Time limit: 0
Quiz-summary
0 of 40 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
Information
CCNA Cyber Ops (Version 1.1) – Chapter 12 Test Online Full
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 40 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- Answered
- Review
-
Question 1 of 40
1. Question
1 pointsHow is the hash value of files useful in network security investigations?Correct
Incorrect
-
Question 2 of 40
2. Question
1 pointsWhich tool is a Security Onion integrated host-based intrusion detection system?Correct
Incorrect
-
Question 3 of 40
3. Question
1 pointsWhich type of evidence supports an assertion based on previously obtained evidence?Correct
Incorrect
-
Question 4 of 40
4. Question
1 pointsWhich tool is developed by Cisco and provides an interactive dashboard that allows investigation of the threat landscape?Correct
Incorrect
-
Question 5 of 40
5. Question
1 pointsWhich term is used to describe the process of converting log entries into a common format?Correct
Incorrect
-
Question 6 of 40
6. Question
1 pointsAccording to NIST, which step in the digital forensics process involves extracting relevant information from data?Correct
Incorrect
-
Question 7 of 40
7. Question
1 pointsA law office uses a Linux host as the firewall device for the network. The IT administrator is adding a rule to the firewall iptables to block internal hosts from connecting to a remote device that has the IP address 209.165.202.133. Which command should the administrator use?Correct
Incorrect
-
Question 8 of 40
8. Question
1 pointsWhat procedure should be avoided in a digital forensics investigation?Correct
Incorrect
-
Question 9 of 40
9. Question
1 pointsWhich statement describes a feature of timestamps in Linux?Correct
