IT Essentials (Version 7.00) – IT Essentials 8.0 Bridge Final exam Answers
1. Which DNS resource record is used to resolve a domain name to an IPv6 address?
- A
- AAAA
- MX
- TXT
2. Which DNS SPAM management feature uses cryptography by creating a TXT RR that contains the public encryption key of the domain?
- SPF
- DKIM
- DMARC
3. Which message is broadcasted by a DHCPv4 client to initiate the lease obtaining process?
- DHCPACK
- DHCPDISCOVER
- DHCPOFFER
- DHCPREQUEST
4. Which message is unicasted by a DHCPv4 server to confirm that the host can use the offered IP configuration?
- DHCPACK
- DHCPDISCOVER
- DHCPOFFER
- DHCPREQUEST
5. Which two messages are used in the DHCP lease renewal process (Choose two.)?
- DHCPACK
- DHCPDISCOVER
- DHCPOFFER
- DHCPREQUEST
6. Which of the following are based on logical connections, instead of physical connections?
- VLANS
- Subnets
- DNS entries
- unverified switch ports
7. What is the file type that can contain all the installation files for an operating system?
- EXE
- DLL
- ISO
- BAT
8. Which graphics card is recommended for intense 3D art rendering and video editing?
- Dedicated graphics card
- Integrated graphics processor
9. What Windows Deployment Tool would a technician use to deploy applications to multiple computers across a given network?
- Group Policy
- Local Security Policy
- EFS
- APIPA
10. A user believes their gaming PC has been compromised because a gaming application provided location information. Which Windows 10 feature could be used to enable or disable the sharing of location information?
- apps settings
- privacy and security settings
- account settings
- gaming settings
11. After cables were reconnected to a switch in a wiring closet, several PCs that had been previously configured manually can no longer access resources outside the local network. The PC configurations were not altered in the process and resources on the local network can still be accessed. What is a possible cause of the problem?
- The PCs are no longer on the correct VLAN.
- The DNS configuration on the PCs is incorrect.
- The DHCP server has been misconfigured.
- The cabling to the PCs is faulty.
12. A technician wants to upgrade several computers to Windows 10 over the network. Which of the following boot methods supports this upgrade method?
- SSH
- HTTPS
- HTTP
- PXE
13. What happens when you are running a game in Windows 10 and have turned on the Gaming mode?
- prevents Windows Update from performing driver installations and sending restart notifications
- prevents the antivirus program from running in the background
- prevents Windows defender from running in the background
- gives 100% of the CPU cycle to the GPU
14. Refer to the exhibit. Which commands would the technician enter in Windows 10 PowerShell to determine the GUID of the GPT partition displayed?
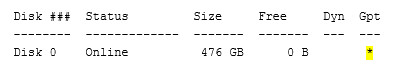
DISKPART> select disk 0
DISKPART> uniqueid disk
C:\WINDOWS\system32> diskpart
DISKPART> select disk 0
DISKPART> list disk
DISKPART> select disk 0
DISKPART> select disk 0
C:\WINDOWS\system32> sfc/scannow
15. Which statement describes how hosts on VLANs communicate?
- Hosts on different VLANs can communicate using a wireless network.
- Hosts on different VLANs can communicate using a layer 2 switch.
- Hosts on different VLANs should be in the same IP network.
- Hosts on different VLANs communicate through routers.
16. A technician is trying to upgrade a computer running Windows 10 Pro to Windows 11 Pro. The computer hardware specs are as follows:
- 512 GB SSD drive
- 8 GB RAM
- a graphics card compatible with DirectX 12 or later with WDDM 2.0 driver
- Trusted Platform Module (TPM) version 1.0.
- Secure boot capable BIOS
- Intel i7 Quad Core Processor
During the installation, the following message is displayed “This PC doesn’t currently meet all the system requirements for Windows 11”. What is the most probable reason for this?
