Check answers here:
IT Essentials (Version 8.0) Final Exam (Chapters 10-14) Answers
Quiz-summary
0 of 159 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
- 151
- 152
- 153
- 154
- 155
- 156
- 157
- 158
- 159
Information
IT Essentials 7.0 Final Exam (Chapters 10-14) Test Online
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 159 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
- 151
- 152
- 153
- 154
- 155
- 156
- 157
- 158
- 159
- Answered
- Review
-
Question 1 of 159
1. Question
1 pointsMatch the Windows 10 boot sequence after the boot manager (bootmgr.exe) loads.Correct
Incorrect
-
Question 2 of 159
2. Question
1 pointsMatch the correct API with its function within the Windows 10 environment.Correct
Incorrect
-
Question 3 of 159
3. Question
1 pointsWhich two tools are available to transfer user data and settings from an old Windows computer to a Windows operating system on a new computer? (Choose two.)Correct
Incorrect
Hint
When a new operating system is being installed, existing user data and settings need to be migrated from the old to the new operating system. The User State Migration Tool and the Windows Easy Transfer Tool are available to perform this task on the Windows Vista, 7, and 8 operating systems. -
Question 4 of 159
4. Question
1 pointsA user wants to extend a primary partition formatted with the NTFS file system with the unallocated space on the hard disk. What must the user do after the primary partition is extended to make it usable?Correct
Incorrect
Hint
A partition must be formatted with the NTFS file system in order to extend it by using the unallocated space on the disk. Once the partition has been extended, the disk type must be converted to a dynamic disk in order for the new partition to be accessible. -
Question 5 of 159
5. Question
1 pointsWhy is a full format more beneficial than a quick format when preparing for a clean OS installation?Correct
Incorrect
Hint
A full format removes files from a partition while scanning the disk for bad sectors. A quick format will remove files from a partition but does not scan a disk for bad sectors. -
Question 6 of 159
6. Question
1 pointsA technician wishes to prepare the computers in the network for disaster recovery. The network consists of a variety of desktops and laptops from different vendors. All the computers are running either a 32-bit version of Windows 10 Pro or a 64-bit version of Windows 10 Pro. How would the technician prepare the recovery media?Correct
Incorrect
Hint
All the PCs are from different vendors and thus have dissimilar hardware configurations. Furthermore, all the PCs have a variety of 32-bit Windows 10 and 64-bit Windows 10. Because the PCs have different versions of the OS and dissimilar hardware, you cannot use the same image on all the PCs . In order to use a single image, Sysprep must be used to strip out machine specific information like the SID, and all PCs must have the same hardware configuration and the same version of the Windows operating system. -
Question 7 of 159
7. Question
1 pointsA technician wishes to deploy Windows 10 Pro to multiple PCs through the remote network installation process. The technician begins by connecting the new PCs to the network and booting them up. However, the deployment fails because the target PCs are unable to communicate with the deployment server. What is the possible cause?Correct
Incorrect
Hint
The NIC cards on the new PCs have to be PXE-enabled in order for them to communicate with the remote installation services on the server. -
Question 8 of 159
8. Question
1 pointsWhich condition is required when planning to install Windows on a GPT disk?Correct
Incorrect
Hint
The globally unique identifier (GUID) partition table (GPT) makes use of a number of modern techniques to expand on the older MBR partitioning scheme. GPT is commonly used in computers with UEFI firmware. For Windows 10 to be installed on, and boot, from a GPT disk UEFI must be used. -
Question 9 of 159
9. Question
1 pointsA technician wishes to perform a customized unattended network installation of Windows 10 on a PC. The requirements include the installation of specific applications and device drivers through the use of an answer file. What would the technician use to create the answer file?Correct
Incorrect
Hint
To perform a custom Windows Unattended installation, setup.exe must be run with the user options found in the answer file. Additional packages, such as applications or drivers, can be added to the answer file. The Windows System Image Manager (SIM) is used to create the setup answer file. -
Question 10 of 159
10. Question
1 pointsAn organization has purchased a custom application for the sales staff that can only be installed on a 64-bit Windows operating system. Each member of the sales staff has a Windows 8.1 32-bit PC. What must the IT department do in order to install and run the application on the sales staff computers?Correct
Incorrect
Hint
A 32-bit OS cannot be upgraded to a 64-bit OS. In this case a clean install of Windows 64-bit would be the only option because the application requires a 64-bit Windows environment to work. -
Question 11 of 159
11. Question
1 pointsMatch the tabs of the Windows 10 Task Manager to their functions. (Not all options are used.)Correct
Incorrect
-
Question 12 of 159
12. Question
1 pointsMatch the drive status indicators in the Disk Management utility with their description. (Not all options are used.)Correct
Incorrect
-
Question 13 of 159
13. Question
1 pointsMatch the wireless security settings to the description. (Not all options are used.)Correct
Incorrect
-
Question 14 of 159
14. Question
1 pointsWhat are two possible solutions to any Windows computer restarting continuously and never displaying the desktop? (Choose two.)Correct
Incorrect
Hint
Upgrading the processor, upgrading the video card, or resetting the hard drive jumper would not fix this problem. Boot order settings cannot cause the system to reboot continuously. -
Question 15 of 159
15. Question
