23.0 Introduction
23.0.1 Why Should I Take this Module?
How much money should an organization spend on network security and cyberoperations? How does an organization know how much effort and resources to put into keeping the network and data safe? These questions can be answered through the assessment of risk and vulnerability. Cybersecurity analysts and security experts use a variety of tools to perform vulnerability assessments. Network and device profiling provide a baseline that serves as a reference point for identifying deviations from normal operations. Similarly, server profiling is used to establish the accepted operating state of servers. Organizations use the Common Vulnerability Scoring System (CVSS) for weighting the risks of a vulnerability using a variety of metrics. Organizations then apply risk management techniques to select and specify its security controls. Organizations use an Information Security Management System (ISMS) to identify, analyze, and address information security risks. This module covers details of network and server profiling, CVSS, risk management techniques, and ISMS.
23.0.2 What Will I Learn in this Module?
Module Title: Endpoint Vulnerability Assessment
Module Objective: Explain how endpoint vulnerabilities are assessed and managed.
| Topic Title | Topic Objective |
|---|---|
| Network and Server Profiling | Explain the value of network and server profiling. |
| Common Vulnerability Scoring System (CVSS) | Explain how CVSS reports are used to describe security vulnerabilities. |
| Secure Device Management | Explain how secure device management techniques are used to protect data and assets. |
| Information Security Management Systems | Explain how information security management systems are used to protect assets. |
23.1 Network and Server Profiling
23.1.1 Network Profiling
In order to detect serious security incidents, it is important to understand, characterize, and analyze information about normal network functioning. Networks, servers, and hosts all exhibit typical behavior for a given point in time. Network and device profiling can provide a statistical baseline that serves as a reference point. Unexplained deviations from the baseline may indicate a compromise.
Care must be taken when capturing baseline data so that all normal network operations are included in the baseline. In addition, it is important that the baseline is current. It should not include network performance data that is no longer part of normal functioning. For example, rises in network utilization during periodic server backup operations is part of normal network functioning and should be part of the baseline data. However, measurement of traffic that corresponds to outside access to an internal server that has been moved to the cloud would not be. A means of capturing just the right period for baseline measurement is known as sliding window anomaly detection. It defines a window that is most representative of network operation and deletes data that is out of date. This process continues with repeated baseline measurements to ensure that baseline measurement statistics depict network operation with maximum accuracy.
Increased utilization of WAN links at unusual times can indicate a network breach and exfiltration of data. Hosts that begin to access obscure internet servers, resolve domains that are obtained through dynamic DNS, or use protocols or services that are not needed by the system user can also indicate compromise. Deviations in network behavior are difficult to detect if normal behavior is not known.
Tools like NetFlow and Wireshark can be used to characterize normal network traffic characteristics. Because organizations can make different demands on their networks depending on the time of day or day of the year, network baselining should be carried out over an extended period. The figure displays some questions to ask when establishing a network baseline.
Elements of a Network Profile
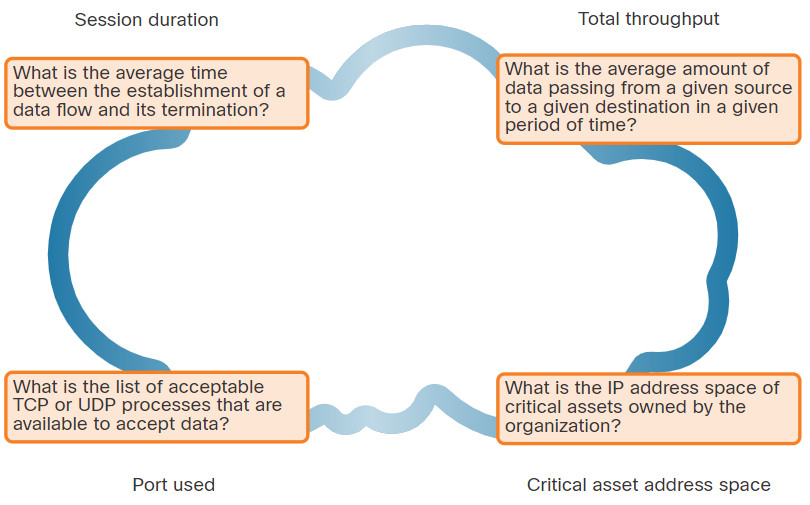
The table lists important elements of the network profile.
| Network Profile Element | Description |
|---|---|
| Session duration | This is the time between the establishment of a data flow and its termination. |
| Total throughput | This is the amount of data passing from a given source to a given destination in a given period of time. |
| Ports used | This is a list of TCP or UDP processes that are available to accept data. |
| Critical asset address space | These are the IP addresses or the logical location of essential systems or data. |
In addition, a profile of the types of traffic that typically enter and leave the network is an important tool in understanding network behavior. Malware can use unusual ports that may not be typically seen during normal network operation. Host-to-host traffic is another important metric. Most network clients communicate directly with servers, so an increase of traffic between clients can indicate that malware is spreading laterally through the network.
Finally, changes in user behavior, as revealed by AAA, server logs, or a user profiling system like Cisco Identity Services Engine (ISE) is another valuable indicator. Knowing how individual users typically use the network leads to detection of potential compromise of user accounts. A user who suddenly begins logging in to the network at strange times from a remote location should raise alarms if this behavior is a deviation from a known norm.
23.1.2 Server Profiling
Server profiling is used to establish the accepted operating state of servers. A server profile is a security baseline for a given server. It establishes the network, user, and application parameters that are accepted for a specific server.
In order to establish a server profile, it is important to understand the function that a server is intended to perform in a network. From there, various operating and usage parameters can be defined and documented.
The table lists elements of a server profile.
| Server Profile Element | Description |
|---|---|
| Listening ports | These are the TCP and UDP daemons and ports that are normally allowed to be open on the server. |
| Logged in users and accounts | These are the parameters defining user access and behavior. |
| Service accounts | These are the definitions of the type of service that an application is allowed to run. |
| Software environment | These are the tasks, processes, and applications that are permitted to run on the server. |
23.1.3 Network Anomaly Detection
Network behavior is described by a large amount of diverse data such as the features of packet flow, features of the packets themselves, and telemetry from multiple sources. One approach to detection of network attacks is the analysis of this diverse, unstructured data using Big Data analytics techniques. This is known as network behavior analysis (NBA).
This entails the use of sophisticated statistical and machine learning techniques to compare normal performance baselines with network performance at a given time. Significant deviations can be indicators of compromise. In addition, network behavior can be analyzed for known network behaviors that indicate compromise.
Anomaly detection can recognize network traffic caused by worm activity that exhibits scanning behavior. Anomaly detection also can identify infected hosts on the network that are scanning for other vulnerable hosts.
The figure illustrates a simplified version of an algorithm designed to detect an unusual condition at the border routers of an enterprise.
