Check answers here:
CyberOps Associate (Version 1.0) – FINAL Exam Answers
Quiz-summary
0 of 190 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
- 151
- 152
- 153
- 154
- 155
- 156
- 157
- 158
- 159
- 160
- 161
- 162
- 163
- 164
- 165
- 166
- 167
- 168
- 169
- 170
- 171
- 172
- 173
- 174
- 175
- 176
- 177
- 178
- 179
- 180
- 181
- 182
- 183
- 184
- 185
- 186
- 187
- 188
- 189
- 190
Information
CyberOps Associate (Version 1.0) – FINAL TEST ONLINE
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 190 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
- 151
- 152
- 153
- 154
- 155
- 156
- 157
- 158
- 159
- 160
- 161
- 162
- 163
- 164
- 165
- 166
- 167
- 168
- 169
- 170
- 171
- 172
- 173
- 174
- 175
- 176
- 177
- 178
- 179
- 180
- 181
- 182
- 183
- 184
- 185
- 186
- 187
- 188
- 189
- 190
- Answered
- Review
-
Question 1 of 190
1. Question
1 pointsWhich two statements are characteristics of a virus? (Choose two.)Correct
Incorrect
Hint
The type of end user interaction required to launch a virus is typically opening an application, opening a web page, or powering on the computer. Once activated, a virus may infect other files located on the computer or other computers on the same network. -
Question 2 of 190
2. Question
1 pointsWhat is a characteristic of a Trojan horse as it relates to network security?Correct
Incorrect
Hint
A Trojan horse carries out malicious operations under the guise of a legitimate program. Denial of service attacks send extreme quantities of data to a particular host or network device interface. Password attacks use electronic dictionaries in an attempt to learn passwords. Buffer overflow attacks exploit memory buffers by sending too much information to a host to render the system inoperable. -
Question 3 of 190
3. Question
1 pointsWhat technique is used in social engineering attacks?Correct
Incorrect
Hint
A threat actor sends fraudulent email which is disguised as being from a legitimate, trusted source to trick the recipient into installing malware on their device, or to share personal or financial information. -
Question 4 of 190
4. Question
1 pointsWhat is a purpose of implementing VLANs on a network?Correct
Incorrect
Hint
VLANs are used on a network to separate user traffic based on factors such as function, project team, or application, without regard for the physical location of the user or device. -
Question 5 of 190
5. Question
1 pointsRefer to the exhibit. A cybersecurity analyst is viewing packets forwarded by switch S2. What addresses will identify frames containing data sent from PCA to PCB?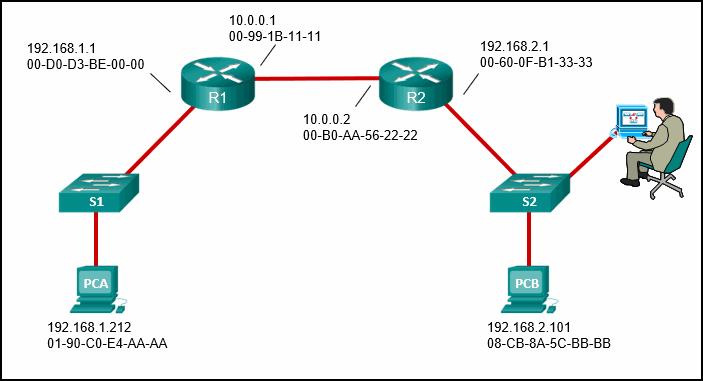 Correct
Correct
Incorrect
Hint
When a message sent from PCA to PCB reaches router R2, some frame header fields will be rewritten by R2 before forwarding to switch S2. The frames will contain the source MAC address of router R2 and the destination MAC address of PCB. The frames will retain the original IPv4 addressing applied by PCA which is the IPv4 address of PCA as the source address and the IPv4 address of PCB as the destination. -
Question 6 of 190
6. Question
1 pointsA cybersecurity analyst needs to collect alert data. What are three detection tools to perform this task in the Security Onion architecture? (Choose three.)Correct
Incorrect
Hint
A Security Onion Architecture: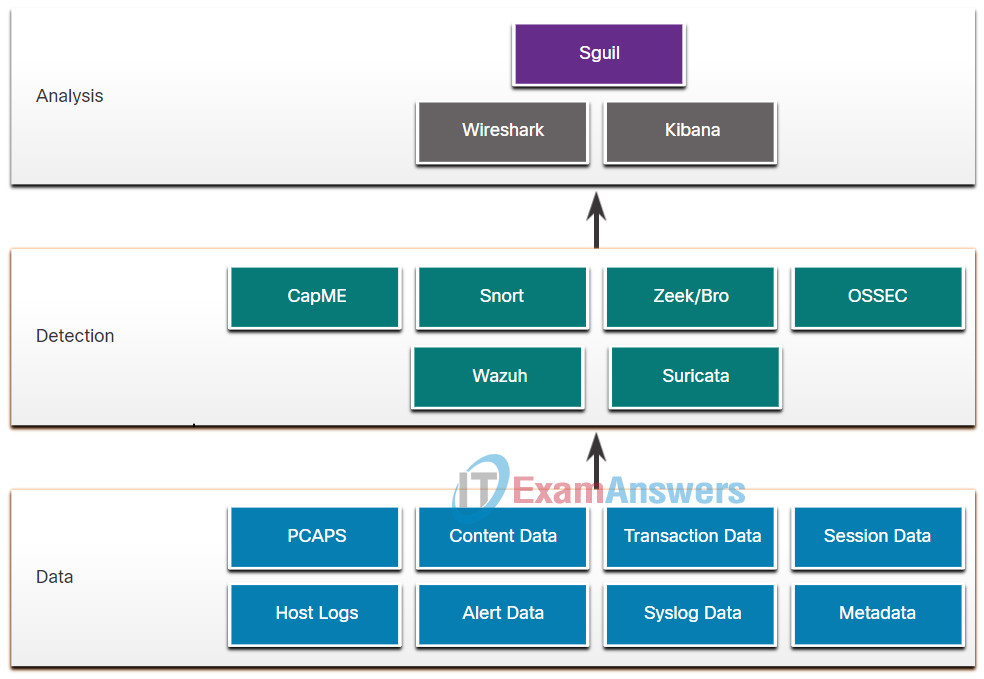 Detection tools in Security Onion Architecture include: CapME, Snort, Zeek, OSSEC, Wazuh, Suricata.