1 pointsA technician uses Microsoft Deployment Image Servicing and Management (DISM) tool to create a Windows image file on one of the workstations running Windows 10. When the technician tries to clone another workstation with the image file, the workstation exhibits network connectivity issues on completion. What could cause this?Correct
Incorrect
Hint
The technician must use Sysprep to clean up the local specific configuration, such as the SID, otherwise the cloned systems will not work properly. -
Question 16 of 159
16. Question
1 pointsA user complains that user files cannot be synced with the network file server while the user is traveling out of the office. The user had access to the internet but no access to the company network server. How can this be addressed?Correct
Incorrect
Hint
Because the user has access to the internet, access to the Microsoft OneDrive cloud based service is possible and thus the user can sync with Microsoft OneDrive, which in turn can sync with the company network server from across the internet. -
Question 17 of 159
17. Question
1 pointsA technician has connected a new internal hard drive to a Windows 10 PC. What must be done in order for Windows 10 to use the new hard drive?Correct
Incorrect
Hint
The new hard drive needs to be initialized before it can be used in Windows. This will involve formatting the disk which will erase any existing data on the drive. -
Question 18 of 159
18. Question
1 pointsWhat service does PRINT$ provide?Correct
Incorrect
Hint
PRINT$ is a hidden share for printer drivers. It is shared by default and used to access remote shared printers or provide drivers to clients when sharing a printer. -
Question 19 of 159
19. Question
1 pointsA technician is troubleshooting a Windows 10 laptop infected with a virus that has damaged the master boot record. The technician has booted the laptop using the installation media and is attempting to repair the laptop from the command line interface. Which command can the technician use to repair the corrupt master boot record?Correct
Incorrect
Hint
The sfc /scannow command is used to check the integristy of the system files. The msconfig command allows for viewing the startup configuration mode, while the chkdsk command is used to repair the Windows file system. The bootrec /fixmbr command is used to repair a corrupt master boot record in a Windows 10 environment. -
Question 20 of 159
20. Question
1 pointsA user reports that a Windows 10 PC displays the error message “Invalid Boot Disk” during the boot process. The IT technician attempts to boot the computer and finds that the error message occurs immediately after the POST. What could be the possible cause?Correct
Incorrect
Hint
The message “invalid Boot Disk” could be a symptom of a missing or damaged MBR/GPT, a missing or damaged Boot Configuration Data file, a boot sector virus, a boot order not set correctly in BIOS, media without an operating system being in a drive, a hard drive not detected or damaged, or the absence of an installed operating system. -
Question 21 of 159
21. Question
1 pointsWhich port number is used by Virtual Network Computing (VNC) to provide remote screen sharing between devices?Correct
Incorrect
Hint
Virtual Network Computing (VNC) is a freeware product that is similar in functionality to RDP and works over port 5900. -
Question 22 of 159
22. Question
1 pointsWhich feature is included with macOS and provides the ability for a remote user to view and change files, folders, and applications on the local computer?Correct
Incorrect
Hint
In macOS, remote access functionality is provided by the Screen Sharing feature, which is based on Virtual Network Computing (VNC). VNC is a freeware product that is similar in functionality to RDP and works over port 5900. -
Question 23 of 159
23. Question
1 pointsWhich area of concern falls under the operations and planning category in IT documentation?Correct
Incorrect
Hint
There are four broad categories of IT documentation: Policies, Operations, Projects, and User documentation. Operations is concerned with inventory management. -
Question 24 of 159
24. Question
1 pointsMatch the individual languages with their corresponding classification.Correct
Incorrect
Hint
Scripting languages include Windows batch files, PowerShell, Linux shell script, VBScript, JavaScript, and Python. Compiled languages include C, C++, C#, and Java. -
Question 25 of 159
25. Question
1 pointsWhich two actions should a technician take if illegal content, such as child pornography, is discovered on the hard drive of a customer computer? (Choose two.)Correct
Incorrect
Hint
If illegal content is found, begin documentation to build a chain of custody and contact a first responder immediately. -
Question 26 of 159
26. Question
1 pointsWhat are three pieces of information a level one technician should gather from a customer? (Choose three.)Correct
Incorrect
Hint
A level one technician should gather information from the customer and solve simple problems. For more advanced diagnostics, opening the computer case, running diagnostics software, and performing remote connections, the problem should be escalated to a level two technician. -
Question 27 of 159
27. Question
1 pointsWhat two actions are appropriate for a support desk technician to take when assisting customers? (Choose two.)Correct
Incorrect
Hint
When dealing with customers, a technician should show professionalism in all aspects. A technician should observe the process before putting a customer on hold. First, let the customer finish speaking. Then, explain that there is need to put the customer on hold for a short period, and ask the customer for permission to do so. Tell the customer that it will be only a few minutes and explain what you will do during the period. When the customer agrees to be put on hold, thank the customer. -
Question 28 of 159
28. Question
1 pointsA support desk technician is dealing with an angry customer. Which two approaches should the technician take in dealing with the customer? (Choose two.)Correct
Incorrect
Hint
