Network Technician Career Path Exam Answers
1. What two radio frequency bands are used in home Wireless LANs? (Choose two.)
- 5 MHz
- 9 MHz
- 2.4 GHz
- 5 GHz
- 900 GHz
2. Which is a characteristic of the network SSID?
- It is encrypted by default.
- It is case sensitive.
- It contains exactly 16 characters.
- It is only required for guest access.
3. What is the function of the SSID on a wireless network?
- It identifies the wireless protocol in use.
- It contains the password required to join the network.
- It identifies the wireless standard required to join the network.
- It identifies the WLAN in use on the network.
4. What makes fiber preferable to copper cabling for interconnecting buildings? (Choose three.)
- durable connections
- limited susceptibility to EMI/RFI
- greater distances per cable run
- lower installation cost
- easily terminated
- greater bandwidth potential
5. What is the purpose of protocols in data communications?
- specifying the device operating systems that will support the communication
- dictating the content of the message sent during communication
- specifying the bandwidth of the channel or medium for each type of communication
- providing the rules required for a specific type of communication to occur
6. Which two functions are primary functions of a router? (Choose two.)
- packet forwarding
- domain name resolution
- MAC address assignment
- path selection
7. What three blocks of addresses are defined by RFC 1918 for private network use? (Choose three.)
- 172.16.0.0/12
- 169.254.0.0/16
- 192.168.0.0/16
- 10.0.0.0/8
- 100.64.0.0/14
- 239.0.0.0/8
8. Consider the group of five IPv4 addresses each with the subnet mask of 255.255.255.0. Which two IPv4 addresses belong to the same local network? (Choose two.)
- 192.168.10.2
- 193.168.10.16
- 192.167.10.74
- 192.168.10.56
- 192.168.100.62
9. Which IPv6 address notation is valid?
- 2001:0DB8::ABCD::1234
- 2001::ABCD::
- ABCD:160D::4GAB:FFAB
- 2001:DB8:0:1111::200
10. When IPv4 is configured for a computer on a network, what does the subnet mask identify?
- the dynamic subnetwork configuration
- the device that the computer uses to access another network
- the part of the IP address that identifies the network
- the pool of addresses assigned within the network
11. What is one difference between a switch and a router?
- A router creates smaller broadcast domains, and a switch extends the size of a broadcast domain.
- A router provides segmentation at Layer 2, and a switch provides segmentation at Layer 3.
- A router uses a routing table to store information about destination host IP addresses, and a switch uses an ARP table to store information about destination host MAC addresses.
- A router propagates broadcast messages, and a switch does not propagate broadcast messages.
12. What is a benefit of adding a router within an IP network?
- reduces the number of hosts that can connect to the network
- increases the size of the local network
- controls host-to-host traffic within a single local network
- keeps broadcasts contained within a local network
13. Refer to the exhibit. The IP address of which device interface should be used as the default gateway setting of host H1?
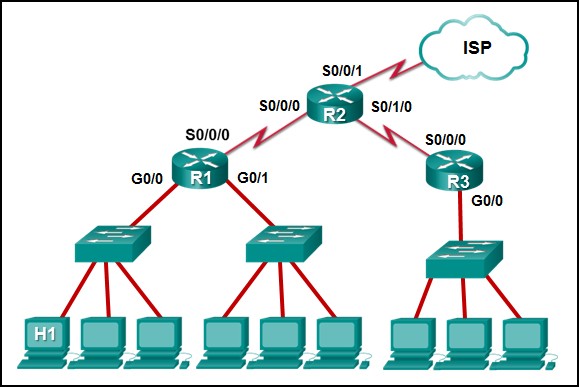
Network Technician Career Path Exam
- R1: S0/0/0
- R2: S0/0/0
- R1: G0/0
- R2: S0/0/1
14. A user types www.cisco.com into a web browser to visit the corporate website. Which service will resolve the domain name to an associated IP address?
- FTP
- DHCP
- DNS
- SMTP
15. A new employee is attempting to configure a cell phone to connect to the email server of the company. Which port number should be selected when using the IMAP4 protocol to access email messages stored on the local server?
- 143
- 25
- 110
- 69
16. What application protocol is used to transfer files between systems?
- FTP
- SSH
- DHCP
- IMAP
17. An employee of a large corporation remotely logs into the company using the appropriate username and password. The employee is attending an important video conference with a customer concerning a large sale. It is important for the video quality to be excellent during the meeting. The employee is unaware that after a successful login, the connection to the company ISP failed. The secondary connection, however, activated within seconds. The disruption was not noticed by the employee or other employees.