Detection tools in Security Onion Architecture include: CapME, Snort, Zeek, OSSEC, Wazuh, Suricata. -
Question 7 of 190
7. Question
1 pointsMatch the Security Onion tool with the description.Correct
Incorrect
-
Question 8 of 190
8. Question
1 pointsIn network security assessments, which type of test is used to evaluate the risk posed by vulnerabilities to a specific organization including assessment of the likelihood of attacks and the impact of successful exploits on the organization?Correct
Incorrect
Hint
A risk analysis includes assessment of the likelihood of attacks, identifies types of likely threat actors, and evaluates the impact of successful exploits on the organization. -
Question 9 of 190
9. Question
1 pointsMatch the server profile element to the description. (Not all options are used.)Correct
Incorrect
Hint
The elements of a server profile include the following:Listening ports – the TCP and UDP daemons and ports that are allowed to be open on the server User accounts – the parameters defining user access and behavior Service accounts – the definitions of the type of service that an application is allowed to run on a given host Software environment – the tasks, processes, and applications that are permitted to run on the server -
Question 10 of 190
10. Question
1 pointsIn addressing an identified risk, which strategy aims to shift some of the risk to other parties?Correct
Incorrect
Hint
There are four potential strategies for responding to risks that have been identified: Risk avoidance – Stop performing the activities that create risk. Risk reduction – Decrease the risk by taking measures to reduce vulnerability. Risk sharing – Shift some of the risk to other parties. Risk retention – Accept the risk and its consequences. -
Question 11 of 190
11. Question
1 pointsWhat is a network tap?Correct
Incorrect
Hint
A network tap is used to capture traffic for monitoring the network. The tap is typically a passive splitting device implemented inline on the network and forwards all traffic, including physical layer errors, to an analysis device. -
Question 12 of 190
12. Question
1 pointsMatch the monitoring tool to the definition.Correct
Incorrect
-
Question 13 of 190
13. Question
1 pointsIf a SOC has a goal of 99.999% uptime, how many minutes of downtime a year would be considered within its goal?Correct
Incorrect
Hint
Within a year, there are 365 days x 24 hours a day x 60 minutes per hour = 525,600 minutes. With the goal of uptime 99.999% of time, the downtime needs to be controlled under 525,600 x (1-0.99999) = 5.256 minutes a year. -
Question 14 of 190
14. Question
1 pointsThe HTTP server has responded to a client request with a 200 status code. What does this status code indicate?Correct
Incorrect
-
Question 15 of 190
15. Question
1 pointsWhat is an advantage for small organizations of adopting IMAP instead of POP?Correct
Incorrect
Hint
IMAP and POP are protocols that are used to retrieve email messages. The advantage of using IMAP instead of POP is that when the user connects to an IMAP-capable server, copies of the messages are downloaded to the client application. IMAP then stores the email messages on the server until the user manually deletes those messages. -
Question 16 of 190
16. Question
1 pointsWhat debugging security tool can be used by black hats to reverse engineer binary files when writing exploits?Correct
Incorrect
-
Question 17 of 190
17. Question
1 pointsMatch the attack tools with the description. (Not all options are used.)Correct
Incorrect
-
Question 18 of 190
18. Question
1 pointsWhat are two features of ARP? (Choose two.)Correct
Incorrect
Hint
When a node encapsulates a data packet into a frame, it needs the destination MAC address. First it determines if the destination device is on the local network or on a remote network. Then it checks the ARP table (not the MAC table) to see if a pair of IP address and MAC address exists for either the destination IP address (if the destination host is on the local network) or the default gateway IP address (if the destination host is on a remote network). If the match does not exist, it generates an ARP broadcast to seek the IP address to MAC address resolution. Because the destination MAC address is unknown, the ARP request is broadcast with the MAC address FFFF.FFFF.FFFF. Either the destination device or the default gateway will respond with its MAC address, which enables the sending node to assemble the frame. If no device responds to the ARP request, then the originating node will discard the packet because a frame cannot be created. -
Question 19 of 190
19. Question
1 pointsWhat is a property of the ARP table on a device?Correct
Incorrect
-
Question 20 of 190
20. Question
1 pointsWhat is the purpose of Tor?Correct
Incorrect
Hint
Tor is a software platform and network of peer-to-peer (P2P) hosts that function as routers. Users access the Tor network by using a special browserthat allows them to browse anonymously. -
Question 21 of 190
21. Question
1 pointsWhich two network protocols can be used by a threat actor to exfiltrate data in traffic that is disguised as normal network traffic? (Choose two.)Correct
Incorrect
-
Question 22 of 190
22. Question
1 pointsWhat is a key difference between the data captured by NetFlow and data captured by Wireshark?Correct
Incorrect
Hint
Wireshark captures the entire contents of a packet. NetFlow does not. Instead, NetFlow collects metadata, or data about the flow. -
Question 23 of 190
23. Question
1 pointsWhich tool captures full data packets with a command-line interface only?Correct
Incorrect
Hint
The command-line tool tcpdump is a packet analyzer. Wireshark is a packet analyzer with a GUI interface. -
Question 24 of 190
24. Question
1 pointsWhich method can be used to harden a device?Correct
Incorrect
Hint
The basic best practices for device hardening are as follows: Ensure physical security. Minimize installed packages. Disable unused services. Use SSH and disable the root account login over SSH. Keep the system updated. Disable USB auto-detection. Enforce strong passwords. Force periodic password changes. Keep users from re-using old passwords. Review logs regularly. -
Question 25 of 190
25. Question
1 pointsIn a Linux operating system, which component interprets user commands and attempts to execute them?Correct
Incorrect
-
Question 26 of 190
26. Question
1 pointsA network administrator is configuring an AAA server to manage RADIUS authentication. Which two features are included in RADIUS authentication? (Choose two.)Correct
Incorrect
Hint
RADIUS authentication supports the following features: RADIUS authentication and authorization as one process Encrypts only the password Utilizes UDP Supports remote-access technologies, 802.1X, and Session Initiation Protocol (SIP) -
Question 27 of 190
27. Question
1 pointsWhat is privilege escalation?Correct
Incorrect
Hint
With privilege escalation, vulnerabilities are exploited to grant higher levels of privilege. After the privilege is granted, the threat actor can access sensitive information or take control of the system. -
Question 28 of 190
28. Question
1 pointsWhat two assurances does digital signing provide about code that is downloaded from the Internet? (Choose two.)Correct
Incorrect
Hint
Digitally signing code provides several assurances about the code: The code is authentic and is actually sourced by the publisher. The code has not been modified since it left the software publisher. The publisher undeniably published the code. This provides nonrepudiation of the act of publishing. -
Question 29 of 190
29. Question
1 pointsAn IT enterprise is recommending the use of PKI applications to securely exchange information between the employees. In which two cases might an organization use PKI applications to securely exchange information between users? (Choose two.)Correct
Incorrect
Hint
The Public Key Infrastructure (PKI) is a third party-system referred to as a certificate authority or CA. The PKI is the framework used to securely exchange information between parties. Common PKI applications are as follows: SSL/TLS certificate-based peer authentication Secure network traffic using IPsec VPNs HTTPS Web traffic Control access to the network using 802.1x authentication Secure email using the S/MIME protocol Secure instant messaging Approve and authorize applications with Code Signing Protect user data with the Encryption File System (EFS) Implement two-factor authentication with smart cards Securing USB storage devices -
Question 30 of 190
30. Question
1 pointsWhich measure can a security analyst take to perform effective security monitoring against network traffic encrypted by SSL technology?Correct
Incorrect
Hint
Deploy a Cisco SSL Appliance to decrypt SSL traffic and send it to intrusion prevention system (IPS) appliances to identify risks normally hidden by SSL. -
Question 31 of 190
31. Question
1 pointsAn administrator is trying to develop a BYOD security policy for employees that are bringing a wide range of devices to connect to the company network. Which three objectives must the BYOD security policy address? (Choose three.)Correct
Incorrect
-
Question 32 of 190
32. Question
1 pointsMatch the security policy with the description. (Not all options are used.)Correct
Incorrect
-
Question 33 of 190
33. Question
1 pointsMatch the attack to the definition. (Not all options are used.)Correct
Incorrect
-
Question 34 of 190
34. Question
1 pointsWhat type of attack targets an SQL database using the input field of a user?Correct
Incorrect
Hint
A criminal can insert a malicious SQL statement in an entry field on a website where the system does not filter the user input correctly. -
Question 35 of 190
35. Question
1 pointsWhat are two characteristics of Ethernet MAC addresses? (Choose two.)Correct
Incorrect
-
Question 36 of 190
36. Question
1 pointsA user calls to report that a PC cannot access the internet. The network technician asks the user to issue the command ping 127.0.0.1 in a command prompt window. The user reports that the result is four positive replies. What conclusion can be drawn based on this connectivity test?Correct
Incorrect
Hint
The ping 127.0.0.1 command is used to verify that the TCP/IP stack is functional. It verifies the proper operation of the protocol stack from the network layer to physical layer, without sending a signal on the media. That is, this test does not go beyond the PC itself. For example, it does not detect whether a cable is connected to the PC or not. -
Question 37 of 190
37. Question
1 pointsWhat characterizes a threat actor?Correct
Incorrect
-
Question 38 of 190
