5.0 Introduction
5.0.1 Why Should I Take this Module?
We all communicate on networks daily. Looking at social media, streaming video, or researching information on the internet are common activities that we normally don’t think much about. However, numerous technological processes are at work to bring us the content that we want from the web.
In this module, you will learn how network protocols work together to allow us to request information and to return that information to us over the network.
5.0.2 What Will I Learn in this Module?
Module Title: Network Protocols
Module Objective: Explain how protocols enable network operations.
| Topic Title | Topic Objective |
|---|---|
| Network Communications Process | Explain the basic operation of data networked communications. |
| Communications Protocols | Explain how protocols enable network operations. |
| Data Encapsulation | Explain how data encapsulation allows data to be transported across the network. |
5.1 Network Communications Process
5.1.1 Networks of Many Sizes
Networks come in all sizes. They range from simple networks that consist of two computers, to networks connecting millions of devices.
Simple home networks let you share resources, such as printers, documents, pictures, and music, among a few local end devices.
Small office and home office (SOHO) networks allow people to work from home, or a remote office. Many self-employed workers use these types of networks to advertise and sell products, order supplies, and communicate with customers.
Businesses and large organizations use networks to provide consolidation, storage, and access to information on network servers. Networks provide email, instant messaging, and collaboration among employees. Many organizations use their network’s connection to the internet to provide products and services to customers.
The internet is the largest network in existence. In fact, the term internet means a “network of networks”. It is a collection of interconnected private and public networks.
In small businesses and homes, many computers function as both the servers and clients on the network. This type of network is called a peer-to-peer network.
5.1.2 Client-Server Communications
All computers that are connected to a network and that participate directly in network communication are classified as hosts. Hosts are also called end devices, endpoints, or nodes. Much of the interaction between end devices is client-server traffic. For example, when you access a web page on the internet, your web browser (the client) is accessing a server. When you send an email message, your email client will connect to an email server.
Servers are simply computers with specialized software. This software enables servers to provide information to other end devices on the network. A server can be single-purpose, providing only one service, such as web pages. A server can be multipurpose, providing a variety of services such as web pages, email, and file transfers.
Client computers have software installed, such as web browsers, email clients, and file transfers applications. This software enables them to request and display the information obtained from the server. A single computer can also run multiple types of client software. For example, a user can check email and view a web page while listening to internet radio.
- File Server – The file server stores corporate and user files in a central location.
- Web Server – The web server runs web server software that allows many computers to access web pages.
- Email Server – The email server runs email server software that enables emails to be sent and received.
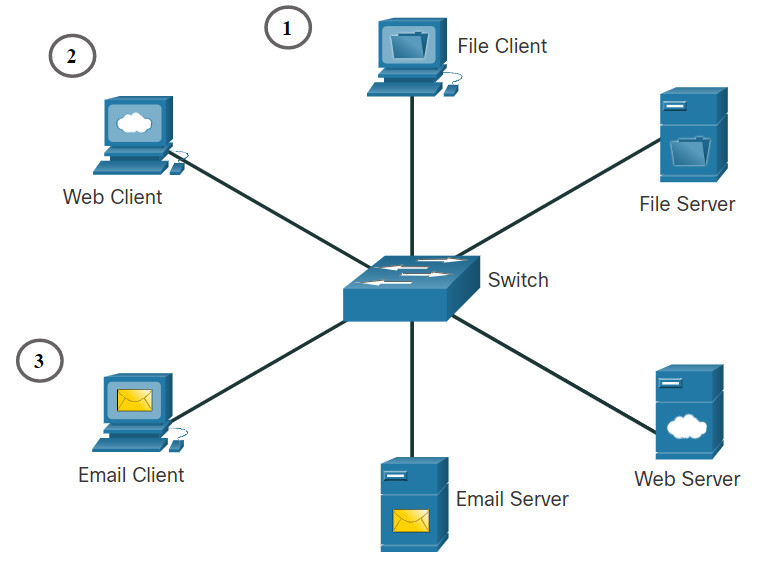
- The File Server stores corporate and user files in a central location. The client devices access these files with client software such as Windows Explorer.
- The Web Server runs web server software and clients use their browser software, such as Windows Microsoft Edge, to access web pages on the server.
- The Email Server runs email server software and clients use their mail client software, such as Microsoft Outlook, to access email on the server.
5.1.3 Typical Sessions
A typical network user at school, at home, or in the office, will normally use some type of computing device to establish many connections with network servers. Those servers could be located in the same room or around the world. Let’s look at a few typical network communication sessions.
5.1.4 Tracing the Path
We tend to think about the data networks we use in our daily lives as we think about driving a car. We do not really care what happens in the engine as long as the car takes us where we want to go. However, just like a car’s mechanic knows the details of how a car operates, cybersecurity analysts need to have a deep understanding of how networks operate.
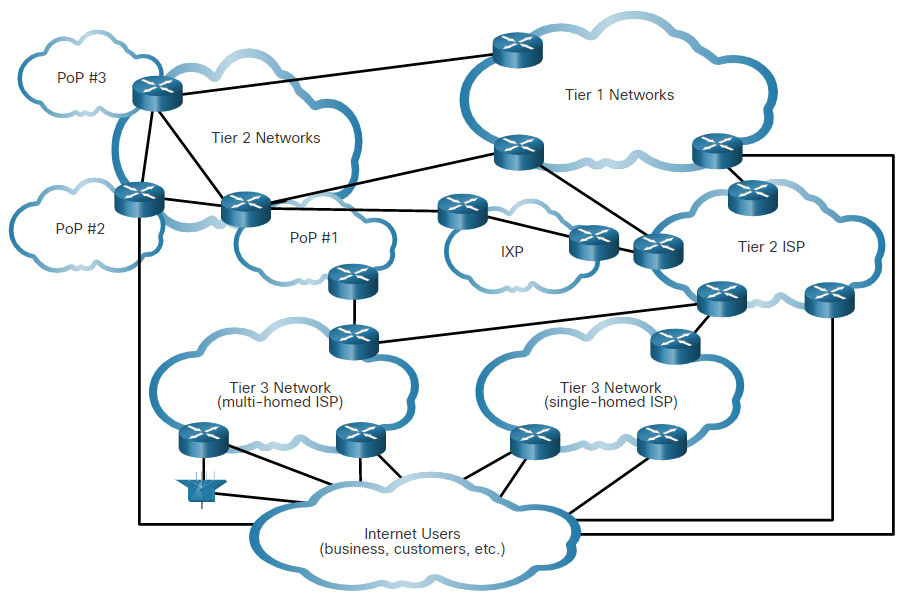
When we connect to a website to read social media or shop, we seldom care about how our data gets to the website and how data from the website gets to us. We are not aware of the many technologies that enable us to use the internet. A combination of copper and fiber-optic cables that go over land and under the ocean carry data traffic. High-speed wireless and satellite technologies are also used. These connections connect telecommunications facilities and internet service providers (ISP) that are distributed throughout the world, as shown in the figure. These global Tier 1 and Tier 2 ISPs connect portions of the internet together, usually through an Internet Exchange Point (IXP). Larger networks will connect to Tier 2 networks through a Point of Presence (PoP), which is usually a location in the building where physical connections to the ISP are made. The Tier 3 ISPs connect homes and businesses to the internet.
