being received, which function in SIEM provides capturing and processing of data in a common format?
- aggregation
- log collection
- normalization
- compliance
53. What is the role of vendor teams as they relate to a computer security incident response team?
- They handle customer reports concerning security vulnerabilities.
- They provide incident handling to other organizations as a fee-based service.
- They coordinate incident handling across multiple teams.
- They use data from many sources to determine incident activity trends.
54. At the request of investors, a company is proceeding with cyber attribution with a particular attack that was conducted from an external source. Which security term is used to describe the person or device responsible for the attack?
- threat actor
- fragmenter
- tunneler
- skeleton
55. What are three of the four interactive landscapes that VERIS schema use to define risk?
- response
- evidence
- attack
- threat
- impact
- control
New Questions for 210-255 Exam (Dump)
1. Which data element must be protected with regards to PCI?
- past health condition
- geographic location
- full name / full account number >>>> full name <<< Came in the exam only
- recent payment amount
2. What is Data mapping used for? (Choose two)
- data accuracy(integrity)
- data availability
- data normalization
- data confidentiality
- data visualization
3. Drag and drop the type of evidence from the left onto the correct description(s) of that evidence on the right.

Correct Answer:
Corroborative evidence – NetFlow based spike in DNS traffic
Indirect evidence – firewall log showing successful communication and threat intelligence stating an IP is known to host malware
Direct evidence – log that shows a command and control check-in from verified malware
4. Which of the following steps in the kill chain would come before the others?
- C2
- Delivery
- Installation
- Exploitation
5. In the context of incident handling phases, which two activities fall under scoping? (Choose two.)
- determining the number of attackers that are associated with a security incident
- ascertaining the number and types of vulnerabilities on your network
- identifying the extent that a security incident is impacting protected resources on the network
- determining what and how much data may have been affected
- identifying the attackers that are associated with a security incident
6. What does the CSIRT incident response provider usually do?
- provide incident handling services to their parent organization.
- provide incident handling services to a country
- coordinate and facilitate the handling of incidents across various CSIRTs
- focus on synthesizing data from various sources to determine trends and patterns in incident activity
- handle reports of vulnerabilities in their software or hardware products
- offer incident handling services as a for-fee service to other organizations
7. Which process is being utilized when IPS events are removed to improve data integrity?
- data normalization
- data availability
- data protection
- data signature
8. According to NIST what option is unnecessary for containment strategy?
- The delayed containment
- Monitoring with methods other than sandboxing
9. What is the difference between deterministic and probabilistic assessment method?
- At deterministic method we know the facts beforehand and at probabilistic method we make assumptions
- At probabilistic method we know the facts beforehand and at deterministic method we make assumptions
- Probabilistic method has an absolute nature
- Deterministic method has an absolute nature
10. In Microsoft Windows, as files are deleted the space they were allocated eventually is considered available for use by other files. This creates alternating used and unused areas of various sizes. What is this called?
- network file storing
- free space fragmentation
- alternate data streaming
- defragmentatio
11. When performing threat hunting against a DNS server, which traffic toward the affected domain is considered a starting point?
- HTTPS traffic
- TCP traffic
- HTTP traffic
- UDP traffic
12. Filtering ports in Wireshark?
- tcp.port == 80
- tcp port equals 80
- tcp.port 80
- port 80
13. What attribute belonging VERIS schema?
- confidentiality/possession
- integrity/authenticity
- availability/utility
14. Which of the following can be identified by correlating DNS intelligence and other security events? (Choose two)
- Communication to CnC servers
- Configuration issues
- Routing problems
- Malicious domain based on reputation
15. A CMS plugin creates two files that are accessible from the Internet myplugin.html and exploitable.php. A newly discovered exploit takes advantage of an injection vulnerability in exploitable.php. To exploit the vulnerability, one must send an HTTP POST with specific variables to exploitable.php. You see traffic to your webserver that consists of only HTTP GET requests to myplugin.html. Which category best describes this activity?
- weaponization
- exploitation
- installation
- reconnaissance
16. Which CVSSv3 Attack Vector metric value requires the attacker to physically touch or manipulate the vulnerable component?
- local
- physical
- network
- adjacent
17. During which phase of the forensic process is data that is related to a specific event labeled and recorded to preserve its integrity?
- collection
- examination
- reporting
- investigation
18. What is the definition of confidentiality according to CVSSv3 framework?
- This metric measures the impact to the confidentiality of the information resources that are managed by a software component due to a successfully exploited vulnerability.
- This metric measures the impact to integrity of a successfully exploited vulnerability. Integrity refers to the trustworthiness and veracity of information.
- This metric measures the impact to the availability of the impacted component resulting from a successfully exploited vulnerability.
19. You receive an alert for malicious code that exploits Internet Explorer and runs arbitrary code on the site visitor machine. The malicious code is on an external site that is being visited by hosts on your network. Which user agent in the HTTP headers in the requests from your internal hosts warrants further investigation?