Incorrect
-
Question 10 of 40
10. Question
1 pointsWhich tool is included with Security Onion that is used by Snort to automatically download new rules?Correct
Incorrect
-
Question 11 of 40
11. Question
1 pointsWhich tool would an analyst use to start a workflow investigation?Correct
Incorrect
-
Question 12 of 40
12. Question
1 pointsWhat is indicated by a Snort signature ID that is below 3464?Correct
Incorrect
-
Question 13 of 40
13. Question
1 pointsHow does an application program interact with the operating system?Correct
Incorrect
-
Question 14 of 40
14. Question
1 pointsA threat actor has successfully breached the network firewall without being detected by the IDS system. What condition describes the lack of alert?Correct
Incorrect
-
Question 15 of 40
15. Question
1 pointsUse the following scenario to answer the questions. A company has just had a cybersecurity incident. The threat actor or actors appeared to have a goal of network disruption and appeared to use a common security hack tool that overwhelmed a particular server with a large amount of traffic, which rendered the server inoperable. a. How would a certified cybersecurity analyst classify this type of threat actor?Correct
Incorrect
-
Question 16 of 40
16. Question
1 pointsUse the following scenario to answer the questions. A company has just had a cybersecurity incident. The threat actor or actors appeared to have a goal of network disruption and appeared to use a common security hack tool that overwhelmed a particular server with a large amount of traffic, which rendered the server inoperable. The security team at this company has removed the compromised server and preserved it with the security hack still embedded. What type of evidence is this?Correct
