1. A computer is presenting a user with a screen requesting payment before the user data is allowed to be accessed by the same user. What type of malware is this?
- A type of virus
- A type of logic bomb
- A type of ransomware
- A type of worm
2. What is cyberwarfare?
- It is an attack only on military targets.
- It is an attack on a major corporation.
- It is an attack that only involves robots and bots.
- It is an attack designed to disrupt, corrupt, or exploit national interests.
3. How can a security information and event management system in an SOC be used to help personnel fight against security threats?
- By collecting and filtering data
- By filtering network traffic
- By authenticating users to network resources
- By encrypting communications to remote sites
4. Which three technologies should be included in an SOC security information and event management system? (Choose three.)
- Proxy service
- User authentication
- Threat intelligence
- Security monitoring
- Intrusion prevention
- Event collection, correlation, and analysis
5. What name is given to hackers who hack for a political or social cause?
- White hat
- Hacker
- Hacktivist
- Blue hat
6. Which organization is an international nonprofit organization that offers the CISSP certification?
- (ISC)2
- IEEE
- GIAC
- CompTIA
7. After a security incident is verified in a SOC, an incident responder reviewsthe incident but cannot identify the source of the incident and form an effective mitigation procedure. To whom should the incident ticket be escalated?
- A cyberoperations analyst for help
- An SME for further investigation
- An alert analyst for further analysis
- The SOC manager to ask for other personnel to be assigned
8. The term Alert Analyst refers to which group of personnel in an SOC?
- Tier 1 personnel
- Tier 2 personnel
- Tier 3 personnel
- SOC managers
9. What is a rogue wireless hotspot?
- It is a hotspot that was set up with outdated devices.
- It is a hotspot that does not encrypt network user traffic.
- It is a hotspot that does not implement strong user authentication mechanisms.
- It is a hotspot that appears to be from a legitimate business but was actually set up by someone without the permission from the business.
10. What is a potential risk when using a free and open wireless hotspot in a public location?
- Too many users trying to connect to the Internet may cause a network traffic jam.
- The Internet connection can become too slow when many users access the wireless hotspot.
- Network traffic might be hijacked and information stolen.
- Purchase of products from vendors might be required in exchange for the Internet access.
11. How does a security information and event management system (SIEM) in a SOC help the personnel fight against security threats?
- by integrating all security devices and appliances in an organization
- by analyzing logging data in real time
- by combining data from multiple technologies
- by dynamically implementing firewall rules
12. Which statement best describes a motivation of hacktivists?
- They are part of a protest group behind a political cause.
- They are curious and learning hacking skills.
- They are trying to show off their hacking skills.
- They are interested in discovering new exploits.
13. If a SOC has a goal of 99.999% uptime, how many minutes of downtime a year would be considered within its goal?
- Approximately 5 minutes per year.
- Approximately 10 minutes per year.
- Approximately 20 minutes per year.
- Approximately 30 minutes per year.
14. Why do IoT devices pose a greater risk than other computing devices on a network?
- Most IoT devices do not require an Internet connection and are unable to receive new updates.
- IoT devices cannot function on an isolated network with only an Internet connection.
- Most IoT devices do not receive frequent firmware updates.
- IoT devices require unencrypted wireless connections.
15. Which two services are provided by security operations centers? (Choose two.)
- managing comprehensive threat solutions
- ensuring secure routing packet exchanges
- responding to data center physical break-ins
- monitoring network security threats
- providing secure Internet connections
16. Users report that a database file on the main server cannot be accessed. A database administrator verifies the issue and notices that the database file is now encrypted. The organization receives a threatening email demanding payment for the decryption of the database file. What type of attack has the organization experienced?
- man-in-the-middle attack
- DoS attack
- ransomware
- Trojan horse
17. Which organization offers the vendor-neutral CySA+ certification?
- IEEE
- CompTIA
- (ISC)²
- GIAC
18. What was used as a cyberwarfare weapon to attack a uranium enrichment facility in Iran?
- DDoS
- SQL injection
- PSYOPS
- Stuxnet
19. Which three technologies should be included in a SOC security information and event management system? (Choose three.)
- firewall appliance
- security monitoring
- log management
- intrusion prevention
- proxy service
- threat intelligence
20. Which personnel in a SOC is assigned the task of verifying whether an alert triggered by monitoring software represents a true security incident?
- SOC Manager
- Tier 2 personnel
- Tier 3 personnel
- Tier 1 personnel
21. Which statement describes cyberwarfare?
- Cyberwarfare is an attack carried out by a group of script kiddies.
- It is a series of personal protective equipment developed for soldiers involved in nuclear war.
- It is simulation software for Air Force pilots that allows them to practice under a simulated war scenario.
- It is Internet-based conflict that involves the penetration of information systems of other nations.
22. in the operation of a SOC, which system is frequently used to let an analyst select alerts from a pool to investigate?
- syslog server
- registration system
- ticketing system
- security alert knowledge-based system
23. What name is given to an amateur hacker?
- red hat
- script kiddie
- black hat
- blue team
24. Which personnel in a SOC are assigned the task of hunting for potential threats and implementing threat detection tools?
