Time limit: 0
Quiz-summary
0 of 36 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
Information
CCNA Cyber Ops (Version 1.1) – Chapter 7 Test Online Full
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 36 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- Answered
- Review
-
Question 1 of 36
1. Question
1 pointsWhat are two monitoring tools that capture network traffic and forward it to network monitoring devices? (Choose two.)Correct
Incorrect
-
Question 2 of 36
2. Question
1 pointsWhich technology is an open source SIEM system?Correct
Incorrect
-
Question 3 of 36
3. Question
1 pointsWhat network attack seeks to create a DoS for clients by preventing them from being able to obtain a DHCP lease?Correct
Incorrect
-
Question 4 of 36
4. Question
1 pointsWhich protocol would be the target of a cushioning attack?Correct
Incorrect
-
Question 5 of 36
5. Question
1 pointsWhich network monitoring capability is provided by using SPAN?Correct
Incorrect
-
Question 6 of 36
6. Question
1 pointsWhich type of DNS attack involves the cybercriminal compromising a parent domain and creating multiple subdomains to be used during the attacks?Correct
Incorrect
-
Question 7 of 36
7. Question
1 pointsRefer to the exhibit. What protocol would be used by the syslog server service to create this type of output for security purposes?Correct
Incorrect
-
Question 8 of 36
8. Question
1 pointsWhat is the result of a passive ARP poisoning attack?Correct
Incorrect
-
Question 9 of 36
9. Question
1 pointsWhich term is used for bulk advertising emails flooded to as many end users as possible?Correct
Incorrect
-
Question 10 of 36
10. Question
1 pointsWhich capability is provided by the aggregation function in SIEM?Correct
Incorrect
-
Question 11 of 36
11. Question
1 pointsWhich protocol is attacked when a cybercriminal provides an invalid gateway in order to create a man-in-the-middle attack?Correct
Incorrect
-
Question 12 of 36
12. Question
1 pointsWhich network monitoring tool can provide a complete audit trail of basic information of all IP flows on a Cisco router and forward the data to a device?Correct
Incorrect
-
Question 13 of 36
13. Question
1 pointsWhat are two methods used by cybercriminals to mask DNS attacks? (Choose two.)Correct
Incorrect
-
Question 14 of 36
14. Question
1 pointsWhich protocol is exploited by cybercriminals who create malicious iFrames?Correct
Incorrect
-
Question 15 of 36
15. Question
1 pointsWhich SIEM function is associated with speeding up detection of security threats by examining logs and events from different systems?Correct
Incorrect
-
Question 16 of 36
16. Question
1 pointsIn which TCP attack is the cybercriminal attempting to overwhelm a target host with half-open TCP connections?Correct
Incorrect
-
Question 17 of 36
17. Question
1 pointsIn which type of attack is falsified information used to redirect users to malicious Internet sites?Correct
Incorrect
-
Question 18 of 36
18. Question