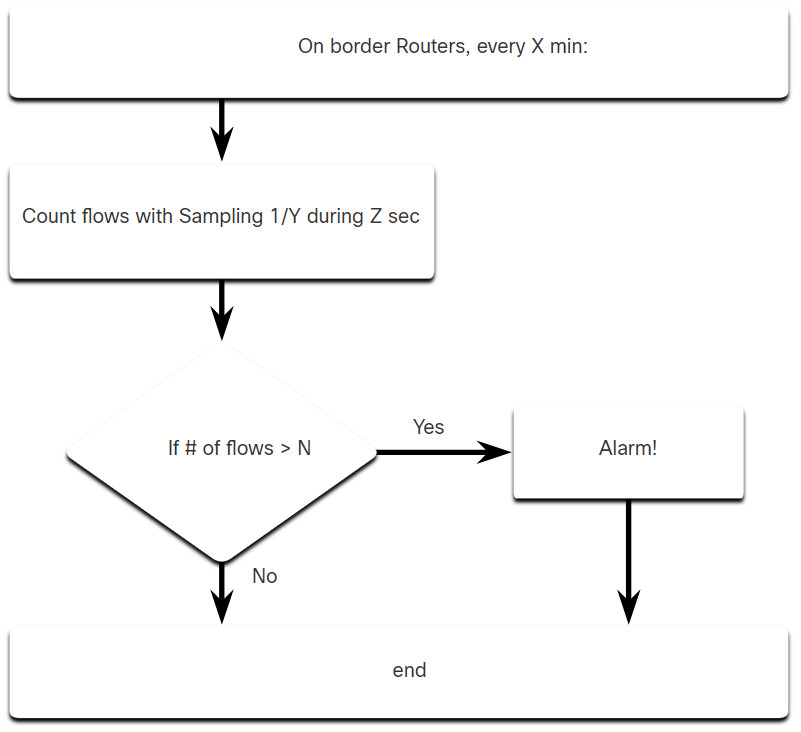
For example, the cybersecurity analyst could provide the following values:
- X = 5
- Y = 100
- Z = 30
- N = 500
Now, the algorithm can be interpreted as: Every 5th minute, get a sampling of 1/100th of the flows during second 30. If the number of flows is greater than 500, generate an alarm. If the number of flows is less than 500, do nothing. This is a simple example of using a traffic profile to identify the potential for data loss.
In addition to statistical and behavioral approaches to anomaly detection is rule-based anomaly detection. Rule-based detection analyzes decoded packets for attacks based on pre-defined patterns.
23.1.4 Network Vulnerability Testing
Most organizations connect to public networks in some way due to the need to access the internet. These organizations must also provide internet facing services of various types to the public. Because of the vast number of potential vulnerabilities, and the fact that new vulnerabilities can be created within an organization network and its internet facing services, periodic security testing is essential.
The table lists various types of tests that can be performed.
| Term | Description |
|---|---|
| Risk Analysis |
|
| Vulnerability Assessment |
|
| Penetration Testing |
|
The table lists examples of activities and tools that are used in vulnerability testing.
| Activity | Description | Tools |
|---|---|---|
| Risk analysis | Individuals conduct comprehensive analysis of impacts of attacks on core company assets and functioning | Internal or external consultants, risk management frameworks |
| Vulnerability Assessment | Patch management, host scans, port scanning, other vulnerability scans and services | OpenVas, Microsoft Baseline Analyzer, Nessus, Qualys, Nmap |
| Penetration Testing | Use of hacking techniques and tools to penetrate network defenses and identify depth of potential penetration | Metasploit, CORE Impact, ethical hackers |
23.2 Common Vulnerability Scoring System (CVSS)
23.2.1 CVSS Overview
The Common Vulnerability Scoring System (CVSS) is a risk assessment tool that is designed to convey the common attributes and severity of vulnerabilities in computer hardware and software systems. The third revision, CVSS 3.0, is a vendor-neutral, industry standard, open framework for weighting the risks of a vulnerability using a variety of metrics. These weights combine to provide a score of the risk inherent in a vulnerability. The numeric score can be used to determine the urgency of the vulnerability, and the priority of addressing it. The benefits of the CVSS can be summarized as follows:
- It provides standardized vulnerability scores that should be meaningful across organizations.
- It provides an open framework with the meaning of each metric openly available to all users.
- It helps prioritize risk in a way that is meaningful to individual organizations.
The Forum of Incident Response and Security Teams (FIRST) has been designated as the custodian of the CVSS to promote its adoption globally. The Version 3 standard was developed with contributions by Cisco and other industry partners. Version 3.1 was released in June of 2019. The figure displays the specification page for the CVSS at the FIRST website.
23.2.2 CVSS Metric Groups
Before performing a CVSS assessment, it is important to know key terms that are used in the assessment instrument.
Many of the metrics address the role of what the CVSS calls an authority. An authority is a computer entity, such as a database, operating system, or virtual sandbox, that grants and manages access and privileges to users.
CVSS Metric Groups
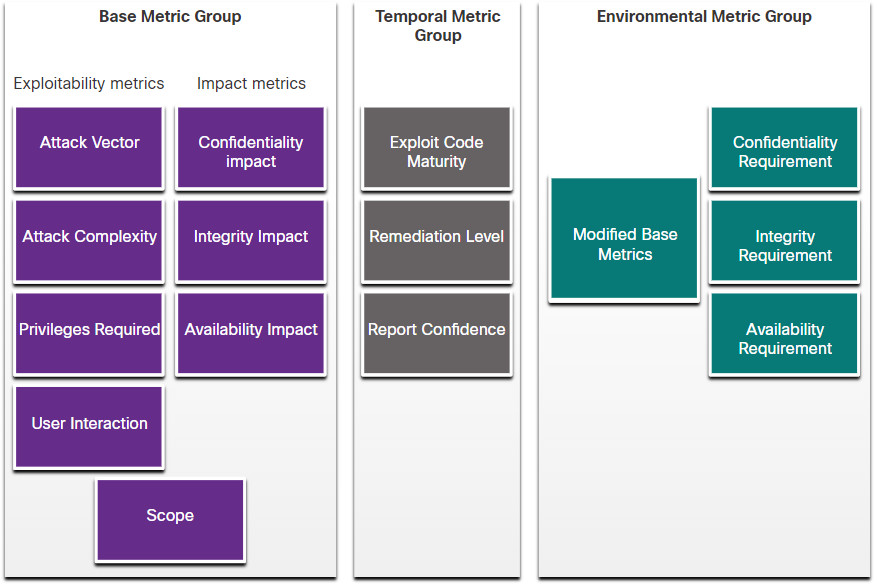
As shown in the figure, the CVSS uses three groups of metrics to assess vulnerability.
23.2.3 CVSS Base Metric Group
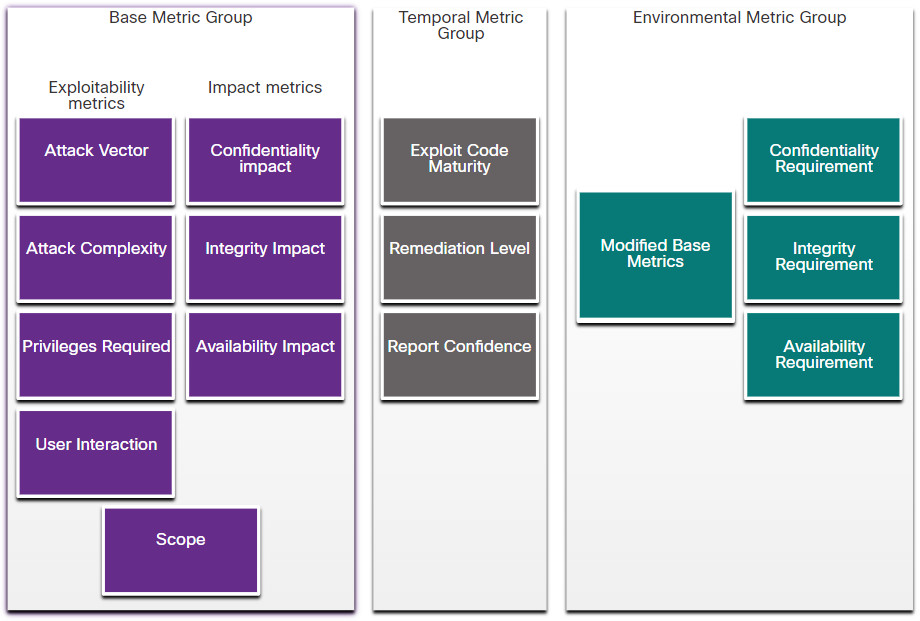
The figure highlights the Base Metric Group.