Incorrect
-
Question 17 of 40
17. Question
1 pointsUse the following scenario to answer the questions. A company has just had a cybersecurity incident. The threat actor or actors appeared to have a goal of network disruption and appeared to use a common security hack tool that overwhelmed a particular server with a large amount of traffic, which rendered the server inoperable. Which type of attack was achieved?Correct
Incorrect
-
Question 18 of 40
18. Question
1 pointsUse the following scenario to answer the questions. A company has just had a cybersecurity incident. The threat actor or actors appeared to have a goal of network disruption and appeared to use a common security hack tool that overwhelmed a particular server with a large amount of traffic, which rendered the server inoperable. What would be the threat attribution in this case?Correct
Incorrect
-
Question 19 of 40
19. Question
1 pointsUse the following scenario to answer the questions. A company has just had a cybersecurity incident. The threat actor or actors appeared to have a goal of network disruption and appeared to use a common security hack tool that overwhelmed a particular server with a large amount of traffic, which rendered the server inoperable. What are three common tools used to carry out this type of attack? (Choose three.)Correct
Incorrect
-
Question 20 of 40
20. Question
1 pointsRefer to the exhibit. A network security specialist issues the command tcpdump to capture events. What is the function provided by the ampersand symbol used in the command?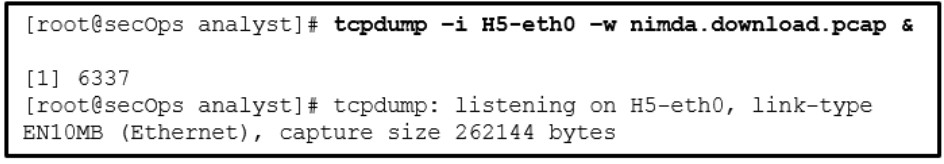 Correct
Correct
Incorrect
-
Question 21 of 40
21. Question