What three network characteristics are described in this scenario? (Choose three.)
- powerline networking
- scalability
- security
- integrity
- fault tolerance
- quality of service
18. Which two scenarios would benefit the user the most by adding quality of service (QoS) to the network? (Choose two.)
- Students are updating information about their sport activities on the class Facebook page.
- A student is sending emails to a friend.
- A student is communicating via Skype with a friend in another country.
- Students are watching a lecture from a YouTube site.
19. Which three statements describe the functions of the Cisco hierarchical network design model? (Choose three.)
- Route summarization is not necessary at the core and distribution layers.
- The core layer usually employs a star topology.
- The goal of the core layer is maximizing throughput.
- The distribution layer is responsible for traffic filtering and isolating failures from the core.
- The access layer provides a means of connecting end devices to the network.
- The distribution layer distributes network traffic directly to end users.
20. Refer to the exhibit. PC1 sends a frame with the destination MAC address 3c97.0e07.a1b2. Switch S1 looks up the destination MAC address in its CAM table but the address is not there. What will the switch do?
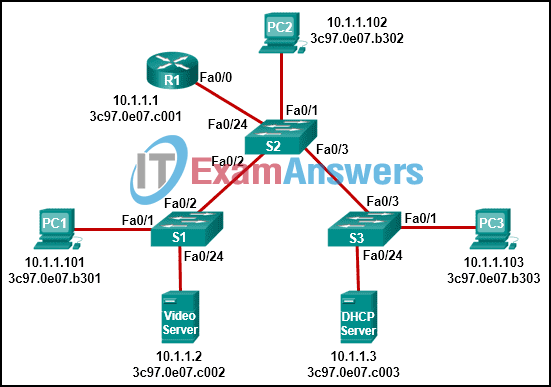
- It willl add the destination MAC address to the CAM table.
- It will forward the frame out all ports except Fa0/1.
- It will send a destination unreachable message back to PC1.
- The switch will drop the frame.
- It will forward the frame out port Fa0/2 towards the router.
21. Refer to the exhibit. Host A has sent a packet to host B. What will be the source MAC and IP addresses on the packet when it arrives at host B?
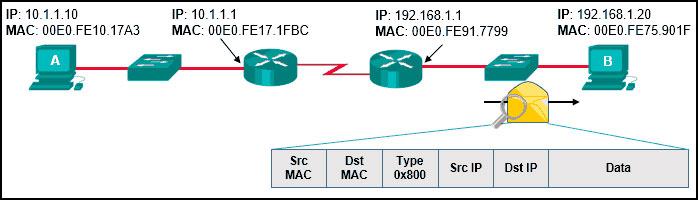
Network Technician Pathway Course Final Exam
- Source MAC: 00E0.FE91.7799
Source IP: 10.1.1.10 - Source MAC: 00E0.FE10.17A3
Source IP: 10.1.1.10 - Source MAC: 00E0.FE10.17A3
Source IP: 192.168.1.1 - Source MAC: 00E0.FE91.7799
Source IP: 10.1.1.1 - Source MAC: 00E0.FE91.7799
Source IP: 192.168.1.1
22. What is the dotted decimal representation of the IPv4 address 11001011.00000000.01110001.11010011?
- 203.0.113.211
- 209.165.201.223
- 192.0.2.199
- 198.51.100.201
23. Which statement is true regarding the UDP client process during a session with a server?
- Application servers have to use port numbers above 1024 in order to be UDP capable.
- A three-way handshake takes place before the transmission of data begins.
- Datagrams that arrive in a different order than that in which they were sent are not placed in order.
- A session must be established before datagrams can be exchanged.
24. A home network has both wired and wireless connectivity. From a laptop computer, the user issues a ping to the wireless printer located in another room. The first two echo requests fail, but the last two succeed. Additional pings are all successful. Why do the first two echo requests fail?
- The distance between the computer and the printer causes delay on the first two pings.
- The computer and the printer must join the wireless network first and that process takes time.
- The computer must use ARP to obtain the MAC address of the printer and this process takes time.
- The wireless printer must be activated and that takes time.