- Mozilla/5.0 (compatible, MSIE 10.0, Windows NT 6.2, Trident 6.0)
- Mozilla/5.0 (XII; Linux i686; rv: 1.9.2.20) Gecko/20110805
- Mozilla/5.0 (Windows NT 6.1; WOW64; rv: 4O0) Gecko/20100101
- Opera/9.80 (XII; Linux i686; Ubuntu/14.10) Presto/2.12.388 Version/12.16
20. Which netstat command show ports?
- netstat -g
- netstat -l
- netstat -r
- netstat -v
21. Which identifies both the source and destination location?
- IP address
- URL
- ports
- MAC address
22. Which network device creates and sends the initial packet of a session?
- source
- origination
- destination
- network
23. Which of the following is one of the main goals of the CSIRT?
- Configure the organization’s firewall
- Monitor the organizations IPS devices
- Minimize and control the damage associated with incidents, provide guidance for mitigation and work to prevent future incidents
- Hire security professionals who will be part of the InfoSec team of the organization
24. Which goal of data normalization is true?
- Reduce data redundancy.
- Increase data redundancy.
- Reduce data availability.
- Increase data availability
25. Which of the following is not an example of reconnaissance?
- Searching the robots.txt file
- Redirecting users to a source and scanning traffic to learn about the target
- Scanning without completing the three-way handshake
- Communicating over social media
26. From a security perspective, why is it important to employ a clock synchronization protocol on a network?
- so that everyone knows the local time
- to ensure employees adhere to work schedule
- to construct an accurate timeline of events when responding to an incident
- to guarantee that updates are pushed out according to schedule
27. During which phase of the forensic process are tools and techniques used to extract the relevant information from the collective data?
- examination
- reporting
- collection
- investigation
28. Which option allows a file to be extracted from a TCP stream within Wireshark?
- File > Export Objects
- Analyze > Extract
- Tools > Export > TCP
- View > Extract
29. Drag and drop the elements of incident handling from the left into the correct order on the right.
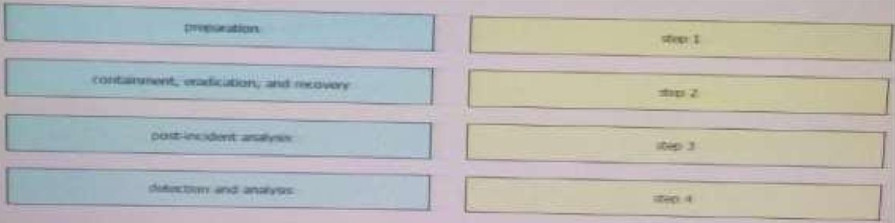
Correct Answer:
1- Preparation
2- Detection and analysis
3- Containment, eradication and recovery
4- Post incident analysis
30. Which of the following is typically a responsibility of a PSIRT (Product SIRT)?
- Configure the organization’s firewall
- Monitor security logs
- Investigate security incidents in a SOC
- Disclosure vulnerabilities in the organization’s products and services
31. Which of the following is an example of a coordination center?
- Cisco PSIRT
- Microsoft MSRC
- CERT division of the SEI
- FIRST
32. Choose the option that best describes NIST data integrity
- use only sha-1
- use only md5
- you must hash data & backup and compare hashes
- no need to hash data & backup and compare hashes
33. What is NAC?
- Non-Admin Closure
- Network Access Control
- Nepal Airline Corporations
- Network Address Control
34. Which of the following is not true about listening ports?
- A listening port is a port held open by a running application in order to accept inbound connections.
- Seeing traffic from a known port will identify the associated service.
- Listening ports use values that can range between 1 and 65535.
- TCP port 80 is commonly known for Internet traffic.
35. Which of the following are examples of some of the responsibility of a corporate CSIRT and the policies it helps create? (Choose four)
- Scanning vendor customer network
- incident classification and handling
- Information classification and protection
- Information dissemination
- Record retentions and destruction
36. Which element is included in an incident response plan?
- organization mission
- junior analyst approval
- day-to-day firefighting
- siloed approach to communications
37. Which option creates a display filter on Wireshark on a host IP address or name?
- ip.address == <address> or ip.network == <network>
- [tcp|udp] ip.[src|dst] port <port>
- ip.addr == <addr> or ip.name == <name>
- ip.addr == <addr> or ip.host == <host>
38. Which type of analysis allows you to see how likely an exploit could affect your network?
- descriptive
- casual
- probabilistic
- inferential
39. Which CSIRT category provides incident handling services to their parent organization such as a bank, a manufacturing company, a university, or afederal agency?
- internal CSIRT
- national CSIRT
- coordination centers
- analysis centers
- vendor teams
- incident response providers
40. Which regular expression matches “color” and “colour”?
- col[0-9]+our
- colo?ur
- colou?r
- ]a-z]{7}
41. Which element is part of an incident response plan?
- organizational approach to incident response
- organizational approach to security
- disaster recovery
- backups
42. Refer to the exhibit. Which type of log is this an example of?

- syslog
- NetFlow log
- proxy log
- IDS log
43. Based on nistsp800-61R2 what are the recommended protections against malware?
- Malware prevention software
44. Which option can be addressed when using retrospective security techniques?
- if the affected host needs a software update
- how the malware entered our network
- why the malware is still in our network
- if the affected system needs replacement
45. Which Security Operations Center’s goal is to provide incident handling to a country?
- Coordination Center
- Internal CSIRT
- National CSIRT
- Analysis Center
46. What protocol is related to NAC?
- 802.1Q
- 802.1X
- 802.1E
- 802.1F
47. According to NIST what option(s) should be contained in issue tracking system?
- The current status of the incident
- A summary of the incident
- Indicators related to the incident
- Other incidents related to this incident
- Actions taken by all incident handlers on this incident
- Chain of custody, if applicable
- Impact assessments related to the incident
- Contact information for other involved parties (e.g., system owners, system administrators)
- A list of evidence gathered during the incident investigation
- Comments from incident handlers
- Next steps to be taken (e.g., rebuild the host, upgrade an application).
