22.0 Introduction
22.0.1 Why Should I Take this Module?
Endpoints are any device that communicates with any other device on a network. This includes the thousands of PCs, printers, servers, and other devices that are found in a large network. Each endpoint is vulnerable to attack. How can all of these endpoints be protected, and can we know if any one of them has been compromised by a threat actor or malware? This module describes various endpoint protection technologies and methods, which combine to help better protect your home and your organization.
22.0.2 What Will I Learn in this Module?
Module Title: Endpoint Protection
Module Objective: Explain how a malware analysis website generates a malware analysis report.
| Topic | Topic Objective |
|---|---|
| Antimalware Protection | Explain methods of mitigating malware |
| Host-based Intrusion Prevention | Explain host-based IPS/IDS log entries |
| Application Security | Explain how a sandbox is used to analyze malware |
22.1 Antimalware Protection
22.1.1 Endpoint Threats
The term “endpoint” is defined in various ways. For the purpose of this course, we can define endpoints as hosts on the network that can access or be accessed by other hosts on the network. This obviously includes computers and servers, however many other devices can also access the network. With the rapid growth of the Internet of Things (IoT), other types of devices are now endpoints on the network. This includes networked security cameras, controllers, and even light bulbs and appliances. Each endpoint is potentially a way for malicious software to gain access to a network. In addition, new technologies, such as cloud, expand the boundaries of enterprise networks to include locations on the internet for which enterprises are not responsible.
Devices that remotely access networks through VPNs are also endpoints that need to be considered. These endpoints could inject malware into the VPN network from the public network.
The following points summarize some of the reasons why malware remains a major challenge:
- According to research from Cybersecurity Ventures, by 2021 a new organization will fall victim to a ransomware attack every 11 seconds.
- Ransomware attacks will cost the global economy $6 trillion annually by 2021.
- In 2018, 8 million attempts to steal system resources using cryptojacking malware were observed.
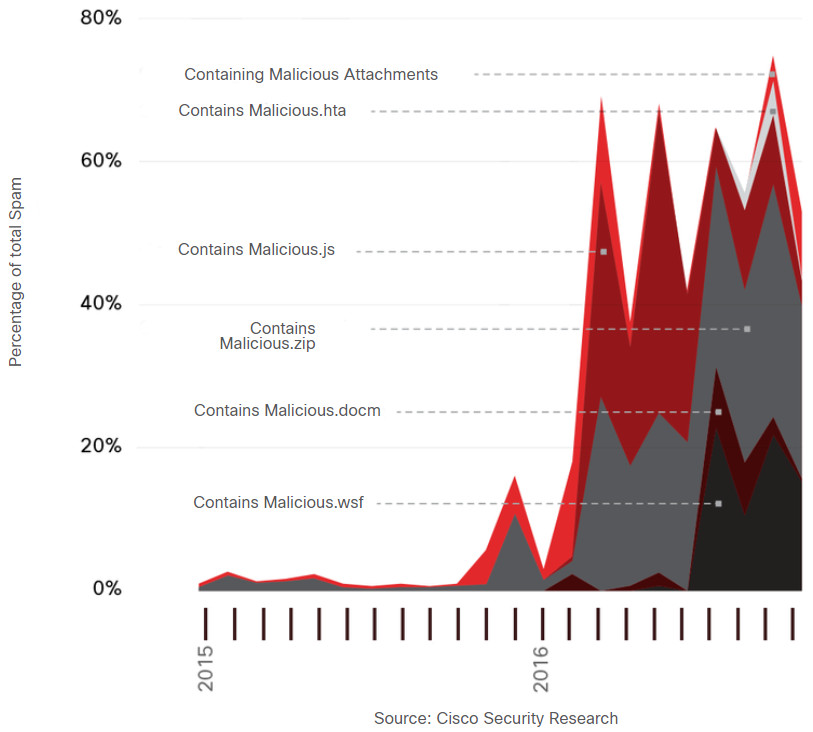
- From 2016 to early 2017, global spam volume increased dramatically. 8 to 10 percent of this spam can be considered to be malicious, as shown in the figure.
- In 2020, it is projected that the average number of cyber attacks per macOS device will rise from 4.8 in 2018 to 14.2 in 2020.
- Several common types of malware have been found to significantly change features in less than 24 hours in order to evade detection.
Malicious Spam Percentage
22.1.2 Endpoint Security
News media commonly cover external network attacks on enterprise networks. These are some examples of such attacks:
- DoS attacks on an organization’s network to degrade or even halt public access to it
- Breach of an organization’s web server to deface their web presence
- Breach of an organization’s data servers and hosts to steal confidential information
Various network security devices are required to protect the network perimeter from outside access. As shown in the figure, these devices could include a hardened router that is providing VPN services, a next generation firewall (ASA, in the figure), an IPS appliance, and an authentication, authorization, and accounting (AAA) services server (AAA Server, in the figure).