38. Question
1 pointsA computer is presenting a user with a screen requesting payment before the user data is allowed to be accessed by the same user. What type of malware is this?Correct
Incorrect
Hint
Ransomware commonly encrypts data on a computer and makes the data unavailable until the computer user pays a specific sum of money -
Question 39 of 190
39. Question
1 pointsWhich ICMPv6 message type provides network addressing information to hosts that use SLAAC?Correct
Incorrect
-
Question 40 of 190
40. Question
1 pointsWhich tol included in the Security Onion is a series of software plugins that send different types of data to the Elasticsearch data stores?Correct
Incorrect
-
Question 41 of 190
41. Question
1 pointsWhich two types of unreadable network traffic could be eliminated from data collected by NSM? (Choose two.)Correct
Incorrect
Hint
To reduce the huge amount of data collected so that cybersecurity analysts can focus on critical threats, some less important or unusable data could be eliminated from the datasets. For example, encrypted data, such as IPsec and SSL traffic, could be eliminated because it is unreadable in a reasonable time frame. -
Question 42 of 190
42. Question
1 pointsWhich core open source component of the Elastic-stack is responsible for accepting the data in its native format and making elements of the data consistent across all sources?Correct
Incorrect
-
Question 43 of 190
43. Question
1 pointsMatch the security incident stakeholder with the role.Correct
Incorrect
-
Question 44 of 190
44. Question
1 pointsIn the NIST incident response process life cycle, which type of attack vector involves the use of brute force against devices, networks, or services?Correct
Incorrect
Hint
Common attack vectors include media, attrition, impersonation, and loss or theft. Attrition attacks are any attacks that use brute force. Media attacks are those initiated from storage devices. Impersonation attacks occur when something or someone is replaced for the purpose of the attack, and loss or theft attacks are initiated by equipment inside the organization. -
Question 45 of 190
45. Question
1 pointsMatch the security organization with its security functions. (Not all options are used.)Correct
Incorrect
-
Question 46 of 190
46. Question
1 pointsWhat is a characteristic of CybOX?Correct
Incorrect
-
Question 47 of 190
47. Question
1 pointsAfter host A receives a web page from server B, host A terminates the connection with server B. Match each step to its correct option in the normal termination process for a TCP connection. (Not all options are used.)Correct
Incorrect
-
Question 48 of 190
48. Question
1 pointsWhat are two ways that ICMP can be a security threat to a company? (Choose two.)Correct
Incorrect
Hint
ICMP can be used as a conduit for DoS attacks. It can be used to collect information about a network such as the identification of hosts and network structure, and by determining the operating systems being used on the network. -
Question 49 of 190
49. Question
1 pointsWhich three IPv4 header fields have no equivalent in an IPv6 header? (Choose three.)Correct
Incorrect
Hint
Unlike IPv4, IPv6 routers do not perform fragmentation. Therefore, all three fields supporting fragmentation in the IPv4 header are removed and have no equivalent in the IPv6 header. These three fields are fragment offset, flag, and identification. IPv6 does support host packet fragmentation through the use of extension headers, which are not part of the IPv6 header. -
Question 50 of 190
50. Question
1 pointsWhich twonetcommands are associated with network resource sharing? (Choose two.)Correct
Incorrect
Hint
Thenetcommand is a very important command. Some commonnetcommands include these:net accounts– sets password and logon requirements for usersnet session– lists or disconnects sessions between a computer and other computers on the networknet share– creates, removes, or manages shared resourcesnet start– starts a network service or lists running network servicesnet stop– stops a network servicenet use– connects, disconnects, and displays information about shared network resourcesnet view– shows a list of computers and network devices on the network
-
Question 51 of 190
51. Question
1 pointsMatch the Windows 10 Registry key with its description. (Not all options are used)Correct
Incorrect
-
Question 52 of 190
52. Question
1 pointsWhich PDU format is used when bits are received from the network medium by the NIC of a host?Correct
Incorrect
Hint
When received at the physical layer of a host, the bits are formatted into a frame at the data link layer. A packet is the PDU at the network layer. A segment is the PDU at the transport layer. A file is a data structure that may be used at the application layer. -
Question 53 of 190
53. Question
1 pointsA user is executing a tracert to a remote device. At what point would a router, which is in the path to the destination device, stop forwarding the packet?Correct
Incorrect
Hint
When a router receives a traceroute packet, the value in the TTL field is decremented by 1. When the value in the field reaches zero, the receiving router will not forward the packet, and will send an ICMP Time Exceeded message back to the source. -
Question 54 of 190
54. Question
1 pointsRefer to the exhibit. What solution can provide a VPN between site A and site B to support encapsulation of any Layer 3 protocol between the internal networks at each site?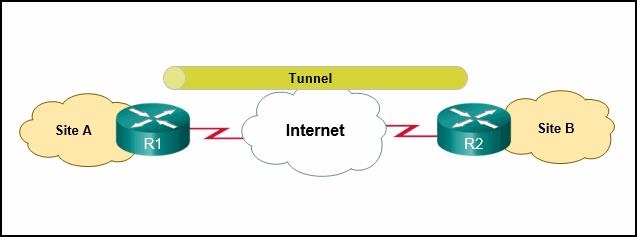 Correct
Correct
Incorrect
Hint
A Generic Routing Encapsulation (GRE) tunnel is a non-secure, site-to-site VPN tunneling solution that is capable of encapsulating any Layer 3 protocol between multiple sites across over an IP internetwork. -
Question 55 of 190
55. Question
1 pointsFor what purpose would a network administrator use the Nmap tool?Correct
Incorrect
-
Question 56 of 190
56. Question
1 pointsMatch the network service with the description.Correct
Incorrect
-
Question 57 of 190
57. Question
1 pointsA client application needs to terminate a TCP communication session with a server. Place the termination process steps in the order that they will occur. (Nat all options are used.)Correct
Incorrect
-
Question 58 of 190
58. Question
1 pointsMatch the attack surface with attack exploits.Correct
Incorrect
-
Question 59 of 190
59. Question
1 pointsMatch the Linux host-based firewall application with its description.Correct
Incorrect
-
Question 60 of 190
60. Question
1 pointsWhat network attack seeks to create a DoS for clients by preventing them from being able to obtain a DHCP lease?Correct
Incorrect
Hint
DCHP starvation attacks are launched by an attacker with the intent to create a DoS for DHCP clients. To accomplish this goal, the attacker uses a tool that sends many DHCPDISCOVER messages in order to lease the entire pool of available IP addresses, thus denying them to legitimate hosts. -
Question 61 of 190
61. Question
1 pointsRefer to the exhibit. If Host1 were to transfer a file to the server, what layers of the TCP/IP model would be used?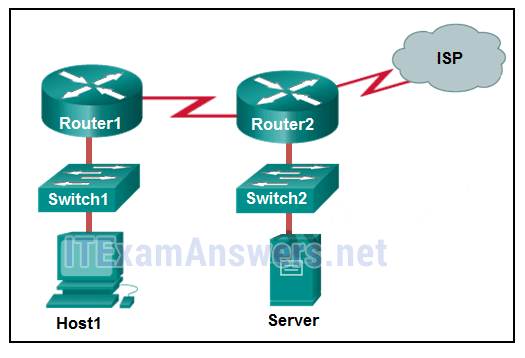 Correct
Correct
Incorrect
Hint
The TCP/IP model contains the application, transport, internet, and network access layers. A file transfer uses the FTP application layer protocol. The data would move from the application layer through all of the layers of the model and across the network to the file server. -
Question 62 of 190
62. Question
1 pointsA company has a file server that shares a folder named Public. The network security policy specifies that the Public folder is assigned Read-Only rights to anyone who can log into the server while the Edit rights are assigned only to the network admin group. Which component is addressed in the AAA network service framework?Correct
Incorrect
Hint
After a user is successfully authenticated (logged into the server), the authorization is the process of determining what network resources the user can access and what operations (such as read or edit) the user can perform. -
Question 63 of 190
63. Question
1 pointsMatch the destination network routing table entry type with a defintion.Correct
Incorrect
-
Question 64 of 190
64. Question
1 pointsA person coming to a cafe for the first time wants to gain wireless access to the Internet using a laptop. What is the first step the wireless client will do in order to communicate over the network using a wireless management frame?Correct
Incorrect
Hint
In order for wireless devices to communicate on a wireless network, management frames are used to complete a three-stage process: Discover the AP Authenticate with the AP Associate with the AP -
Question 65 of 190
65. Question
1 pointsA device has been assigned the IPv6 address of 2001:0db8:cafe:4500:1000:00d8:0058:00ab/64. Which is the network identifier of the device?Correct
Incorrect
Hint
The address has a prefix length of /64. Thus the first 64 bits represent the network portion, whereas the last 64 bits represent the host portion of the IPv6 address. -
Question 66 of 190
66. Question
1 pointsAn administrator wants to create four subnetworks from the network address 192.168.1.0/24. What is the network address and subnet mask of the second useable subnet?Correct
Incorrect
Hint
The number of bits that are borrowed would be two, thus giving a total of 4 useable subnets: 192.168.1.0 192.168.1.64 192.168.1.128 192.168.1.192 Because 2 bits are borrowed, the new subnet mask would be /26 or 255.255.255.192 -
Question 67 of 190
67. Question
1 pointsWhat term describes a set of software tools designed to increase the privileges of a user or to grant access to the user to portions of the operating system that should not normally be allowed?Correct
Incorrect
Hint
A rootkit is used by an attacker to secure a backdoor to a compromised computer, grant access to portions of the operating system normally not permitted, or increase the privileges of a user. -
Question 68 of 190
68. Question
1 pointsThe IT security personnel of an organization notice that the web server deployed in the DMZ is frequently targeted by threat actors. The decision is made to implement a patch management system to manage the server. Which risk management strategy method is being used to respond to the identified risk?Correct
Incorrect
Hint
There are four potential strategies for responding to risks that have been identified:- Risk avoidance – Stop performing the activities that create risk.
- Risk reduction – Decrease the risk by taking measures to reduce vulnerability.
- Risk sharing – Shift some of the risk to other parties.
- Risk retention – Accept the risk and its consequences.