48. According to NIST what option(s) should be contained in issue tracking system?
- inspect other incident related to the incident
49. similar to this … the same answer
Which of the following make the file unique?
- file timestamp
- file hash
- file size
50. Which of the following is one of the most used Linux file systems that has several improvements over its predecessors and that supports journaling?
- NTFS
- exFAT
- Ext5
- Ext4
51. attacker using robots.txt is under which category?
- Reconnaissance
- Weaponization
- Delivery
- Exploitation
- Installation
- Command and control (C2)
- Actions on objectives
52. What do the CSIRT incident analysis centers usually do?
- provide incident handling services to their parent organization
- provide incident handling services to a country
- coordinate and facilitate the handling of incidents across various CSIRTs
- focus on synthesizing data from various sources to determine trends and patterns in incident activity
- handle reports of vulnerabilities in their software or hardware products
- offer incident handling services as a for-fee service to other organizations
53. Refer to the exhibit. We have performed a malware detection on the Cisco website.
Which statement about the result is true?
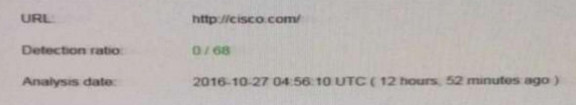
- The website has been marked benign on all 68 checks.
- The threat detection needs to run again.
- The website has 68 open threats.
- The website has been marked benign on 0 checks
54. Which element can be used by a threat actor to discover a possible opening into a target network and can also be used by an analyst to determine the protocol of the malicious traffic?
- TTLs
- ports
- SMTP replies
- IP addresses
55. Which option is a misuse variety per VERIS enumerations?
- snooping
- hacking
- theft
- assault
56. A user on your network receives an email in their mailbox that contains a malicious attachment. There is no indication that the file was run. Which category as defined in the Kill-chain model does this activity fall under?
- reconnaissance
- weaponization
- delivery
- installation
57. What is the definition of integrity according to CVSSv3 framework?
- This metric measures the impact to the confidentiality of the information resources that are managed by a software component due to a successfully exploited vulnerability.
- This metric measures the impact to integrity of a successfully exploited vulnerability. Integrity refers to the trustworthiness and veracity of information.
- This metric measures the impact to the availability of the impacted component resulting from a successfully exploited vulnerability.
58. Which of the following are not components of the 5-tuple of a flow in NetFlow? (Choose two)
- Source IP address
- Flow record ID
- Source port
- Gateway
- Destination port
59. Which netstat command show ports? (Choose two)
- netstat –a
- netstat -l >> came in the exam
- netstat -v
- netstat -g
60. Which of the following is not an example of weaponization
- Connecting to a CnC server
- Wrapping software with a RAT
- Creating backdoor in an app
- Developing an automated script to inject commands on a USB device
61.
62.
Refer to the following packet capture. Which of the following statements is true?
Exhibit:
00:00:04.549138 IP omar.cisco.com.34548 > 93.184.216.34.telnet: Flags
[S], seq 3152949738, win 29200,options [mss 1460,sackOK,TS val 1193148797 ecr 0,nop,wscale 7], length 0 00:00:05.547084 IP
omar.cisco.com.34548 > 93.184.216.34.telnet: Flags [S], seq
3152949738, win 29200, options [mss 1460,sackOK,TS val 1193149047 ecr
0,nop,wscale 7], length 0 00:00:07.551078 IP omar.cisco.com.34548 >
93.184.216.34.telnet: Flags [S], seq
3152949738, win 29200, options [mss 1460,sackOK,TS val 1193149548 ecr
0,nop,wscale 7], length 0 00:00:11.559081 IP omar.cisco.com.34548 >
93.184.216.34.telnet: Flags [S], seq
3152949738, win 29200,
options [mss 1460,sackOK,TS val 1193150550 ecr 0,nop,wscale 7], length 0
- The host with IP 93.184.216.34 is the source
- The host omar.cisco is the destination
- The server omar.cisco.com is responding to 93.184.216.34 with four packets
- This is a telnet transaction that is timing out and the server is not responding
63. What information from HTTP logs can be used to find a threat actor?
- referrer
- IP address
- user-agent
- URL
64. At which stage attacking the vulnerability belongs in Cyber kill chain?
- Reconnaissance
- Weaponization
- Delivery
- Exploitation
- Installation
- Command and control (C2)
- Actions on objectives
65. Which statement about threat actors is true?
- They are any company assets that are threatened.
- They are any assets that are threatened.
- They are perpetrators of attacks.
- They are victims of attacks.