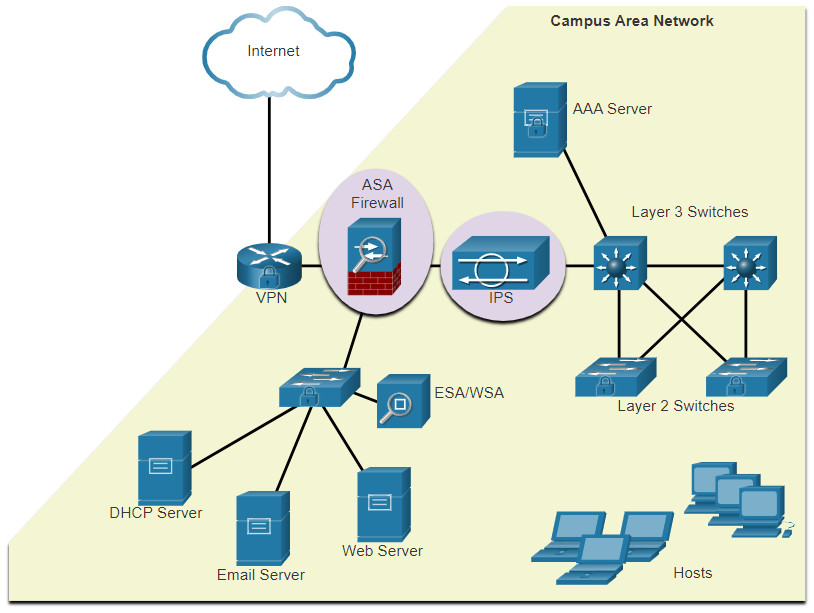
However, many attacks originate from inside the network. Therefore, securing an internal LAN is nearly as important as securing the outside network perimeter. Without a secure LAN, users within an organization are still susceptible to network threats and outages that can directly affect an organization’s productivity and profit margin. After an internal host is infiltrated, it can become a starting point for an attacker to gain access to critical system devices, such as servers and sensitive information.
Specifically, there are two internal LAN elements to secure:
- Endpoints – Hosts commonly consist of laptops, desktops, printers, servers, and IP phones, all of which are susceptible to malware-related attacks.
- Network infrastructure – LAN infrastructure devices interconnect endpoints and typically include switches, wireless devices, and IP telephony devices. Most of these devices are susceptible to LAN-related attacks including MAC address table overflow attacks, spoofing attacks, DHCP related attacks, LAN storm attacks, STP manipulation attacks, and VLAN attacks.
22.1 This module focuses on securing endpoints.
22.1.3 Host-Based Malware Protection
The network perimeter is always expanding. People access corporate network resources with mobile devices that use remote access technologies such as VPN. These same devices are also used on unsecured, or minimally secured, public and home networks. Host-based antimalware/antivirus software and host-based firewalls are used to protect these devices.
Antivirus/Antimalware Software
This is software that is installed on a host to detect and mitigate viruses and malware. Examples are Windows Defender Virus & Threat Protection, Cisco AMP for Endpoints, Norton Security, McAfee, Trend Micro, and others. Antimalware programs may detect viruses using three different approaches:
- Signature-based – This approach recognizes various characteristics of known malware files.
- Heuristics-based – This approach recognizes general features shared by various types of malware.
- Behavior-based – This approach employs analysis of suspicious behavior.
Many antivirus programs are able to provide real-time protection by analyzing data as it is used by the endpoint. These programs also scan for existing malware that may have entered the system prior to it being recognizable in real time.
Host-based antivirus protection is also known as agent-based. Agent-based antivirus runs on every protected machine. Agentless antivirus protection performs scans on hosts from a centralized system. Agentless systems have become popular for virtualized environments in which multiple OS instances are running on a host simultaneously. Agent-based antivirus running in each virtualized system can be a serious drain on system resources. Agentless antivirus for virtual hosts involves the use of a special security virtual appliance that performs optimized scanning tasks on the virtual hosts. An example of this is VMware’s vShield.
Host-based Firewall
This software is installed on a host. It restricts incoming and outgoing connections to connections initiated by that host only. Some firewall software can also prevent a host from becoming infected and stop infected hosts from spreading malware to other hosts. This function is included in some operating systems. For example, Windows includes Windows Defender Firewall with Advanced Security as shown in the figure.