-
Question 69 of 190
69. Question
1 pointsWhat are three characteristics of an information security management system? (Choose three.)Correct
Incorrect
Hint
An Information Security Management System (ISMS) consists of a management framework through which an organization identifies, analyzes, and addresses information security risks. ISMSs are not based in servers or security devices. Instead, an ISMS consists of a set of practices that are systematically applied by an organization to ensure continuous improvement in information security. ISMSs provide conceptual models that guide organizations in planning, implementing, governing, and evaluating information security programs. ISMSs are a natural extension of the use of popular business models, such as Total Quality Management (TQM) and Control Objectives for Information and Related Technologies (COBIT), into the realm of cybersecurity. An ISMS is a systematic, multi-layered approach to cybersecurity. The approach includes people, processes, technologies, and the cultures in which they interact in a process of risk management. -
Question 70 of 190
70. Question
1 pointsWhich three technologies should be included in a SOC security information and event management system? (Choose three.)Correct
Incorrect
Hint
Technologies in a SOC should include the following: • Event collection, correlation, and analysis • Security monitoring • Security control • Log management • Vulnerability assessment • Vulnerability tracking • Threat intelligence Proxy server, VPN, and IPS are security devices deployed in the network infrastructure. -
Question 71 of 190
71. Question
1 pointsWhat part of the URL, http://www.cisco.com/index.html, represents the top-level DNS domain?Correct
Incorrect
Hint
The components of the URL http://www.cisco.com/index.htm are as follows: http = protocol www = part of the server name cisco = part of the domain name index = file name com = the top-level domain -
Question 72 of 190
72. Question
1 pointsWhat best describes the security threat of spoofing?Correct
Incorrect
-
Question 73 of 190
73. Question
1 pointsA newly created company has fifteen Windows 10 computers that need to be installed before the company can open for business. What is a best practice that the technician should implement when configuring the Windows Firewall?Correct
Incorrect
Hint
Only disable Windows Firewall if other firewall software is installed. Use the Windows Firewall (Windows 7 or 8) or the Windows Defender Firewall (Windows 10) Control Panel to enable or disable the Windows Firewall. -
Question 74 of 190
74. Question
1 pointsWhich statement defines the difference between session data and transaction data in logs?Correct
Incorrect
-
Question 75 of 190
75. Question
1 pointsMatch the network monitoring data type with the description.Correct
Incorrect
-
Question 76 of 190
76. Question
1 pointsWhich device supports the use of SPAN to enable monitoring of malicious activity?Correct
Incorrect
Hint
SPAN is a Cisco technology that allows all of the traffic from one port to be redirected to another port. -
Question 77 of 190
77. Question
1 pointsWhich term is used for describing automated queries that are useful for adding efficiency to the cyberoperations workflow?Correct
Incorrect
Hint
A playbook is an automated query that can add efficiency to the cyberoperations workflow. -
Question 78 of 190
78. Question
1 pointsWhen ACLs are configured to block IP address spoofing and DoS flood attacks, which ICMP message should be allowed both inbound and outbound?Correct
Incorrect
-
Question 79 of 190
79. Question
1 pointsAfter a security monitoring tool identifies a malware attachment entering the network, what is the benefit of performing a retrospective analysis?Correct
Incorrect
Hint
General security monitoring can identify when a malware attachment enters a network and which host is first infected. Retrospective analysis takes the next step and is the tracking of the behavior of the malware from that point forward. -
Question 80 of 190
80. Question
1 pointsWhich two data types would be classified as personally identifiable information (PII)? (Choose two.)Correct
Incorrect
-
Question 81 of 190
81. Question
1 pointsA help desk technician notices an increased number of calls relating to the performance of computers located at the manufacturing plant. The technician believes that botnets are causing the issue. What are two purposes of botnets? (Choose two.)Correct
Incorrect
Hint
Botnets can be used to perform DDoS attacks, obtain data, or transmit malware to other devices on the network. -
Question 82 of 190
82. Question
1 pointsWhich two statements describe the use of asymmetric algorithms? (Choose two.)Correct
Incorrect
Hint
Asymmetric algorithms use two keys: a public key and a private key. Both keys are capable of the encryption process, but the complementary matched key is required for decryption. If a public key encrypts the data, the matching private key decrypts the data. The opposite is also true. If a private key encrypts the data, the corresponding public key decrypts the data. -
Question 83 of 190
83. Question
1 pointsWhich three security services are provided by digital signatures? (Choose three.)Correct
Incorrect
Hint
Digital signatures are a mathematical technique used to provide three basic security services. Digital signatures have specific properties that enable entity authentication and data integrity. In addition, digital signatures provide nonrepudiation of the transaction. In other words, the digital signature serves as legal proof that the data exchange did take place. -
Question 84 of 190
84. Question
1 pointsWhat are two methods to maintain certificate revocation status? (Choose two.)Correct
Incorrect
Hint
A digital certificate might need to be revoked if its key is compromised or it is no longer needed. The certificate revocation list (CRL) and Online Certificate Status Protocol (OCSP), are two common methods to check a certificate revocation status. -
Question 85 of 190
85. Question
1 pointsWhat are two uses of an access control list? (Choose two.)Correct
Incorrect
Hint
ACLs can be used for the following:Limit network traffic in order to provide adequate network performance Restrict the delivery of routing updates Provide a basic level of security Filter traffic based on the type of traffic being sent Filter traffic based on IP addressing -
Question 86 of 190
86. Question
1 pointsA client is using SLAAC to obtain an IPv6 address for the interface. After an address has been generated and applied to the interface, what must the client do before it can begin to use this IPv6 address?Correct
Incorrect
Hint
Stateless DHCPv6 or stateful DHCPv6 uses a DHCP server, but Stateless Address Autoconfiguration (SLAAC) does not. A SLAAC client can automatically generate an address that is based on information from local routers via Router Advertisement (RA) messages. Once an address has been assigned to an interface via SLAAC, the client must ensure via Duplicate Address Detection (DAD) that the address is not already in use. It does this by sending out an ICMPv6 Neighbor Solicitation message and listening for a response. If a response is received, then it means that another device is already using this address. -
Question 87 of 190
87. Question
1 pointsA technician is troubleshooting a network connectivity problem. Pings to the local wireless router are successful but pings to a server on the Internet are unsuccessful. Which CLI command could assist the technician to find the location of the networking problem?Correct
Incorrect
Hint
The tracert utlility (also known as the tracert command or tracert tool) will enable the technician to locate the link to the server that is down. The ipconfig command displays the computer network configuration details. The ipconfig/renew command requests an IP address from a DHCP server. Msconfig is not a network troubleshooting command. -
Question 88 of 190
88. Question
1 pointsWhat are two evasion techniques that are used by hackers? (Choose two.)Correct
Incorrect
Hint
The following methods are used by hackers to avoid detection:Encryption and tunneling – hide or scramble the malware content Resource exhaustion – keeps the host device too busy to detect the invasion Traffic fragmentation – splits the malware into multiple packets Protocol-level misinterpretation – sneaks by the firewall Pivot – uses a compromised network device to attempt access to another device Rootkit – allows the hacker to be undetected and hides software installed by the hacker -
Question 89 of 190
89. Question
1 pointsWhen a security attack has occurred, which two approaches should security professionals take to mitigate a compromised system during the Actions on Objectives step as defined by the Cyber Kill Chain model? (Choose two.)Correct
Incorrect
Hint
When security professionals are alerted about the system compromises, forensic analysis of endpoints should be performed immediately for rapid triage. In addition, detection efforts for further attacking activities such as data exfiltration, lateral movement, and unauthorized credential usage should be enhanced to reduce damage to the minimum. -
Question 90 of 190
90. Question
1 pointsPlace the seven steps defined in the Cyber Kill Chain in the correct order.Correct
Incorrect
-
Question 91 of 190
91. Question
1 pointsWhich field in the TCP header indicates the status of the three-way handshake process?Correct
Incorrect
Hint
The value in the control bits field of theTCP header indicates the progress and status of the connection. -
Question 92 of 190
92. Question
1 pointsA user opens three browsers on the same PC to access www.cisco.com to search for certification course information. The Cisco web server sends a datagram as a reply to the request from one of the web browsers. Which information is used by the TCP/IP protocol stack in the PC to identify which of the three web browsers should receive the reply?Correct
Incorrect
Hint
Each web browser client application opens a randomly generated port number in the range of the registered ports and uses this number as the source port number in the datagram that it sends to a server. The server then uses this port number as the destination port number in the reply datagram that it sends to the web browser. The PC that is running the web browser application receives the datagram and uses the destination port number that is contained in this datagram to identify the client application. -
Question 93 of 190
93. Question
1 pointsWhat are two scenarios where probabilistic security analysis is best suited? (Choose two.)Correct
Incorrect
Hint