CVSS Metric Groups
The table lists the criteria for the Base Metric Group Exploitability metrics.
| Criteria | Description |
|---|---|
| Attack vector | This is a metric that reflects the proximity of the threat actor to the vulnerable component. The more remote the threat actor is to the component, the higher the severity. Threat actors close to your network or inside your network are easier to detect and mitigate. |
| Attack complexity | This is a metric that expresses the number of components, software, hardware, or networks, that are beyond the attacker’s control and that must be present for a vulnerability to be successfully exploited. |
| Privileges required | This is a metric that captures the level of access that is required for a successful exploit of the vulnerability. |
| User interaction | This metric expresses the presence or absence of the requirement for user interaction for an exploit to be successful. |
| Scope | This metric expresses whether multiple authorities must be involved in an exploit. This is expressed as whether the initial authority changes to a second authority during the exploit. |
The Base Metric Group Impact metrics increase with the degree or consequence of loss due to the impacted component. The table lists the impact metric components.
| Term | Description |
|---|---|
| Confidentiality Impact | This is a metric that measures the impact to confidentiality due to a successfully exploited vulnerability. Confidentiality refers to the limiting of access to only authorized users. |
| Integrity Impact | This is a metric that measures the impact to integrity due to a successfully exploited vulnerability. Integrity refers to the trustworthiness and authenticity of information. |
| Availability Impact | This is a metric that measures the impact to availability due to a successfully exploited vulnerability. Availability refers to the accessibility of information and network resources. Attacks that consume network bandwidth, processor cycles, or disk space all impact the availability. |
23.2.4 The CVSS Process
The CVSS Base Metrics Group is designed as a way to assess security vulnerabilities that are found in software and hardware systems. It describes the severity of a vulnerability based on the characteristics of a successful exploit of the vulnerability. The other metric groups modify the base severity score by accounting for how the base severity rating is affected by time and environmental factors.
The CVSS process uses a tool called the CVSS v3.1 Calculator, shown in the figure.
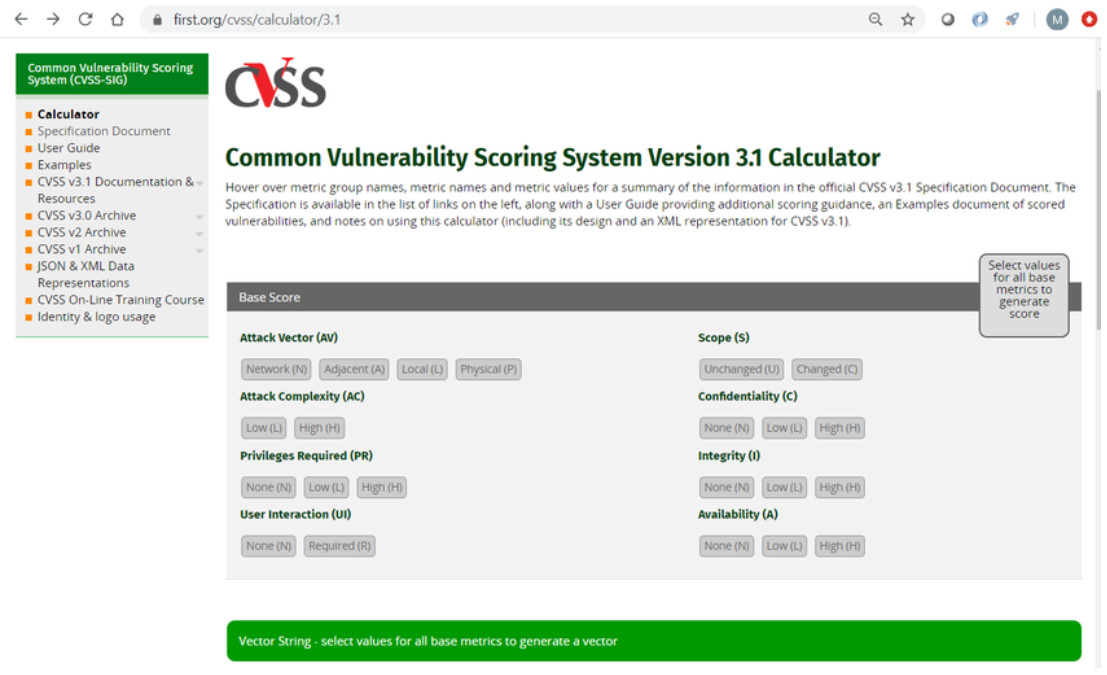
The calculator is like a questionnaire in which choices are made that describe the vulnerability for each metric group. After all choices are made, a score is generated. Pop-up text that explains each metric and metric value is displayed by hovering the mouse over each. Choices are made by choosing one of the values for the metric. Only one choice can be made per metric.
The CVSS calculator can be accessed on the CVSS portion of the FIRST website.
A detailed user guide that defines metric criteria, examples of assessments of common vulnerabilities, and the relationship of metric values to the final score is available to support the process.
After the Base Metric group is completed, the numeric severity rating is displayed, as shown in the figure.
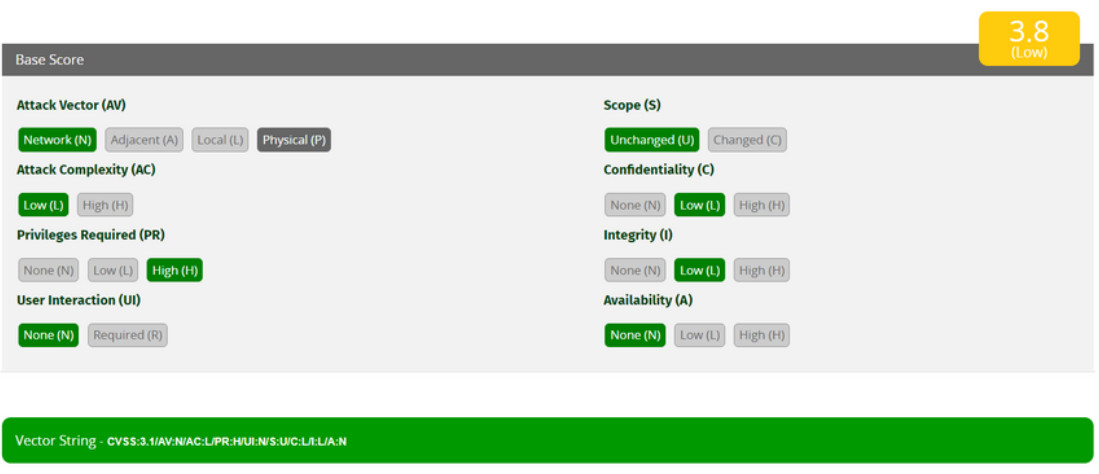
A vector string is also created that summarizes the choices made. If other metric groups are completed, those values are appended to the vector string. The string consists of the initial(s) for the metric, and an abbreviated value for the selected metric value separated by a colon. The metric-value pairs are separated by slashes. The vector strings allow the results of the assessment to be easily shared and compared.