Because of different relationships between ISPs and telecommunications companies, traffic from a computer to an internet server can take many paths. The traffic of a user in one country can take a very indirect path to reach its destination. The traffic might first travel from the local ISP to a facility that has connections to many other ISPs. A user’s internet traffic can go many hundreds of miles in one direction only to be routed in a completely different direction to reach its destination. Some of the traffic can take certain routes to reach the destination, and then take completely different routes to return.
Cybersecurity analysts must be able to determine the origin of traffic that enters the network, and the destination of traffic that leaves it. Understanding the path that network traffic takes is essential to this.
5.1.5 Lab – Tracing a Route
In this lab, you will use two route tracing utilities to examine the internet pathway to destination networks. First, you will verify connectivity to a website. Second, you will use the traceroute utility on the Linux command line. Third, you will use a web-based traceroute tool.
5.2 Communications Protocols
5.2.1 What are Protocols?
Simply having a wired or wireless physical connection between end devices is not enough to enable communication. For communication to occur, devices must know “how” to communicate. Communication, whether by face-to-face or over a network, is governed by rules called protocols. These protocols are specific to the type of communication method occurring.
For example, consider two people communicating face-to-face. Prior to communicating, they must agree on how to communicate. If the communication is using voice, they must first agree on the language. Next, when they have a message to share, they must be able to format that message in a way that is understandable. For example, if someone uses the English language, but poor sentence structure, the message can easily be misunderstood.
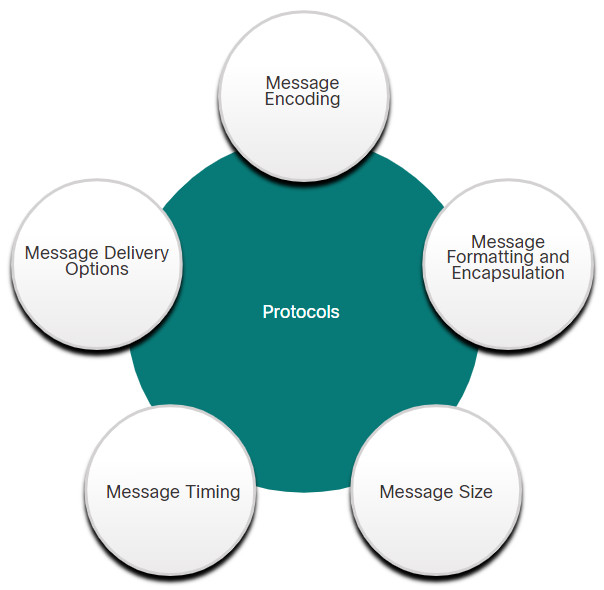
Similarly, network protocols specify many features of network communication, as shown in the figure.
5.2.2 Network Protocols
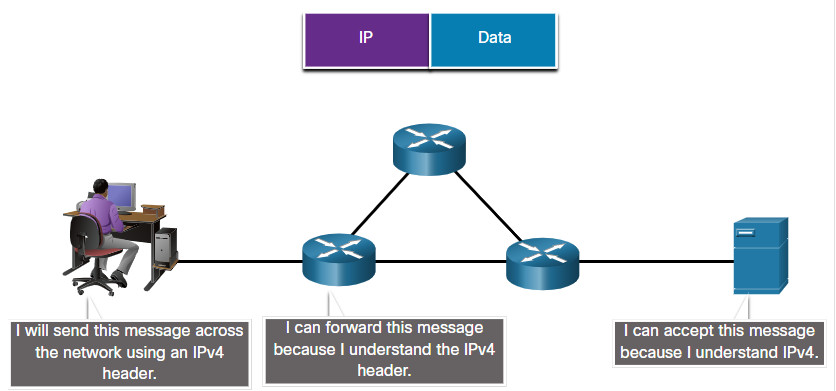
Network protocols provide the means for computers to communicate on networks. Network protocols dictate the message encoding, formatting, encapsulation, size, timing, and delivery options. Networking protocols define a common format and set of rules for exchanging messages between devices. Some common networking protocols are Hypertext Transfer Protocol (HTTP), Transmission Control Protocol (TCP), and Internet Protocol (IP). As a cybersecurity analyst, you must be very familiar with the structure of protocol data and how the protocols function in network communications.
Note: IP in this course refers to both the IPv4 and IPv6 protocols. IPv6 is the most recent version of IP and will eventually replace the more common IPv4.
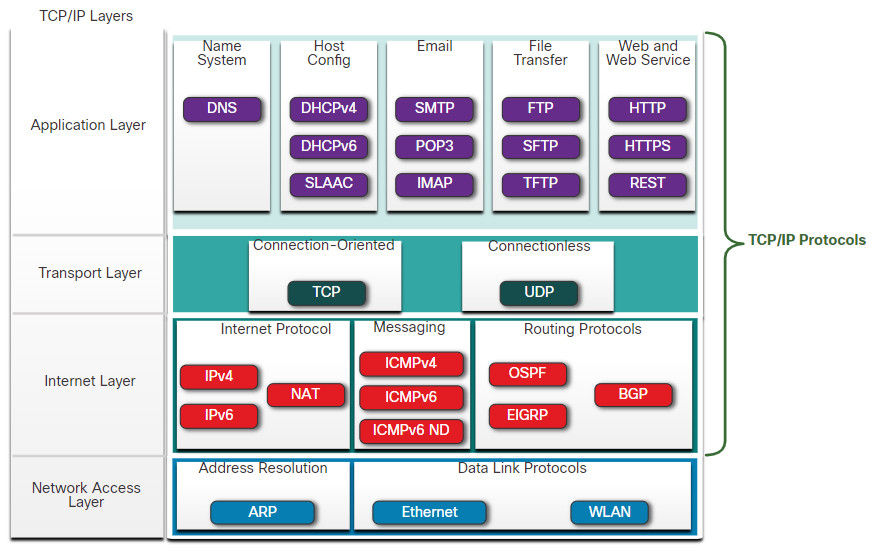
5.2.3 The TCP/IP Protocol Suite
Today, the TCP/IP protocol suite includes many protocols and continues to evolve to support new services. Some of the more popular ones are shown in the figure.