Probabilistic analysis relies on statistical techniques that are designed to estimate the probability that an event will occur based on the likelihood that prior events will occur. -
Question 94 of 190
94. Question
1 pointsWhich tool is a web application that provides the cybersecurity analyst an easy-to-read means of viewing an entire Layer 4 session?Correct
Incorrect
-
Question 95 of 190
95. Question
1 pointsMatch the category of attacks with the description. (Not all options are used.)Correct
Incorrect
-
Question 96 of 190
96. Question
1 pointsWhat are two characteristics of the SLAAC method for IPv6 address configuration? (Choose two.)Correct
Incorrect
Hint
With SLAAC, the default gateway for IPv6 clients will be the link-local address of the router interface that is attached to the client LAN. The IPv6 addressing is dynamically assigned via the ICMPv6 protocol. SLAAC is a stateless method of acquiring an IPv6 address, a method that requires no servers. When a client is configured to obtain its addressing information automatically via SLAAC, the client sends a router solicitation message to the IPv6 all-routers multicast address FF02::2. The router advertisement messages are sent by routers to provide addressing information to clients. -
Question 97 of 190
97. Question
1 pointsA technician notices that an application is not responding to commands and that the computer seems to respond slowly when applications are opened. What is the best administrative tool to force the release of system resources from the unresponsive application?Correct
Incorrect
Hint
Use the Task Manager Performance tab to see a visual representation of CPU and RAM utilization. This is helpful in determining if more memory is needed. Use the Applications tab to halt an application that is not responding. -
Question 98 of 190
98. Question
1 pointsHow can statistical data be used to describe or predict network behavior?Correct
Incorrect
Hint
Statistical data is created through the analysis of other forms of network data. Statistical characteristics of normal network behavior can be compared to current network traffic in an effort to detect anomalies. Conclusions resulting from analysis can be used to describe or predict network behavior. -
Question 99 of 190
99. Question
1 pointsWhich metric in the CVSS Base Metric Group is used with an attack vector?Correct
Incorrect
Hint
This is a metric that reflects the proximity of the threat actor to the vulnerable component. The more remote the threat actor is to the component, the higher the severity. Threat actors close to your network or inside your network are easier to detect and mitigate. -
Question 100 of 190
100. Question
1 pointsWhich NIST Cybersecurity Framework core function is concerned with the development and implementation of safeguards that ensure the delivery of critical infrastructure services?Correct
Incorrect
-
Question 101 of 190
101. Question
1 pointsWhich two techniques are used in a smurf attack? (Choose two.)Correct
Incorrect
Hint
A smurf attack uses amplification and reflection techniques to overwhelm a targeted host. The threat actor forwards ICMP echo request messages that contain the source IP address of the victim to a large number of hosts. These hosts all reply to the spoofed IP address of the victim with the intent of overwhelming it. -
Question 102 of 190
102. Question
1 pointsWhat is the primary objective of a threat intelligence platform (TIP)?Correct
Incorrect
-
Question 103 of 190
103. Question
1 pointsWhich wireless parameter is used by an access point to broadcast frames that include the SSID?Correct
Incorrect
Hint
The two scanning or probing modes an access point can be placed into are passive or active. In passive mode, the AP advertises the SSID, supported standards, and security settings in broadcast beacon frames. In active mode, the wireless client must be manually configured for the same wireless parameters as the AP has configured. -
Question 104 of 190
104. Question
1 pointsMatch the field in the Event table of Sguil to the description.Correct
Incorrect
-
Question 105 of 190
105. Question
1 pointsAn employee connects wirelessly to the company network using a cell phone. The employee then configures the cell phone to act as a wireless access point that will allow new employees to connect to the company network. Which type of security threat best describes this situation?Correct
Incorrect
Hint
Configuring the cell phone to act as a wireless access point means that the cell phone is now a rogue access point. The employee unknowingly breached the security of the company network by allowing a user to access the network without connecting through the company access point. Cracking is the process of obtaining passwords from data stored or transmitted on a network. Denial of service attacks refer to sending large amounts of data to a networked device, such as a server, to prevent legitimate access to the server. Spoofing refers to access gained to a network or data by an attacker appearing to be a legitimate network device or user. -
Question 106 of 190
106. Question
1 pointsWhat information is required for a WHOIS query?Correct
Incorrect
-
Question 107 of 190
107. Question
1 pointsWhich two statements describe the characteristics of symmetric algorithms? (Choose two.)Correct
Incorrect
Hint
Symmetric encryption algorithms use the same key (also called shared secret) to encrypt and decrypt the data. In contrast, asymmetric encryption algorithms use a pair of keys, one for encryption and another for decryption. -
Question 108 of 190
108. Question
1 pointsWhat are two drawbacks to using HIPS? (Choose two.)Correct
Incorrect
-
Question 109 of 190
109. Question
1 pointsWhat are three functions provided by the syslog service? (Choose three.)Correct
Incorrect
Hint
There are three primary functions provided by the syslog service:- gathering logging information
- selection of the type of information to be logged
- selection of the destination of the logged information
-
Question 110 of 190
110. Question
1 pointsWhich consideration is important when implementing syslog in a network?Correct
Incorrect
-
Question 111 of 190
111. Question
1 pointsWhat are the two ways threat actors use NTP? (Choose two.)Correct
Incorrect
Hint
Threat actors may attempt to attack the NTP infrastructure in order to corrupt time information used to correlate logged network events. This can serve to obfuscate traces of ongoing exploits. In addition, threat actors have been known to use NTP systems to direct DDoS attacks through vulnerabilities in client or server software. While these attacks do not necessarily result in corrupted security monitoring data, they can disrupt network availability. -
Question 112 of 190
112. Question
1 pointsWhich two features are included by both TACACS+ and RADIUS protocols? (Choose two.)Correct
Incorrect
Hint
Both TACACS+ and RADIUS support password encryption (TACACS+ encrypts all communication) and use Layer 4 protocol (TACACS+ uses TCP and RADIUS uses UDP). TACACS+ supports separation of authentication and authorization processes, while RADIUS combines authentication and authorization as one process. RADIUS supports remote access technology, such as 802.1x and SIP; TACACS+ does not. -
Question 113 of 190
113. Question
1 pointsMatch the SIEM function to the description.Correct
Incorrect
-
Question 114 of 190
114. Question
1 pointsWhat are two types of attacks used on DNS open resolvers? (Choose two.)Correct
Incorrect
Hint
Three types of attacks used on DNS open resolvers are as follows:DNS cache poisoning – attacker sends spoofed falsified information to redirect users from legitimate sites to malicious sites DNS amplification and reflection attacks – attacker sends an increased volume of attacks to mask the true source of the attack DNS resource utilization attacks – a denial of service (DoS) attack that consumes server resources -
Question 115 of 190
115. Question
1 pointsWhat are three goals of a port scan attack? (Choose three.)Correct
Incorrect
-
Question 116 of 190
116. Question
1 pointsWhich protocol or service uses UDP for a client-to-server communication and TCP for server-to-server communication?Correct
Incorrect
Hint
Some applications may use both TCP and UDP. DNS uses UDP when clients send requests to a DNS server, and TCP when two DNS serves directly communicate. -
Question 117 of 190
117. Question
1 pointsWhat is one difference between the client-server and peer-to-peer network models?Correct
Incorrect
Hint
Data transfer speeds depend on a number of factors including the amount of traffic, the quality of service imposed, and the network media. Transfer speeds are not dependent on the network model type. File transfers can occur using the client-server model or the peer-to-peer model. A data transfer between a device acting in the client role and a device acting in the server role can occur in both peer-to-peer and client-server networks. -
Question 118 of 190
118. Question
1 pointsWhich statement is correct about network protocols?Correct
Incorrect
Hint
Network protocols are implemented in hardware, or software, or both. They interact with each other within different layers of a protocol stack. Protocols have nothing to do with the installation of the network equipment. Network protocols are required to exchange information between source and destination devices in both local and remote networks. -
Question 119 of 190
119. Question
1 pointsWhich approach can help block potential malware delivery methods, as described in the Cyber Kill Chain model, on an Internet-faced web server?Correct
Incorrect
Hint
A threat actor may send the weapon through web interfaces to the target server, either in file uploads or coded web requests. By analyzing the infrastructure storage path used for files, security measures can be implemented to monitor and detect malware deliveries through these methods. -
Question 120 of 190
120. Question
1 pointsWhich meta-feature element in the Diamond Model classifies the general type of intrusion event?Correct
Incorrect
Hint
Methodology – This is used to classify the general type of event, such as port scan, phishing, content delivery attack, syn flood, etc. -
Question 121 of 190
121. Question
1 pointsWhich Linux command is used to manage processes?Correct
Incorrect
Hint
The kill command is used to stop, restart, or pause a process. The chrootkit command is used to check the computer for rootkits, a set of software tools that can increase the privilege level of a user or grant access to portions of software normally not allowed. The grep command is used to look for a file or text within a file. The ls command is used to list files, directories, and file information. -
Question 122 of 190
122. Question