25. What are two potential network problems that can result from ARP operation? (Choose two.)
- On large networks with low bandwidth, multiple ARP broadcasts could cause data communication delays.
- Multiple ARP replies result in the switch MAC address table containing entries that match the MAC addresses of hosts that are connected to the relevant switch port.
- Large numbers of ARP request broadcasts could cause the host MAC address table to overflow and prevent the host from communicating on the network.
- Manually configuring static ARP associations could facilitate ARP poisoning or MAC address spoofing.
- Network attackers could manipulate MAC address and IP address mappings in ARP messages with the intent of intercepting network traffic.
26. In the OSI model, what three functional areas are addressed by physical layer standards? (Choose three.)
- physical components
- frame encapsulation
- media access control
- signaling
- encoding
- error detection and retransmission
27. How do hosts ensure that their packets are directed to the correct network destination?
- They search in their own local routing table for a route to the network destination address and pass this information to the default gateway.
- They send a query packet to the default gateway asking for the best route.
- They always direct their packets to the default gateway, which will be responsible for the packet delivery.
- They have to keep their own local routing table that contains a route to the loopback interface, a local network route, and a remote default route.
28. Refer to the exhibit. The router receives a packet with the destination IP address of 172.17.10.14. What will the router do with this packet?
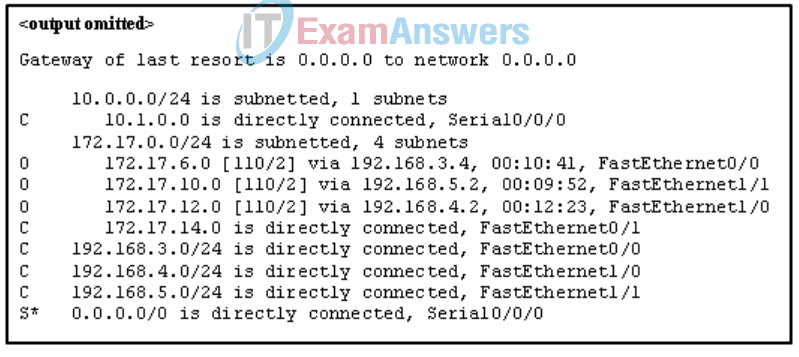
- Forward the packet through interface FastEthernet1/1.
- Forward the packet through interface FastEthernet0/1.
- Forward the packet through interface Serial0/0/0.
- Drop the packet.
29. A user has taken a personal laptop to work. The laptop is unable to discover the name of the office wireless network. What are two potential causes of this problem? (Choose two.)
- The laptop has not received an IP address from the wireless router.
- The wireless router is set to mixed mode.
- The laptop must be configured with the office workgroup name.
- The network does not support the wireless protocol in use by the laptop.
- The wireless router is not broadcasting the SSID.
30. A user is complaining that an external web page is taking longer than normal to load.The web page does eventually load on the user machine. Which tool should the technician use with administrator privileges in order to locate where the issue is in the network?
- ipconfig /displaydns
- ping
- nslookup
- tracert
31. Local workstations are unable to access web pages located on the www.cisco.com web server. Pings from the workstations to the server using the ping www.cisco.com command are successful. What settings should the administrator check to determine the cause of the problem?
- MAC address settings
- IP address settings
- firewall settings
- DNS server settings
32. A technician receives a trouble ticket from a user reporting that a website is no longer accessible. What two questions would the technician ask to narrow down the potential problem? (Choose two.)
- What operating system is installed on your computer?
- Can you access other web sites from this computer browser?
- What model computer are you using to access this site?
- Could you access this web site previously from this device?
- Do you remember your password to this web site?
33. Which two actions demonstrate effective active listening techniques when assisting a customer with a problem? (Choose two.)
- re-asking questions the customer has already answered when describing the problem
- stopping the customer so you can ask questions as you think of them
- allowing the customer to explain the problem
- correcting the customer when they use incorrect technical terms or jargon
- Let the customer know that you are listening by interjecting phrases such as “I understand,” “I see,” and “OK.”
34. Which question enables the technician to determine the scope of a network issue reported by a user?
- Are other users in your area experiencing the same issue?
- Is the problem one that you have experienced before?
- Are you seeing any error messages when the problem occurs?
- Have you added any new applications recently?
35. Employees in an organization report that they cannot access the customer database on the main server. Further investigation reveals that the database file is now encrypted. Shortly afterward, the organization receives a threatening email demanding payment for the decryption of the database file. What type of attack has the organization experienced?