Angry customers should be allowed to explain the problem, then be redirected to discussing how the problem can be solved. Transferring the customer, replying in a rude tone, and asking unrelated questions will usually increase, not ease, the anger being expressed by the customer. -
Question 29 of 159
29. Question
1 pointsWhat two kinds of problems should be escalated from a level one technician to a level two technician? (Choose two.)Correct
Incorrect
Hint
A problem should be escalated to a level two technician when the problem is going to take a long time to fix, is affecting a large number of users, or requires knowledge or expertise that the level one technician does not possess. -
Question 30 of 159
30. Question
1 pointsAn IT technician in a service company has provided extensive remote IT support with product deployment for a customer. After the completion of the contract, a complaint is filed against the IT technician for not following company policy by sending unsolicited emails about services and products that are not related to the contract. What two things should the IT support technician have done differently? (Choose two.)Correct
Incorrect
Hint
While working with customers both briefly and over an extended period of time, it is possible to form friendly relationships. It is important to always follow company policy and never send unsolicited messages to a customer. Also do not send unsolicited mass mailings or chain letters to customers from a company email address. Any personal relationships should be kept via personal email accounts and should not reflect the IT organization of the employer. -
Question 31 of 159
31. Question
1 pointsA third-party security firm is performing a security audit of a company and recommends the company utilize the Remote Desktop Protocol. What are two characteristics of the Microsoft Remote Desktop Protocol (RDP)? (Choose two.)Correct
Incorrect
Hint
The Remote Desktop protocol (RDP) is used to remotely access a Windows OS. It is a client/server protocol.The port number for RDP is TCP port 3389 and it uses encryption. -
Question 32 of 159
32. Question
1 pointsWhich subject area describes collecting and analyzing data from computer systems, networks, and storage devices, as part of an investigation of alleged illegal activity?Correct
Incorrect
Hint
The field of computer forensics involves collecting and analyzing data from computer systems, networks, wireless communications, and storage devices. -
Question 33 of 159
33. Question
1 pointsIn a computer forensics investigation, which type of data is considered volatile data and can be lost if power is removed from the computer?Correct
Incorrect
Hint
Volatile data is a data that is lost when power is turned off, and is located in temporary storage such as RAM, cache, CPU or in transit between them. -
Question 34 of 159
34. Question
1 pointsRefer to the exhibit. During the troubleshooting of software that is installed on a computer system, a level one technician requires help from a level two technician. The file shown in the exhibit must be sent to the level two technician. How should the level one technician deliver this file?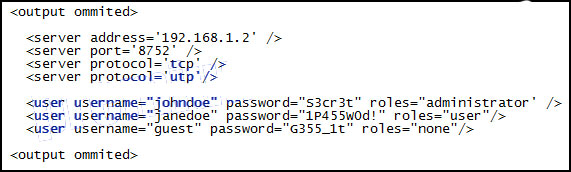 Correct
Correct
Incorrect
Hint
Customer privacy should be maintained. The easiest way to preserve it is removing any occurrence of passwords from the documentation that is being sent to another technician. If a client password is required to solve the problem, it should be sent to another technician through a specific document. -
Question 35 of 159
35. Question
1 pointsWhat skill is essential for a level one technician to have?Correct
Incorrect
Hint
The level one technician must be able to translate the description of a customer problem into a succinct sentence or two that is entered into the work order. -
Question 36 of 159
36. Question
1 pointsWhat is used to control illegal use of software and content?Correct
Incorrect
Hint
Digital rights management, or DRM, is software that is designed to prevent illegal access to digital content. -
Question 37 of 159
37. Question
1 pointsWhat determines the level of support that a call center technician will provide to an individual customer?Correct
Incorrect
Hint
A call center technician must provide the level of support that is outlined in the SLA for that individual customer. -
Question 38 of 159
38. Question
1 pointsA bench technician enters the server room and finds the backup server computer case open. The hard drives containing patient medical data are all physically disconnected from the motherboard and the SATA data cables are hanging outside the case. Which step should the technician immediately take?Correct
Incorrect
Hint
When a potential crime scene is found, a chain of custody must be observed and followed. The technician should immediately locate another employee who is qualified to collect evidence. Disconnecting or reconnecting the drives or attempting to move data may adversely affect the chain of custody. -
Question 39 of 159
39. Question
1 pointsWhat is the difference between a scripting language and a compiled language?Correct
Incorrect
Hint
A scripting language is different than a compiled language because each line is interpreted and then executed when the script is run. Compiled languages need to be converted into executable code using a compiler. Another difference between the two types of languages is that compiled languages are executed by the CPU while scripting languages are executed by a command interpreter or by the operating system. -
Question 40 of 159
40. Question
1 pointsWhich methods can be used to implement multifactor authentication?Correct
Incorrect
Hint
A cybersecurity specialist must be aware of the technologies available that support the CIA triad. -
Question 41 of 159
41. Question
1 pointsWhen responding to a call from a customer who is experiencing problems with a computer, the technician notices that a number of system files on the computer have been renamed. Which two possible solutions could the technician implement to resolve the problem? (Choose two.)Correct
Incorrect
Hint