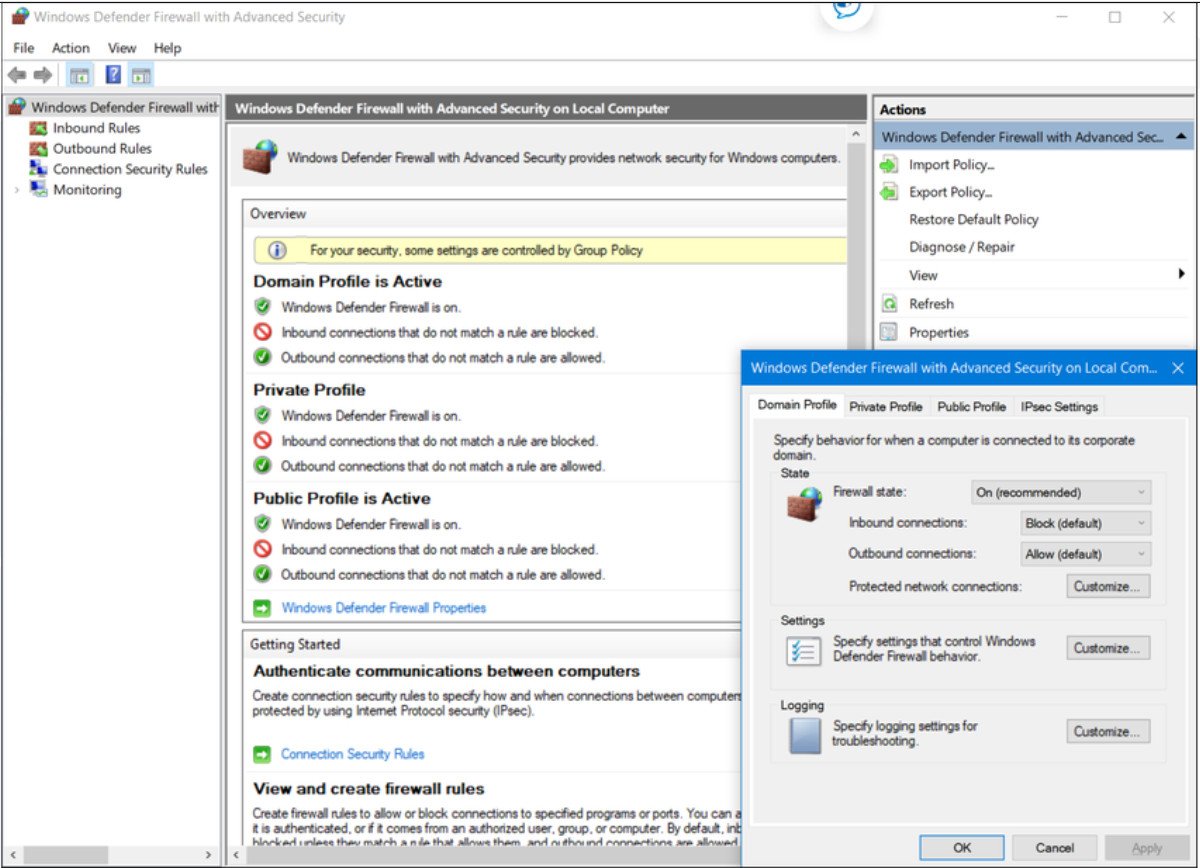
Other solutions are produced by other companies or organizations. The Linux iptables and TCP Wrappers tools are examples. Host-based firewalls are discussed in more detail later in the module.
Host-based Security Suites
It is recommended to install a host-based suite of security products on home networks as well as business networks. These host-based security suites include antivirus, anti-phishing, safe browsing, Host-based intrusion prevention system, and firewall capabilities. These various security measures provide a layered defense that will protect against most common threats.
In addition to the protection functionality provided by host-based security products is the telemetry function. Most host-based security software includes robust logging functionality that is essential to cybersecurity operations. Some host-based security programs will submit logs to a central location for analysis.
There are many host-based security programs and suites available to users and enterprises. The independent testing laboratory AV-TEST provides high-quality reviews of host-based protections, as well as information about many other security products.
Search the internet for the AVTest organization to learn more about AV-TEST.
22.1.4 Network-Based Malware Protection
Advanced Malware Protection Everywhere
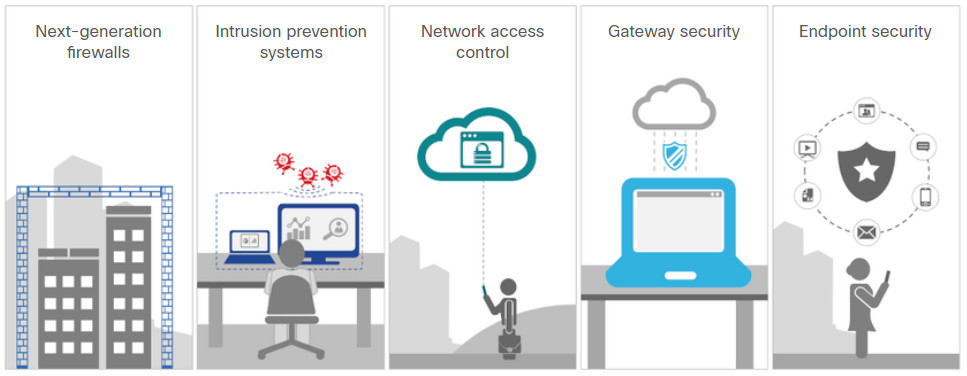
New security architectures for the borderless network address security challenges by having endpoints use network scanning elements. These devices provide many more layers of scanning than a single endpoint possibly could. Network-based malware prevention devices are also capable of sharing information among themselves to make better informed decisions.