TCP/IP is the protocol suite used by the internet and the networks of today. TCP/IP has two important aspects for vendors and manufacturers:
- Open standard protocol suite – This means it is freely available to the public and can be used by any vendor on their hardware or in their software.
- Standards-based protocol suite – This means it has been endorsed by the networking industry and approved by a standards organization. This ensures that products from different manufacturers can interoperate successfully.
5.2.4 Message Formatting and Encapsulation
When a message is sent from source to destination, it must use a specific format or structure. Message formats depend on the type of message and the channel that is used to deliver the message.
5.2.5 Message Size
Another rule of communication is message size.
5.2.6 Message Timing
Message timing is also very important in network communications. Message timing includes the following:
- Flow Control – This is the process of managing the rate of data transmission. Flow control defines how much information can be sent and the speed at which it can be delivered. For example, if one person speaks too quickly, it may be difficult for the receiver to hear and understand the message. In network communication, there are network protocols used by the source and destination devices to negotiate and manage the flow of information.
- Response Timeout – If a person asks a question and does not hear a response within an acceptable amount of time, the person assumes that no answer is coming and reacts accordingly. The person may repeat the question or instead, may go on with the conversation. Hosts on the network use network protocols that specify how long to wait for responses and what action to take if a response timeout occurs.
- Access method – This determines when someone can send a message. Click Play in the figure to see an animation of two people talking at the same time, then a “collision of information” occurs, and it is necessary for the two to back off and start again. Likewise, when a device wants to transmit on a wireless LAN, it is necessary for the WLAN network interface card (NIC) to determine whether the wireless medium is available.

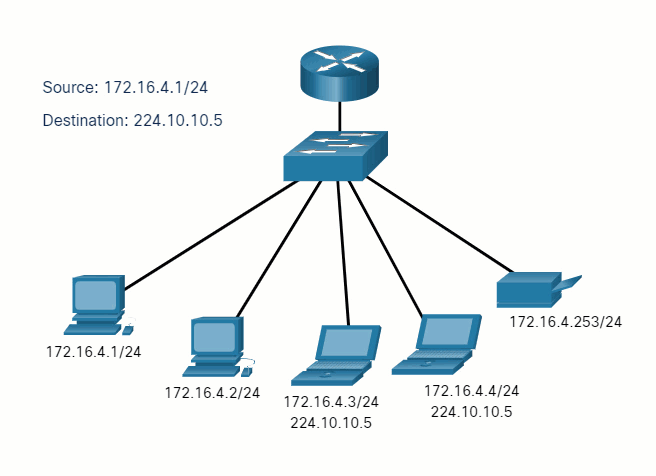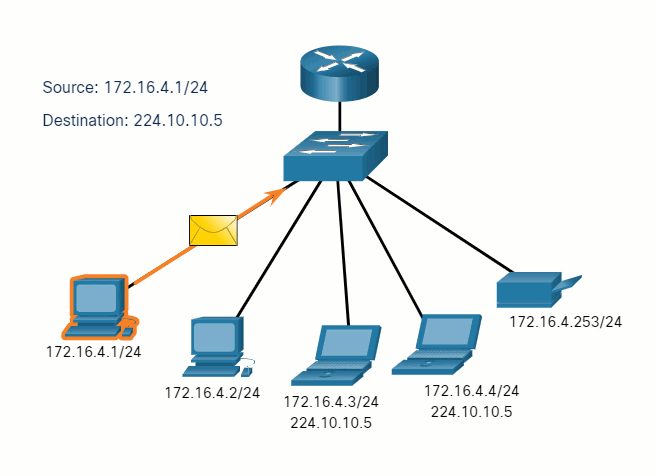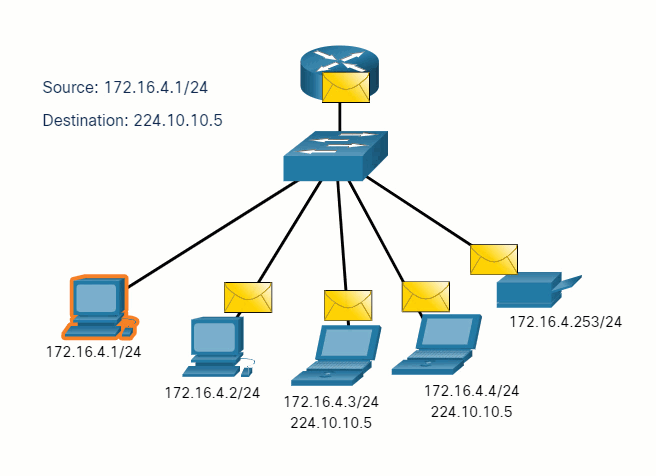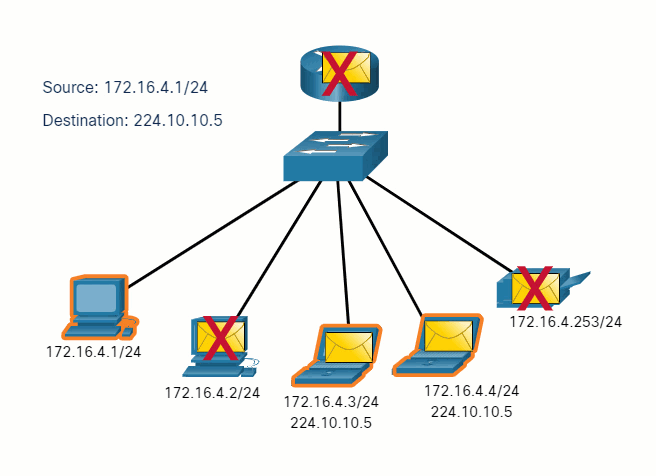