- man-in-the-middle attack
- DoS attack
- trojan horse
- ransomware
36. A secretary receives a phone call from someone claiming that their manager is about to give an important presentation but the presentation files are corrupted.
The caller sternly asks that the secretary email the presentation right away to a personal email address. The caller also states that the secretary is being held personally responsible for the success of this presentation.
What type of social engineering tactic is the caller using?
- intimidation
- trusted partners
- familiarity
- urgency
37. What do you call an impersonation attack that takes advantage of a trusted relationship between two systems?
- spamming
- man-in-the-middle
- sniffing
- spoofing
38. Match the examples of cyber threat to the description.
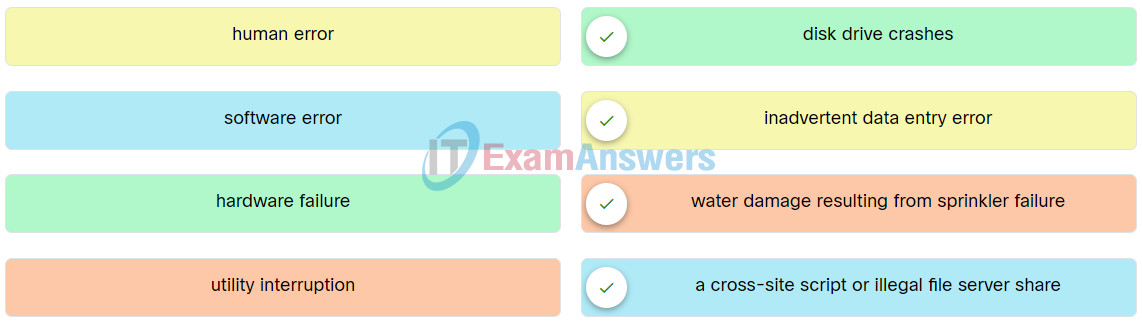
Network Technician Pathway Course Final Exam Q38
39. Match the characteristics to the correct type of fiber.
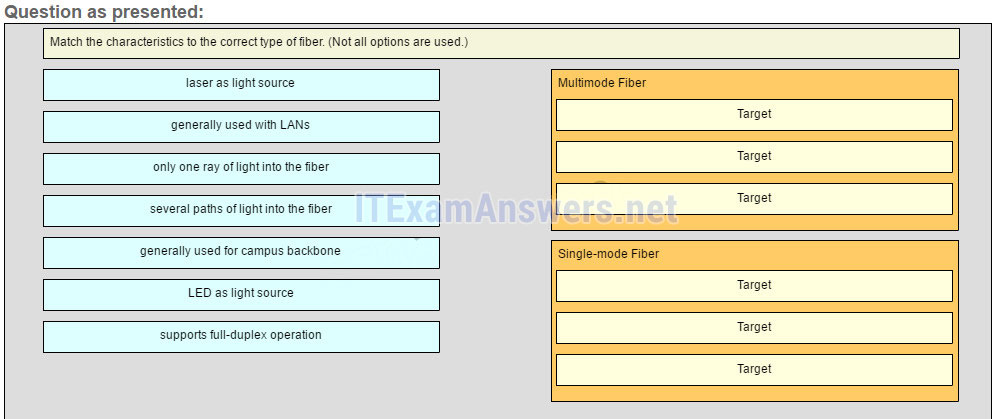
Answer
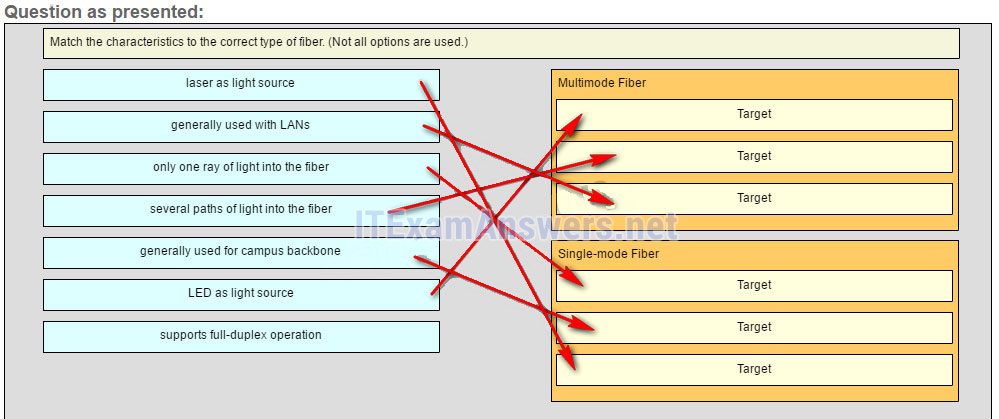
LED as light source: Multimode Fiber
Laser as light source: Single-mode Fiber
Generally used with Campus backbone: Single-mode Fiber
Generally used with LANs: Multimode Fiber
Several paths of light into the fiber: Multimode Fiber