The table lists the key for the Base Metric group.
| Metric Name | Initials | Possible Values | Values |
|---|---|---|---|
| Attack Vector | AV | [N, A, L, P] | N = Network A = Adjacent L = Local P = Physical |
| Attack Complexity | AC | [L, H] | L = Low H = High |
| Privileges Required | PR | [N, L, H] | N = None L = Low H = High |
| User Interaction | UI | [N, R] | N = None R = Required |
| Scope | S | [U, C] | U = Unchanged C = Changed |
| Confidentiality Impact | C | [H, L, N] | H = High L = Low N = None |
| Integrity Impact | I | [H, L, N] | H = High L = Low N = None |
| Availability Impact | A | [H, L, N] | H = High L = Low N = None |
The values for the numeric severity rating string CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:L/I:L/A:N are listed in the table.
| Metric Name | Values |
|---|---|
| Attack Vector, AV | Network |
| Attack Complexity, AC | Low |
| Privileges Required, PR | High |
| User Interaction, UI | None |
| Scope, S | Unchanged |
| Confidentiality Impact, C | Low |
| Integrity Impact, I | Low |
| Availability Impact, A | None |
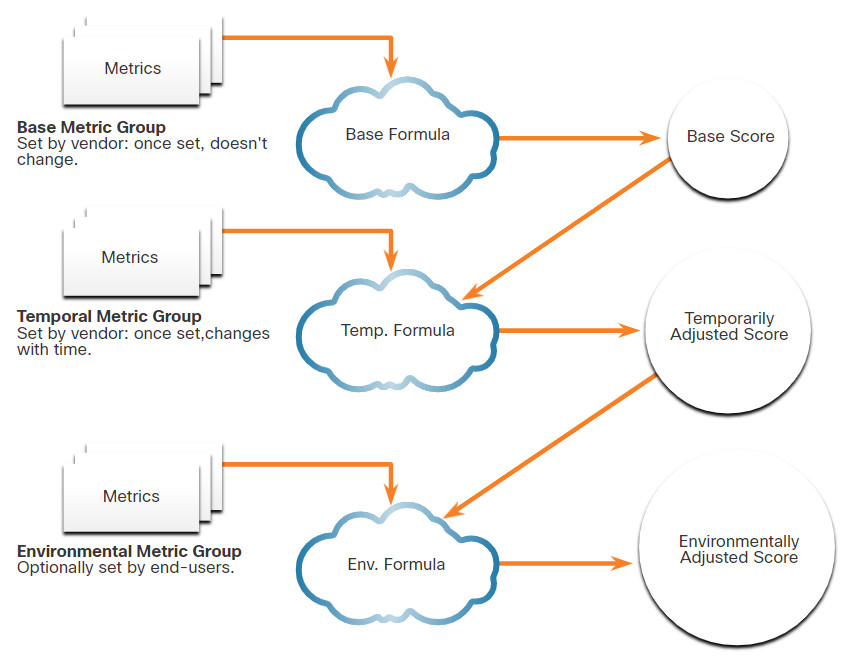
In order for a score to be calculated for the Temporal or Environmental metric groups, the Base Metric group must first be completed. The Temporal and Environmental metric values then modify the Base Metric results to provide an overall score. The interaction of the scores for the metric groups is shown in the figure.
23.2.5 CVSS Reports
The ranges of scores and the corresponding qualitative meaning is shown in the table.
| Rating | CVSS Score |
|---|---|
| None | 0 |
| Low | 0.1 – 3.9 |
| Medium | 4.0 – 6.9 |
| High | 7.0 – 8.9 |
| Critical | 9.0 – 10.0 |
Frequently, the Base and Temporal metric group scores will be supplied to customers by the application or security vendor in whose product the vulnerability has been discovered. The affected organization completes the environmental metric group to tailor the vendor-supplied scoring to the local context.
The resulting score serves to guide the affected organization in the allocation of resources to address the vulnerability. The higher the severity rating, the greater the potential impact of an exploit and the greater the urgency in addressing the vulnerability. While not as precise as the numeric CVSS scores, the qualitative labels are very useful for communicating with stakeholders who are unable to relate to the numeric scores.
In general, any vulnerability that exceeds 3.9 should be addressed. The higher the rating level, the greater the urgency for remediation.
23.2.6 Other Vulnerability Information Sources
There are other important vulnerability information sources. These work together with the CVSS to provide a comprehensive assessment of vulnerability severity. There are two systems that operate in the United States:
Common Vulnerabilities and Exposures (CVE)
This is a dictionary of common names, in the form of CVE identifiers, for known cybersecurity vulnerabilities. The CVE identifier provides a standard way to research a reference to vulnerabilities. When a vulnerability has been identified, CVE identifiers can be used to access fixes. In addition, threat intelligence services use CVE identifiers, and they appear in various security system logs. The CVE Details website provides a linkage between CVSS scores and CVE information. It allows browsing of CVE vulnerability records by CVSS severity rating.
Search the internet for Mitre for more information on CVE as shown in the figure.
National Vulnerability Database (NVD)
This utilizes CVE identifiers and supplies additional information on vulnerabilities such as CVSS threat scores, technical details, affected entities, and resources for further investigation. The database was created and is maintained by the U.S. government National Institute of Standards and Technology (NIST) agency.
23.3 Secure Device Management
23.3.1 Risk Management
Risk management involves the selection and specification of security controls for an organization. It is part of an ongoing organization-wide information security program that involves the management of the risk to the organization or to individuals associated with the operation of a system.
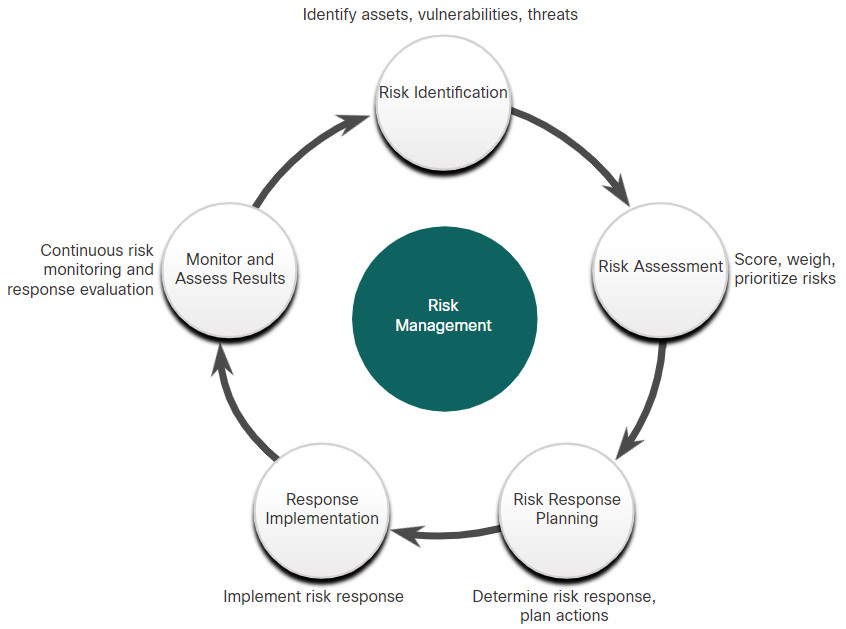
Risk management is an ongoing, multi-step, cyclical process, as shown in the figure.