- Tier 1 Analyst
- SOC Manager
- Tier 2 Incident Reporter
- Tier 3 SME
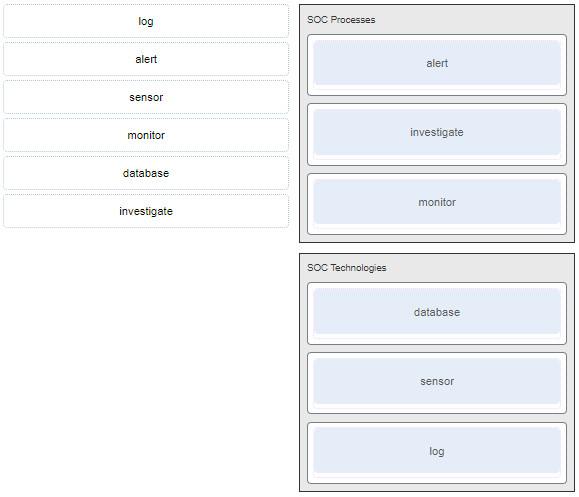
25. Match the components to the major categories in a SOC.
26. Match the job titles to SOC personnel positions. (Not all options are used.)
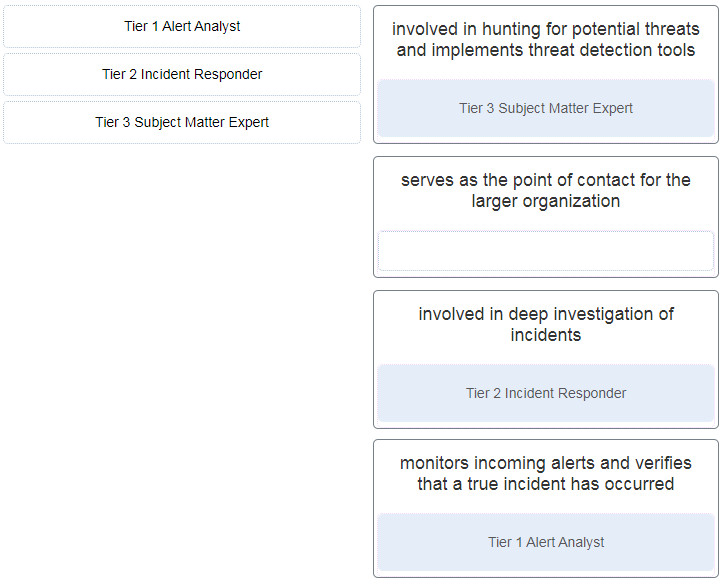
- Tier 1 Alert Analyst —> monitors incoming alerts & verifies that a true incident has occured
- Tier 2 Incident Responder –> involved in deep investigation of incident
- Tier 3 Subject Matter Expert –> involved in hunting for potential threads & implements thread detection tools
- (not use) –> serve as the point of contact for the large organitazion
27. What name is given to a amateur hacker?
- blue team
- red hat
- script kiddie
- black hat

I this still valid?
What name is givento an amateur hacker?
1. Redhat
2.blackhat
3.blueteam
4.svript kiddle
script kiddle
there is a recent update on cyber security. they have increase the module to like 23 module can this still work fine for it?
Which version you are learning?
Hello Admin! See this link for module 1
<hidden>
Thank you so much! I will update this exam.
I can do the same for the rest of the course “CyberOps Associate 1.0”. I only need time :)
ps: HTML is best viewed through Microsoft Edge or Internet Explorer.
OK, I can wait. I want to thank you for all the support you have given me during my time here. I appreciate all of your support. :)
I would also like to thank you for building and maintaining your site. He is very helpful to many newcomers to this specialty!
ps: I think I’m better off sending you modules as I build them because you will probably change this information for your site?
ps2: How can I best send them to you? Can I post links right here or privately?
OK! You can send it to my email: [email protected]
Thank you!
pls what the course feedback
Match the job titles to SOC personnel positions. (Not all options are used.)
Tier 1 Alert Analyst
Tier 2 Incident Responder
Tier 3 Subject Matter Expert
opsi :
-serve as the point of contact for the large organitazion
-monitors incoming alerts & verifies that a true incident has occured
-involved in hunting for potential threads & implements thread detection tools
-involved in deep investigation of incident
Which personnel in a SOC are assigned the task of hunting for potential threats and implementing threat detection tools?
Tier 2 Incident Reporter
SOC Manager
Tier 3 SME
Tier 1 Analyst
Tier 3 SME
Which three technologies should be included in a SOC security information and event management system? (Choose three.)
Options are :
firewall appliance
intrusion prevention
log management
security monitoring
proxy service
threat intelligence
Refer to curriculum topic: 1.2.1
Technologies in a SOC should include the following:
Event collection, correlation, and analysis
* Security monitoring
Security control
* Log management
Vulnerability assessment
Vulnerability tracking
*Threat intelligence
Proxy server, user authentication, and IPS are security devices and mechanisms deployed in the network infrastructure and managed by NOC.
Security monitoring
threat intelligence
Log management