Only one ray of light into the fiber: Single-mode Fiber
40. Match each DHCP message type with its description.
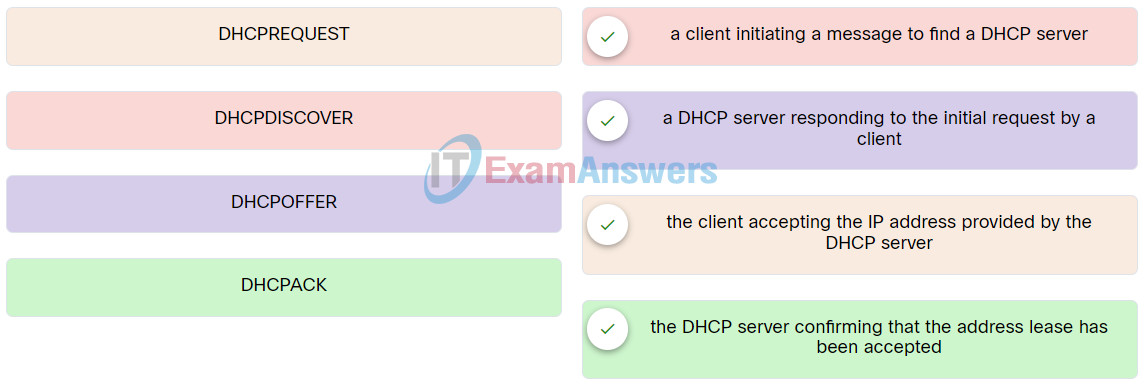
Network Technician Pathway Course Final Exam 40
41. Match the definition to the type of cloud.
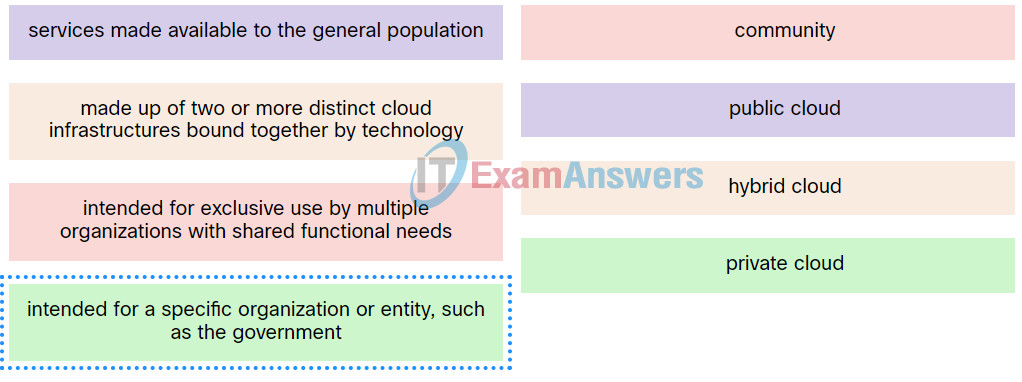
Network Technician Pathway Course Final Exam Q41
42. A client device has initiated a secure HTTP request to a web browser. Which well-known port address number is associated with the destination address?
- 110
- 80
- 443
- 404
43. Which address should be configured as the default gateway address of a client device?
- the IPv4 address of the router interface that is connected to the same LAN
- the Layer 2 address of the switch management interface
- the Layer 2 address of the switch port that is connected to the workstation
- the IPv4 address of the router interface that is connected to the internet
44. Which two applications provide virtual terminal access to remote servers? (Choose two.)
- DHCP
- SMTP
- SSH
- DNS
- Telnet
45. Refer to the exhibit. An administrator is troubleshooting connectivity on the office network. PC1 is able to send print jobs to Printer1, but is unable to access File Server1. Which action would correct the problem?
