1. How does BYOD change the way in which businesses implement networks?
- BYOD devices are more expensive than devices that are purchased by an organization.
- BYOD provides flexibility in where and how users can access network resources.
- BYOD requires organizations to purchase laptops rather than desktops.
- BYOD users are responsible for their own network security, thus reducing the need for organizational security policies.
Explanation: A BYOD environment requires an organization to accommodate a variety of devices and access methods. Personal devices, which are not under company control, may be involved, so security is critical. Onsite hardware costs will be reduced, allowing a business to focus on delivering collaboration tools and other software to BYOD users.
2. Which device is usually the first line of defense in a layered defense-in-depth approach?
- internal router
- firewall
- access layer switch
- edge router
Explanation: The edge router connects an organization to a service provider. The edge router has a set of rules that specify which traffic is allowed or denied.
3. With the evolution of borderless networks, which vegetable is now used to describe a defense-in-depth approach?
- cabbage
- lettuce
- artichoke
- onion
Explanation: The artichoke is now used to provide a visual analogy to describe a defense-in-depth security approach. The onion used to be descriptive because the attacker would “peel away” each layer of the network defense mechanisms. Now the artichoke is used because a single petal or leaf can be moved or removed to reveal sensitive information.
4. Which type of business policy establishes the rules of conduct and the responsibilities of employees and employers?
- data
- security
- employee
- company
Explanation: Business policies set a baseline of acceptable use. Company policies establish the rules and conduct and the responsibilities of both employees and the employer. Company policies protect the rights of the workers as well as the business interests of the company.
5. An administrator is concerned with restricting which network applications and uses are acceptable to the organization. What security policy component does the administrator use to address these concerns?
- network maintenance policy
- remote access policy
- incident handling procedures policy
- acceptable use policy
Explanation: The acceptable use policy (AUP) identifies which network applications and uses are acceptable to an organization.
6. What component of a security policy explicitly defines the type of traffic allowed on a network and what users are allowed and not allowed to do?
- acceptable use policies
- remote access policies
- password policies
- identification and authentication policies
Explanation: Security policies specify requirements and provide a baseline for organizations. Security policies may include the following:
- Identification and authentication policies that specify authorized individuals that have access to network resources and verification procedures
- Password policies that ensure minimum requirements are met and authentication methods are being enforced and updated
- Remote access policies that identify how remote users can access a network and to what they are allowed to connect
- Acceptable use policies that identify network applications and network usage that are allowed within the organization
7. What device would be used as the third line of defense in a defense-in-depth approach?
- host
- firewall
- edge router
- internal router
Explanation: In a defense-in-depth approach, the edge router would form the first line of defense. The firewall would be the second line of defense followed by the internal router making up the third line of defense.
8. Refer to the exhibit. The security policy of an organization allows employees to connect to the office intranet from their homes. Which type of security policy is this?
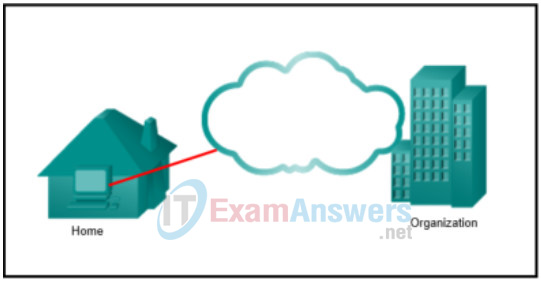
- incident handling
- remote access
- network maintenance
- acceptable use
Explanation: The remote access policy section of a corporate security policy identifies how remote users can access a network and what is accessible via remote connectivity.
9. What is a characteristic of a layered defense-in-depth security approach?
- The layers define a set of security objectives for a company and define the rules of behavior for users and administrators.
- The failure of one safeguard does not affect the effectiveness of the other safeguards.
- The different layers work in isolation to create a security architecture.
- The layers set a baseline of acceptable use of the network.
Explanation: In the layered defense-in-depth security approach, the different layers work together to create a security architecture in which the failure of one safeguard does not affect the effectiveness of the other safeguards.
10. Which is a BYOD security best practice?
- have all users install an antivirus program of their choice on the BYOD device
- subscribe to a device locator service with remote wipe feature
- disable use of MDM software on any of the BYOD devices
- use one global complex password for all BYOD devices
Explanation: One of the best practices for BYOD devices is subscribing to a device locator service with remote wipe feature in the event the device is lost or stolen.
11. What do security compliance regulations define?
- which websites users cannot access
- which defense-in-depth mechanisms to adopt
- what organizations are responsible for providing and the liability for failure to comply
- which security appliances can be used
Explanation: Compliance regulations define what organizations are responsible for providing and the liability failure to comply. The compliance regulations that an organization is obligated to follow will differ from one organization to the next because the regulations depend on the type of organization and the data that the organization handles.
12. What device would be used as a second line of defense in a defense-in-depth approach?
- edge router
- internal router
- switch
- firewall
Explanation: In a defense-in-depth approach, the edge router would form the first line of defense. The firewall would be the second line of defense followed by the internal router making up the third line of defense.
13. Which two areas must an IT security person understand in order to identify vulnerabilities on a network? (Choose two.)
- hardware used by applications
- data analysis trends
- number of systems on each network
- network baseline data
- important applications used
Explanation: In order to identify security vulnerabilities, a cybersecurity expert must understand the applications being used and their associated vulnerabilities, as well as the hardware used.