1 pointsRefer to the exhibit. A cybersecurity analyst is using Sguil to verify security alerts. How is the current view sorted?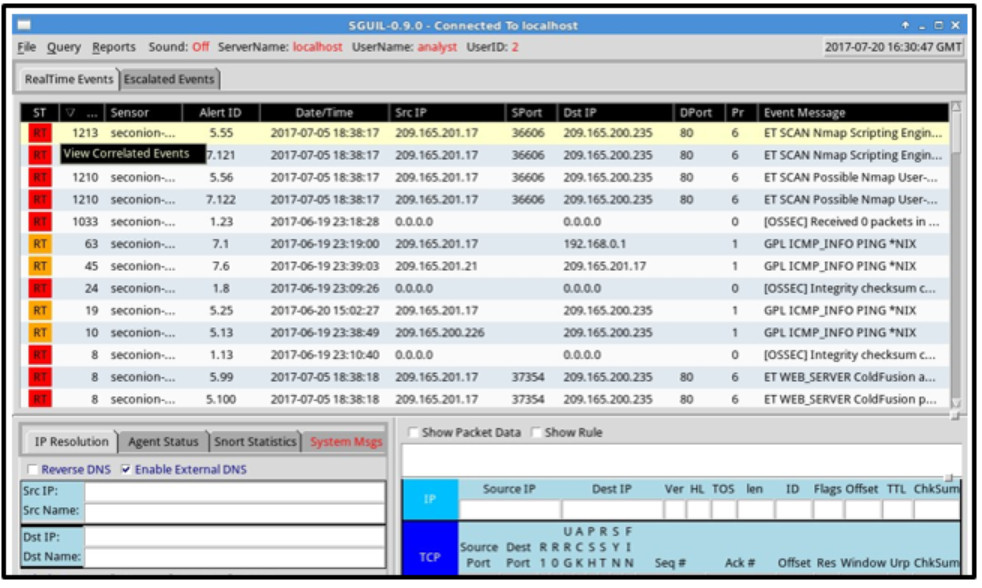 Correct
Correct
Incorrect
-
Question 22 of 40
22. Question
1 pointsWhich three procedures in Sguil are provided to security analysts to address alerts? (Choose three.)Correct
Incorrect
-
Question 23 of 40
23. Question
1 pointsWhich two strings will be matched by the regular expression? (Choose two.) Level[^12]Correct
Incorrect
-
Question 24 of 40
24. Question
1 pointsWhich statement describes the status after the Security Onion VM is started?Correct
Incorrect
-
Question 25 of 40
25. Question
1 pointsWhat are the three core functions provided by the Security Onion? (Choose three.)Correct
Incorrect
-
Question 26 of 40
26. Question
1 pointsRefer to the exhibit. A network security analyst is using the Follow TCP Stream feature in Wireshark to rebuild the TCP transaction. However, the transaction data seems indecipherable. What is the explanation for this?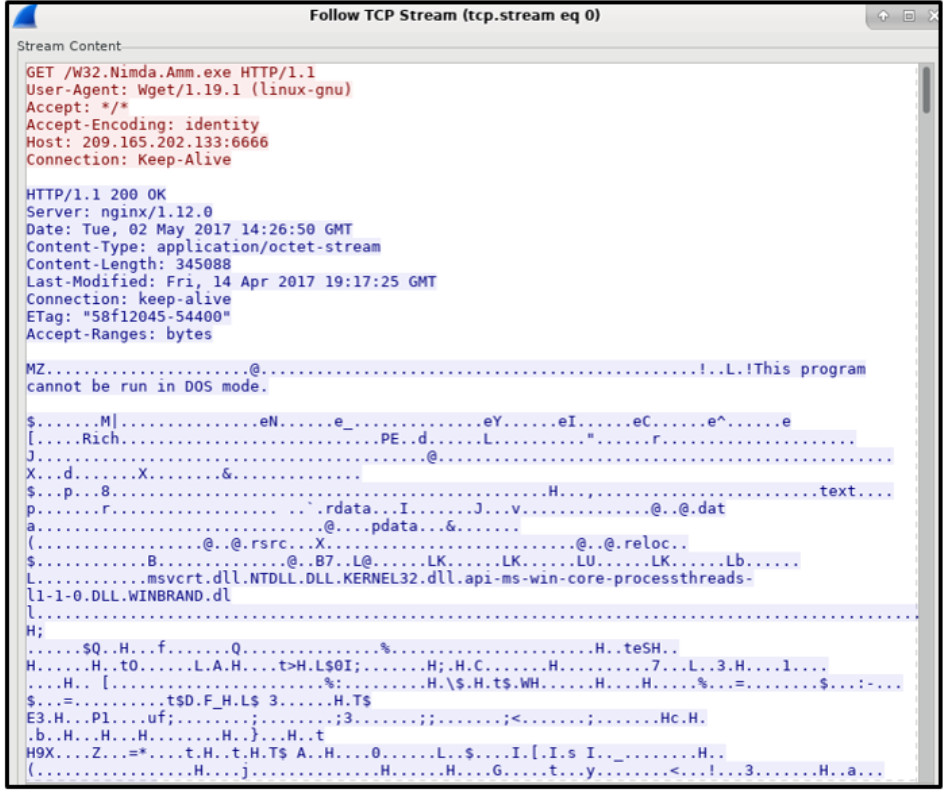 Correct
Correct
Incorrect
-
Question 27 of 40
27. Question
1 pointsWhat is the tool that has alert records linked directly to the search functionality of the Enterprise Log Search and Archive (ELSA)?Correct
Incorrect
-
Question 28 of 40
28. Question
1 pointsRefer to the exhibit. A network security analyst is examining captured data using Wireshark. The captured frames indicate that a host is downloading malware from a server. Which source port is used by the host to request the download?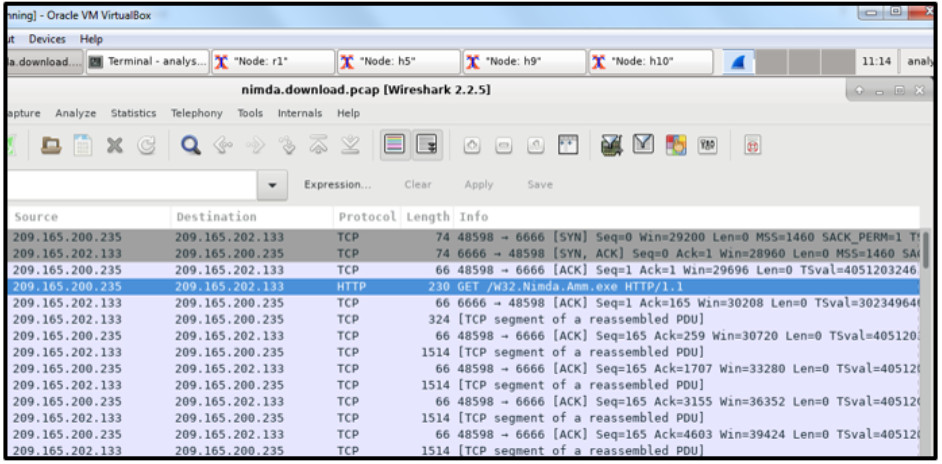 Correct
Correct
Incorrect
-
Question 29 of 40
29. Question
1 pointsWhich two types of unreadable network traffic could be eliminated from data collected by NSM? (Choose two.)Correct
