Time limit: 0
Quiz-summary
0 of 41 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
Information
CCNA Cyber Ops (Version 1.1) – Chapter 11 Test Online Full
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 41 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- Answered
- Review
-
Question 1 of 41
1. Question
1 pointsHow does using HTTPS complicate network security monitoring?Correct
Incorrect
-
Question 2 of 41
2. Question
1 pointsWhich protocol is used to send e-mail messages between two servers that are in different e-mail domains?Correct
Incorrect
-
Question 3 of 41
3. Question
1 pointsWhat are two ways that ICMP can be a security threat to a company? (Choose two.)Correct
Incorrect
-
Question 4 of 41
4. Question
1 pointsWhich function is provided by the Sguil application?Correct
Incorrect
-
Question 5 of 41
5. Question
1 pointsWhich two options are network security monitoring approaches that use advanced analytic techniques to analyze network telemetry data? (Choose two.)Correct
Incorrect
-
Question 6 of 41
6. Question
1 pointsA system administrator has recommended to the CIO a move of some applications from a Windows server to a Linux server. The proposed server will use ext4 partitions and serve as a web server, file server, and print server. The CIO is considering the recommendation, but has some questions regarding security. Which two methods does Linux use to log data in order to identify a security event? (Choose two.)Correct
Incorrect
-
Question 7 of 41
7. Question
1 pointsA system administrator has recommended to the CIO a move of some applications from a Windows server to a Linux server. The proposed server will use ext4 partitions and serve as a web server, file server, and print server. The CIO is considering the recommendation, but has some questions regarding security. What is a daemon?Correct
Incorrect
-
Question 8 of 41
8. Question
1 pointsA system administrator has recommended to the CIO a move of some applications from a Windows server to a Linux server. The proposed server will use ext4 partitions and serve as a web server, file server, and print server. The CIO is considering the recommendation, but has some questions regarding security. Because the company uses discretionary access control (DAC) for user file management, what feature would need to be supported on the server?Correct
Incorrect
-
Question 9 of 41
9. Question
1 pointsA system administrator has recommended to the CIO a move of some applications from a Windows server to a Linux server. The proposed server will use ext4 partitions and serve as a web server, file server, and print server. The CIO is considering the recommendation, but has some questions regarding security. What are two benefits of using an ext4 partition instead of ext3? (Choose two.)Correct
Incorrect
-
Question 10 of 41
10. Question
1 pointsHow can IMAP be a security threat to a company?Correct
Incorrect
-
Question 11 of 41
11. Question
1 pointsA system administrator runs a file scan utility on a Windows PC and notices a file lsass.exe in the Program Files directory. What should the administrator do?Correct
Incorrect
-
Question 12 of 41
12. Question
1 pointsHow does a web proxy device provide data loss prevention (DLP) for an enterprise?Correct
Incorrect
-
Question 13 of 41
13. Question
1 pointsA system analyst is reviewing syslog messages and notices that the PRI value of a message is 26. What is the severity value of the message?Correct
Incorrect
-
Question 14 of 41
14. Question
1 pointsWhich statement describes session data in security logs?Correct
Incorrect
-
Question 15 of 41
15. Question
1 pointsIn a Cisco AVC system, in which module is NetFlow deployed?Correct
Incorrect
-
Question 16 of 41
16. Question
1 pointsWhat port number would be used if a threat actor was using NTP to direct DDoS attacks?Correct
Incorrect
-
Question 17 of 41
17. Question
1 pointsWhich information can be provided by the Cisco NetFlow utility?Correct