66. Which of the following is not an example of the VERIS main schema categories?
- Incident tracking
- Victim demographics
- Incident descriptions
- Incident forensics ID
67. Which stakeholder group is responsible for containment, eradication, and recovery in incident handling?
- facilitators
- practitioners
- leaders and managers
- decision makers
68. What is accomplished in the identification phase of incident handling?
- determining the responsible user
- identifying source and destination IP addresses
- defining the limits of your authority related to a security event
- determining that a security event has occurred
69. Which option has a drastic impact on network traffic because it can cause legitimate traffic to be blocked?
- true positive
- true negative
- false positive
- false negative
70. Which string matches the regular expression r(ege)+x?
- rx
- regeegex
- r(ege)x
- rege+x
71. What is the definition of availability accord to CVSSv3 framework?
- This metric measures the impact to the confidentiality of the information resources that are managed by a software component due to a successfully exploited vulnerability.
- This metric measures the impact to integrity of a successfully exploited vulnerability. Integrity refers to the trustworthiness and veracity of information.
- This metric measures the impact to the availability of the impacted component resulting from a successfully exploited vulnerability.
72. In addition to cybercrime and attacks, evidence found on a system or network may be presented in a court of law to support accusations of crime or civil action, including which of the following?
- Fraud, money laundering, and theft
- Drug-related crime
- Murder and acts of violence
- All of the above
73. Which of the following is an example of a managed security offering where incident response experts monitor and respond to security alerts in a SOC?
- Cisco CloudLock
- Cisco’s Active Threat Analytics (ATA)
- Cisco Managed Firepower Service
- Cisco Jasper
74. Which information must be left out of a final incident report?
- server hardware configurations
- exploit or vulnerability used
- impact and/or the financial loss
- how the incident was detected
75. Which two components are included in a 5-tuple? (Choose two.)
- port number
- destination IP address
- data packet
- user name
- host logs
76. Refer to the exhibit. Drag and drop the element name from the left onto the correct piece of the NetFlow v5 record from a security event on the right.


Correct Answer:
10.232.38.20 – Source address
3120 – Bytes transmitted
80 – Source port
208.100.26.233 – Destination address
60 – Number of packets
39613 – Destination port TCP –
Protocol
77. Refer to the exhibit. You notice that the email volume history has been abnormally high. Which potential result is true?
- Email sent from your domain might be filtered by the recipient.
- Messages sent to your domain may be queued up until traffic dies down.
- Several hosts in your network may be compromised.
- Packets may be dropped due to network congestion.
78. Refer to the Exhibit. A customer reports that they cannot access your organization’s website. Which option is a possible reason that the customer cannot access the website?
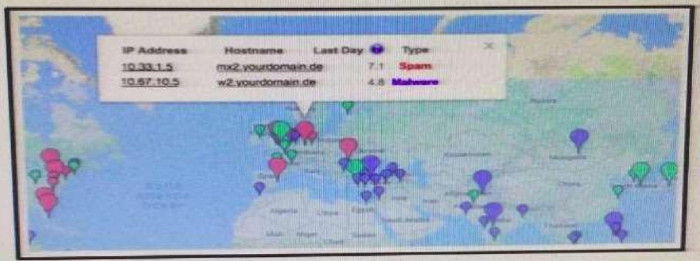
- The server at 10.33.1.5 is using up too much bandwidth causing a denial- of-service.
- The server at 10.67.10.5 has a virus.
- A vulnerability scanner has shown that 10.67.10.5 has been compromised.
- Web traffic sent from 10.67.10.5 has been identified as malicious by Internet sensors.
79. may be this came in inverse the national in choices and the answer in the … read and understand it
Which of the following are core responsibilities of a national CSIRT and CERT?
- Provide solutions for bug bounties
- Provide vulnerability brokering to vendors within a country
- Protect their citizens by providing security vulnerability info, security awareness training, best practices, and other info
- Create regulations around cybersecurity within the country
80 Which of the following are the three broad categories of cybersecurity investigations?
- Public, private, and individual investigations
- Judiciary, private, and individual investigations
- Public, private, and corporate investigations
- Government, corporate, and private investigations
81 Which component of the NIST SP800-61 r2 incident handling strategy reviews data?
- preparation
- detection and analysis
- containment, eradication, and recovery
- post-incident analysis
82. Which of the following has been used to evade IDS / IPS devices?
- SNMP
- HTTP
- TNP
- Fragmentation
83. Which CVSSv3 metric value increases when the attacker is able to modify all files protected by the vulnerable component?
- confidentiality
- integrity
- availability
- complexity
84. Which description of a retrospective malware detection is true?
- You use Wireshark to identify the malware source.
- You use historical information from one or more sources to identify the affected host or file.
- You use information from a network analyzer to identify the malware source.
- You use Wireshark to identify the affected host or file.
85. What is the process of remediation the system from attack so that responsible threat actor can be revealed?
- Validating the Attacking Host’s IP Address
- Researching the Attacking Host through Search Engines.
- Using Incident Databases.
- Monitoring Possible Attacker Communication Channels.