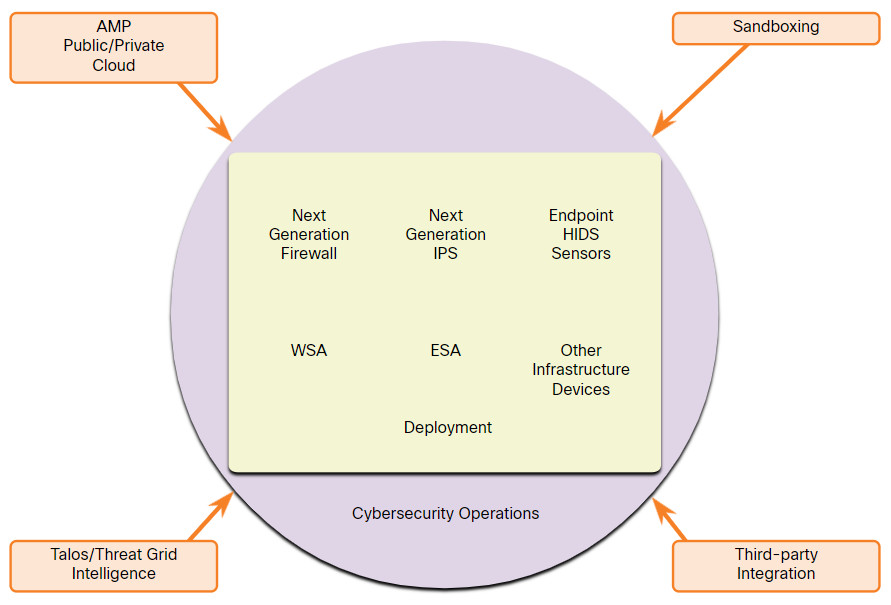
Protecting endpoints in a borderless network can be accomplished using network-based, as well as host-based techniques, as shown in the figure above. The following are examples of devices and techniques that implement host protections at the network level.
- Advanced Malware Protection (AMP) – This provides endpoint protection from viruses and malware.
- Email Security Appliance (ESA) – This provides filtering of SPAM and potentially malicious emails before they reach the endpoint. An example is the Cisco ESA.
- Web Security Appliance (WSA) – This provides filtering of websites and blacklisting to prevent hosts from reaching dangerous locations on the web. The Cisco WSA provides control over how users access the internet and can enforce acceptable use policies, control access to specific sites and services, and scan for malware.
- Network Admission Control (NAC) – This permits only authorized and compliant systems to connect to the network.
These technologies work in concert with each other to give more protection than host-based suites can provide, as shown in the figure.
22.2 Host-Based Intrusion Prevention
22.2.1 Host-Based Firewalls
Host-based personal firewalls are standalone software programs that control traffic entering or leaving a computer. Firewall apps are also available for Android phones and tablets.
Host-based firewalls may use a set of predefined policies, or profiles, to control packets entering and leaving a computer. They also may have rules that can be directly modified or created to control access based on addresses, protocols, and ports. Host-based firewall applications can also be configured to issue alerts to users if suspicious behavior is detected. They can then offer the user the ability to allow an offending application to run or to be prevented from running in the future.
Logging varies depending on the firewall application. It typically includes the date and time of the event, whether the connection was allowed or denied, information about the source or destination IP addresses of packets, and the source and destination ports of the encapsulated segments. In addition, common activities such as DNS lookups and other routine events can show up in host-based firewall logs, so filtering and other parsing techniques are useful for inspecting large amounts of log data.
One approach to intrusion prevention is the use of distributed firewalls. Distributed firewalls combine features of host-based firewalls with centralized management. The management function pushes rules to the hosts and may also accept log files from the hosts.
Whether installed completely on the host or distributed, host-based firewalls are an important layer of network security along with network-based firewalls. Here are some examples of host-based firewalls:
- Windows Defender Firewall – First included with Windows XP, Windows Firewall (now Windows Defender Firewall) uses a profile-based approach to firewall functionality. Access to public networks is assigned the restrictive Public firewall profile. The Private profile is for computers that are isolated from the internet by other security devices, such as a home router with firewall functionality. The Domain profile is the third available profile. It is chosen for connections to a trusted network, such as a business network that is assumed to have an adequate security infrastructure. Windows Firewall has logging functionality and can be centrally managed with customized group security policies from a management server such as System Center 2012 Configuration Manager.
- iptables – This is an application that allows Linux system administrators to configure network access rules that are part of the Linux kernel Netfilter modules.
- nftables – The successor to iptables, nftables is a Linux firewall application that uses a simple virtual machine in the Linux kernel. Code is executed within the virtual machine that inspects network packets and implements decision rules regarding packet acceptance and forwarding.
- TCP Wrappers – This is a rule-based access control and logging system for Linux. Packet filtering is based on IP addresses and network services.
22.2.2 Host-Based Intrusion Detection
The distinction between host-based intrusion detection and intrusion prevention is blurred. In fact, some sources refer to host-based intrusion detection and prevention systems (HIPDS). Because the industry seems to favor the use of the acronym HIDS, we will use it in our discussion here.