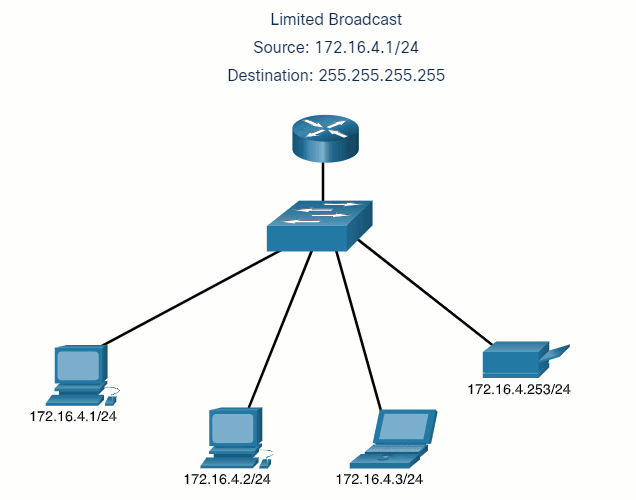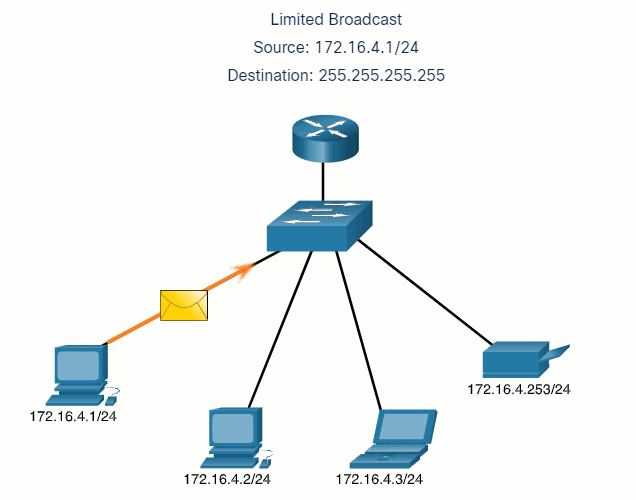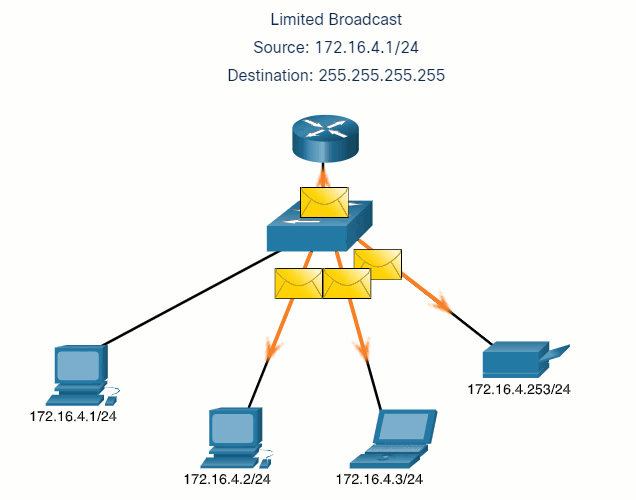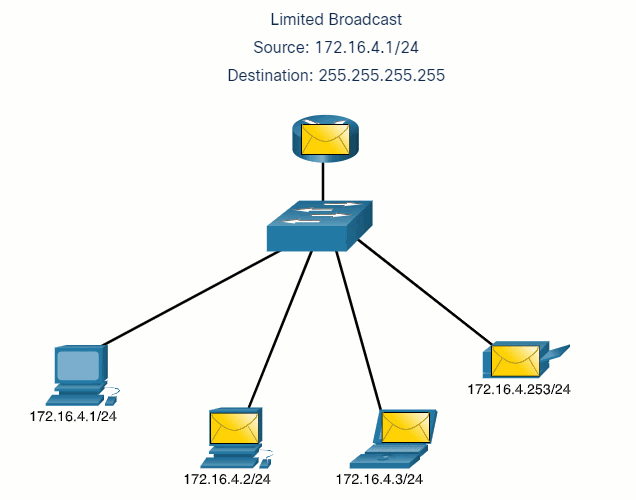
5.2.7 Unicast, Multicast, and Broadcast
A message can be delivered in different ways. Sometimes, a person wants to communicate information to a single individual. At other times, the person may need to send information to a group of people at the same time, or even to all people in the same area.
Hosts on a network use similar delivery options to communicate. These methods of communication are called unicast, multicast, and broadcast.
5.2.8 The Benefits of Using a Layered Model
You cannot actually watch real packets travel across a real network the way you can watch the components of a car being put together on an assembly line. so, it helps to have a way of thinking about a network so that you can imagine what is happening. A model is useful in these situations.
Complex concepts such as how a network operates can be difficult to explain and understand. For this reason, a layered model is used to modularize the operations of a network into manageable layers.
These are the benefits of using a layered model to describe network protocols and operations:
- Assisting in protocol design because protocols that operate at a specific layer have defined information that they act upon and a defined interface to the layers above and below
- Fostering competition because products from different vendors can work together
- Preventing technology or capability changes in one layer from affecting other layers above and below
- Providing a common language to describe networking functions and capabilities
As shown in the figure, there are two layered models that are used to describe network operations:
- Open System Interconnection (OSI) Reference Model
- TCP/IP Reference Model
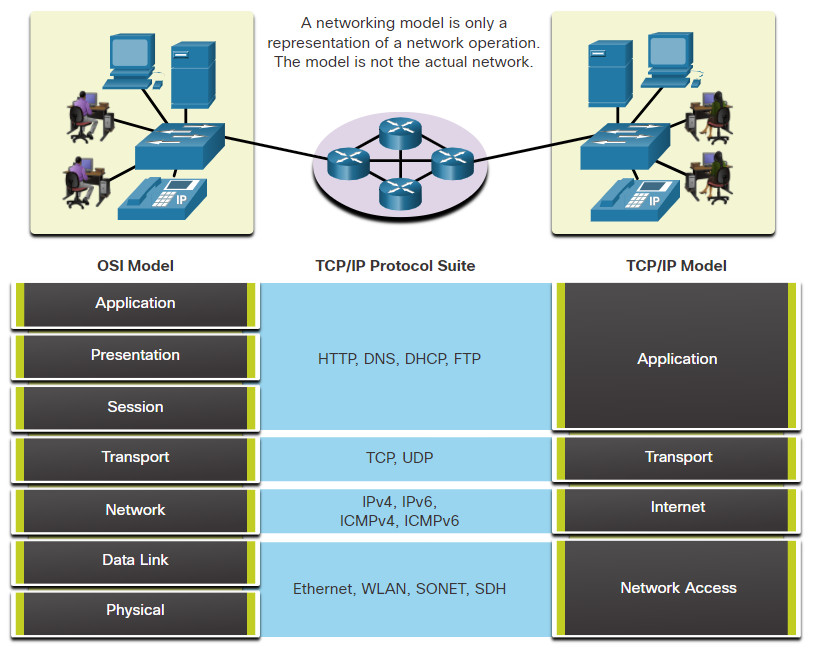
5.2.9 The OSI Reference Model
The OSI reference model provides an extensive list of functions and services that can occur at each layer. This type of model provides consistency within all types of network protocols and services by describing what must be done at a particular layer, but not prescribing how it should be accomplished.