Renamed system files are usually the result of a virus on the computer. Removing the virus and restoring the computer from a backup are the only two possible solutions in this case. -
Question 42 of 159
42. Question
1 pointsA technician suspects that a security issue is causing problems with a computer. What two actions could be performed to test theories of probable cause when troubleshooting the PC? (Choose two.)Correct
Incorrect
Hint
Several actions can be taken by a technician when security issues are suspected as the possible cause of a problem with a computer. Logging in as a different user or disconnecting the PC from the network to isolate the cause of the problem are two possible actions. -
Question 43 of 159
43. Question
1 pointsThe CIO wants to secure data on company laptops by implementing file encryption. The technician determines the best method is to encrypt each hard drive using Windows BitLocker. Which two things are needed to implement this solution? (Choose two.)Correct
Incorrect
Hint
Windows provides a method to encrypt files, folders, or entire hard drives depending on need. However, certain BIOS settings and configurations are necessary to implement encryption on an entire hard disk. -
Question 44 of 159
44. Question
1 pointsWhat is an accurate description of asymmetric encryption technology?Correct
Incorrect
-
Question 45 of 159
45. Question
1 pointsWhich type of security threat can be transferred through email and is used to gain sensitive information by recording the keystrokes of the email recipient?Correct
Incorrect
Hint
Adware does not record keystrokes. A worm self-replicates across the network. A Trojan appears to be a legitimate program while carrying malware, and grayware is a general term for software that may be malware. -
Question 46 of 159
46. Question
1 pointsA manager reports that unusual things are happening on a Windows computer. The technician determines that malware is the culprit. What can the technician do to remove stubborn malware?Correct
Incorrect
Hint
Booting the computer in Safe Mode prevents most drivers from loading. Additional antimalware software can then be installed to remove or quarantine malware. Sometimes the storage drive must be wiped, the operating system reinstalled, and data restored from a backup. -
Question 47 of 159
47. Question
1 pointsAn employee that has worked at the company for many years has started a home-based business selling crafts. While leaving an office meeting, a company supervisor notices the employee buying supplies for the personal crafting business of the employee. What section of the security policy should the supervisor review when determining how to handle this situation?Correct
Incorrect
Hint
The acceptable use policies section of a security policy commonly identifies network resources and usages that are acceptable to the organization. They might also state the ramifications that can occur if this security policy is violated. -
Question 48 of 159
48. Question
1 pointsWhat Windows utility should be used to configure password rules and account lockout policies on a system that is not part of a domain?Correct
Incorrect
Hint
A technician must be aware of the technologies and measures that are used as countermeasures to protect the organization from threats and vulnerabilities. A Windows Domain Security Policy is used and applied when a user logs in to a computer that is on a corporate network. A Windows Local Security Policy is used for stand-alone computers to enforce security settings. -
Question 49 of 159
49. Question
1 pointsA customer brings in a computer that is asking for a password as soon as it powers on, even before the operating system boots. Which type of password is enabled?Correct
Incorrect
Hint
A BIOS password is configured by entering the BIOS Setup program. If unknown, it can be removed by placing a jumper over two motherboard pins. Some motherboards support BIOS password removal by removing the CMOS battery, but if this is done, all BIOS settings will be reset to the default values. -
Question 50 of 159
50. Question
1 pointsWhen attempting to improve system performance for Linux computers with a limited amount of memory, why is increasing the size of the swap file system not considered the best solution?Correct
Incorrect
Hint
The swap file system is used by Linux when it runs out of physical memory. When needed, the kernel moves inactive RAM content to the swap partition on the hard disk. Storing and retrieving content in the swap partition is much slower than RAM is, and therefore using the swap partition should not be considered the best solution to improving system performance. -
Question 51 of 159
51. Question
1 pointsWhat are three features of GPS on mobile devices? (Choose three.)Correct
Incorrect
Hint
Navigation, specialized search results, and device tracking are features of GPS on mobile devices. Remote wipe may be a feature on some mobile devices, but is not related to GPS. Phone number lookup and gas mileage calculations are not GPS features. -
Question 52 of 159
52. Question
1 pointsWhich three components are used to assign file and directory permissions in Linux systems? (Choose three.)Correct
Incorrect
Hint
In Linux, file and directory permissions are assigned as follows:- Owner – the owner user of the file or directory
- Group – the user group that has been assigned to the file or directory
- All users – all other users on the system
-
Question 53 of 159
53. Question
1 pointsA user downloads a widget onto his Android phone but is puzzled to see that when the widget is touched an app is launched. What is a possible cause?Correct
Incorrect
Hint
Widgets are programs that when installed associate with the application they were built for. This will cause the application to launch when the widget icon is touched on the touchscreen of the Android device. -
Question 54 of 159
54. Question
1 pointsWhat is the purpose of running mobile device apps in a sandbox?Correct
Incorrect
Hint
Mobile device apps are run in a sandbox that isolates them from other resources. Bypassing the phone carrier from preventing access to unauthorized apps is jailbreaking or rooting the device. -