86. Which of the following is not a metadata feature of the Diamond Model?
- Direction
- Result
- Devices
- Resources
87. Which of the following is one of the main goals of data normalization?
- To save duplicate logs for redundancy
- To purge redundant data while maintaining data integrity
- To correlate IPS and IDS logs with DNS
- To correlate IPS and IDS logs with Firewall logs
88. Refer to the exhibit. Which application protocol is in this PCAP file?
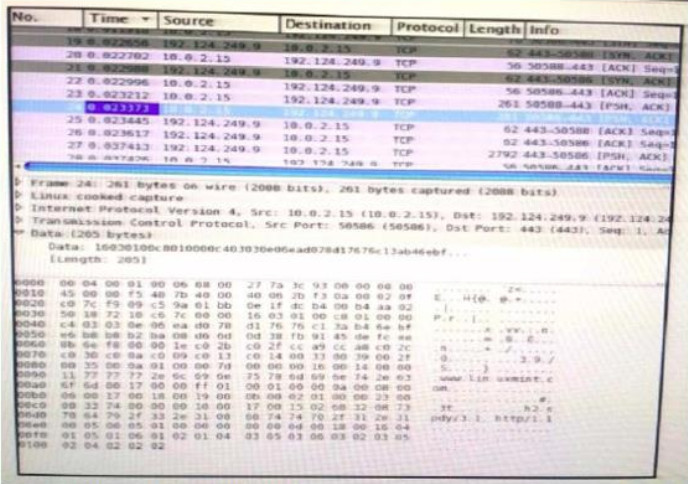
- TCP
- SSH
- HTTP
- SSL
89. What is the correct about listening port?
- A listening port is a port open by a running application in order to accept inbound connections.
- A listening port is a port open by a running application in order to accept outbound connections.
90. Refer to the exhibit. Which packet contains a file that is extractable within Wireshark?
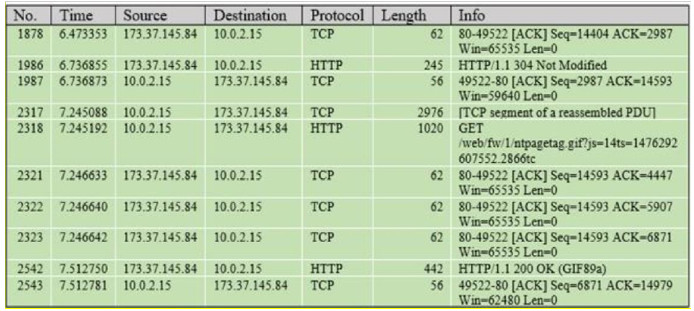
- 1986
- 2318
- 2542
- 2317
91. Which two HTTP header fields relate to intrusion analysis? (Choose two).
- user-agent
- host
- connection
- language
- handshake type
92. Which type of analysis assigns values to scenarios to see what the outcome might be in each scenario?
- deterministic
- exploratory
- probabilistic
- descriptive
93. Which CVSSv3 metric captures the level of access that is required for a successful attack?
- attack vector
- attack complexity
- privileges required
- user interaction
94. Refer to the exhibit. Which type of log is this an example of?

- IDS log
- proxy log
- NetFlow log
- syslog
95. Which CVSSv3 metric value increases when attacks consume network bandwidth, processor cycles, or disk space?
- confidentiality
- integrity
- availability
- complexity
96. Select and Place:
97. Employee are allowed to access internal websites. Employee access an internal website but IDS report as a malicious behavior
- True positive
- True negative
- False positive
- False negative
98. Refer to the exhibit. Drag and drop the element name from the left onto the correct piece of the PCAP file on the right.
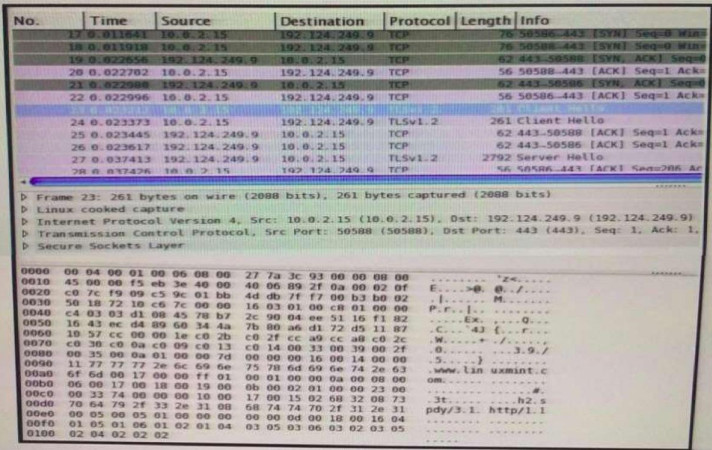
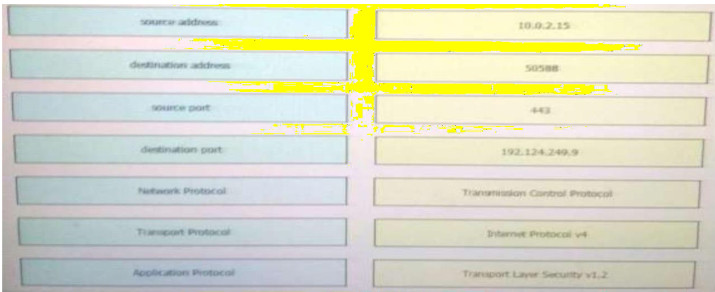
Correct Answer:
10.0.2.15 – Source address
50588 – Source port
443 – Destination port
192.124.249.9 – Destination address
TCP – Transport protocol
Internet Protocal v4 – Network protocol
TLSv1.2 – Application protocol
99. Which of the following are the three metrics, or scores, of the CVSS?
- Baseline score
- Base score
- Environmental score
- Temporal score
100. Filtering ports in wireshark?
- tcp.port = 80
- tcp.port equals 80
- tcp.port != 80
- tcp.port equal 80
101. You see 100 HTTP GET and POST requests for various pages on one of your web servers. The user agent in the requests contain php code that, if executed, creates and writes to a new php file on the webserver. Which category does this event fall under as defined in the Diamond Model of Intrusion?