It also describes the interaction of each layer with the layers directly above and below. The TCP/IP protocols discussed in this course are structured around both the OSI and TCP/IP models. The table shows details about each layer of the OSI model. The functionality of each layer and the relationship between layers will become more evident throughout this course as the protocols are discussed in more detail.
| OSI Model Layer | Description |
|---|---|
| 7 – Application | The application layer contains protocols used for process-to-process communications. |
| 6 – Presentation | The presentation layer provides for common representation of the data transferred between application layer services. |
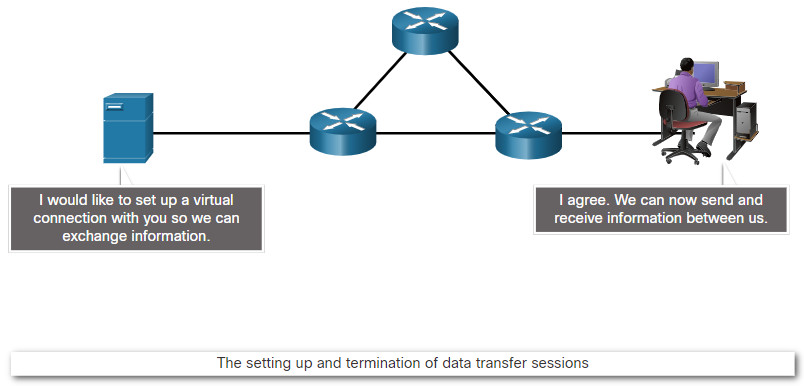
| 5 – Session | The session layer provides services to the presentation layer to organize its dialogue and to manage data exchange. |
| 4 – Transport | The transport layer defines services to segment, transfer, and reassemble the data for individual communications between the end devices. |
| 3 – Network | The network layer provides services to exchange the individual pieces of data over the network between identified end devices. |
| 2 – Data Link | The data link layer protocols describe methods for exchanging data frames between devices over a common media |
| 1 – Physical | The physical layer protocols describe the mechanical, electrical, functional, and procedural means to activate, maintain, and de-activate physical connections for a bit transmission to and from a network device. |
Note: Whereas the TCP/IP model layers are referred to only by name, the seven OSI model layers are more often referred to by number rather than by name. For instance, the physical layer is referred to as Layer 1 of the OSI model, data link layer is Layer 2, and so on.
5.2.10 The TCP/IP Protocol Model
The TCP/IP protocol model for internetwork communications was created in the early 1970s and is sometimes referred to as the internet model. This type of model closely matches the structure of a particular protocol suite. The TCP/IP model is a protocol model because it describes the functions that occur at each layer of protocols within the TCP/IP suite. TCP/IP is also used as a reference model. The table shows details about each layer of the OSI model.
| TCP/IP Model Layer | Description |
|---|---|
| 4 – Application | Represents data to the user, plus encoding and dialog control. |
| 3 – Transport | Supports communication between various devices across diverse networks. |
| 2 – Internet | Determines the best path through the network. |
| 1 – Network Access | Controls the hardware devices and media that make up the network. |
The definitions of the standard and the TCP/IP protocols are discussed in a public forum and defined in a publicly available set of IETF request for comment (RFC) documents. An RFC is authored by networking engineers and sent to other IETF members for comments.
5.3 Data Encapsulation
5.3.1 Segmenting Messages