Question 55 of 159
55. Question
1 pointsWhich built-in tool is available on a Mac OS X machine to perform disk backups?Correct
Incorrect
Hint
Time Machine is an automatic backup utility in the Mac OS. The Mac Disk Utility allows an administrator to configure disk backups. The Deja Dup tool is a tool built into the Linux OS for backing up data. Finder is similar to the Windows File Explorer tool and is used to navigate the Mac OS file system. -
Question 56 of 159
56. Question
1 pointsA user calls the help desk reporting that a laptop with Linux freezes on startup and displays kernel panic. What could cause this problem?Correct
Incorrect
Hint
A corrupted driver or failing hardware could cause kernel panic for Linux or Mac OS. The laptop will not be able to boot successfully. Either GRUB or LILO corruption or GRUB or LILO deletion would cause the stop screen to display a “Missing GRUB” or “Missing LILO” message. A resource unavailable to an application will cause the application to stop responding, but not prevent a laptop from starting up. -
Question 57 of 159
57. Question
1 pointsA user calls the help desk to report that a mobile device exhibits very slow performance. What could cause this problem?Correct
Incorrect
Hint
A power-intensive app that is running in the background could consume most of the CPU cycles and thus the device would exhibit very slow performance for other apps. If an app is not compatible with the device, the device operating system would freeze. If the operating system has encountered an error, the device will fail to respond. -
Question 58 of 159
58. Question
1 pointsWhich term describes a partition that is used to store and boot an operating system by default?Correct
Incorrect
-
Question 59 of 159
59. Question
1 pointsWhich term describes a file system that supports a partition size up to 16 exabytes?Correct
Incorrect
-
Question 60 of 159
60. Question
1 pointsWhich term describes a file system for USB flash drives that supports files larger than 4 GB?Correct
Incorrect
-
Question 61 of 159
61. Question
1 pointsWhich term describes a partition that supports up to 23 logical drives?Correct
Incorrect
-
Question 62 of 159
62. Question
1 pointsWhich term describes a file system for optical disk media?Correct
Incorrect
-
Question 63 of 159
63. Question
1 pointsWhich term describes a type of partition that would only exist on a hard disk that has an MBR?Correct
Incorrect
-
Question 64 of 159
64. Question
1 pointsWhich term describes a type of storage device that supports a partition to be extended into adjacent unallocated space as long as it is contiguous?Correct
Incorrect
-
Question 65 of 159
65. Question
1 pointsWhich term describes a general name for physical areas on a hard drive?Correct
Incorrect
-
Question 66 of 159
66. Question
1 pointsWhich term describes a partition scheme that takes a portion of disk space of 512 bytes long and that contains the boot loader?Correct
Incorrect
-
Question 67 of 159
67. Question
1 pointsWhich term describes a type of storage device that supports a volume that can span across more than one disk?Correct
Incorrect
-
Question 68 of 159
68. Question
1 pointsA technician is booting a laptop that has Windows 10 installed with 2 GB RAM. The boot process is currently working on the following step: NTOSKRNL.EXE starts the login file called WINLOGON.EXE. What is the next step that will happen in the boot process?Correct
Incorrect
-
Question 69 of 159
69. Question
1 pointsA user is booting a tablet that has Windows 10 installed. The boot process is currently working on the following step: WINLOGON.EXE displays the Windows Welcome screen What is the next step that will happen in the boot process?Correct
Incorrect
-
Question 70 of 159
70. Question
1 pointsA manager is booting a tablet that has Windows 8 installed. The boot process is currently working on the following step: POST. What is the next step that will happen in the boot process?Correct
Incorrect
-
Question 71 of 159
71. Question
1 pointsAn accountant is booting a PC that has Windows 8 installed. The boot process is currently working on the following step: BIOS locates and reads the configuration settings that are stored in the CMOS memory. What is the next step that will happen in the boot process?Correct
Incorrect
-
Question 72 of 159
72. Question
1 pointsA network analyst is booting a PC that has Windows 7 installed with 2 GB RAM. The boot process is currently working on the following step: The code in the boot sector is executed and the control of the boot process is given to Windows Boot Manager. What is the next step that will happen in the boot process?Correct
Incorrect
-
Question 73 of 159
73. Question
1 pointsAn analyst is booting a desktop that has Windows 7 installed with 4 GB RAM. The boot process is currently working on the following step: Winload uses the path specified in BOOTMGR to find the boot partition. What is the next step that will happen in the boot process?Correct
Incorrect
-
Question 74 of 159
74. Question
1 pointsA gamer is booting a desktop that has Windows 7 installed on dynamic drives. The boot process is currently working on the following step: WinLoad reads the registry files, chooses a hardware profile, and loads the device drivers. What is the next step that will happen in the boot process?Correct
Incorrect
-
Question 75 of 159
75. Question
1 pointsA technician is booting a laptop that has Windows 10 installed with 2 GB RAM. The boot process is currently working on the following step: The Windows kernel takes over the boot process. What is the next step that will happen in the boot process?Correct
Incorrect
-
Question 76 of 159
76. Question
1 pointsA user is booting a laptop that has Windows 10 installed. The boot process is currently working on the following step: WINLOGON.EXE displays the Windows Welcome screen What is the next step that will happen in the boot process?Correct
Incorrect
-
Question 77 of 159
77. Question