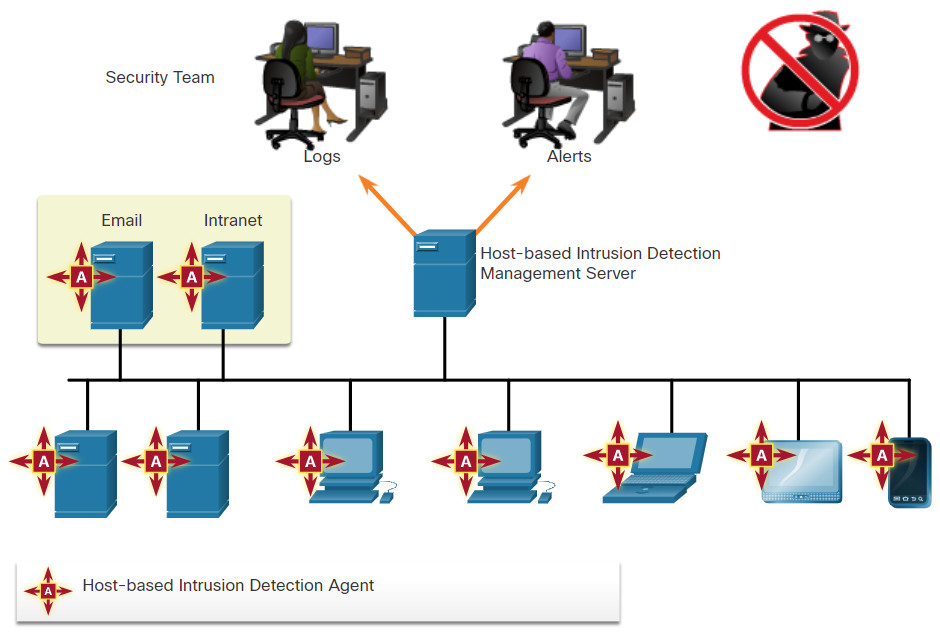
A host-based intrusion detection system (HIDS) is designed to protect hosts against known and unknown malware. A HIDS can perform detailed monitoring and reporting on the system configuration and application activity. It can provide log analysis, event correlation, integrity checking, policy enforcement, rootkit detection, and alerting. A HIDS will frequently include a management server endpoint, as shown in the figure.
A HIDS is a comprehensive security application that combines the functionalities of antimalware applications with firewall functionality. A HIDS not only detects malware but also can prevent it from executing if it should reach a host. Because the HIDS software must run directly on the host, it is considered an agent-based system.
Host-based Intrusion Detection Architecture
22.2.3 HIDS Operation
It can be said that host-based security systems function as both detection and prevention systems because they prevent known attacks and detect unknown potential attacks. A HIDS uses both proactive and reactive strategies. A HIDS can prevent intrusion because it uses signatures to detect known malware and prevent it from infecting a system. However, this strategy is only good against known threats. Signatures are not effective against new, or zero day, threats. In addition, some malware families exhibit polymorphism. This means that variations of a type, or family, of malware may be created by attackers that will evade signature-based detections by changing aspects of the malware signature just enough so that it will not be detected. An additional set of strategies are used to detect the possibility of successful intrusions by malware that evades signature detection:
- Anomaly-based – Host system behavior is compared to a learned baseline model of normal behavior. Significant deviations from the baseline are interpreted as the result of some sort of intrusion. If an intrusion is detected, the HIDS can log details of the intrusion, send alerts to security management systems, and take action to prevent the attack. The measured baseline is derived from both user and system behavior. Because many things other than malware can cause system behavior to change, anomaly detection can create many erroneous results which can increase the workload for security personnel and also lower the credibility of the system.
- Policy-based – Normal system behavior is described by rules, or the violation of rules, that are predefined. Violation of these policies will result in action by the HIDS. The HIDS may attempt to shut down software processes that have violated the rules and can log these events and alert personnel to violations. Most HIDS software comes with a set of predefined rules. With some systems, administrators can create custom policies that can be distributed to hosts from a central policy management system.
22.2.4 HIDS Products
There are a number of HIDS products on the market today. Most of them utilize software on the host and some sort of centralized security management functionality that allows integration with network security monitoring services and threat intelligence. Examples are Cisco AMP, AlienVault USM, Tripwire, and Open Source HIDS SECurity (OSSEC).
OSSEC uses a central manager server and agents that are installed on individual hosts. Currently, agents are available for Mac, Windows, Linux, and Solaris platforms. The OSSEC server, or Manager, can also receive and analyze alerts from a variety of network devices and firewalls over syslog. OSSEC monitors system logs on hosts and also conducts file integrity checking. OSSEC can detect rootkits and other malware, and can also be configured to run scripts or applications on hosts in response to event triggers.
Search the internet for OSSEC to learn more.
22.3 Application Security
22.3.1 Attack Surface
Recall that a vulnerability is a weakness in a system or its design that could be exploited by a threat. An attack surface is the total sum of the vulnerabilities in a given system that is accessible to an attacker. The attack surface can consist of open ports on servers or hosts, software that runs on internet-facing servers, wireless network protocols, and even users.