- delivery
- reconnaissance
- action on objectives
- installation
- exploitation
102. Which of the following is the team that handles the investigation, resolution, and disclosure of security vulnerabilities in vendor products and services?
- CSIRT
- ICASI
- USIRP
- PSIRT
103. Which source provides reports of vulnerabilities in software and hardware to a Security Operations Center?
- Analysis Center
- National CSIRT
- Internal CSIRT
- Physical Security
104. Nistsp800-61R2 what are the recommended protections against malware?
- install software to detect malware
- update antivirus signature
105. Which option is generated when a file is run through an algorithm and generates a string specific to the contents of that file?
- URL
- hash
- IP address
- destination port
106. An organization has recently adjusted its security stance in response to online threats made by a known hacktivist group. Which term defines the initial event in the NIST SP800-61 r2?
- Indicator
- Precursor
- online assault
- trigger
107. You see confidential data being exfiltrated to an IP address that is attributed to a known Advanced Persistent Threat group. Assume that this is part of a real attack and not a network misconfiguration. Which category does this event fall under as defined in the Diamond Model of Intrusion?
- reconnaissance
- weaponization
- delivery
- action on objectives
108. Which two statements correctly describe the victim demographics section of the VERIS schema? (Choose two.)
- The victim demographics section describes but does not identify the organization that is affected by the incident.
- The victim demographics section compares different types of organizations or departments within a single organization.
- The victim demographics section captures general information about the incident.
- The victim demographics section uses geolocation data to identify the organization name of the victim and the threat actor.
109. You have run a suspicious file in a sandbox analysis tool to see what the file does. The analysis report shows that outbound callouts were made post infection. Which two pieces of information from the analysis report are needed or required to investigate the callouts? (Choose two.)
- file size
- domain names
- dropped files
- signatures
- host IP addresses
110. Which data type is protected under the PCI compliance framework?
- credit card type
- primary account number
- health conditions
- provision of individual care
111. Which option filters a LibPCAP capture that used a host as a gateway?
- tcp|udp] [src|dst] port
- [src|dst] net [{mask }|{len }]
- ether [src|dst] host
- gateway host
112. Which kind of evidence can be considered most reliable to arrive at an analytical assertion?
- direct
- corroborative
- indirect
- circumstantial
- textual
113. What mechanism does the Linux operating system provide to control access to files?
- privileges required
- user interaction
- file permissions
- access complexity
114. Which two options can be used by a threat actor to determine the role of a server? (Choose two.)
- PCAP
- tracert
- running processes
- hard drive configuration
- applications
115. In VERIS, an incident is viewed as a series of events that adversely affects the information assets of an organization. Which option contains the elements that every event is comprised of according to VERIS incident model’?
- victim demographics, incident description, incident details, discovery & response
- victim demographics, incident details, indicators of compromise, impact assessment
- actors, attributes, impact, remediation
- actors, actions, assets, attributes
116. Which feature is used to find possible vulnerable services running on a server?
- CPU utilization
- security policy
- temporary internet files
- listening ports
117. Refer to the exhibit. What can be determined from this ping result? Exhibit:
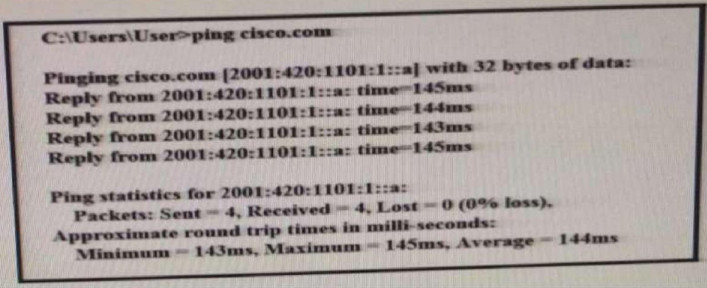
- The public IP address of cisco.com is 2001:420:1101:1::a.
- The Cisco.com website is down.
- The Cisco.com website is responding with an internal IP.
- The public IP address of cisco.com is an IPv4 address.
120. Which option is unnecessary for determining the appropriate containment strategy according to NIST.SP80061r2?
- attack vector used to compromise the system
- time and resources needed to implement strategy
- need for evidence preservation
- effectiveness of the strategy
121. To which category do attributes belong within the VERIS schema
- victim demographics
- incident tracking
- Discovery and response
- incident description
123. How do you enforce network access control automatically?
- IGMP
- SNMP
- 802.1X
- Port Security
124. Which Linux file system allows unlimited folder subdirectory structure
- ext4
- ext3
- ext2
- NTFS
125. Providing cybersecurity protection to Federal civilian executive branch agencies through intrusion detection and prevention capabilities. Which team?