Incorrect
-
Question 18 of 41
18. Question
1 pointsWhat is Tor?Correct
Incorrect
-
Question 19 of 41
19. Question
1 pointsWhich statement describes statistical data in network security monitoring processes?Correct
Incorrect
-
Question 20 of 41
20. Question
1 pointsRefer to the exhibit. A network administrator is reviewing an Apache access log message. What is the status of the access request by the client?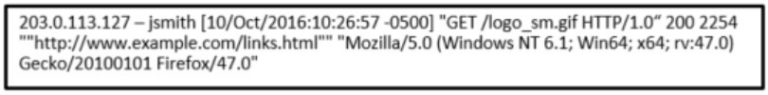 Correct
Correct
Incorrect
-
Question 21 of 41
21. Question
1 pointsHow might corporate IT professionals deal with DNS-based cyber threats?Correct
Incorrect
-
Question 22 of 41
22. Question
1 pointsRefer to the exhibit. A junior network engineer is handed a print-out of the network information shown. Which protocol or service originated the information shown in the graphic?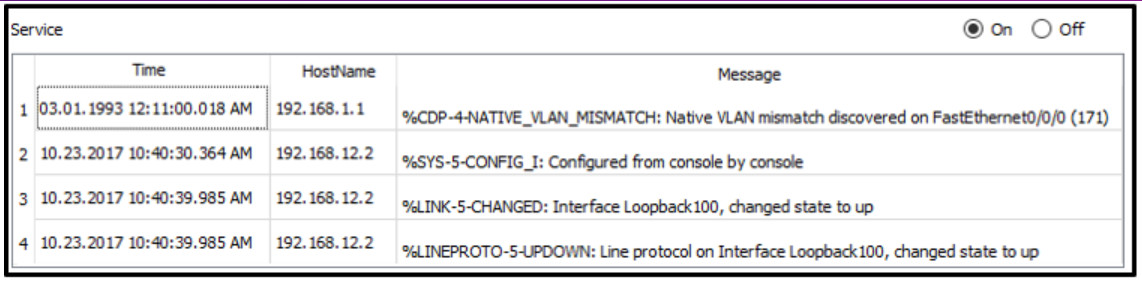 Correct
Correct
Incorrect
-
Question 23 of 41
23. Question
1 pointsWhich technology is used in Cisco Next-Generation IPS devices to consolidate multiple security layers into a single platform?Correct
Incorrect
-
Question 24 of 41
24. Question
1 pointsRefer to the exhibit. How is the traffic from the client web browser being altered when connected to the destination website of www.cisco.com?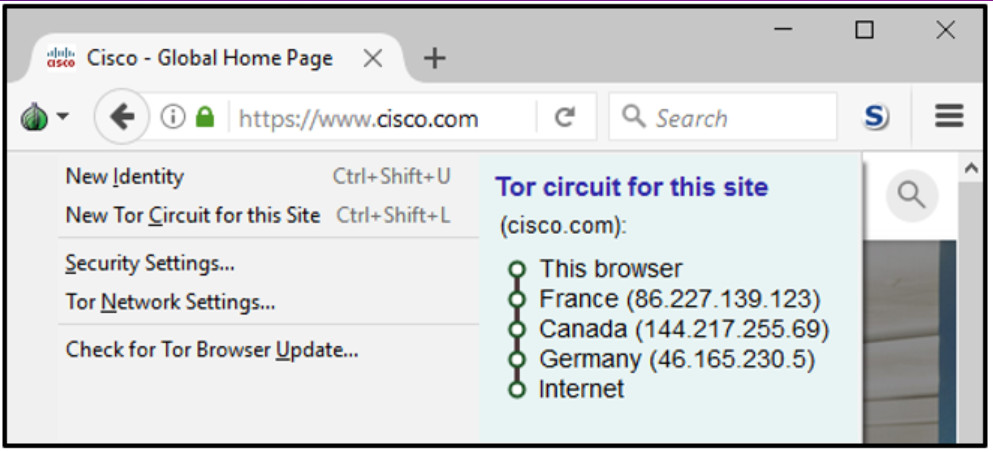 Correct
Correct
Incorrect
-
Question 25 of 41
25. Question
1 pointsWhich Windows log contains information about installations of software, including Windows updates?Correct
Incorrect
-
Question 26 of 41
26. Question
1 pointsWhich Windows log records events related to login attempts and operations related to file or object access?Correct
Incorrect
-
Question 27 of 41
27. Question
1 pointsWhat does it indicate if the timestamp in the HEADER section of a syslog message is preceded by a period or asterisk symbol?Correct
Incorrect
-
Question 28 of 41
28. Question
1 pointsWhich two application layer protocols manage the exchange of messages between a client with a web browser and a remote web server? (Choose two.)Correct
Incorrect
-
Question 29 of 41
29. Question
1 pointsWhich protocol is a name resolution protocol often used by malware to communicate with command-and-control (CnC) servers?Correct
Incorrect
-
Question 30 of 41
30. Question
1 pointsWhich statement describes the tcpdump tool?Correct
Incorrect
-
Question 31 of 41
31. Question
1 pointsWhich Windows host log event type describes the successful operation of an application, driver, or service?Correct
Incorrect
-
Question 32 of 41
32. Question
1 pointsA NIDS/NIPS has identified a threat. Which type of security data will be generated and sent to a logging device?Correct
Incorrect
-
Question 33 of 41
33. Question
1 pointsWhat is the purpose of Tor?Correct
Incorrect
-
Question 34 of 41
34. Question
1 pointsWhich statement describes an operational characteristic of NetFlow?Correct
Incorrect
-
Question 35 of 41
35. Question
1 pointsWhich type of security data can be used to describe or predict network behavior?Correct
Incorrect
-
Question 36 of 41
36. Question
1 pointsWhat type of server can threat actors use DNS to communicate with?Correct
Incorrect
-
Question 37 of 41
37. Question
1 pointsIn a Cisco AVC system, in which module is NBAR2 deployed?Correct
Incorrect
-
Question 38 of 41
38. Question
1 pointsA security analyst reviews network logs. The data shows user network activities such as username, IP addresses, web pages accessed, and timestamp. Which type of data is the analyst reviewing?Correct
Incorrect
-
Question 39 of 41
39. Question
1 pointsWhich type of server daemon accepts messages sent by network devices to create a collection of log entries?Correct
Incorrect
-
Question 40 of 41
40. Question
1 pointsWhich Windows tool can be used to review host logs?Correct
Incorrect
-
Question 41 of 41
41. Question
1 pointsWhich two protocols may devices use in the application process that sends email? (Choose two.)Correct
Incorrect