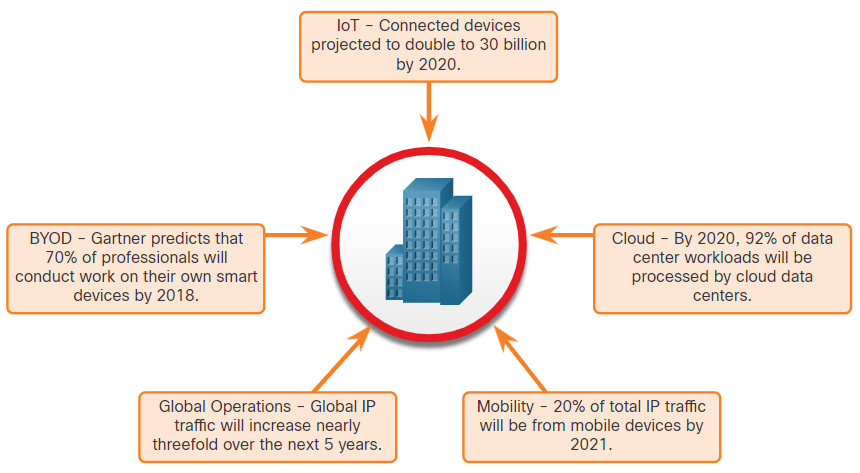
The attack surface is continuing to expand, as shown in the figure. More devices are connecting to networks through the Internet of Things (IoT) and Bring Your Own Device (BYOD). Much of network traffic now flows between devices and some location in the cloud. Mobile device use continues to increase. All of these trends contribute to a prediction that global IP traffic will increase threefold in the next five years.
The SANS Institute describes three components of the attack surface:
- Network Attack Surface – The attack exploits vulnerabilities in networks. This can include conventional wired and wireless network protocols, as well as other wireless protocols used by smartphones or IoT devices. Network attacks also exploit vulnerabilities at the network and transport layers.
- Software Attack Surface – The attack is delivered through exploitation of vulnerabilities in web, cloud, or host-based software applications.
- Human Attack Surface – The attack exploits weaknesses in user behavior. Such attacks include social engineering, malicious behavior by trusted insiders, and user error.
An Expanding Attack Surface
22.3.2 Application Blacklisting and Whitelisting
One way of decreasing the attack surface is to limit access to potential threats by creating lists of prohibited applications. This is known as blacklisting.
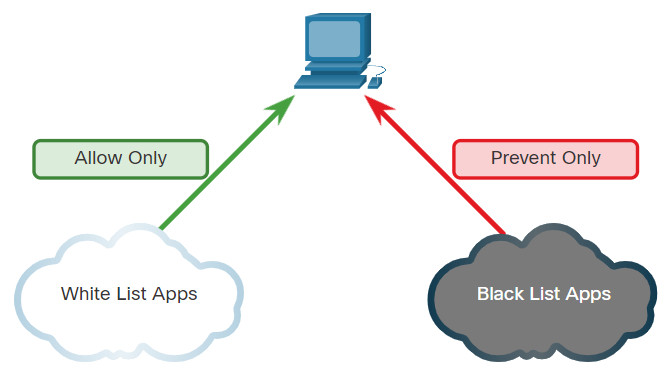
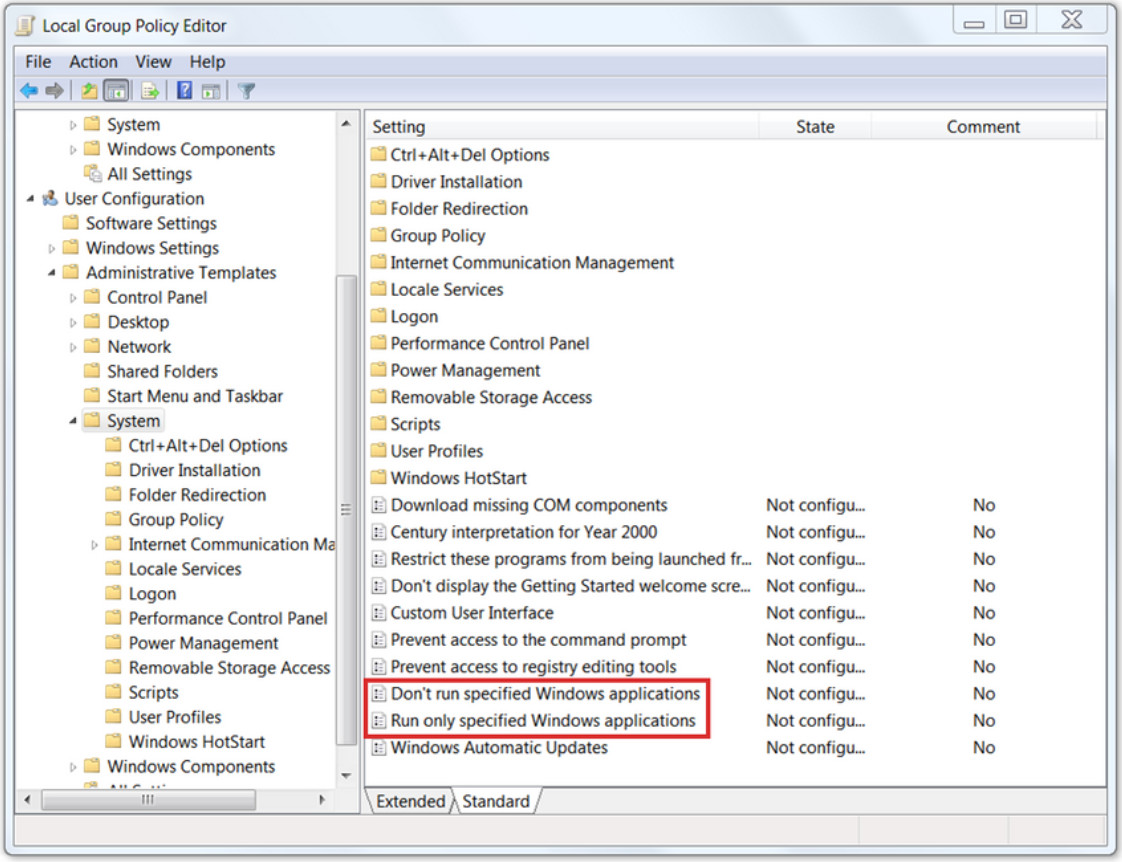
Application blacklists can dictate which user applications are not permitted to run on a computer. Similarly, whitelists can specify which programs are allowed to run, as shown in the figure. In this way, known vulnerable applications can be prevented from creating vulnerabilities on network hosts.