1 pointsA manager is booting a tablet that has Windows 8 installed. The boot process is currently working on the following step: The Windows kernel takes over the boot process. What is the next step that will happen in the boot process?Correct
Incorrect
-
Question 78 of 159
78. Question
1 pointsUsers in a company have complained about network performance. After investigation, the IT staff has determined that the attacker was using a specific technique that affected the TCP three-way handshake. What is the type of network attack?Correct
Incorrect
-
Question 79 of 159
79. Question
1 pointsUsers in a company have complained about network performance. After investigation, the IT staff has determined that the attacker is using a technique that compares hashed passwords to potential hashes the hacker has. What is the type of network attack?Correct
Incorrect
-
Question 80 of 159
80. Question
1 pointsUsers in a company have complained about network performance. After investigation, the IT staff has determined that the DNS server was sent with an enormous amount of false requests, thus overwhelming the server. What is the type of network attack?Correct
Incorrect
-
Question 81 of 159
81. Question
1 pointsUsers in a company have complained about network performance. After investigation, the IT staff has determined that the attacker is using a vulnerability that is known to the software vendor, but not patched yet. What is the type of network attack?Correct
Incorrect
-
Question 82 of 159
82. Question
1 pointsUsers in a company have complained about network performance. After investigation, the IT staff has determined that zombies were used to attack the firewall. What is the type of network attack?Correct
Incorrect
-
Question 83 of 159
83. Question
1 pointsUsers in a company have complained about network performance. After investigation, the IT staff has determined that zombies were used to attack the firewall. What is the type of network attack?Correct
Incorrect
-
Question 84 of 159
84. Question
1 pointsUsers in a company have complained about network performance. After investigation, the IT staff has determined that the attacker is using a table of words that potentially could be used as passwords. What is the type of network attack?Correct
Incorrect
-
Question 85 of 159
85. Question
1 pointsUsers in a company have complained about network performance. After investigation, the IT staff has determined that the attacker injected false records on the server that translates IP addresses to domain names. What is the type of network attack?Correct
Incorrect
-
Question 86 of 159
86. Question
1 pointsUsers in a company have complained about network performance. After investigation, the IT staff has determined that the attacker is using a technique that compares hashed passwords to potential hashes the hacker has. What is the type of network attack?Correct
Incorrect
-
Question 87 of 159
87. Question
1 pointsUsers in a company have complained about network performance. After investigation, the IT staff has determined that the attacker was using a specific technique that affected the TCP three-way handshake. What is the type of network attack?Correct
Incorrect
-
Question 88 of 159
88. Question
1 pointsA PC technician has been asked by a supervisor to recommend a security solution for a company that wants a device to monitor incoming and outgoing traffic and stop any malicious activity. Which security technique should the technician recommend?Correct
Incorrect
-
Question 89 of 159
89. Question
1 pointsA PC technician has been asked by a supervisor to recommend a security solution for a machine where the antimalware software cannot remove all of the malware. Which security technique should the technician recommend?Correct
Incorrect
-
Question 90 of 159
90. Question
1 pointsA PC technician has been asked by a supervisor to recommend a security solution for a machine where the antimalware software cannot remove all of the malware. Which security technique should the technician recommend?Correct
Incorrect
-
Question 91 of 159
91. Question
1 pointsA PC technician has been asked by a supervisor to recommend a security solution for preventing tailgating. Which security technique should the technician recommend?Correct
Incorrect
-
Question 92 of 159
92. Question
1 pointsA PC technician has been asked by a supervisor to recommend a security solution for drive redundancy. Which security technique should the technician recommend?Correct
Incorrect
-
Question 93 of 159
93. Question
1 pointsA PC technician has been asked by a supervisor to recommend a security solution for drive redundancy. Which security technique should the technician recommend?Correct
Incorrect
-
Question 94 of 159
94. Question
1 pointsA PC technician has been asked by a supervisor to recommend a security solution for phishing. Which security technique should the technician recommend?Correct
Incorrect
-
Question 95 of 159
95. Question
1 pointsA PC technician has been asked by a supervisor to recommend a security solution for protecting a computer used to log in at a dental clinic from someone using a bootable disk containing hacking tools. Which security technique should the technician recommend?Correct
Incorrect
-
Question 96 of 159
96. Question
1 pointsA PC technician has been asked by a supervisor to recommend a security solution for protecting a computer used to log in at a dental clinic from someone using a bootable disk containing hacking tools. Which security technique should the technician recommend?Correct
Incorrect
-
Question 97 of 159
97. Question
1 pointsA PC technician has been asked by a supervisor to recommend a security solution for a manager traveling who needs access to internal corporate resources. Which security technique should the technician recommend?Correct
Incorrect
-
Question 98 of 159
98. Question
1 pointsWhy would a gamer need to use the move command?Correct
Incorrect
-
Question 99 of 159
99. Question
1 pointsWhy would a gamer need to use the copy command?Correct
Incorrect
-
Question 100 of 159
100. Question