- Federal CSIRT
- Federal PSIRT
- National CSIRT
- National PSIRT
126. Which type verification typically consists of using tools to compute the message digest of the original and copies data, then Fs to make sure that they are the same?
- evidence collection order
- data integrity
- data preservation
- volatile data collection
127. What define the roadmap for implementing the incident response correlation?
- Incident response plan
- Incident response policy
- Incident response procedures
128. Which expression creates a filter on a host IP address or name?
- [src|dst] host
- [tcp|udp] [src|dst] port
- ether [src|dst] host
- gateway host
129. Which analyzing technique describe the outcome as well as how likely each outcome is?
- deterministic
- exploratory
- probabilistic
- descriptive
130. Which value in profiling servers in a system is true?
- it can identify when network performance has decreased
- it can identify servers that have been exploited
- it can identify when network ports have been connected
- it can protect the address space of critical hosts.
131. Which event artifact can be used to identify HTTP GET requests for a specific file?
- HTTP status code
- TCP ACK
- destination IP
- URI
132. Which CVSSv3 metric value increases when conditions beyond the attacker’s control must exist in order to exploit the vulnerability.
- confidentiality
- attack vector
- availability
- attack complexity
133. What is the common artifact that is used to uniquely identify a detected file?
- Hash
- Timestamp
- File size
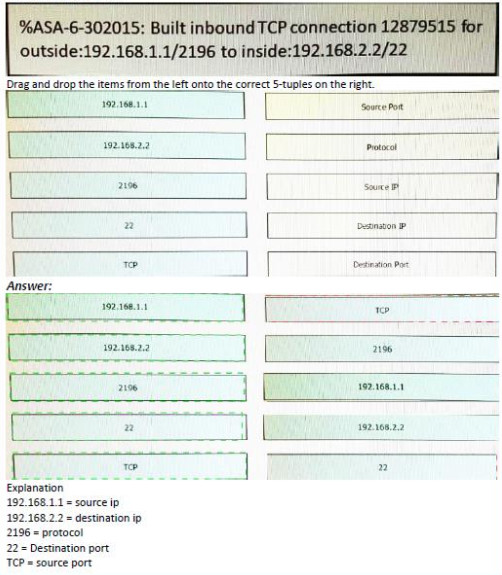
134. Refer to exhibit
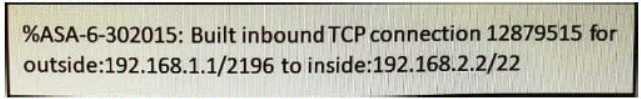
Drag and drop the items from the left onto the correct 5-tuples on the right.
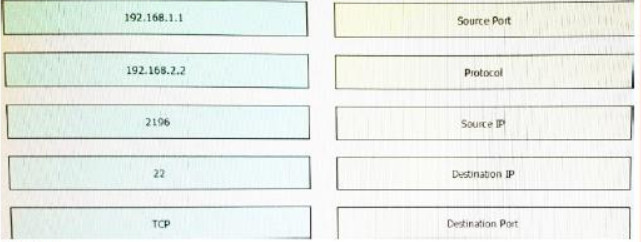
Answer:
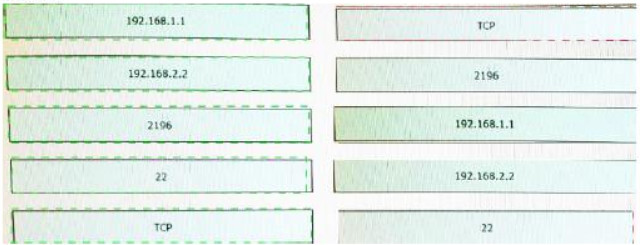
Explanation:
192.168.1.1 = source ip
192.168.2.2 = destination ip
2196 = protocol
22 = Destination port
TCP = source port
135. What are the metric values of the confidentiality based on the CVSS framework?
- Low-high
- Low –Medium-high
- High-Low-none
136. Which signature type results in a legitimate alert been dismissed?
- True negative
- False negative
- True Positive
- False Positive
137. Which incident handling is focused on minimizing the impact of an incident?
- Scoping
- Reporting
- Containment
- Eradication
- Remediation
139. According to NIST 86, which action describes the volatile data collection?
- Collect data before rebooting
- Collect data while rebooting
- Collect data after rebooting
- Collect data that contains malware
140. Which statement about collecting data evidence when performing digital forensics is true?
- Allowing unrestricted access to impacted devices
- Not allowing items of evidence to be physically touch
- Powering off the device after collecting the data
- It must be preserved and integrity checked
141. Which option is the process of remediating the network and systems and/or reconstructing the attack so that the responsible threat actor can be revealed?