A Risk Management Process
Risk is determined as the relationship between threat, vulnerability, and the nature of the organization. It first involves answering the following questions as part of a risk assessment:
- Who are the threat actors who want to attack us?
- What vulnerabilities can threat actors exploit?
- How would we be affected by attacks?
- What is the likelihood that different attacks will occur?
NIST Special Publication 800-30 describes risk assessment as:
…the process of identifying, estimating, and prioritizing information security risks. Assessing risk requires the careful analysis of threat and vulnerability information to determine the extent to which circumstances or events could adversely impact an organization and the likelihood that such circumstances or events will occur.
The full publication is available for download from NIST.
A mandatory activity in risk assessment is the identification of threats and vulnerabilities and the matching of threats with vulnerabilities in what is often called threat-vulnerability (T-V) pairing. The T-V pairs can then be used as a baseline to indicate risk before security controls are implemented. This baseline can then be compared to ongoing risk assessments as a means of evaluating risk management effectiveness. This part of risk assessment is referred to as determining the inherent risk profile of an organization.
After the risks are identified, they may be scored or weighted as a way of prioritizing risk reduction strategies. For example, vulnerabilities that are found to have corresponded with multiple threats can receive higher ratings. In addition, T-V pairs that map to the greatest institutional impact will also receive higher weightings.
The table lists the four potential ways to respond to risks that have been identified, based on their weightings or scores.
| Risk | Description |
|---|---|
| Risk avoidance |
|
| Risk reduction |
|
| Risk sharing |
|
| Risk retention |
|
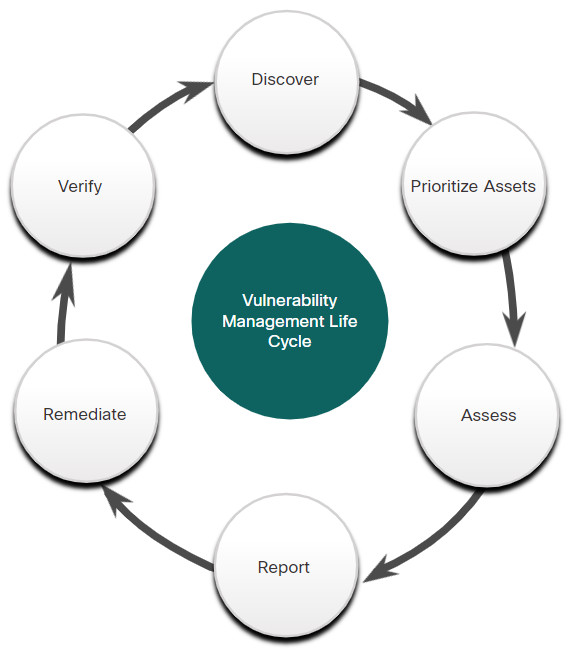
23.3.3 Vulnerability Management
According to NIST, vulnerability management is a security practice that is designed to proactively prevent the exploitation of IT vulnerabilities that exist within an organization. The expected result is to reduce the time and money spent dealing with vulnerabilities and the exploitation of those vulnerabilities. Proactively managing vulnerabilities of systems will reduce or eliminate the potential for exploitation and involve considerably less time and effort than responding after an exploitation has occurred.
Vulnerability management requires a robust means of identifying vulnerabilities based on vendor security bulletins and other information systems such as CVE. Security personnel must be competent in assessing the impact, if any, of vulnerability information they have received. Solutions should be identified with effective means of implementing and assessing the unanticipated consequences of implemented solutions. Finally, the solution should be tested to verify that the vulnerability has been eliminated.
Vulnerability Management Life Cycle
23.3.4 Asset Management
Asset management involves the implementation of systems that track the location and configuration of networked devices and software across an enterprise. As part of any security management plan, organizations must know what equipment accesses the network, where that equipment is within the enterprise and logically on the network, and what software and data those systems store or can access. Asset management not only tracks corporate assets and other authorized devices, but also can be used to identify devices that are not authorized on the network.
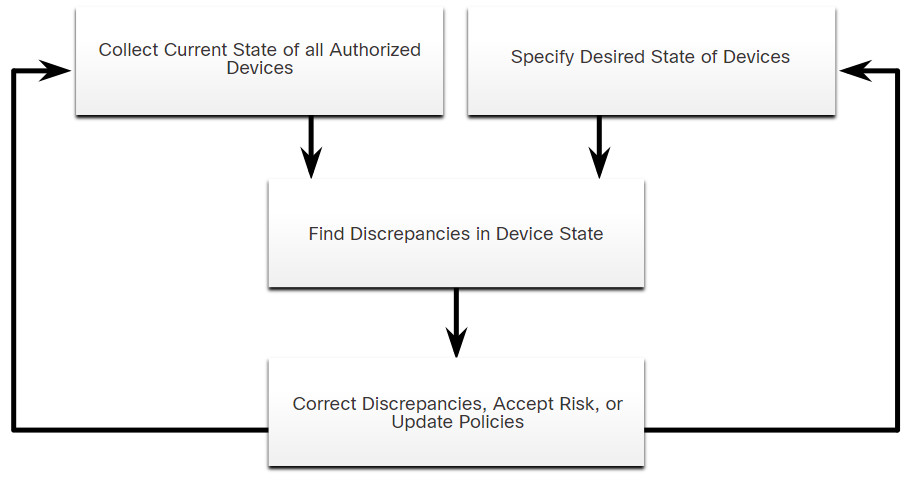
NIST specifies in publication NISTIR 8011 Volume 2, the detailed records that should be kept for each relevant device. NIST describes potential techniques and tools for operationalizing an asset management process:
- Automated discovery and inventory of the actual state of devices
- Articulation of the desired state for those devices using policies, plans, and procedures in the organization’s information security plan
- Identification of non-compliant authorized assets
- Remediation or acceptance of device state, possible iteration of desired state definition
- Repeat the process at regular intervals, or ongoing
The figure provides an overview of this process.
23.3.5 Mobile Device Management
Mobile device management (MDM), especially in the age of BYOD, presents special challenges to asset management. Mobile devices cannot be physically controlled on the premises of an organization. They can be lost, stolen, or tampered with, putting data and network access at risk. Part of an MDM plan is acting when devices leave the custody of the responsible party. Measures that can be taken include disabling the lost device, encrypting the data on the device, and enhancing device access with more robust authentication measures.
Due to the diversity of mobile devices it is possible that some devices that will be used on the network are inherently less secure than others. Network administrators should assume that all mobile devices are untrusted until they have been properly secured by the organization.
MDM systems, such as Cisco Meraki Systems Manager, shown in the figure, allow security personnel to configure, monitor and update a very diverse set of mobile clients from the cloud.