1 pointsWhy would a university student need to use the robocopy command?Correct
Incorrect
-
Question 101 of 159
101. Question
1 pointsWhy would a university student need to use the xcopy command?Correct
Incorrect
-
Question 102 of 159
102. Question
1 pointsWhy would a technical support representative need to use the format command?Correct
Incorrect
-
Question 103 of 159
103. Question
1 pointsWhy would a technical support representative need to use the bootrec command?Correct
Incorrect
-
Question 104 of 159
104. Question
1 pointsWhy would a technical support representative need to use the ipconfig command?Correct
Incorrect
-
Question 105 of 159
105. Question
1 pointsWhy would a user need to use the netstat command?Correct
Incorrect
-
Question 106 of 159
106. Question
1 pointsWhy would a user need to use the nslookup command?Correct
Incorrect
-
Question 107 of 159
107. Question
1 pointsWhy would a manager need to use the ping command?Correct
Incorrect
-
Question 108 of 159
108. Question
1 pointsWhat are two probable causes of a user unable to access local resources such as file shares or printers on a wired network? (Choose two.)Correct
Incorrect
Hint
There are many issues which can cause local resources to be unavailable. These include bad cabling, a switch or router not functioning, a firewall blocking traffic, DNS name resolution not working, or failed services. -
Question 109 of 159
109. Question
1 pointsThe IT department has just purchased 15 wireless access points in order to provide full wireless coverage for all 100 employees within the company and is looking to deploy the most secure and scalable wireless implementation. Which open source authentication method would perform authentication on behalf of all 15 wireless network devices?Correct
Incorrect
Hint
RADIUS and TACACS+ both use a separate server that performs authentication on behalf of network devices. However, RADIUS is an open standard and provides greater compatibility. -
Question 110 of 159
110. Question
1 pointsA technician is upgrading many PCs used within the company. How should the technician dispose of an old inkjet printer cartridge?Correct
Incorrect
-
Question 111 of 159
111. Question
1 pointsA client packet is received by a server. The packet has a destination port number of 3389. What service application is the client requesting?Correct
Incorrect
-
Question 112 of 159
112. Question
1 pointsA client packet is received by a server. The packet has a destination port number of 67. What service application is the client requesting?Correct
Incorrect
-
Question 113 of 159
113. Question
1 pointsA client packet is received by a server. The packet has a destination port number of 443. What service application is the client requesting?Correct
Incorrect
-
Question 114 of 159
114. Question
1 pointsA client packet is received by a server. The packet has a destination port number of 69. What service application is the client requesting?Correct
Incorrect
-
Question 115 of 159
115. Question
1 pointsA client packet is received by a server. The packet has a destination port number of 445. What service application is the client requesting?Correct
Incorrect
-
Question 116 of 159
116. Question
1 pointsA client packet is received by a server. The packet has a destination port number of 548. What service application is the client requesting?Correct
Incorrect
-
Question 117 of 159
117. Question
1 pointsA client packet is received by a server. The packet has a destination port number of 80. What service application is the client requesting?Correct
Incorrect
-
Question 118 of 159
118. Question
1 pointsA client packet is received by a server. The packet has a destination port number of 3389. What service application is the client requesting?Correct
Incorrect
-
Question 119 of 159
119. Question
1 pointsA PC technician has been asked by a supervisor to recommend a security solution for a small company that wants stateful firewall services. Which security technique should the technician recommend?Correct
Incorrect
-
Question 120 of 159
120. Question
1 pointsA gamer is booting a desktop that has Windows 10 installed on dynamic drives. The boot process is currently working on the following step: WinLoad reads the registry files, chooses a hardware profile, and loads the device drivers. What is the next step that will happen in the boot process?Correct
Incorrect
-
Question 121 of 159
121. Question
1 pointsA technician is working on a laptop and an error message about decryption appears when opening an email. What is a possible solution for this situation?Correct
Incorrect
-
Question 122 of 159
122. Question
1 pointsA technician is working on a laptop and an error message about decryption appears when opening an email. What is a possible solution for this situation?Correct
Incorrect
-
Question 123 of 159
123. Question
1 pointsA technician is working on a laptop and an error message about decryption appears when opening an email. What is a possible solution for this situation?Correct
Incorrect
-
Question 124 of 159
124. Question
1 pointsA technician is working on a laptop and a key on the keyboard is not responding as it should. What is a possible solution for this situation?Correct
Incorrect
-
Question 125 of 159
125. Question
1 pointsA technician is working on a laptop and a key on the keyboard is not responding as it should. What is a possible solution for this situation?Correct
Incorrect
-
Question 126 of 159
126. Question
1 pointsA technician is working on a laptop and GPS is not functioning. What is a possible solution for this situation?Correct
Incorrect
-
Question 127 of 159
127. Question
1 pointsA technician is working on a laptop and GPS is not functioning. What is a possible solution for this situation?Correct
Incorrect
-
Question 128 of 159
128. Question
1 pointsA technician is working on a laptop and GPS is not functioning. What is a possible solution for this situation?Correct
Incorrect
-
Question 129 of 159
129. Question
1 pointsA technician is working on a laptop and GPS is not functioning. What is a possible solution for this situation?Correct