- Secure Boot has not been enabled in the bios
- the PC is not connected to the internet
- the ISO is corrupt
- the Trusted Platform Module should be version 2
17. Where can you configure the recording time in Windows 10 in order to capture your game play?
- Start > Settings > Gaming > Xbox Game Bar
- Start > Settings > Gaming > Captures
- Start > Settings > Gaming > Game Mode
- Start > Settings > Privacy
18. Which Windows 10 security feature helps to reduce the risk of malware exploiting the privileges of the Administrators group?
- SFC
- DNS
- EFS
- UAC
19. What is two-factor authentication (2FA)?
- two different authentication factors are used for verification
- two different passwords are used for verification
- the password undergoes two hashing functions
- two passwords undergo two separate hashing functions
20. A technician wants to upgrade a user computer to Windows 10 but keep the current settings and files intact during the new installation. Which upgrade method should the technician use?
- clean install
- network install
- image deployment
- in-place upgrade
21. Which security method in Windows 10 uses a single username and password once for multiple applications?
- EFS
- SSO
- permission propagation
- inheritance
22. A technician is setting up a booth at a company job fair. The technician needs to ensure job seekers can interact with the company application securely and limit all other activities on the laptop. The technician must also ensure that whenever the computer is rebooted or powered on it logs on automatically without a password. Which account type would the technician set up on this kiosk machine to do this?
- Administrator
- Power user
- Guest
- Standard user
23. Which two features in Microsoft Windows 10 require a user to input the Windows Hello Pin in order to set them up?
- File encryption using EFS
- Window Hello Facial
- Windows PC Privacy Settings
- Window Hello Fingerprint
- Folder encryption using EFS
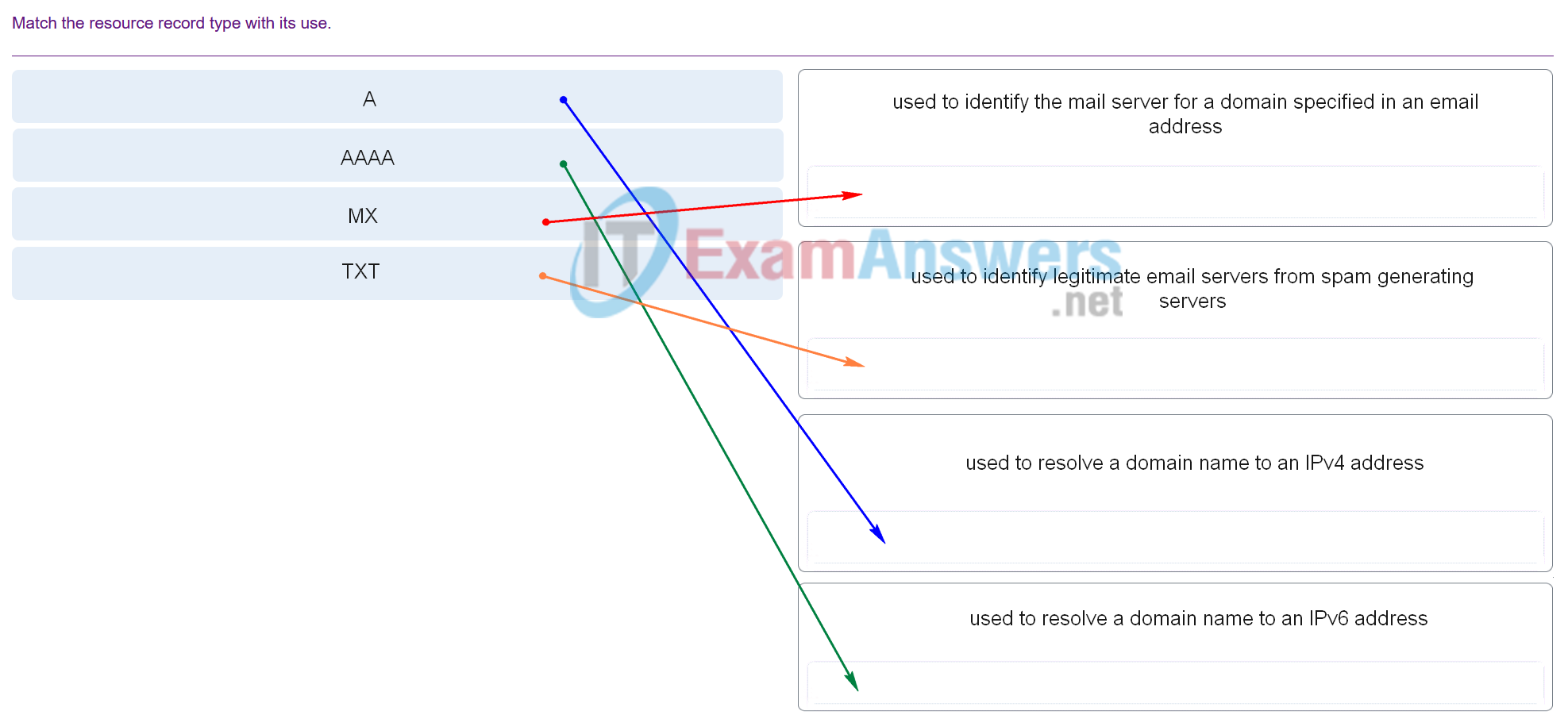
24. Match the resource record type with its use.
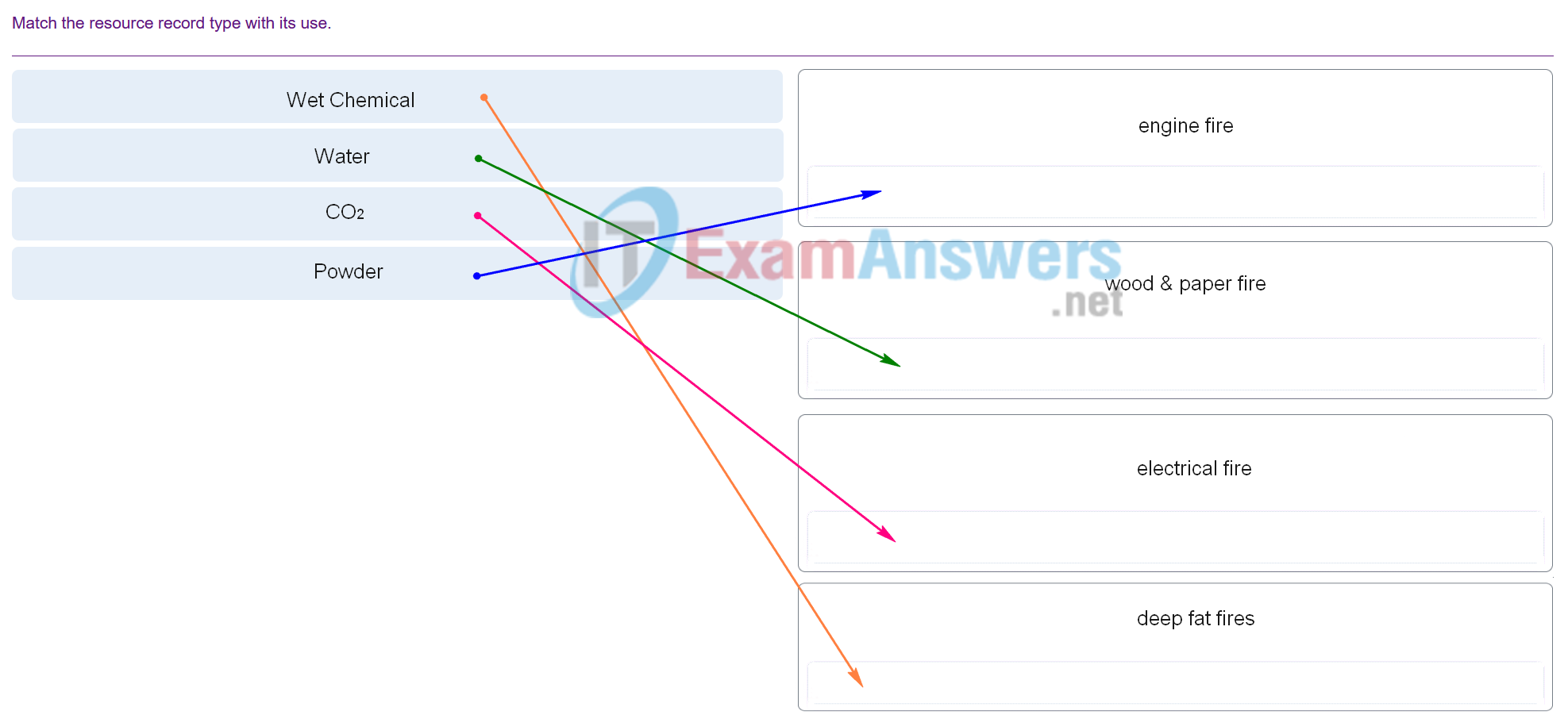
25. Match the type of Fire Extinguisher required for the type of fire described,
26. The acronym for putting out a fire using a fire extinguisher is PASS. What does PASS stand for?
- Pin, Angle, Squeeze, Spread
- Pull, Aim, Squeeze, Sweep
- Pin, Aim, Squeeze, Sweep
- Pull, Aim, Squeeze, Spread
- Pull, Accuracy, Squeeze, Spread