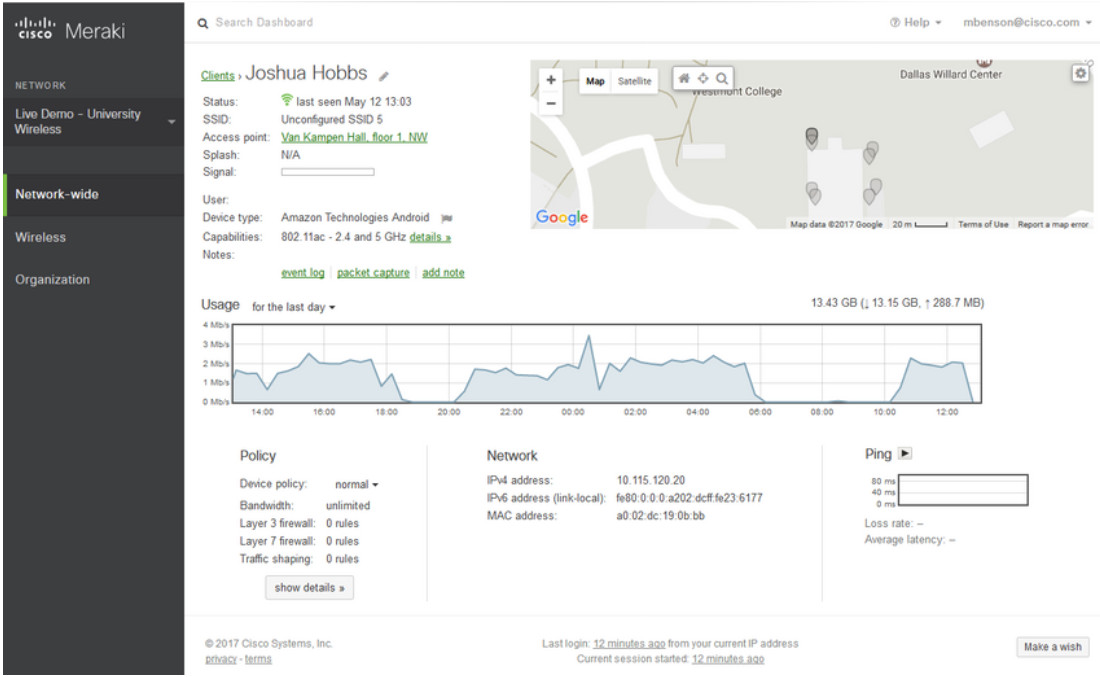
23.3.6 Configuration Management
Configuration management addresses the inventory and control of hardware and software configurations of systems. Secure device configurations reduce security risk. For example, an organization provides many computers and laptops to its workers. This enlarges the attack surface for the organization, because each system may be vulnerable to exploits. To manage this, the organization may create baseline software images and hardware configurations for each type of machine. These images may include a basic package of required software, endpoint security software, and customized security policies that control user access to aspects of the system configuration that could be made vulnerable. Hardware configurations may specify the permitted types of network interfaces and the permitted types of external storage.
Configuration management extends to the software and hardware configuration of networking devices and servers as well. As defined by NIST, configuration management:
Comprises a collection of activities focused on establishing and maintaining the integrity of products and systems, through control of the processes for initializing, changing, and monitoring the configurations of those products and systems.
NIST Special Publication 800-128 on configuration management for network security is available for download from NIST.
For internetworking devices, software tools are available that will backup configurations, detect changes in configuration files, and enable bulk change of configurations across a number of devices.
With the advent of cloud data centers and virtualization, management of numerous servers presents special challenges. Tools like Puppet, Chef, Ansible, and SaltStack enable efficient management of servers that are used in cloud-based computing.
23.3.7 Enterprise Patch Management
Patch management is related to vulnerability management. Vulnerabilities frequently appear in critical client, server, and networking device operating systems and firmware. Application software, especially internet applications and frameworks like Acrobat, Flash, and Java, also are frequently discovered to have vulnerabilities. Patch management involves all aspects of software patching, including identifying required patches, acquiring, distributing, installing, and verifying that the patch is installed on all required systems. Installing patches is frequently the most effective way to mitigate software vulnerabilities. Sometimes, they are the only way to do so.
Patch management is required by some compliance regulations, such as Sarbanes Oxley (SOX) and the Health Insurance Portability and Accountability Act (HIPAA). Failure to implement patches in a systematic and timely manner could result in audit failure and penalties for non-compliance. Patch management depends on asset management data to identify systems that are running software that requires patching. Patch management software is available from companies such as SolarWinds and LANDesk. Microsoft System Center Configuration Manager (SCCM) is an enterprise-level tool for automated distribution of patches to a large number of Microsoft Windows workstations and servers.