1 pointsWhich tool can be used in a Cisco AVC system to analyze and present the application analysis data into dashboard reports?Correct
Incorrect
Hint
A management and reporting system, such as Cisco Prime, can be used to analyze and present the application analysis data into dashboard reports for use by network monitoring personnel. -
Question 123 of 190
123. Question
1 pointsWhich Windows Event Viewer log includes events regarding the operation of drivers, processes, and hardware?Correct
Incorrect
Hint
By default Windows keeps four types of host logs:- Application logs – events logged by various applications
- System logs – events about the operation of drivers, processes, and hardware
- Setup logs – information about the installation of software, including Windows updates
- Security logs – events related to security, such as logon attempts and operations related to file or object management and access
-
Question 124 of 190
124. Question
1 pointsWhich method is used to make data unreadable to unauthorized users?Correct
Incorrect
Hint
Network data can be encrypted using various cryptography applications so that the data is made unreadable to unauthorized users. Authorized users have the cryptography application so the data can be unencrypted. -
Question 125 of 190
125. Question
1 pointsMatch the tabs of the Windows 10 Task Manager to their functions. (Not all options are used.)Correct
Incorrect
-
Question 126 of 190
126. Question
1 pointsFor network systems, which management system addresses the inventory and control of hardware and software configurations?Correct
Incorrect
Hint
Configuration management addresses the inventory and control of hardware and software configurations of network systems. -
Question 127 of 190
127. Question
1 pointsMatch the common network technology or protocol with the description. (Not all options are used.)Correct
Incorrect
-
Question 128 of 190
128. Question
1 pointsWhat are the three core functions provided by the Security Onion? (Choose three.)Correct
Incorrect
Hint
Security Onion is an open source suite of Network Security Monitoring (NSM) tools for evaluating cybersecurity alerts. For cybersecurity analysts the Security Onion provides full packet capture, network-based and host-based intrusion detection systems, and alert analysis tools. -
Question 129 of 190
129. Question
1 pointsIn NAT terms, what address type refers to the globally routable IPv4 address of a destination host on the Internet?Correct
Incorrect
Hint
From the perspective of a NAT device, inside global addresses are used by external users to reach internal hosts. Inside local addresses are the addresses assigned to internal hosts. Outside global addresses are the addresses of destinations on the external network. Outside local addresses are the actual private addresses of destination hosts behind other NAT devices. -
Question 130 of 190
130. Question
1 pointsWhich two fields or features does Ethernet examine to determine if a received frame is passed to the data link layer or discarded by the NIC? (Choose two.)Correct
Incorrect
Hint
An Ethernet frame is not processed and is discarded if it is smaller than the minimum (64 bytes) or if the calculated frame check sequence (FCS) value does not match the received FCS value. Auto-MDIX (automatic medium-dependent interface crossover) is Layer 1 technology that detects cable straight-through or crossover types. The source MAC address is not used to determine how the frame is received. CEF (Cisco Express Forwarding) is a technology used to expedite Layer 3 switching. -
Question 131 of 190
131. Question
1 pointsWhich type of data would be considered an example of volatile data?Correct
Incorrect
Hint
Volatile data is data stored in memory such as registers, cache, and RAM, or it is data that exists in transit. Volatile memory is lost when the computer loses power. -
Question 132 of 190
132. Question
1 pointsWhat is the main purpose of exploitations by a threat actor through the weapon delivered to a target during the Cyber Kill Chain exploitation phase?Correct
Incorrect
Hint
After the weapon has been delivered, the threat actor uses it to break the vulnerability and gain control of the target. The threat actor will use an exploit that gains the effect desired, does it quietly, and avoids detections. Establishing a back door in the target system is the phase of installation. -
Question 133 of 190
133. Question
1 pointsRefer to the exhibit. An administrator is trying to troubleshoot connectivity between PC1 and PC2 and uses the tracert command from PC1 to do it. Based on the displayed output, where should the administrator begin troubleshooting?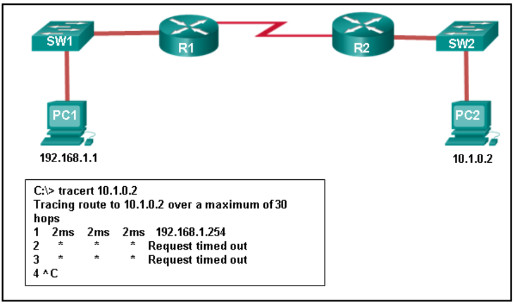 Correct
Correct
Incorrect
Hint
Tracert is used to trace the path a packet takes. The only successful response was from the first device along the path on the same LAN as the sending host. The first device is the default gateway on router R1. The administrator should therefore start troubleshooting at R1. -
Question 134 of 190
134. Question
1 pointsWhat three security tools does Cisco Talos maintain security incident detection rule sets for? (Choose three.)Correct
Incorrect
Hint
Talos maintains the security incident detection rule sets for the Snort.org, ClamAV, and SpamCop network security tools. -
Question 135 of 190
135. Question
1 pointsWhich host-based firewall uses a three-profile approach to configure the firewall functionality?Correct
Incorrect
Hint
Windows Firewall uses a profile-based approach to configuring firewall functionality. It uses three profiles, Public, Private, and Domain, to define firewall functions. -
Question 136 of 190
136. Question
1 pointsWhen a user visits an online store website that uses HTTPS, the user browser queries the CA for a CRL. What is the purpose of this query?Correct
Incorrect
Hint
A digital certificate must be revoked if it is invalid. CAs maintain a certificate revocation list (CRL), a list of revoked certificate serial numbers that have been invalidated. The user browser will query the CRL to verify the validity of a certificate. -
Question 137 of 190
137. Question
1 pointsWhich step in the Vulnerability Management Life Cycle determines a baseline risk profile to eliminate risks based on asset criticality, vulnerability threat, and asset classification?Correct
Incorrect
Hint
The steps in the Vulnerability Management Life Cycle include these:- Discover – inventory all assets across the network and identify host details, including operating systems and open services, to identify vulnerabilities
- Prioritize assets – categorize assets into groups or business units, and assign a business value to asset groups based on their criticality to business operations
- Assess – determine a baseline risk profile to eliminate risks based on asset criticality, vulnerability threats, and asset classification
- Report – measure the level of business risk associated with assets according to security policies. Document a security plan, monitor suspicious activity, and describe known vulnerabilities.
- Remediate – prioritize according to business risk and fix vulnerabilities in order of risk
- Verify – verify that threats have been eliminated through follow-up audits
-
Question 138 of 190
138. Question
1 pointsWhich management system implements systems that track the location and configuration of networked devices and software across an enterprise?Correct
Incorrect
Hint
Asset management involves the implementation of systems that track the location and configuration of networked devices and software across an enterprise. -
Question 139 of 190
139. Question
1 pointsA network administrator is reviewing server alerts because of reports of network slowness. The administrator confirms that an alert was an actual security incident. What is the security alert classification of this type of scenario?Correct
Incorrect
Hint
True Positive: The alert has been verified to be an actual security incident. False Positive: The alert does not indicate an actual security incident. Benign activity that results in a false positive is sometimes referred to as a benign trigger. True Negative: No security incident has occurred. The activity is benign. False Negative: An undetected incident has occurred. -
Question 140 of 190
140. Question
1 pointsWhich application layer protocol is used to provide file-sharing and print services to Microsoft applications?Correct
Incorrect
Hint
SMB is used in Microsoft networking for file-sharing and print services. The Linux operating system provides a method of sharing resources with Microsoft networks by using a version of SMB called SAMBA. -
Question 141 of 190
141. Question
1 pointsWhich device in a layered defense-in-depth approach denies connections initiated from untrusted networks to internal networks, but allows internal users within an organization to connect to untrusted networks?Correct
Incorrect
Hint
A firewall is typically a second line of defense in a layered defense-in-depth approach to network security. The firewall typically connects to an edge router that connects to the service provider. The firewall tracks connections initiated within the company going out of the company and denies initiation of connections from external untrusted networks going to internal trusted networks. -
Question 142 of 190
142. Question
1 pointsWhat are two potential network problems that can result from ARP operation? (Choose two.)Correct
Incorrect
Hint
Large numbers of ARP broadcast messages could cause momentary data communications delays. Network attackers could manipulate MAC address and IP address mappings in ARP messages with the intent to intercept network traffic. ARP requests and replies cause entries to be made into the ARP table, not the MAC address table. ARP table overflows are very unlikely. Manually configuring static ARP associations is a way to prevent, not facilitate, ARP poisoning and MAC address spoofing. Multiple ARP replies resulting in the switch MAC address table containing entries that match the MAC addresses of connected nodes and are associated with the relevant switch port are required for normal switch frame forwarding operations. It is not an ARP caused network problem. -
Question 143 of 190
143. Question
1 pointsWhich three procedures in Sguil are provided to security analysts to address alerts? (Choose three.)Correct
Incorrect
Hint
Sguil is a tool for addressing alerts. Three tasks can be completed in Sguil to manage alerts:- Alerts that have been found to be false positives can be expired.
- An alert can be escalated if the cybersecurity analyst is uncertain how to handle it.
- Events that have been identified as true positives can be categorized.