27. What is the function of the Secure Boot setting in UEFI firmware?
- it allows for support of up to 2.2 terabyte hard drives
- it enables only Windows 8 or Windows 10 to be used as an operating system
- it increases the boot upload speed
- it enables AHCI (Advanced Host Controller Interface) mode
28. When an end device requests services from a DHCPv4 server it receives a host IPv4 address and a subnet mask. Which two other IPv4 addresses are also typically provided to a DCHPv4 client? (Choose two.)
- local HTTP web server address
- DNS server address
- automatic private IPv4 address
- LAN default gateway address
- LAN NTP server address
29. What is an acceptable use policy?
- It is an agreement between two or more parties that defines the appropriate user access to resources or services.
- It is used to identify potential issues, provide insights for improvements, and take corrective action to prevent critical and major future incidents .
- It is a step-by-step instruction guide detailing how to access computers and networked services efficiently and securely.
- It is a centralized repository of articles and documents that allows the users to create, share, and manage knowledge across the organization.
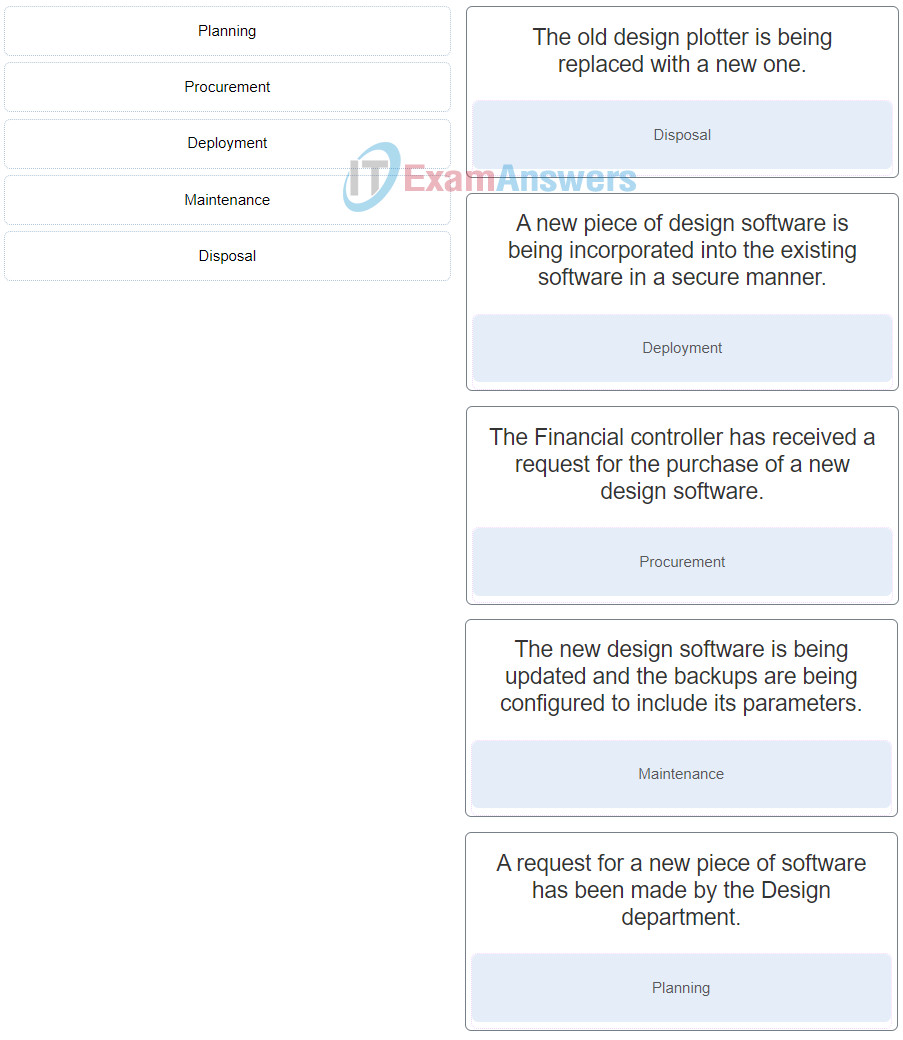
30. Match the stages of the procurement lifecycle to the scenarios described.
IT Essentials ( Version 7.00) – IT Essentials 8.0 Bridge exam Q30
31. What action must be performed first when disposing of an asset that has reached the end of its lifecycle?
- destroy the asset
- donate or recycle the asset
- sanitize any data contained in the asset
- find the appropriate waste disposal company
32. What is the reason why the DHCPREQUEST message is sent as a broadcast during the DHCPv4 process?
- for hosts on other subnets to receive the information
- to notify other hosts not to request the same IP address
- for routers to fill their routing tables with this new information
- to notify other DHCP servers on the subnet that the IP address was leased
33. Which three statements describe a DHCP Discover message? (Choose three.)
- The message comes from a client seeking an IP address.
- The destination IP address is 255.255.255.255.
- All hosts receive the message, but only a DHCP server replies.
- The source MAC address is 48 ones (FF-FF-FF-FF-FF-FF).
- The message comes from a server offering an IP address.
- Only the DHCP server receives the message.
