Time limit: 0
Quiz-summary
0 of 41 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
Information
CCNA Cyber Ops (Version 1.1) – Chapter 6 Test Online Full
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 41 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- Answered
- Review
-
Question 1 of 41
1. Question
1 pointsWhat type of malware has the primary objective of spreading across the network?Correct
Incorrect
-
Question 2 of 41
2. Question
1 pointsWhy would a rootkit be used by a hacker?Correct
Incorrect
-
Question 3 of 41
3. Question
1 pointsWhich type of hacker is motivated to protest against political and social issues?Correct
Incorrect
-
Question 4 of 41
4. Question
1 pointsWhat is a characteristic of a Trojan horse as it relates to network security?Correct
Incorrect
-
Question 5 of 41
5. Question
1 pointsWhat is a botnet?Correct
Incorrect
-
Question 6 of 41
6. Question
1 pointsWhich type of Trojan horse security breach uses the computer of the victim as the source device to launch other attacks?Correct
Incorrect
-
Question 7 of 41
7. Question
1 pointsWhat is the primary goal of a DoS attack?Correct
Incorrect
-
Question 8 of 41
8. Question
1 pointsWhat is a main purpose of launching an access attack on network systems?Correct
Incorrect
-
Question 9 of 41
9. Question
1 pointsWhat causes a buffer overflow?Correct
Incorrect
-
Question 10 of 41
10. Question
1 pointsA company pays a significant sum of money to hackers in order to regain control of an email and data server. Which type of security attack was used by the hackers?Correct
Incorrect
-
Question 11 of 41
11. Question
1 pointsWhat is the term used to describe an email that is targeting a specific person employed at a financial institution?Correct
Incorrect
-
Question 12 of 41
12. Question
1 pointsWhich access attack method involves a software program that attempts to discover a system password by the use of an electronic dictionary?Correct
Incorrect
-
Question 13 of 41
13. Question
1 pointsIn what way are zombies used in security attacks?Correct
Incorrect
-
Question 14 of 41
14. Question
1 pointsWhat are two evasion methods used by hackers? (Choose two.)Correct
Incorrect
-
Question 15 of 41
15. Question
1 pointsWhat are two purposes of launching a reconnaissance attack on a network? (Choose two.)Correct
Incorrect
-
Question 16 of 41
16. Question
1 pointsWhat are three techniques used in social engineering attacks? (Choose three.)Correct
Incorrect
-
Question 17 of 41
17. Question
1 pointsAn attacker is using a laptop as a rogue access point to capture all network traffic from a targeted user. Which type of attack is this?Correct
Incorrect
-
Question 18 of 41
18. Question
1 pointsA user is curious about how someone might know a computer has been infected with malware. What are two common malware behaviors? (Choose two.)Correct
Incorrect
-
Question 19 of 41
19. Question
1 pointsWhich type of security attack would attempt a buffer overflow?Correct
Incorrect
-
Question 20 of 41
20. Question
1 pointsWhat is a significant characteristic of virus malware?Correct