Incorrect
-
Question 130 of 159
130. Question
1 pointsA technician is working on a laptop and GPS is not functioning. What is a possible solution for this situation?Correct
Incorrect
-
Question 131 of 159
131. Question
1 pointsWhy would a manager need to use the tracert command?Correct
Incorrect
-
Question 132 of 159
132. Question
1 pointsWhy would a manager need to use the sfc command?Correct
Incorrect
-
Question 133 of 159
133. Question
1 pointsWhy would a technician need to use the DISM command?Correct
Incorrect
-
Question 134 of 159
134. Question
1 pointsWhy would a technician need to use the tasklist command?Correct
Incorrect
-
Question 135 of 159
135. Question
1 pointsWhy would an analyst need to use the taskkill command?Correct
Incorrect
-
Question 136 of 159
136. Question
1 pointsWhy would an analyst need to use the msconfig command?Correct
Incorrect
-
Question 137 of 159
137. Question
1 pointsWhy would an analyst need to use the dir command?Correct
Incorrect
-
Question 138 of 159
138. Question
1 pointsWhy would a bank manager need to use the gpupdate command?Correct
Incorrect
-
Question 139 of 159
139. Question
1 pointsWhy would a bank manager need to use the gpresult command?Correct
Incorrect
-
Question 140 of 159
140. Question
1 pointsWhy would a lawyer need to use the cd command?Correct
Incorrect
-
Question 141 of 159
141. Question
1 pointsThe IT department has just purchased 15 wireless access points in order to provide full wireless coverage for all 100 employees within the company and is looking to deploy the most secure and scalable wireless implementation. Which open source authentication method would perform authentication on behalf of all 15 wireless network devices?Correct
Incorrect
Hint
RADIUS and TACACS+ both use a separate server that performs authentication on behalf of network devices. However, RADIUS is an open standard and provides greater compatibility. -
Question 142 of 159
142. Question
1 pointsRefer to the exhibit. What is true of this mobile device screen? Correct
Correct
Incorrect
Hint
The Windows Phone interface uses tiles to represent apps. Tiles are rectangular areas of a screen that identify the app and may also contain active content such as text messages, news feeds, and photos. -
Question 143 of 159
143. Question
1 pointsAn accountant is booting a PC that has Windows 10 installed. The boot process is currently working on the following step: BIOS locates and reads the configuration settings that are stored in the CMOS memory. What is the next step that will happen in the boot process?Correct
Incorrect
-
Question 144 of 159
144. Question
1 pointsAn analyst is booting a desktop that has Windows 10 installed with 4 GB RAM. The boot process is currently working on the following step: Winload uses the path specified in BOOTMGR to find the boot partition. What is the next step that will happen in the boot process?Correct
Incorrect
-
Question 145 of 159
145. Question
1 pointsWhat is a possible situation when it might be necessary to boot Windows 10 from a bootable recovery USB device?Correct
Incorrect
-
Question 146 of 159
146. Question
1 pointsWhich statement is true regarding mobile devices using the Wireless Wide Area Network (WWAN)?Correct
Incorrect
-
Question 147 of 159
147. Question
1 pointsA Windows 10 computer locks up with a stop error during startup and then automatically reboots. The automatic restart setting is making it difficult to see any error messages. What can be done so that the error messages can be viewed?Correct
Incorrect
-
Question 148 of 159
148. Question
1 pointsWhich statement is true regarding libraries in Windows 10?Correct
Incorrect
-
Question 149 of 159
149. Question
1 pointsA corporation would like to use three or more factors for the password authentication policy. How can this be achieved?Correct
Incorrect
-
Question 150 of 159
150. Question
1 pointsA system administrator has been asked to protect the sensitive data on Windows 10 computers of all management employees. Which Windows 10 feature can be used to selectively encrypt individual files within the user accounts of each manager?Correct
Incorrect
-
Question 151 of 159
151. Question
1 pointsWhich two statements are true regarding 64-bit processor architecture? (Choose two.)Correct
Incorrect
-
Question 152 of 159
152. Question
1 pointsA manager is booting a tablet that has Windows 10 installed. The boot process is currently working on the following step: POST. What is the next step that will happen in the boot process?Correct
Incorrect
-
Question 153 of 159
153. Question
1 pointsA computer technician uses Windows tools to gather information such as system components, operating system, users, and disk drives on multiple systems within the company. Another technician suggests that the tasks would take less time if they were automated. Which two built-in scripting capabilities in Windows enable a technician to run a simple text file, created in Notepad, which contains the necessary commands and variables? (Choose two.)Correct
Incorrect
-
Question 154 of 159
154. Question
1 pointsWhy would a lawyer need to use the tracert command?Correct
Incorrect
-
Question 155 of 159
155. Question
1 pointsMatch the file system with the respective description.Correct
Incorrect
-
Question 156 of 159
156. Question
1 pointsMatch the steps that will lead to the loading of bootmgr.exe in a 32 bit Windows 10 environment.Correct
Incorrect
-
Question 157 of 159
157. Question
1 pointsA technician wishes to start Windows 10 in safe mode to troubleshoot it. What key or key combination would begin this process?Correct
Incorrect
-
Question 158 of 159
158. Question
1 pointsSelect the Windows 10 version that best meets the described use.Correct
Incorrect
-
Question 159 of 159
159. Question
1 pointsA user notes that the username and password are automatically populated in the Microsoft Edge browser when logging into a secure site. When the user tries to log into the same site using Google Chrome, the username and password do not save automatically. Why is this occurring?Correct
Incorrect