34. Match each DHCP message type with its description. (Not all options are used.)
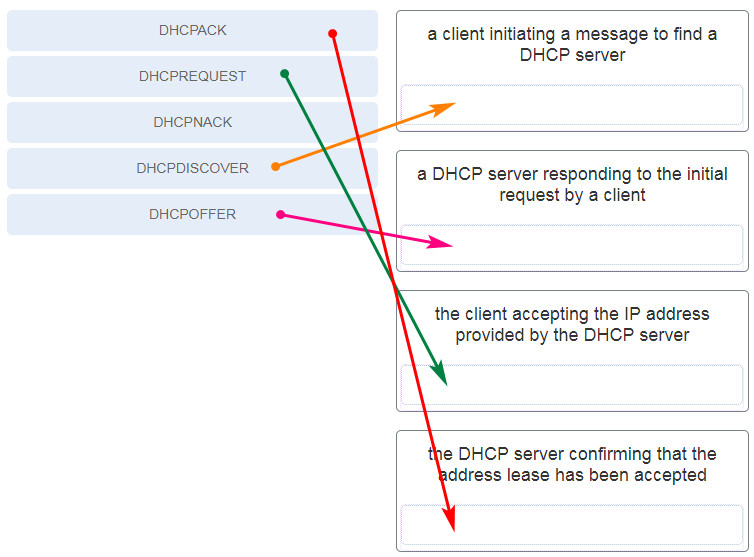
35. What type of information is contained in a DNS MX record?
- the fully qualified domain name (FQDN) of the alias used to identify a service
- the IP address for an FQDN entry
- the IP address of an authoritative name server
- the domain name mapped to a mail exchange server
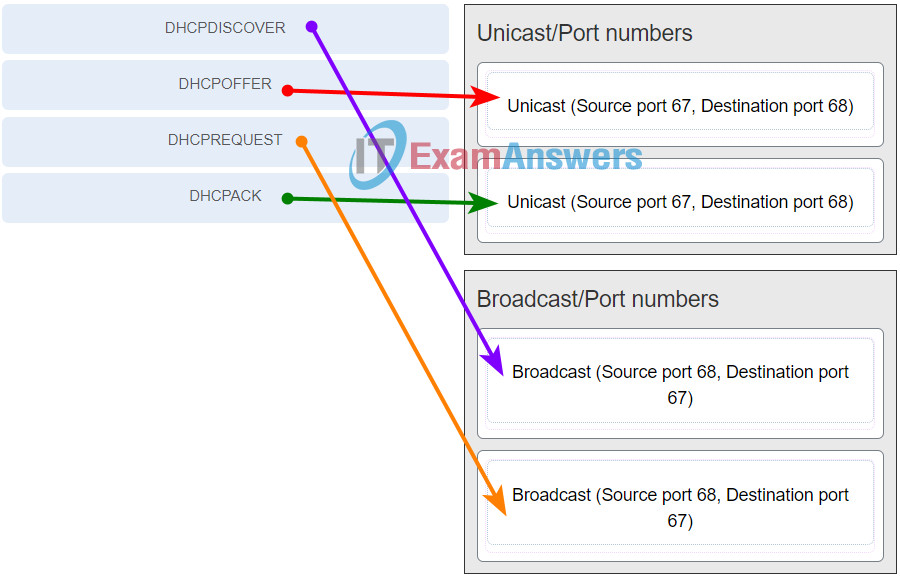
36. Match the DHCP message with the port numbers and message types used.
IT Essentials ( Version 7.00) – IT Essentials 8.0 Bridge exam q36
37. Which DNS SPAM Management feature uses an unencrypted RR to identify authorized servers permitted to send emails from the domain?
- DMARC
- DKIM
- SPF
- AAAA
38. Which type of server keeps a list of domain names and their associated IP address information in resource records (RRs)?
- DNS
- WINS
- Domain controller
- DHCP

Match the stages of the procurement lifecycle to the scenarios described.
Place the options in the following order:
Disposal
Deployment
Procurement
Maintenance
Planning
Added, thank you very much!
A technician is trying to upgrade a computer running Windows 10 Pro to Windows 11 Pro. The computer hardware specs are as follows:
During the installation, the following message is displayed “This PC doesn’t currently meet all the system requirements for Windows 11”. What is the most probable reason for this?
CORRECT
the Trusted Platform Module should be version 2
COMMENTS
While the requirement to upgrade a Windows 10 device to Windows 11 is only that the PC be Secure Boot capable by having UEFI/BIOS enabled, you may also consider enabling or turning Secure Boot on for better security.
The minimum requirements to upgrade a computer running Windows 10 Pro to Windows 11 Pro are:
Note- While the requirement to upgrade a Windows 10 device to Windows 11 is only that the PC be Secure Boot capable by having UEFI/BIOS enabled, you may also consider enabling or turning Secure Boot on for better security.
Match the DHCP message with the port numbers and message types used.
Place the options in the following order:
[+] DHCPOFFER
[+] DHCPACK
[#] DHCPDISCOVER
[#] DHCPREQUEST