Whitelists are created in accordance with a security baseline that has been established by an organization. The baseline establishes an accepted amount of risk, and the environmental components that contribute to that level of risk. Non-whitelisted software can violate the established security baseline by increasing risk.
Application Blacklisting and Whitelisting
The figure shows the Windows Local Group Policy Editor blacklisting and whitelisting settings.
Websites can also be whitelisted and blacklisted. These blacklists can be manually created, or they can be obtained from various security services. Blacklists can be continuously updated by security services and distributed to firewalls and other security systems that use them. Cisco’s Firepower security management system is an example of a system that can access the Cisco Talos security intelligence service to obtain blacklists. These blacklists can then be distributed to security devices within an enterprise network.
Search the internet for The Spamhaus Project, which is an example of a free blacklist service.
22.3.3 System-Based Sandboxing
Sandboxing is a technique that allows suspicious files to be executed and analyzed in a safe environment. Automated malware analysis sandboxes offer tools that analyze malware behavior. These tools observe the effects of running unknown malware so that features of malware behavior can be determined and then used to create defenses against it.
As mentioned previously, polymorphic malware changes frequently and new malware appears regularly. Malware will enter the network despite the most robust perimeter and host-based security systems. HIDS and other detection systems can create alerts on suspected malware that may have entered the network and executed on a host. Systems such as Cisco AMP can track the trajectory of a file through the network, and can “roll back” network events to obtain a copy of the downloaded file. This file can then be executed in a sandbox, such as Cisco Threat Grid Glovebox, and the activities of the file documented by the system. This information can then be used to create signatures to prevent the file from entering the network again. The information can also be used to create detection rules and automated plays that will identify other systems that have been infected.
Cuckoo Sandbox is a popular free malware analysis system sandbox. It can be run locally and have malware samples submitted to it for analysis. A number of other online public sandboxes exist. These services allow malware samples to be uploaded for analysis. Some of these services are VirusTotal, Joe Sandbox, and CrowdStrike Falcon Sandbox.
An interesting online tool is ANY.RUN, which is shown in the figure. It offers the ability to upload a malware sample for analysis like any online sandbox. However, it offers a very rich interactive reporting functionality that is full of details regarding the malware sample. ANY.RUN runs the malware and captures a series of screen shots of the malware if it has interactive elements that display on the sandbox computer screen. You can view public samples that have been submitted by ANY.RUN users to investigate information about newly discovered malware or malware that is currently circulating on the internet. Reports include network and internet activity of the malware, including HTTP requests and DNS queries. Files that are executed as part of the malware process are shown and rated for threat. Details are available for the files including multiple hash values, hexadecimal and ASCII views of the file contents, and the system changes made by the files. In addition, identifying indicators of compromise, such as the malware file hashes, DNS requests, and the IP connections that are made by the malware are also shown. Finally, the tactics taken by the malware are mapped to the MITRE ATT&CK Matrix with each tactic linked to details on the MITRE website.