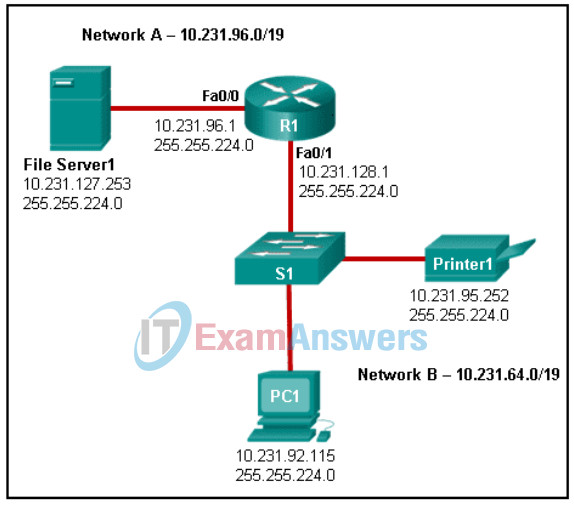
Network Technician Pathway Course Final Exam
- Change the R1 Fa0/1 interface IP address to 10.231.64.1.
- Change the File Server1 IP address to 10.231.96.253.
- Change the PC1 IP address to 10.231.64.115.
- Change the R1 Fa0/0 interface subnet mask to 255.255.0.0.
46. A group of Windows PCs in a new subnet has been added to an Ethernet network. When testing the connectivity, a technician finds that these PCs can access local network resources but not the Internet resources. To troubleshoot the problem, the technician wants to initially confirm the IP address and DNS configurations on the PCs, and also verify connectivity to the local router. Which three Windows CLI commands and utilities will provide the necessary information? (Choose three.)
- netsh interface ipv6 show neighbor
- tracert
- nslookup
- ping
- arp -a
- ipconfig
- telnet
47. A user reports that the computer occasionally loses connectivity when streaming videos from the web. The technician suspects that a network hardware issue may exist in a device located between the computer and the internet edge router. Which documentation would the technician use to determine where network devices are located in the path from the user to the edge router?
- logical topology map
- physical topology map
- three-layer enterprise network design model
- cloud service architecture diagram
48. What type of connection is used when a teleworker must have secure access to devices and services located on an enterprise network?
- HTTP
- VPN
- FTP
- RTP
49. What is the default SSID Broadcast setting on a wireless router?
- Auto
- Off
- Disabled
- Enabled
50. Match the authentication method to description.
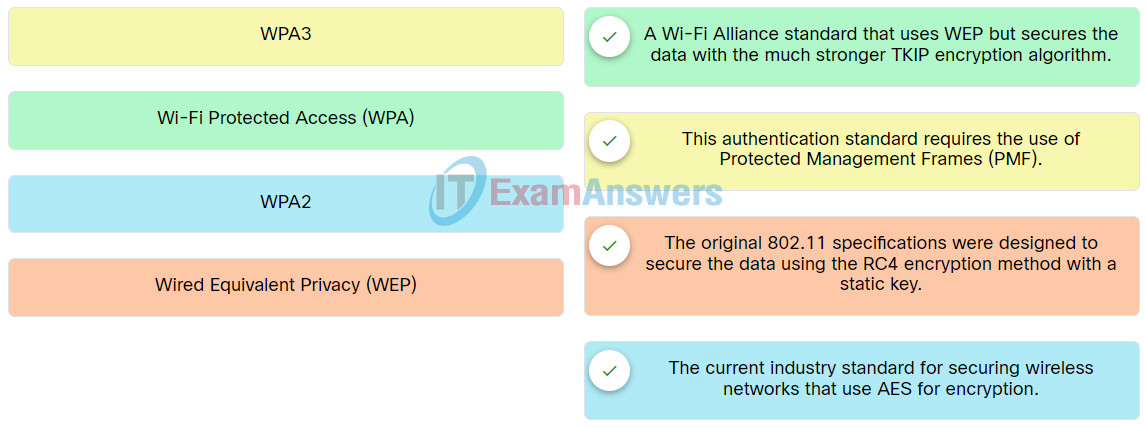
51. What is the purpose of using the Windows BitLocker tool?
- to encrypt only memory
- to encrypt only folders
- to encrypt only temporary files
- to encrypt the entire hard drive