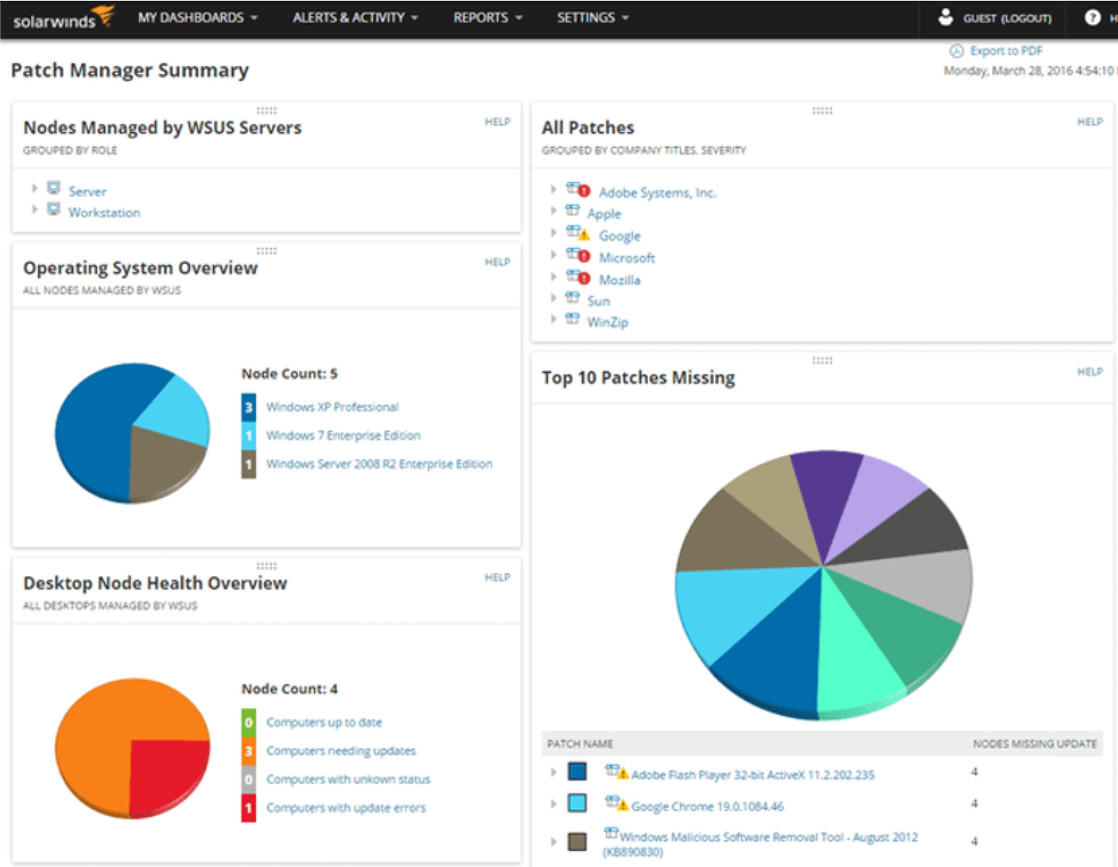
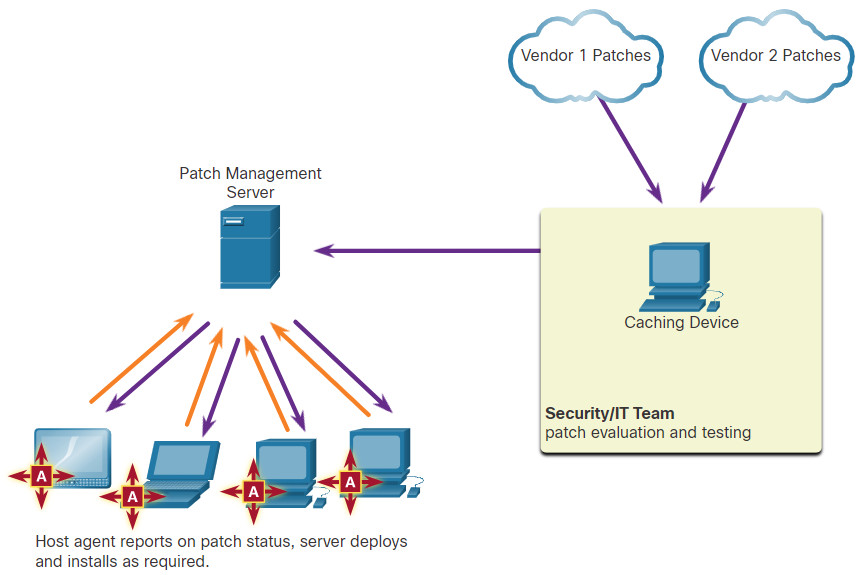
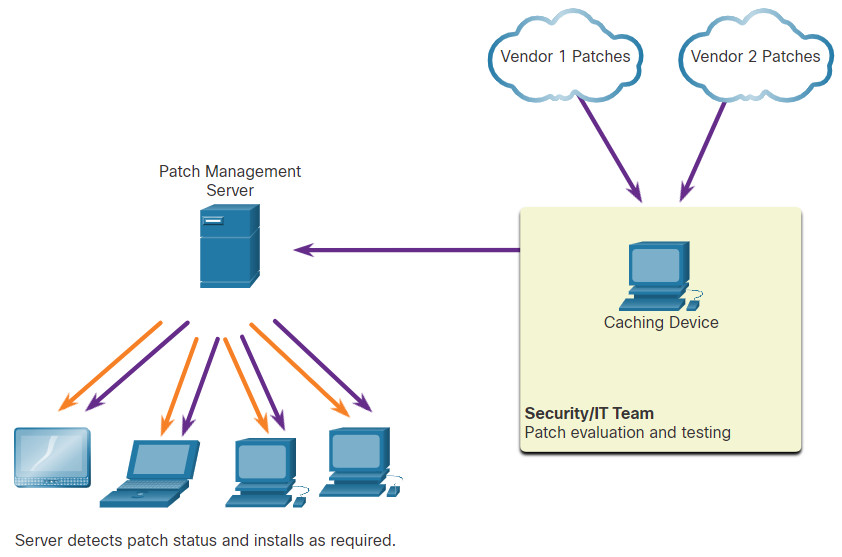
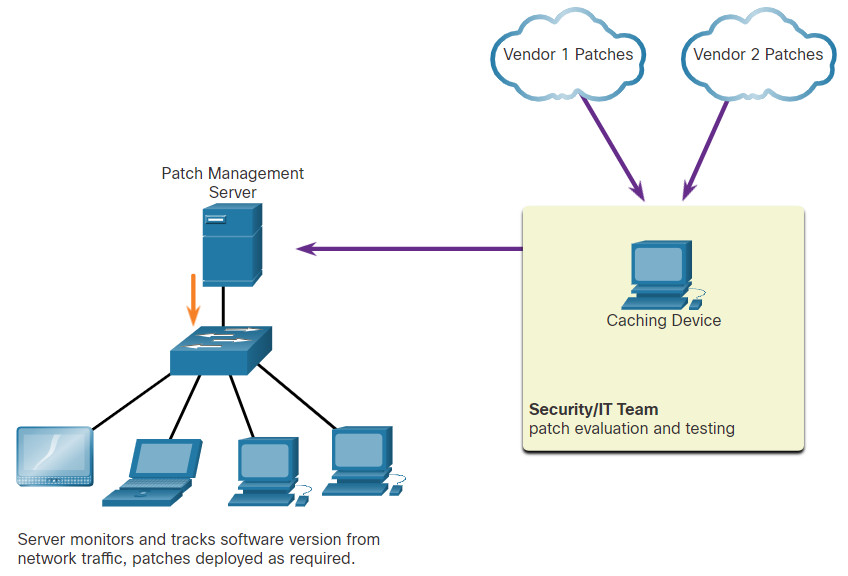
23.3.8 Patch Management Techniques
23.4 Information Security Management Systems
23.4.1 Security Management Systems
An Information Security Management System (ISMS) consists of a management framework through which an organization identifies, analyzes, and addresses information security risks. ISMSs are not based in servers or security devices. Instead, an ISMS consists of a set of practices that are systematically applied by an organization to ensure continuous improvement in information security. ISMSs provide conceptual models that guide organizations in planning, implementing, governing, and evaluating information security programs.
ISMSs are a natural extension of the use of popular business models, such as Total Quality Management (TQM) and Control Objectives for Information and Related Technologies (COBIT), into the realm of cybersecurity.
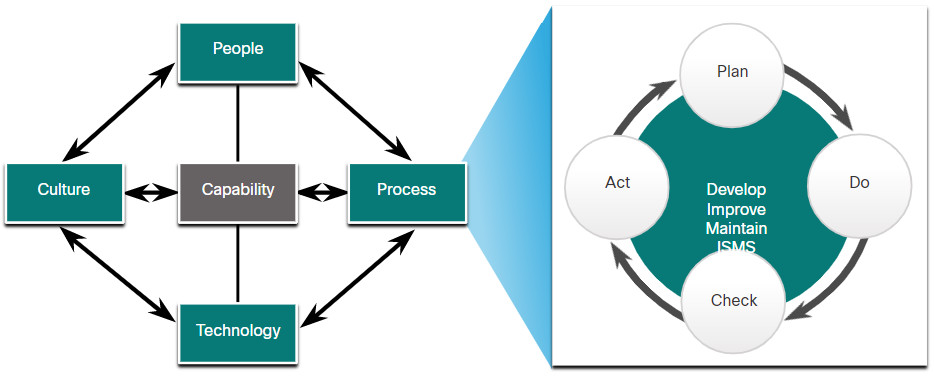
An ISMS is a systematic, multi-layered approach to cybersecurity. The approach includes people, processes, technologies, and the cultures in which they interact in a process of risk management.
An ISMS often incorporates the “plan-do-check-act” framework, known as the Deming cycle, from TQM. It is seen as an elaboration on the process component of the People-Process-Technology-Culture model of organizational capability, as shown in the figure.
A General Model for Organizational Capability
23.4.2 ISO-27001
ISO is the International Organization for Standardization. ISO’s voluntary standards are internationally accepted and facilitate business conducted between nations.
ISO partnered with the International Electrotechnical Commission (IEC) to develop the ISO/IEC 27000 series of specifications for ISMSs, as shown in the table.
| Standard | Description |
|---|---|
| ISO/IEC 27000 | Information security management systems – Overview and vocabulary – Introduction to the standards family, overview of ISMS, essential vocabulary. |
| ISO/IEC 27001 | Information security management systems – Requirements – Provides an overview of ISMS and the essentials of ISMS processes and procedures. |
| ISO/IEC 27003 | Information security management system implementation guidance – Critical factors necessary for successful design and implementation of ISMS. |
| ISO/IEC 27004 | Information security management – Monitoring, measurement, analysis and evaluation – Discussion of metrics and measurement procedures to assess effectiveness of ISMS implementation. |
| ISO/IEC 27005 | Information security risk management – Supports the implementation of ISMS based on a risk-centered management approach. |
The ISO 27001 certification is a global, industry-wide specification for an ISMS. The figure illustrates the relationship of actions stipulated by the standard with the plan-do-check-act cycle.