Knowing the OSI reference model and the TCP/IP protocol model will come in handy when you learn about how data is encapsulated as it moves across a network. It is not as simple as a physical letter being sent through the mail system.
In theory, a single communication, such as a video or an email message with many large attachments, could be sent across a network from a source to a destination as one massive, uninterrupted stream of bits. However, this would create problems for other devices needing to use the same communication channels or links. These large streams of data would result in significant delays. Further, if any link in the interconnected network infrastructure failed during the transmission, the complete message would be lost and would have to be retransmitted in full.
A better approach is to divide the data into smaller, more manageable pieces to send over the network. Segmentation is the process of dividing a stream of data into smaller units for transmissions over the network. Segmentation is necessary because data networks use the TCP/IP protocol suite send data in individual IP packets. Each packet is sent separately, similar to sending a long letter as a series of individual postcards. Packets containing segments for the same destination can be sent over different paths.
This leads to segmenting messages having two primary benefits:
- Increases speed – Because a large data stream is segmented into packets, large amounts of data can be sent over the network without tying up a communications link. This allows many different conversations to be interleaved on the network called multiplexing.
- Increases efficiency – If a single segment fails to reach its destination due to a failure in the network or network congestion, only that segment needs to be retransmitted instead of resending the entire data stream.
Click each button in the figure to view the animations of segmentation and multiplexing.
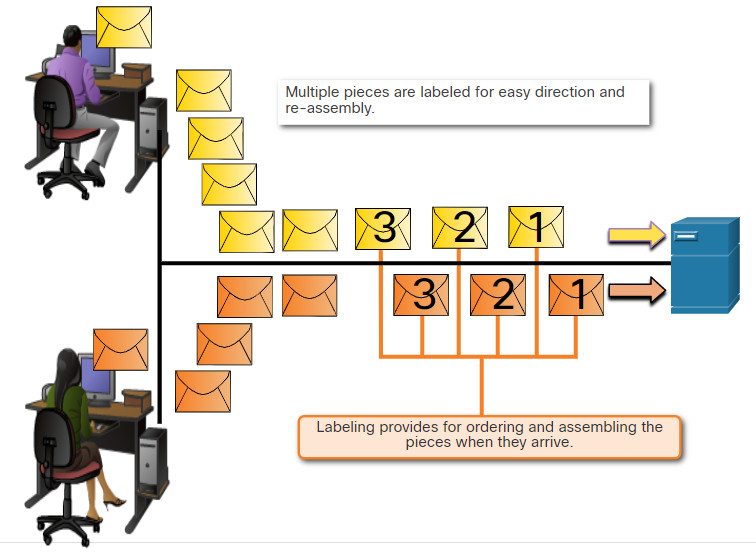
5.3.2 Sequencing
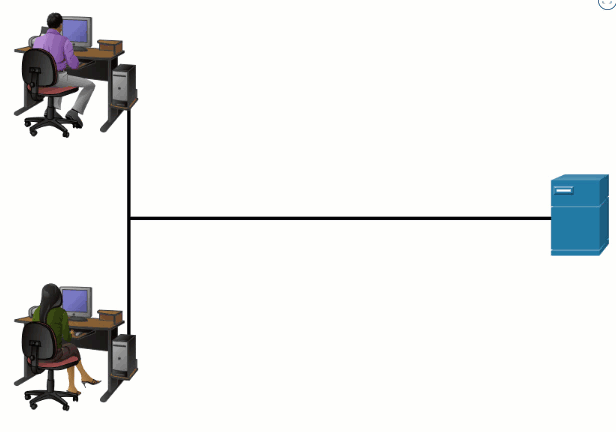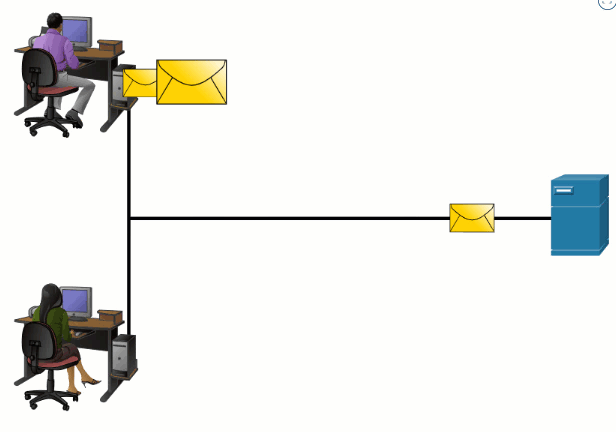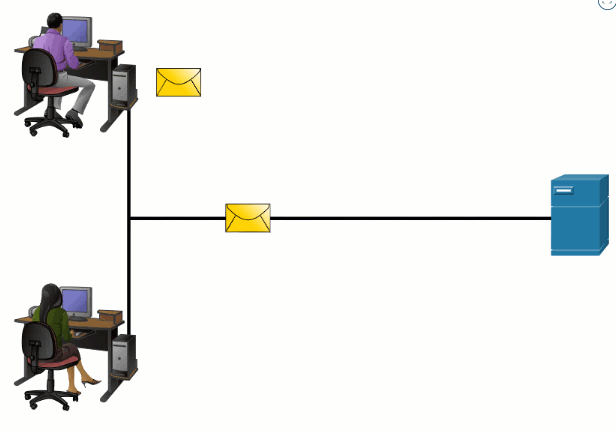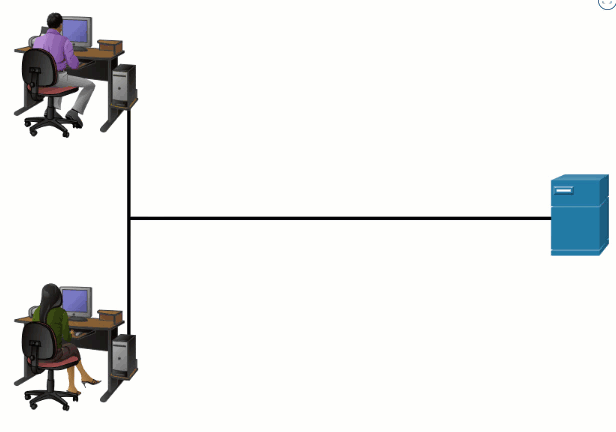
The challenge to using segmentation and multiplexing to transmit messages across a network is the level of complexity that is added to the process. Imagine if you had to send a 100-page letter, but each envelope could only hold one page. Therefore, 100 envelopes would be required, and each envelope would need to be addressed individually. It is possible that the 100-page letter in 100 different envelopes arrives out-of-order. Consequently, the information in the envelope would need to include a sequence number to ensure that the receiver could reassemble the pages in the proper order.
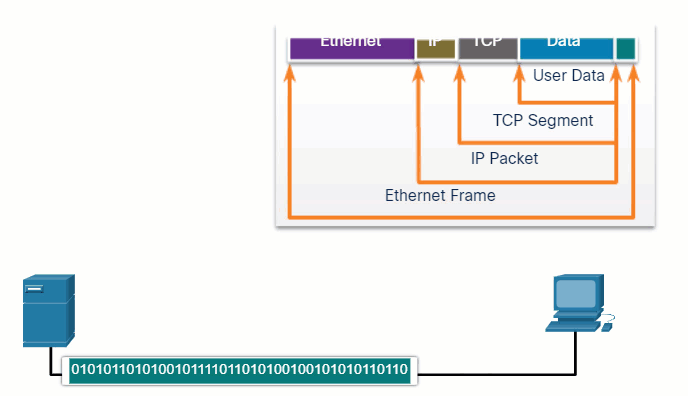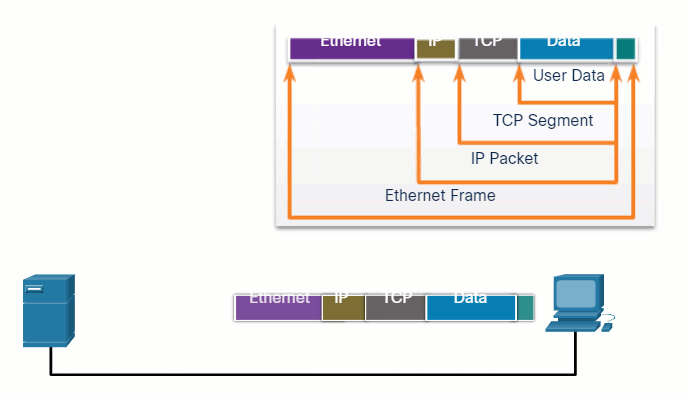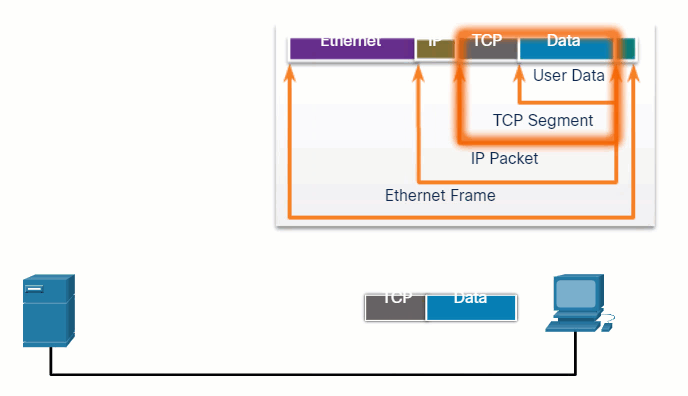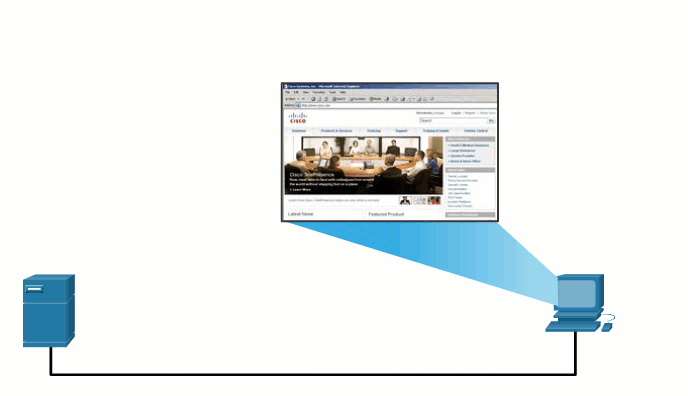
In network communications, each segment of the message must go through a similar process to ensure that it gets to the correct destination and can be reassembled into the content of the original message, as shown in the figure. TCP is responsible for sequencing the individual segments.