Incorrect
-
Question 30 of 40
30. Question
1 pointsWhich two technologies are used in the ELSA tool? (Choose two.)Correct
Incorrect
-
Question 31 of 40
31. Question
1 pointsWhat is the host-based intrusion detection tool that is integrated into Security Onion?Correct
Incorrect
-
Question 32 of 40
32. Question
1 pointsAccording to NIST, which step in the digital forensics process involves drawing conclusions from data?Correct
Incorrect
-
Question 33 of 40
33. Question
1 pointsWhich two strings will be matched by the regular expression [24]? (Choose two.)Correct
Incorrect
-
Question 34 of 40
34. Question
1 pointsWhich alert classification indicates that exploits are not being detected by installed security systems?Correct
Incorrect
-
Question 35 of 40
35. Question
1 pointsA cybersecurity analyst is going to verify security alerts using the Security Onion. Which tool should the analyst visit first?Correct
Incorrect
-
Question 36 of 40
36. Question
1 pointsWhat is the purpose for data normalization?Correct
Incorrect
-
Question 37 of 40
37. Question
1 pointsWhich term describes evidence that is in its original state?Correct
Incorrect
-
Question 38 of 40
38. Question
1 pointsMatch the characteristic to the method of security analysis.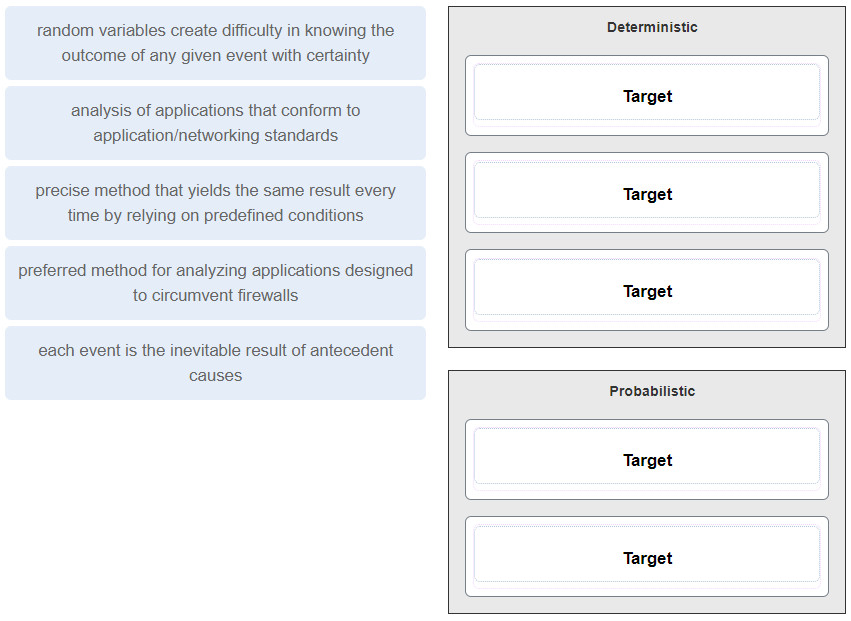 Correct
Correct
Incorrect
-
Question 39 of 40
39. Question
1 pointsMatch the field in the Event table of Sguil to the description.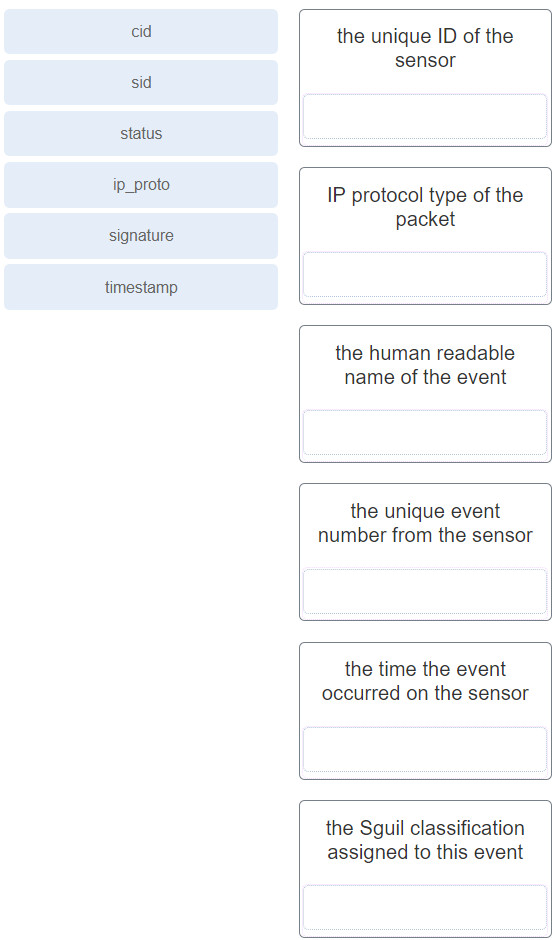 Correct
Correct
Incorrect
-
Question 40 of 40
40. Question
1 pointsPlace the evidence collection priority from most volatile to least volatile as defined by the IETF guidelines.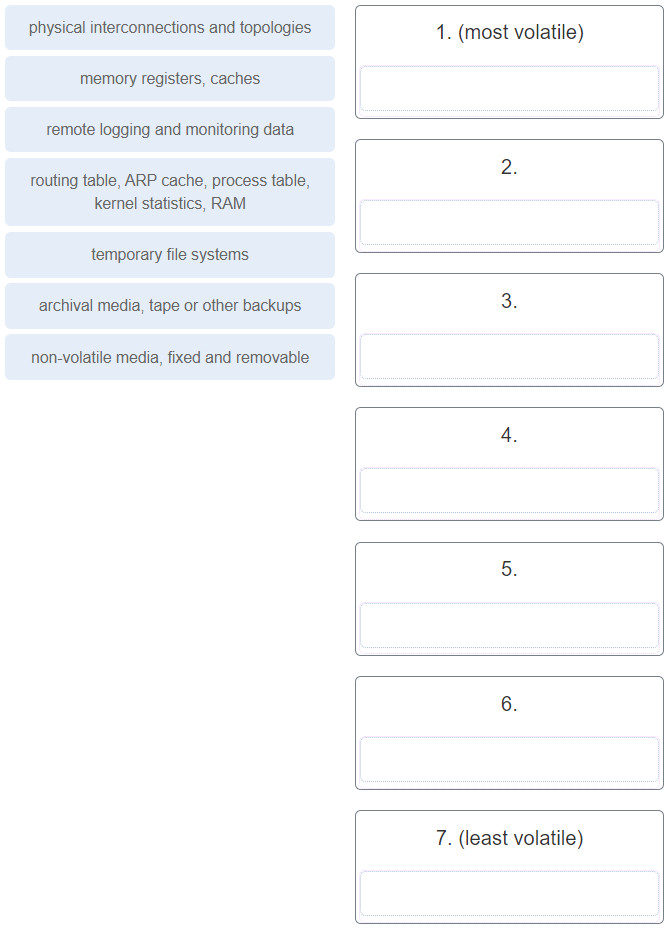 Correct
Correct
Incorrect