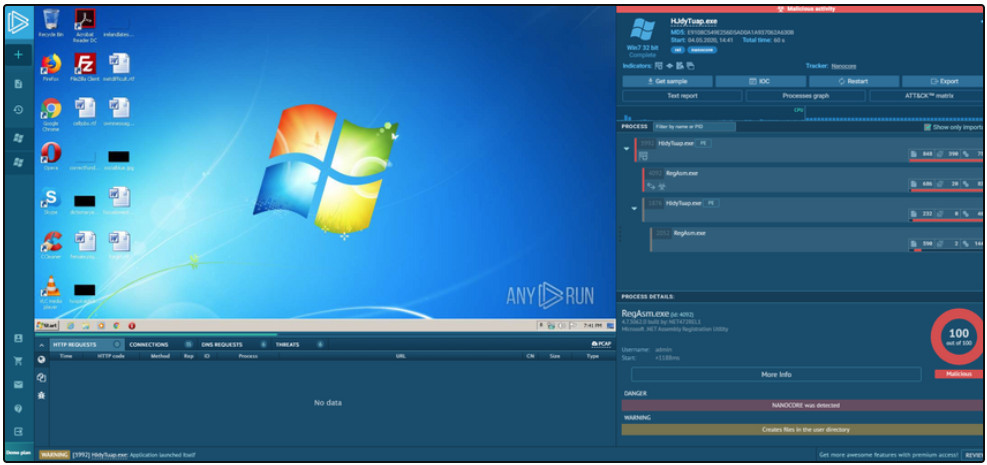
22.3.4 Video – Using a Sandbox to Launch Malware
Play the video to view a demonstration of using sandbox environment to launch and analyze a malware attack.
22.4 Endpoint Protection Summary
22.4.1 What Did I Learn in this Module?
Antimalware Protection
We can define endpoints as hosts on the network that can access or be accessed by other hosts on the network. This obviously includes computers and servers. With the rapid growth of the Internet of Things (IoT), other types of devices are now endpoints on the network. Each endpoint is a potential way for malicious software to gain access to a network. Not all endpoints are within a network. Many endpoints connect to networks remotely over VPN. The network perimeter is always expanding. Various network security devices are required to protect the network perimeter from outside access. However, many attacks originate from inside the network also. Therefore, securing an internal LAN is nearly as important as securing the outside network perimeter. After an internal host is infiltrated, it can become a starting point for an attacker to gain access to critical system devices. There are two internal LAN elements to secure: Endpoints and Network Infrastructure.
Antivirus/Antimalware Software is installed on a host to detect and mitigate viruses and malware. It does this using three different approaches, signature-based (using various characteristics of known malware files), heuristics-based (using general features shared by various types of malware), and behavior-based (using an analysis of suspicious behavior). Many antivirus programs are able to provide real-time protection by analyzing data as it is used by the endpoint. A Host-based Firewall restricts incoming and outgoing connections to connections initiated by that host only. Some firewall software can also prevent a host from becoming infected and stop infected hosts from spreading malware to other hosts. Most host-based security software includes logging functionality that is essential to cybersecurity operations. Network-based malware prevention devices are also capable of sharing information among themselves to make better informed decisions. Protecting endpoints in a borderless network can be accomplished using network-based, as well as host-based techniques.
Host-based Intrusion Prevention
Host-based firewalls may use a set of predefined policies, or profiles, to control packets entering and leaving a computer. They also may have rules that can be directly modified or created to control access based on addresses, protocols, and ports. They can also be configured to issue alerts if suspicious behavior is detected. Logging varies depending on the firewall application. It typically includes date and time of the event, whether the connection was allowed or denied, information about the source or destination IP addresses of packets, and the source and destination ports of the encapsulated segments. Distributed firewalls may also be used. They combine features of host-based firewalls with centralized management. Some examples of host-based firewalls include Windows Defender Firewall, iptables, nftables, and TCP Wrappers. A host-based intrusion detection system (HIDS) protects hosts against known and unknown malware. A HIDS can perform detailed monitoring and reporting on the system configuration and application activity, log analysis, event correlation, integrity checking, policy enforcement, rootkit detection, and alerting. A HIDS will frequently include a management server endpoint. Because the HIDS software must run directly on the host, it is considered an agent-based system. A HIDS uses both proactive and reactive strategies. A HIDS can prevent intrusion because it uses signatures to detect known malware and prevent it from infecting a system. Signatures are not effective against new, or zero day, threats. In addition, some malware families exhibit polymorphism. Additional strategies to detect the possibility of successful include anomaly-based detection and policy-based detection.
Application Security
An attack surface is the total sum of the vulnerabilities in a given system that is accessible to an attacker. It may consist of open ports on servers or hosts, software that is running on internet-facing servers, wireless network protocols, remote devices, and even users. The attack surface is continuing to expand. More devices are connecting to networks through the Internet of Things (IoT) and Bring Your Own Device (BYOD. The SANS Institute describes three components of the attack surface: Network Attack Surface, Software Attack Surface, and Human Attack Surface. One way of decreasing the attack surface is to limit access to potential threats by creating lists of prohibited applications. This is known as blacklisting. Application blacklists can dictate which user applications are not permitted to run on a computer. Similarly, whitelists can specify which programs are allowed to run. Whitelists are created in accordance with a security baseline that has been established by an organization. Blacklists can be manually created, or they can be obtained from various security services. Sandboxing is a technique that allows suspicious files to be executed and analyzed in a safe environment. Automated malware analysis sandboxes offer tools that analyze malware behavior. These tools observe the effects of running unknown malware so that features of malware behavior can be determined and then used to create defenses against it. Polymorphic malware changes frequently and new malware appears regularly. Malware will enter the network despite the most robust perimeter and host-based security systems. HIDS and other detection systems can create alerts on suspected malware that may have entered the network and executed on a host.