5.3.3 Protocol Data Units
As application data is passed down the protocol stack on its way to be transmitted across the network media, various protocol information is added at each level. This is known as the encapsulation process.
Note: Although the UDP PDU is called datagram, IP packets are sometimes also referred to as IP datagrams.
The form that a piece of data takes at any layer is called a protocol data unit (PDU). During encapsulation, each succeeding layer encapsulates the PDU that it receives from the layer above in accordance with the protocol being used. At each stage of the process, a PDU has a different name to reflect its new functions. Although there is no universal naming convention for PDUs, in this course, the PDUs are named according to the protocols of the TCP/IP suite. The PDUs for each form of data are shown in the figure.
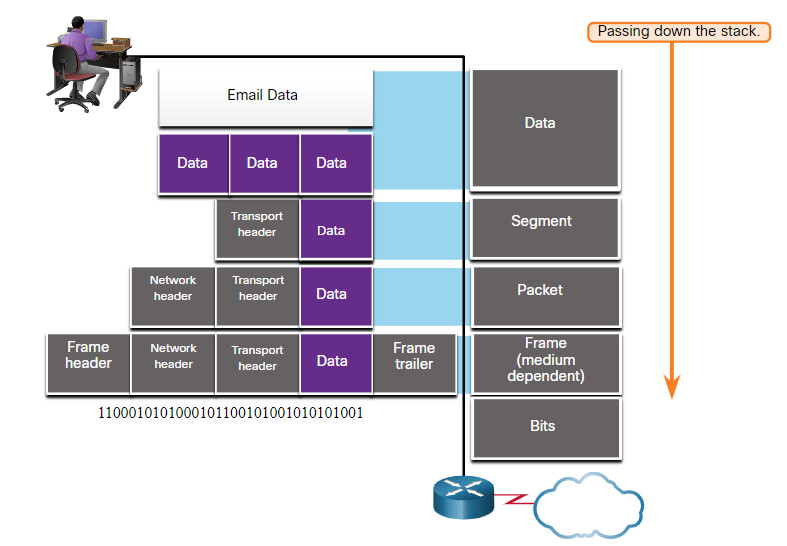
- Data – The general term for the PDU used at the application layer
- Segment – Transport layer PDU
- Packet – Network layer PDU
- Frame – Data Link layer PDU
- Bits – Physical layer PDU used when physically transmitting data over the medium
Note: If the Transport header is TCP, then it is a segment. If the Transport header is UDP then it is a datagram.
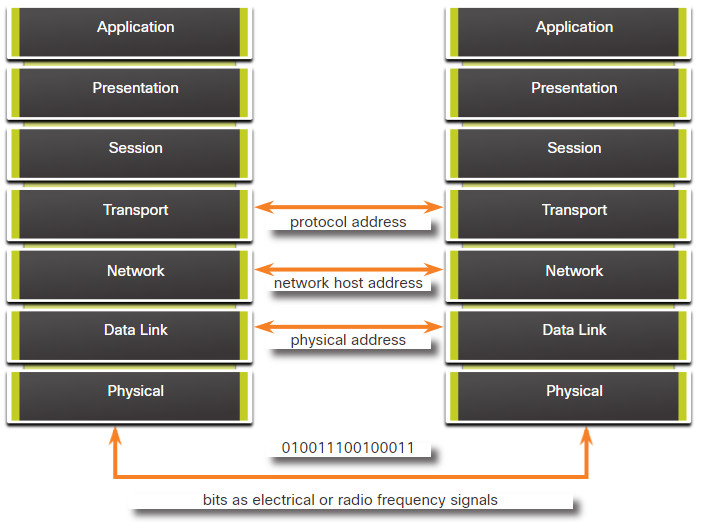
5.3.4 Three Addresses
Network protocols require that addresses be used for network communication. Addressing is used by the client to send requests and other data to a server. The server uses the client’s address to return the requested data to the client that requested it.
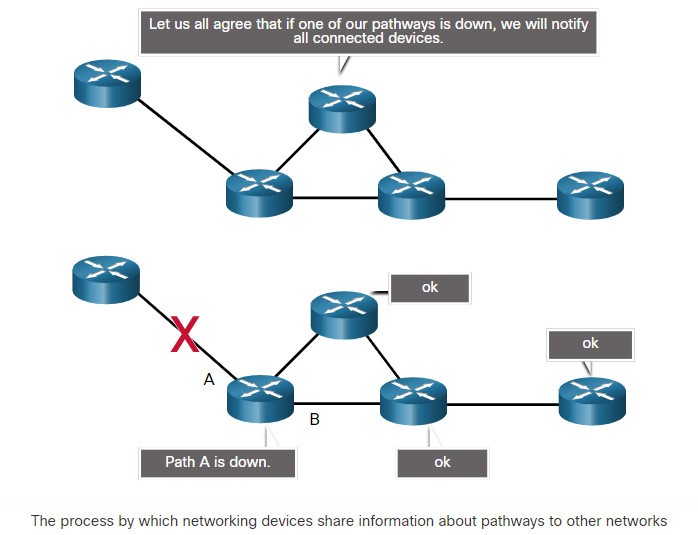
The OSI transport, network, and data link layers all use addressing in some form. The transport layer uses protocol addresses in the form of port numbers to identify network applications that should handle client and server data. The network layer specifies addresses that identify the networks that clients and servers are attached to and the clients and servers themselves. Finally, the data link layer specifies the devices on the local LAN that should handle data frames. All three addresses are required for client-server communication, as shown in the figure.
5.3.5 Encapsulation Example
When messages are being sent on a network, the encapsulation process works from top to bottom. At each layer, the upper layer information is considered data within the encapsulated protocol. For example, the TCP segment is considered data within the IP packet.
You saw this animation previously in this module. This time, click Play and focus on the encapsulation process as a web server sends a web page to a web client.
5.3.6 De-encapsulation Example
This process is reversed at the receiving host and is known as de-encapsulation. De-encapsulation is the process used by a receiving device to remove one or more of the protocol headers. The data is de-encapsulated as it moves up the stack toward the end-user application.