-
Question 144 of 190
144. Question
1 pointsMatch the SOC metric with the description. (Not all options apply.)Correct
Incorrect
-
Question 145 of 190
145. Question
1 pointsWhich two services are provided by the NetFlow tool? (Choose two.)Correct
Incorrect
Hint
NetFlow efficiently provides an important set of services for IP applications including network traffic accounting, usage-based network billing, network planning, security, denial of service monitoring capabilities, and network monitoring. -
Question 146 of 190
146. Question
1 pointsAn administrator discovers that a user is accessing a newly established website that may be detrimental to company security. What action should the administrator take first in terms of the security policy?Correct
Incorrect
Hint
One of the most common security policy components is an AUP. This can also be referred to as an appropriate use policy. This component defines what users are allowed and not allowed to do on the various system components. This includes the type of traffic that is allowed on the network. The AUP should be as explicit as possible to avoid misunderstanding. -
Question 147 of 190
147. Question
1 pointsWhich two tasks can be performed by a local DNS server? (Choose two.)Correct
Incorrect
Hint
Two important functions of DNS are to (1) provide IP addresses for domain names such as http://www.cisco.com, and (2) forward requests that cannot be resolved to other servers in order to provide domain name to IP address translation. DHCP provides IP addressing information to local devices. A file transfer protocol such as FTP, SFTP, or TFTP provides file sharing services. IMAP or POP can be used to retrieve an email message from a server. -
Question 148 of 190
148. Question
1 pointsWhich type of event is logged in Cisco Next-Generation IPS devices (NGIPS) using FirePOWER Services when changes have been detected in the monitored network?Correct
Incorrect
Hint
Network discovery events in Cisco NGIPS represent changes that have been detected in the monitored network. -
Question 149 of 190
149. Question
1 pointsWhich two actions should be taken during the preparation phase of the incident response life cycle defined by NIST? (Choose two.)Correct
Incorrect
-
Question 150 of 190
150. Question
1 pointsWhat subnet mask is represented by the slash notation /20?Correct
Incorrect
Hint
The slash notation /20 represents a subnet mask with 20 1s. This would translate to: 11111111.11111111.11110000.0000, which in turn would convert into 255.255.240.0. -
Question 151 of 190
151. Question
1 pointsWhat is the benefit of converting log file data into a common schema?Correct
Incorrect
Hint
When data is converted into a universal format, it can be effectively structured for performing fast queries and event analysis. -
Question 152 of 190
152. Question
1 pointsWhich Cisco sponsored certification is designed to provide the first step in acquiring the knowledge and skills to work with a SOC team?Correct
Incorrect
Hint
The Cisco Certified CyberOps Associate certification provides a valuable first step in acquiring the knowledge and skills needed to work with a SOC team. It can be a valuable part of a career in the exciting and growing field of cybersecurity operations. -
Question 153 of 190
153. Question
1 pointsWhich three IP addresses are considered private addresses? (Choose three.)Correct
Incorrect
Hint
The designated private IP addresses are within the three IP address ranges:- 10.0.0.0 – 10.255.255.255
- 172.16.0.0 – 172.31.255.255
- 192.168.0.0 – 192.168.255.255
-
Question 154 of 190
154. Question
1 pointsWhen establishing a network profile for an organization, which element describes the time between the establishment of a data flow and its termination?Correct
Incorrect
Hint
A network profile should include some important elements, such as the following: Total throughput – the amount of data passing from a given source to a given destination in a given period of time Session duration – the time between the establishment of a data flow and its termination Ports used – a list of TCP or UDP processes that are available to accept data Critical asset address space – the IP addresses or the logical location of essential systems or data -
Question 155 of 190
155. Question
1 pointsWhat are the stages that a wireless device completes before it can communicate over a wireless LAN network?Correct
Incorrect
-
Question 156 of 190
156. Question
1 pointsMatch the correct sequence of steps typically taken by a threat actor carrying out a domain shadowing attack.Correct
Incorrect
-
Question 157 of 190
157. Question
1 pointsWhat are two properties of a cryptographic hash function? (Choose two.)Correct
Incorrect
Hint
A cryptographic hash function should have the following properties:The input can be any length. The output has a fixed length. The hash value is relatively easy to compute for any given input. The hash is one way and not reversible. The hash is collision free, meaning that two different input values will result in different hash values -
Question 158 of 190
158. Question
1 pointsRefer to the exhibit. The switches have a default configuration. Host A needs to communicate with host D, but host A does not have the MAC address for the default gateway. Which network devices will receive the ARP request sent by host A?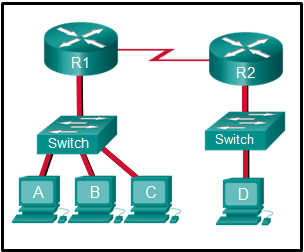 Correct
Correct
Incorrect
-
Question 159 of 190
159. Question
1 pointsWhich type of evidence cannot prove an IT security fact on its own?Correct
Incorrect
Hint
Indirect evidence cannot prove a fact on its own, but direct evidence can. Corroborative evidence is supporting information. Best evidence is most reliable because it is something concrete such as a signed contract. -
Question 160 of 190
160. Question
1 pointsWhat is a characteristic of a probabilistic analysis in an alert evaluation?Correct
Incorrect
Hint
Statistical techniques can be used to evaluate the risk that exploits will be successful in a given network. This type of analysis can help decision makers to better evaluate the cost of mitigating a threat and the damage that an exploit could cause. Two general approaches used to do this are as follows:- Deterministic Analysis: For an exploit to be successful, all prior steps in the exploit must also be successful. The cybersecurity analyst knows the steps for a successful exploit.
- Probabilistic Analysis: Statistical techniques are used to determine the probability that a successful exploit will occur based on the likelihood that each step in the exploit will succeed.
-
Question 161 of 190
161. Question
1 pointsWhy would a network administrator choose Linux as an operating system in the Security Operations Center (SOC)?Correct
Incorrect
Hint
Linux is open source – Any person can acquire Linux at no charge and modify it to fit specific needs. This flexibility allows analysts and administrators to tailor-build an operating system specifically for security analysis. -
Question 162 of 190
162. Question
1 pointsA technician needs to verify file permissions on a specific Linux file. Which command would the technician use?Correct
Incorrect
-
Question 163 of 190
163. Question
1 pointsWhich two protocols may devices use in the application process that sends email? (Choose two.)Correct
Incorrect
Hint
POP, POP3, and IMAP are protocols that are used to retrieve email from servers. SMTP is the default protocol that is used to send email. DNS may be used by the sender email server to find the address of the destination email server. HTTP is a protocol for send and receiving web pages. -
Question 164 of 190
164. Question
1 pointsWhich file system type was specifically created for optical disk media?Correct
Incorrect
-
Question 165 of 190
165. Question
1 pointsA piece of malware has gained access to a workstation and issued a DNS lookup query to a CnC server. What is the purpose of this attack?Correct
Incorrect
Hint
A piece of malware, after accessing a host, may exploit the DNS service by communicating with command-and-control (CnC) servers and then exfiltrate data in traffic disguised as normal DNS lookup queries. Various types of encoding, such as base64, 8-bit binary, and hex can be used to camouflage the data and evade basic data loss prevention (DLP) measures. -
Question 166 of 190
166. Question
1 pointsRefer to the exhibit. Which field in the Sguil event window indicates the number of times an event is detected for the same source and destination IP address?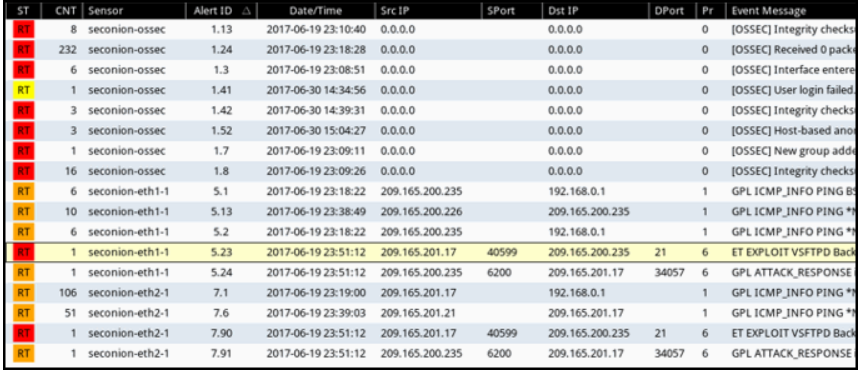 Correct
Correct
Incorrect
Hint
The CNT field indicates the number of times an event is detected from the same source and destination IP address. Having a high number of events can indicated a problem with event signatures. -
Question 167 of 190
167. Question
1 pointsRefer to the exhibit. The IP address of which device interface should be used as the default gateway setting of host H1?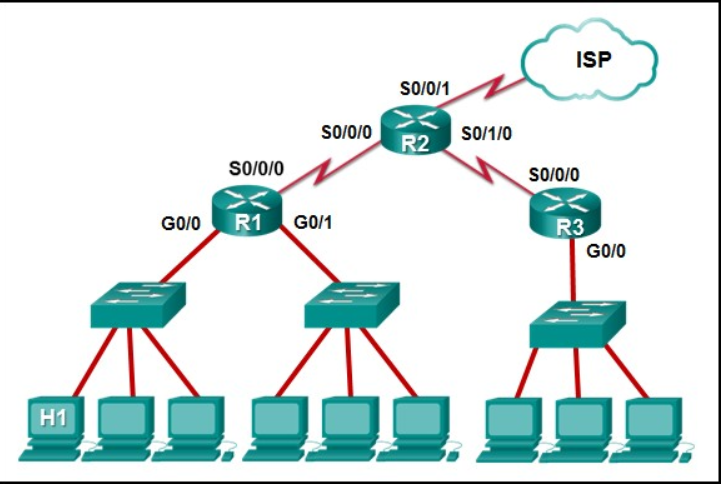 Correct
Correct
Incorrect
Hint
The default gateway for host H1 is the router interface that is attached to the LAN that H1 is a member of. In this case, that is the G0/0 interface of R1. H1 should be configured with the IP address of that interface in its addressing settings. R1 will provide routing services to packets from H1 that need to be forwarded to remote networks. -