- data analytics
- asset attribution
- threat actor attribution
- evidence collection
142. You have a video of suspect entering your office the day your data has being stolen?
- Direct evidence
- Indirect
143. What define the roadmap for implementing the incident response correlative?
- Incident response plan
- Incident response policy
- Incident response procedures
145. Which precursor example is true?
- Admin finds their password has been changed
- A log scan indicating a port scan against a host
- A network device configuration has been changed
146. Which option can be addressed when using retrospective security techniques?
- if the affected host needs a software update
- how the malware entered our network
- why the malware is still in our network
- if the affected system needs replacement
147. What can be addressed when using retrospective security techniques?
- if the affected host needs a software update
- what is the malware working now
- if the affected system needs replacement
- why the malware is still in our network
148. What can be addressed when using retrospective security techniques?
- if the affected host needs a software update
- what system are affected
- if the affected system needs replacement
- why the malware is still in our network
149. Providing cybersecurity protection to Federal civilian executive branch agencies through intrusion detection and prevention capabilities. Which team?
- Federal CSIRT
- Federal PSIRT
- NationalCSIT
- National PSIRT
150. Which option is the logical source device for these events?

- web server
- NetFlow collector
- proxy server
- IDS/IPS
151.
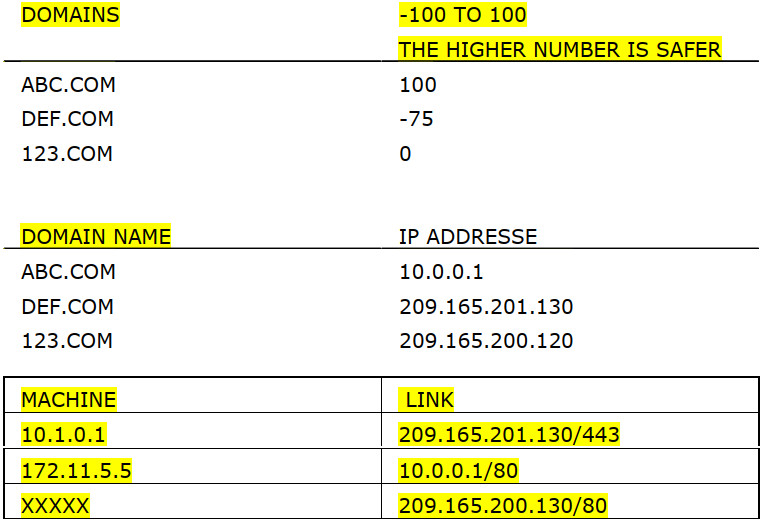
Which machine risk to be infected or something like that ?
- 10.1.0.1
- 172.11.5.5
152. Where HTTP normally used on forensic to find the browser type of the attacker?
- User agent
- Referrer
- Host
- something language
154. Which purpose of data mapping is true?
- Visualize data.
- Find extra vulnerabilities.
- Discover the identities of attackers
- Check that data is correct
155. 32 bit file system related to allocation address table ,which file system?
- EXT4
- NTFS
- FAT16
- FAT32
154. Which statement about collecting data evidence when performing digital forensics is true?
- Allowing unrestricted access to impacted devices
- Not allowing items of evidence to be physically touch
- Powering off the device after collecting the data
- It must be preserved and integrity checked
154. What is accomplished in the identification phase of incident handling?
- determining the responsible user
- identifying source and destination IP addresses
- defining the limits of your authority related to a security
- determining that a security event has occurred
155. What is the definition of confidentiality according to CVSSv3 framework?
- It a metric that impact confidentiality of information managed by a software due to unsuccessful exploited vulnerability
- It a metric that impact confidentiality of information managed by a person due to successful exploited vulnerability
- It a metric that impact confidentiality of information managed by a software due to successful exploited vulnerability
- It a metric that impact confidentiality of information managed by a person due to unsuccessful exploited vulnerability
156. Which statement describes the function provided by the Tor network?
- It distributes user packets through load balancing.
- It allows users to browse the Internet anonymously.
- It conceals packet contents by establishing end-to-end tunnels.
- It manipulates packets by mapping IP addresses between two networks.
157. Which two attacks target web servers through exploiting possible vulnerabilities of input functions used by an application? (Choose two.)
- SQL injection
- port scanning
- port redirection
- trust exploitation
- cross-site scripting

is this the dump for cyberops 200-201?
Passed the exam?
Which statement describes the function provided by the Tor network?
Explanation:Tor is a software platform and network of P2P hosts that function as Internet routers on the Tor network. The Tor network allows users to browse the Internet anonymously.
This question belongs to CyberOps Associate (200-201) Certification Practice Exam
Thanks for sharing
Which two attacks target web servers through exploiting possible vulnerabilities of input functions used by an application? (Choose two.)
Explanation:When a web application uses input fields to collect data from clients, threat actors may exploit possible vulnerabilities for entering malicious commands. The malicious commands that are executed through the web application might affect the OS on the web server. SQL injection and cross-site scripting are two different types of command injection attacks.
This question belongs to CyberOps Associate (200-201) Certification Practice Exam
Please kindly update with 210-256 recent questions
Thank you
Dear Sir, Kindly advice if there are any new questions for exams being taken before 28th May dateline.
If there are new questions kindly update.
i can take the examn SECOPS after February ?? Help me please
2 days before i passed the exam 210-255. thanks for itexamanswers.net …
Hi
Do you know if i can take the examn 210-255 after February 24 ?
reply me please !!
great thank you………………