Incorrect
-
Question 21 of 41
21. Question
1 pointsA senior citizen receives a warning on the computer that states that the operating system registry is corrupt and to click a particular link to repair it. Which type of malware is being used to try to create the perception of a computer threat to the user?Correct
Incorrect
-
Question 22 of 41
22. Question
1 pointsWhat is the motivation of a white hat attacker?Correct
Incorrect
-
Question 23 of 41
23. Question
1 pointsWhat is a ping sweep?Correct
Incorrect
-
Question 24 of 41
24. Question
1 pointsWhat is the term used when a malicious party sends a fraudulent email disguised as being from a legitimate, trusted source?Correct
Incorrect
-
Question 25 of 41
25. Question
1 pointsWhat are the three major components of a worm attack? (Choose three.)Correct
Incorrect
-
Question 26 of 41
26. Question
1 pointsWhich security threat installs on a computer without the knowledge of the user and then monitors computer activity?Correct
Incorrect
-
Question 27 of 41
27. Question
1 pointsWhat type of attack uses zombies?Correct
Incorrect
-
Question 28 of 41
28. Question
1 pointsWhat is the best description of Trojan horse malware?Correct
Incorrect
-
Question 29 of 41
29. Question
1 pointsWhat is the purpose of a rootkit?Correct
Incorrect
-
Question 30 of 41
30. Question
1 pointsWhen describing malware, what is a difference between a virus and a worm?Correct
Incorrect
-
Question 31 of 41
31. Question
1 pointsWhat is an example of “hacktivism”?Correct
Incorrect
-
Question 32 of 41
32. Question
1 pointsWhat is the purpose of a reconnaissance attack on a computer network?Correct
Incorrect
-
Question 33 of 41
33. Question
1 pointsWhich tool is used to provide a list of open ports on network devices?Correct
Incorrect
-
Question 34 of 41
34. Question
1 pointsWhich type of attack allows an attacker to use a brute-force approach?Correct
Incorrect
-
Question 35 of 41
35. Question
1 pointsWhich term is used to describe the act of sending an email message in an attempt to divulge sensitive information from someone?Correct
Incorrect
-
Question 36 of 41
36. Question
1 pointsWhat is the significant characteristic of worm malware?Correct
Incorrect
-
Question 37 of 41
37. Question
1 pointsA network administrator detects unknown sessions involving port 21 on the network. What could be causing this security breach?Correct
Incorrect
-
Question 38 of 41
38. Question
1 pointsWhich example illustrates how malware might be concealed?Correct
Incorrect
-
Question 39 of 41
39. Question
1 pointsWhich type of security threat can be described as software that attaches itself to another program to execute a specific unwanted function?Correct
Incorrect
-
Question 40 of 41
40. Question
1 pointsMatch the security concept to the description.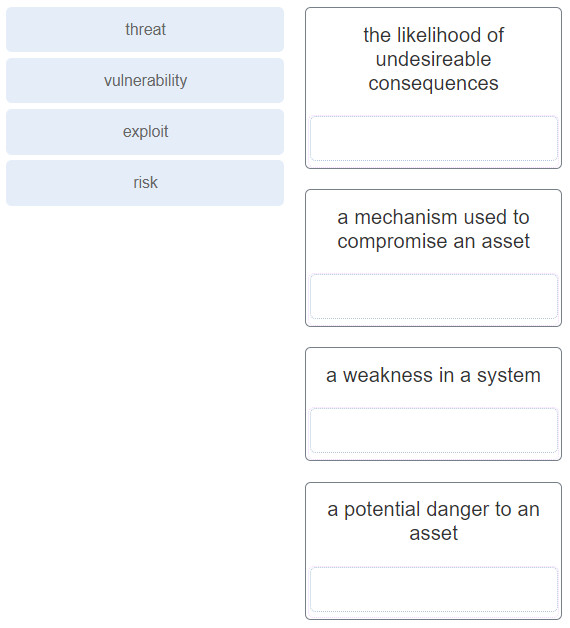 Correct
Correct
Incorrect
-
Question 41 of 41
41. Question
1 pointsMatch the network security testing technique with how it is used to test network security. (Not all options are used.)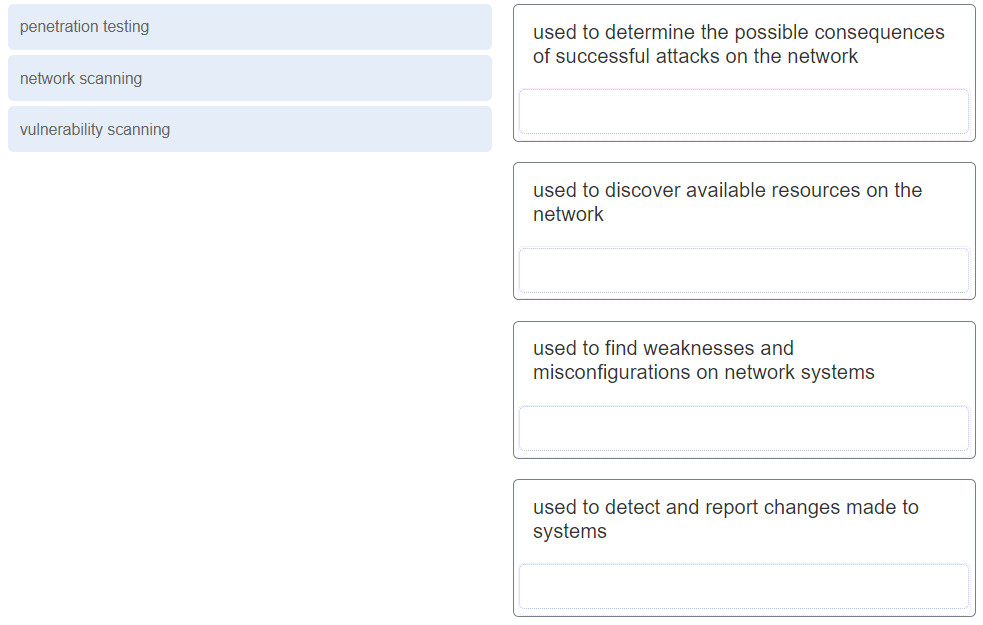 Correct
Correct
Incorrect