Question 168 of 190
168. Question
1 pointsAccording to information outlined by the Cyber Kill Chain, which two approaches can help identify reconnaissance threats? (Choose two.)Correct
Incorrect
Hint
Threat actors may use port scanning toward a web server of an organization and identify vulnerabilities on the server. They may visit the web server to collect information about the organization. The web server logging should be enabled and the logging data should be analyzed to identify possible reconnaissance threats. Building playbooks by filtering and combining related web activities by visitors can sometimes reveal the intentions of threat actors. -
Question 169 of 190
169. Question
1 pointsWhich two ICMPv6 messages are used during the Ethernet MAC address resolution process? (Choose two.)Correct
Incorrect
Hint
IPv6 uses neighbor solicitation (NS) and neighbor advertisement (NA) ICMPv6 messages for MAC address resolution. -
Question 170 of 190
170. Question
1 pointsWhat best describes the destination IPv4 address that is used by multicasting?Correct
Incorrect
Hint
The destination multicast IPv4 address is a group address, which is a single IP multicast address within the Class D range. -
Question 171 of 190
171. Question
1 pointsWhat is the result of using security devices that include HTTPS decryption and inspection services?Correct
Incorrect
Hint
HTTPS adds extra overhead to the HTTP-formed packet. HTTPS encrypts using Secure Sockets Layer (SSL). Even though some devices can perform SSL decryption and inspection, this can present processing and privacy issues. -
Question 172 of 190
172. Question
1 pointsWhat is a disadvantage of DDNS?Correct
Incorrect
Hint
Dynamic DNS can be abused by threat actors in various ways. Free DDNS services are especially useful to threat actors. DDNS can be used to facilitate the rapid change of IP address for malware command-and-control servers after the current IP address has become widely blocked. -
Question 173 of 190
173. Question
1 pointsMatch the network-based antimalware solution to the function. (Not all options are used.)Correct
Incorrect
-
Question 174 of 190
174. Question
1 pointsA threat actor has identified the potential vulnerability of the web server of an organization and is building an attack. What will the threat actor possibly do to build an attack weapon?Correct
Incorrect
Hint
One tactic of weaponization used by a threat actor after the vulnerability is identified is to obtain an automated tool to deliver the malware payload through the vulnerability. -
Question 175 of 190
175. Question
1 pointsWhich tool included in the Security Onion is a series of software plugins that send different types of data to the Elasticsearch data stores?Correct
Incorrect
-
Question 176 of 190
176. Question
1 pointsWhich term is used to describe the process of identifying the NSM-related data to be gathered?Correct
Incorrect
-
Question 177 of 190
177. Question
1 pointsMatch the alert classification with the description.Correct
Incorrect
-
Question 178 of 190
178. Question
1 pointsAccording to NIST, which step in the digital forensics process involves preparing and presenting information that resulted from scrutinizing data?Correct
Incorrect
Hint
NIST describes the digital forensics process as involving the following four steps: Collection – the identification of potential sources of forensic data and acquisition, handling, and storage of that data Examination – assessing and extracting relevant information from the collected data. This may involve decompression or decryption of the data Analysis – drawing conclusions from the data. Salient features, such as people, places, times, events, and so on should be documented Reporting – preparing and presenting information that resulted from the analysis. Reporting should be impartial and alternative explanations should be offered if appropriate -
Question 179 of 190
179. Question
1 pointsRefer to the exhibit. A cybersecurity analyst is using Sguil to verify security alerts. How is the current view sorted?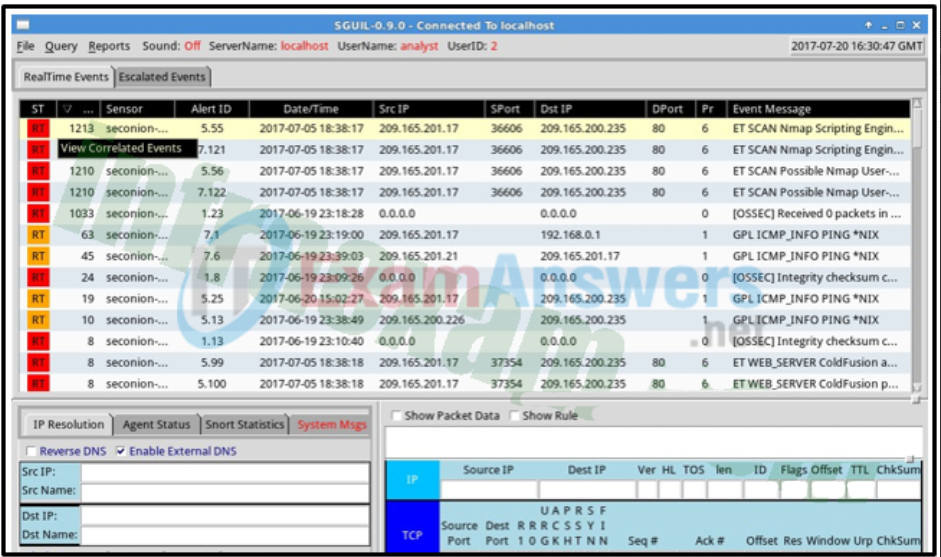 Correct
Correct
Incorrect
Hint
The CNT column, between the ST and Sensor columns, displays the frequency of alerts. By sorting with frfequency, the analyst will get a better sense of what has happened on the network. -
Question 180 of 190
180. Question
1 pointsWhich two options are window managers for Linux? (Choose two.)Correct
Incorrect
-
Question 181 of 190
181. Question
1 pointsWhat are the two methods that a wireless NIC can use to discover an AP? (Choose two.)Correct
Incorrect
Hint
Two methods can be used by a wireless device to discover and register with an access point: passive mode and active mode. In passive mode, the AP sends a broadcast beacon frame that contains the SSID and other wireless settings. In active mode, the wireless device must be manually configured for the SSID, and then the device broadcasts a probe request. -
Question 182 of 190
182. Question
1 pointsA client device has initiated a secure HTTP request to a web browser. Which well-known port address number is associated with the destination address?Correct
Incorrect
Hint
Port numbers are used in TCP and UDP communications to differentiate between the various services running on a device. The well-known port number used by HTTPs is port 443. -
Question 183 of 190
183. Question
1 pointsWhich term describes evidence that is in its original state?Correct
Incorrect
Hint
Evidence can be classified as follows: Best evidence: This is evidence that is in its original state. It might be storage devices used by an accused or archives of files that can be proven to be unaltered. Corroborating evidence: This is evidence that supports a propositionalready supported by initial evidence, therefore confirming the original proposition. Indirect evidence: This evidence acts in combination with other facts to establish a hypothesis. -
Question 184 of 190
184. Question
1 pointsWhich three statements describe a DHCP Discover message? (Choose three.)Correct
Incorrect
Hint
When a host configured to use DHCP powers up on a network it sends a DHCPDISCOVER message. FF-FF-FF-FF-FF-FF is the L2 broadcast address. A DHCP server replies with a unicast DHCPOFFER message back to the host. -
Question 185 of 190
185. Question
1 pointsRefer to the exhibit. The PC is sending a packet to the Server on the remote network. Router R1 is performing NAT overload. From the perspective of the PC, match the NAT address type with the correct IP address. (Not all options are used.)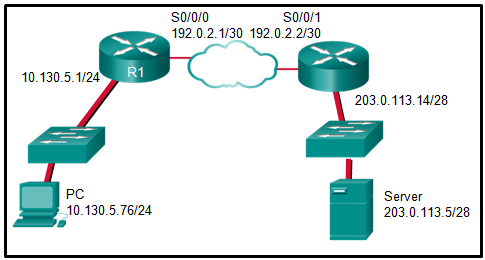 Correct
Correct
Incorrect
Hint
The inside local address is the private IP address of the source or the PC in this instance. The inside global address is the translated address of the source or the address as seen by the outside device. Since the PC is using the outside address of the R1 router, the inside global address is 192.0.2.1. The outside addressing is simply the address of the server or 203.0.113.5. -
Question 186 of 190
186. Question
1 pointsWhich step in the Vulnerability Management Life Cycle categorizes assets into groups or business units, and assigns a business value to asset groups based on their criticality to business operations?Correct
Incorrect
Hint
The steps in the Vulnerability Management Life Cycle include these: Discover – inventory all assets across the network and identify host details, including operating systems and open services to identify vulnerabilities Prioritize assets – categorize assets into groups or business units, and assign a business value to asset groups based on their criticality to business operations Assess – determine a baseline risk profile to eliminate risks based on asset criticality, vulnerability threats, and asset classification Report – measure the level of business risk associated with your assets according to your security policies. Document a security plan, monitor suspicious activity, and describe known vulnerabilities Remediate – prioritize according to business risk and fix vulnerabilities in order of risk Verify – verify that threats have been eliminated through follow-up audits -
Question 187 of 190
187. Question
1 pointsA client application needs to terminate a TCP communication session with a server. Place the termination process steps in the order that they will occur. (Not all options are used.)Correct
Incorrect
Hint
In order to terminate a TCP session, the client sends to the server a segment with the FIN flag set. The server acknowledges the client by sending a segment with the ACK flag set. The server sends a FIN to the client to terminate the server to client session. The client acknowledges the termination by sending a segment with the ACK flag set. -
Question 188 of 190
188. Question
1 pointsMatch the attack vector with the description.Correct
Incorrect
-
Question 189 of 190
189. Question
1 pointsMatch the security management function with the description.Correct
Incorrect
-
Question 190 of 190
190. Question
1 pointsWhat are two functions that are provided by the network layer? (Choose two.)Correct
Incorrect