1 pointsRefer to the exhibit. A junior network administrator is inspecting the traffic flow of a particular server in order to make security recommendations to the departmental supervisor. Which recommendation should be made?Correct
Incorrect
-
Question 19 of 36
19. Question
1 pointsWhich network monitoring tool saves captured packets in a PCAP file?Correct
Incorrect
-
Question 20 of 36
20. Question
1 pointsWhich cyber attack involves a coordinated attack from a botnet of zombie computers?Correct
Incorrect
-
Question 21 of 36
21. Question
1 pointsHow is optional network layer information carried by IPv6 packets?Correct
Incorrect
-
Question 22 of 36
22. Question
1 pointsWhat type of attack targets an SQL database using the input field of a user?Correct
Incorrect
-
Question 23 of 36
23. Question
1 pointsWhat network monitoring technology enables a switch to copy and forward traffic sent and received on multiple interfaces out another interface toward a network analysis device?Correct
Incorrect
-
Question 24 of 36
24. Question
1 pointsWhich technology is a proprietary SIEM system?Correct
Incorrect
-
Question 25 of 36
25. Question
1 pointsWhich term is used to describe legitimate traffic that is mistaken for unauthorized traffic by firewalls and IPSs?Correct
Incorrect
-
Question 26 of 36
26. Question
1 pointsWhich monitoring technology mirrors traffic flowing through a switch to an analysis device connected to another switch port?Correct
Incorrect
-
Question 27 of 36
27. Question
1 pointsWhich network monitoring tool saves captured network frames in PCAP files?Correct
Incorrect
-
Question 28 of 36
28. Question
1 pointsWhich language is used to query a relational database?Correct
Incorrect
-
Question 29 of 36
29. Question
1 pointsWhich network monitoring tool is in the category of network protocol analyzers?Correct
Incorrect
-
Question 30 of 36
30. Question
1 pointsWhich SIEM function is associated with examining the logs and events of multiple systems to reduce the amount of time of detecting and reacting to security events?Correct
Incorrect
-
Question 31 of 36
31. Question
1 pointsWhich network technology uses a passive splitting device that forwards all traffic, including Layer 1 errors, to an analysis device?Correct
Incorrect
-
Question 32 of 36
32. Question
1 pointsWhat technique is a security attack that depletes the pool of IP addresses available for legitimate hosts?Correct
Incorrect
-
Question 33 of 36
33. Question
1 pointsIn what type of attack is a cybercriminal attempting to prevent legitimate users from accessing network services?Correct
Incorrect
-
Question 34 of 36
34. Question
1 pointsWhich network monitoring technology collects IP operational data on packets flowing through Cisco routers and multilayer switches?Correct
Incorrect
-
Question 35 of 36
35. Question
1 pointsMatch the monitoring tool to the description.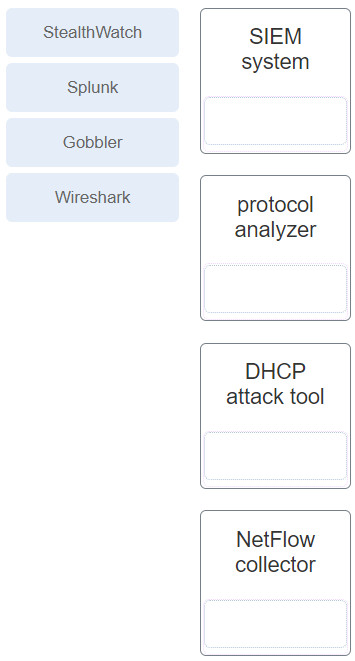 Correct
Correct
Incorrect
-
Question 36 of 36
36. Question
1 pointsMatch the attack to the definition. (Not all options are used.)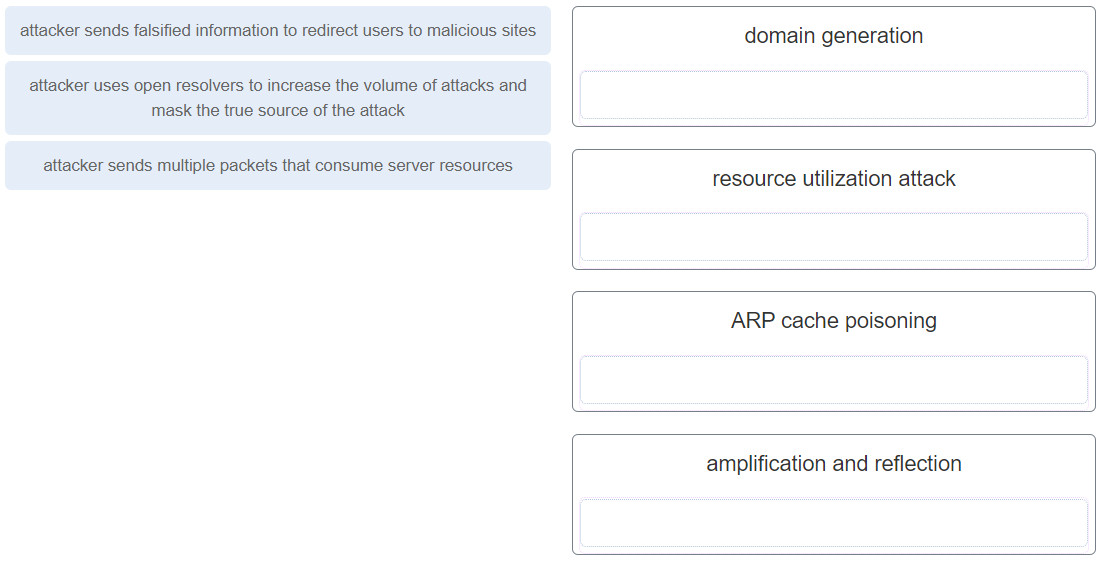 Correct
Correct
Incorrect
