Time limit: 0
Quiz-summary
0 of 37 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
Information
CCNA Cyber Ops (Version 1.1) – Chapter 5 Test Online Full
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 37 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- Answered
- Review
-
Question 1 of 37
1. Question
1 pointsWhat are two types of addresses found on network end devices? (Choose two.)Correct
Incorrect
-
Question 2 of 37
2. Question
1 pointsWhich OSI layer header is rewritten with new addressing information by a router when forwarding between LAN segments?Correct
Incorrect
-
Question 3 of 37
3. Question
1 pointsWhich protocol provides authentication, integrity, and confidentiality services and is a type of VPN?Correct
Incorrect
-
Question 4 of 37
4. Question
1 pointsWhat are two uses of an access control list? (Choose two.)Correct
Incorrect
-
Question 5 of 37
5. Question
1 pointsWhich protocol or service is used to automatically synchronize the software clocks on Cisco routers?Correct
Incorrect
-
Question 6 of 37
6. Question
1 pointsWhich wireless parameter is used by an access point to broadcast frames that include the SSID?Correct
Incorrect
-
Question 7 of 37
7. Question
1 pointsA Cisco router is running IOS 15. What are the two routing table entry types that will be added when a network administrator brings an interface up and assigns an IP address to the interface? (Choose two.)Correct
Incorrect
-
Question 8 of 37
8. Question
1 pointsRefer to the exhibit. The network “A” contains multiple corporate servers that are accessed by hosts from the Internet for information about the corporation. What term is used to describe the network marked as “A”?Correct
Incorrect
-
Question 9 of 37
9. Question
1 pointsWhat is the role of an IPS?Correct
Incorrect
-
Question 10 of 37
10. Question
1 pointsWhich two features are included by both TACACS+ and RADIUS protocols? (Choose two.)Correct
Incorrect
-
Question 11 of 37
11. Question
1 pointsWhat does the TACACS+ protocol provide in a AAA deployment?Correct
Incorrect
-
Question 12 of 37
12. Question
1 pointsWhich parameter is commonly used to identify a wireless network name when a home wireless AP is being configured?Correct
Incorrect
-
Question 13 of 37
13. Question
1 pointsWhat information within a data packet does a router use to make forwarding decisions?Correct
Incorrect
-
Question 14 of 37
14. Question
1 pointsWhich protocol creates a virtual point-to-point connection to tunnel unencrypted traffic between Cisco routers from a variety of protocols?Correct
Incorrect
-
Question 15 of 37
15. Question
1 pointsWhich two statements are true about NTP servers in an enterprise network? (Choose two.)Correct
Incorrect
-
Question 16 of 37
16. Question
1 pointsWhat is true concerning physical and logical topologies?Correct
Incorrect
-
Question 17 of 37
17. Question