You saw this animation previously in this module. This time, click Play and focus on the de-encapsulation process.
5.3.7 Lab – Introduction to Wireshark
Wireshark is a software protocol analyzer, or “packet sniffer” application, used for network troubleshooting, analysis, software and protocol development, and education. Wireshark is used throughout the course to demonstrate network concepts. In this lab, you will use Wireshark to capture and analyze network traffic.
5.3.7 Lab – Introduction to Wireshark
5.4 Network Protocols Summary
5.4.1 What Did I Learn in this Module?
Network Communications
Networks come in all sizes and can be found in homes, businesses, and other organizations. The internet is the largest network in existence . All computers that connect to a network are known as hosts or end devices. Much of the interaction between hosts is client-server traffic. Hosts can operate as clients or servers or both clients and servers in peer-to-peer networks. Servers are hosts that use specialized software to enable them to respond to requests for different types of data from clients. Clients are hosts that use software applications such as web browsers, email clients, or file transfer applications to request data from servers. When we use the internet, we use a combination of copper and fiber optic cables or wireless and satellite communications to carry our data traffic. Connections to the internet are through internet service providers that connect to each other using global Tier 1 and Tier 2 ISPs that connect to each other through Internet Exchange Points (IXP). Larger businesses may connect to Tier 2 ISPs through a Point of Presence (POP). Tier 3 ISPs connect homes and businesses to the internet. Traffic between a computer and an internet server can take many different paths. Some paths can be very direct, but others may seem to go out of the way. In addition, data that is sent between a computer and server may be sent on a different path from that on which it is received.
Communications Protocols
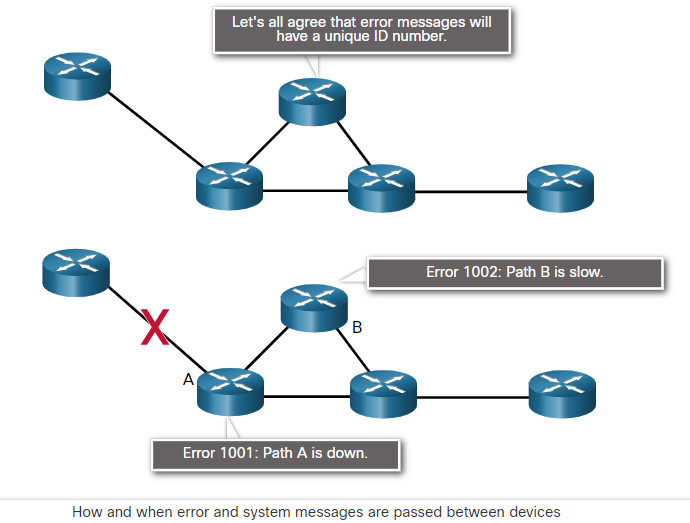
Data communications requires more than just connections. Devices must know how to communicate. For this devices use communications rules or protocols, just as face-to-face communications between people use rules. Network protocols specify many features of network communication such as message encoding, message formatting and encapsulation, message size, message timing, and delivery options. Examples of networking protocols include Hypertext Transfer Protocol (HTTP), Transmission Control Protocol (TC), and Internet Protocol (IP). It is very important that a cybersecurity analyst know the structure of protocol data and how protocols function on the network. Protocols specify how messages are structured and the way that networking devices share information about pathways to other networks. They also specify how and when error and system messages are passed between devices. In addition, protocols specify how data transfer sessions are setup and terminated. The TCP/IP protocol suite is used by the internet and data networks in homes, businesses, and other organizations. The TCP/IP suite is a family of protocols that conform to freely available open-source standards that are endorsed by the networking industry and approved by standards organizations. This enables devices from different manufacturers to work together. The TCP/IP protocol suite has four layers of protocols that work together when messages are sent and received. Common protocols at the application layer of the suite are DNS, DHCP, POP3, and HTTPS, among others. Transport layer protocols are TCP and UDP. Examples of internet layer protocols are IPv4, IPv6, ICMP, and EIGRP. Messages are formatted to conform to protocols standards. Protocol data is encapsulated by putting higher layer data within lower layer data when the data is sent. The reverse process occurs when the data is received. Protocol standards specify the size of messages and how the messages are encoded to be sent over network connections as radio waves, pulses of light, or electrical signals. The receiving host decodes the messages. Protocol standards also specify the rate at which data is sent (flow control), the time that a host waits to receive a response from the destination (response timeout), and the way in which hosts determine when they can send data on a shared-media network (access method). Unicast messages are sent to one destination host. Multicast messages are sent to a group of hosts. Broadcasts are sent to all hosts in the same area of the network. Layered communication models have a number of benefits. Models assist in protocol and device design. They also increase competition between manufacturers because devices must work together. Finally, models prevent changes at one layer from impacting other layers and provide a common way to describe network operation. Two models are the OSI and TCP/IP reference models. The OSI model has seven layers. The different layers have different functions. The TCP/IP model has four layers.
Data Encapsulation
Messages that consist of large amounts of data can not be sent across the network as one massive stream of bits. This is because other people would need to wait for the entire communication to complete before they could use the network, and if the communication failed, the entire message would need to be sent again. Instead, data is broken into a series of smaller pieces and sent over the network. This is called segmentation. Segmentation is required by the TCP/IP protocol suite. Data is sent as packets. Each packet is separately addressed and can take different paths through a network to reach the destination. Segmentation increases the speed and efficiency of data networks. Increased speed is gained because many data conversations can happen at the same time on the network. This is called multiplexing. Efficiency is gained because only data that is not received by a destination needs to be re-sent. Messages are segmented to be sent, and must be recombined when they are received. As data is passed down the protocol stack to be sent, different information is added by each layer. This process is called encapsulation. The form that data takes at different layer is called a protocol data unit (PDU). During encapsulation, the PDUs are encapsulated within PDUs in the next layer down the stack when the data is sent. The reverse process occurs when the data is received. At the OSI application layer, the PDU is generally referred to simply as data. The data is encapsulated into segments or datagrams at the transport layer. The network layer PDU is called a packet, it encapsulates segments. The data link layer encapsulates packets into frames. Finally, the physical layer transmits bits across the network. The OSI transport, network, and data link layers all use addressing. The transport layer uses protocol addresses in the form of port numbers. The network layer uses IP addresses to identify hosts and networks, Finally, the data link layer uses hardware addresses to identify which hosts on the local network should handle frames. These addresses identify the source of the data and the destination of the data. After the data is received, it is de-encapsulated so that the data can be used by the client applications that requested it.