ISO 27001 ISMS Plan-Do-Check-Act Cycle
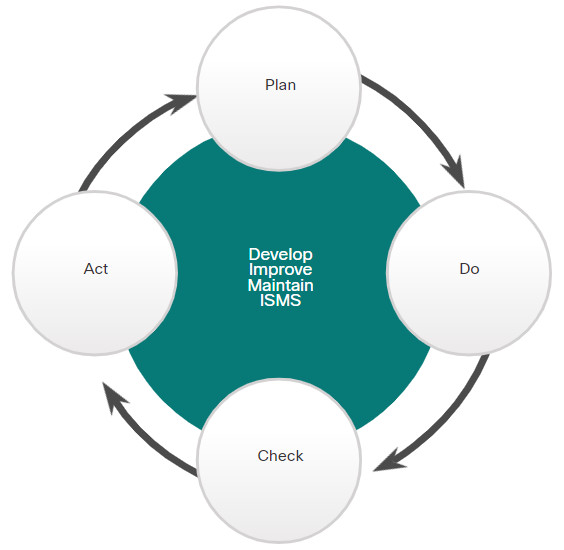
ISO-27001 certification means an organization’s security policies and procedures have been independently verified to provide a systematic and proactive approach for effectively managing security risks to confidential customer information.
23.4.3 NIST Cybersecurity Framework
NIST is very effective in the area of cybersecurity, as we have seen in this module. More NIST standards will be discussed later in the course.
NIST has also developed the Cybersecurity framework which is similar to the ISO/IEC 27000 standards. The NIST framework is a set of standards designed to integrate existing standards, guidelines, and practices to help better manage and reduce cybersecurity risk. The framework was first issued in February 2014 and continues to undergo development.
The framework core consists of a set of activities suggested to achieve specific cybersecurity outcomes, and references examples of guidance to achieve those outcomes. The core functions, which are defined in the table, are split into major categories and subcategories.
| Core Function | Description |
|---|---|
| IDENTIFY | Develop an organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities. |
| PROTECT | Develop and implement the appropriate safeguards to ensure delivery of critical infrastructure services. |
| DETECT | Develop and implement the appropriate activities to identify the occurrence of a cybersecurity event. |
| RESPOND | Develop and implement the appropriate activities to act on a detected cybersecurity event. |
| RECOVER | Develop and implement the appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity event. |
The major categories provide an understanding of the types of activities and outcomes related to each function, as shown in the next table.
| Core Function | Outcome Categories |
|---|---|
| IDENTIFY |
|
| PROTECT |
|
| DETECT |
|
| RESPOND |
|
| RECOVER |
|
Organizations of many types are using the Framework in a number of ways. Many have found it helpful in raising awareness and communicating with stakeholders within their organization, including executive leadership. The Framework is also improving communications across organizations, allowing cybersecurity expectations to be shared with business partners, suppliers, and among sectors. By mapping the Framework to current cybersecurity management approaches, organizations are learning and showing how they match up with the Framework’s standards, guidelines, and best practices. Some parties are using the Framework to reconcile internal policy with legislation, regulation, and industry best practice. The Framework also is being used as a strategic planning tool to assess risks and current practices.
Search the internet for to learn more about the NIST Cybersecurity Framework.
23.5 Endpoint Vulnerability Assessment Summary
23.5.1 What Did I Learn in this Module?
Network and Server Profiling
It is important to perform network and device profiling to provide statistical baseline information that can serve as a reference point for normal network and device performance. Important elements of the network profile include session duration, total throughput, ports used and critical asset address space. Server profiling is used to establish the accepted operating state of servers. A server profile is a security baseline for a given server. It establishes the network, user, and application parameters that are accepted for a specific server. Network behavior is described by a large amount of diverse data such as the features of packet flow, features of the packets themselves, and telemetry from multiple sources. Big data analytics can be used to perform statistical, behavioral, and rule-based anomaly detection.
Network security can be evaluated using a variety of tools and services. Risk analysis is the evaluation of the risk posed by vulnerabilities to a specific organization. Vulnerability assessment uses software to scan Internet-facing servers and internal networks for various types of vulnerabilities. Penetration testing uses authorized simulated attacks to test the strength of network security.
Common Vulnerability Scoring System (CVSS)
The Common Vulnerability Scoring System (CVSS) is a vendor-neutral, industry standard, open framework for rating the risks of a given vulnerability by using a variety of metrics to calculate a composite score. CVSS produces standardized vulnerability scores that should be meaningful across organizations. It is an open framework with the meaning of each metric openly available to all users. It allows prioritization of risk in a way that is meaningful to individual organizations. CVSS uses three groups of metrics to assess vulnerability. The metric groups are the base metric group, the temporal metric group, and the environmental metric group. The base metric group is designed as a way to assess security vulnerabilities that are found in software and hardware systems. Vulnerabilities are rated according to the attack vector, attack complexity, privileges required, user interaction, and scope. The temporal and environmental groups modify the base metric score according to the history of the vulnerability and the context of the specific organization. A CVSS calculator tool is available on the FIRST website. The CVSS calculator yields a number that describes the severity of the risk that is posed by the vulnerability. Scores range from zero to ten. Ranges of scores have qualitative values of none, low, medium, high, or critical risk. In general, any vulnerability that exceeds 3.9 should be addressed. The higher the rating level, the greater the urgency for remediation. Other important vulnerability information sources include Common Vulnerabilities and Exposures (CVE) and the National Vulnerability Database (NVD), both of which are available online.
Secure Device Management
Risk management involves the selection and specification of security controls for an organization. There are four potential ways to respond to risks, Risk avoidance means discontinuing the vulnerable activity, system, or service because the risk is too high. Risk reduction means taking measures to mitigate the risk in order to limit its impact. Risk sharing means outsourcing responsibility for the risk or using insurance to cover damages caused by the risk. Risk retention means accepting the risk and taking no action.
Vulnerability management is a security practice that is designed to proactively prevent the exploitation of IT vulnerabilities that exist within an organization. The vulnerability management life cycle involves six steps: discover, prioritize assets, assess, report, remediate, and verify. Asset management involves the implementation of systems that track the location and configuration of networked devices and software across an enterprise. Mobile device management (MDM) systems allow security personnel to configure, monitor and update a very diverse set of mobile clients from the cloud. Configuration management addresses the inventory and control of hardware and software configurations of systems. Patch management is related to vulnerability management and involves all aspects of software patching, including acquiring, distributing, installing, and verifying patches. Patch management is required by some compliance regulations. There are different patch management techniques such as agent-based, agentless scanning, and passive network monitoring.
Information Security Management Systems
Organizations can use an Information Security Management System (ISMS) to identify, analyze, and address information security risks. Standards for managing cybersecurity risk are available from ISO and NIST. An ISMS is a systematic, multi-layered approach to cybersecurity that includes people, processes, technologies, and the cultures in which they interact in a process of risk management. The International Organization for Standardization (ISO) partnered with the International Electrotechnical Commission (IEC) to develop the ISO/IEC 27000 series of specifications for ISMSs. NIST has also developed the Cybersecurity Framework, which is similar to the ISO/IEC 27000 standards. The NIST framework is a set of standards designed to integrate existing standards, guidelines, and practices to help better manage and reduce cybersecurity risk.