1 pointsWhich layer of the hierarchical design model is a control boundary between the other layers?Correct
Incorrect
-
Question 18 of 37
18. Question
1 pointsWhich protocol or service allows network administrators to receive system messages that are provided by network devices?Correct
Incorrect
-
Question 19 of 37
19. Question
1 pointsWhat is a function of a proxy firewall?Correct
Incorrect
-
Question 20 of 37
20. Question
1 pointsWhat is the function of the distribution layer of the three-layer network design model?Correct
Incorrect
-
Question 21 of 37
21. Question
1 pointsWhich LAN topology requires a central intermediate device to connect end devices?Correct
Incorrect
-
Question 22 of 37
22. Question
1 pointsWhich device can control and manage a large number of corporate APs?Correct
Incorrect
-
Question 23 of 37
23. Question
1 pointsFor which discovery mode will an AP generate the most traffic on a WLAN?Correct
Incorrect
-
Question 24 of 37
24. Question
1 pointsWhat is a feature of the TACACS+ protocol?Correct
Incorrect
-
Question 25 of 37
25. Question
1 pointsWhat is the only attribute used by standard access control lists to identify traffic?Correct
Incorrect
-
Question 26 of 37
26. Question
1 pointsWhat specialized network device is responsible for enforcing access control policies between networks?Correct
Incorrect
-
Question 27 of 37
27. Question
1 pointsWhat information does an Ethernet switch examine and use to build its address table?Correct
Incorrect
-
Question 28 of 37
28. Question
1 pointsWhich device is an intermediary device?Correct
Incorrect
-
Question 29 of 37
29. Question
1 pointsWhich statement describes a difference between RADIUS and TACACS+?Correct
Incorrect
-
Question 30 of 37
30. Question
1 pointsWhich wireless parameter refers to the frequency bands used to transmit data to a wireless access point?Correct
Incorrect
-
Question 31 of 37
31. Question
1 pointsWhat specialized network device uses signatures to detect patterns in network traffic?Correct
Incorrect
-
Question 32 of 37
32. Question
1 pointsWhat type of physical topology can be created by connecting all Ethernet cables to a central device?Correct
Incorrect
-
Question 33 of 37
33. Question
1 pointsWhich network service synchronizes the time across all devices on the network?Correct
Incorrect
-
Question 34 of 37
34. Question
1 pointsWhich network service allows administrators to monitor and manage network devices?Correct
Incorrect
-
Question 35 of 37
35. Question
1 pointsMatch each device to a category.Correct
Incorrect
-
Question 36 of 37
36. Question
1 pointsMatch the destination network routing table entry type with a defintion.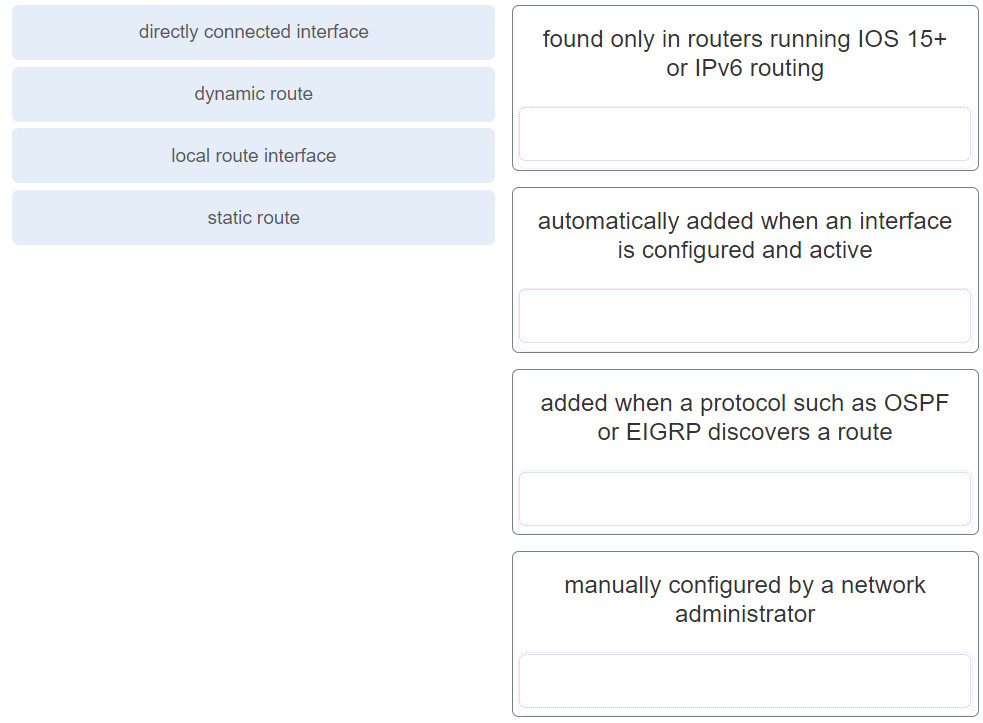 Correct
Correct
Incorrect
-
Question 37 of 37
37. Question
1 pointsMatch the network security device type with the description.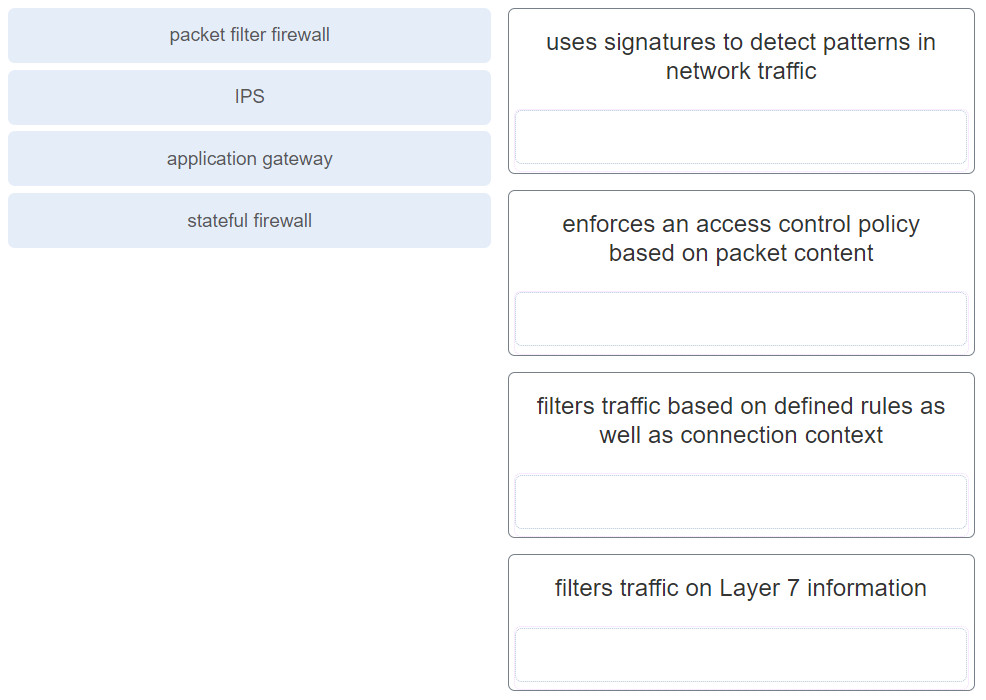 Correct
Correct
Incorrect
