Cybersecurity Pathway Final Exam Answers – Junior Cybersecurity Analyst Career Path Exam
1. What is a characteristic of the security onion analogy to visualizing defense-in-depth?
- The core or heart of the onion represents the firewall surround by protective layers.
- The outer skin of the onion represents hardened internet-facing systems.
- Each layer of the onion may reveal sensitive data that is not well secured.
- All layers of the onion must be penetrated to gain access to vulnerable assets.
2. An administrator wishes to create a security policy document for end-users to protect against known unsafe websites and to warn the user about the dangers and handling of suspicious emails. What type of malware attack is being prevented?
- phishing
- DDoS
- trusted/untrusted sources verification
- adware protection
3. Which data type is protected through the use of an IPsec VPN?
- data in storage
- data in transit
- data in process
- data at rest
4. What technology can be used to protect the integrity of data in transit?
- IPsec tunnels
- hashing
- mutual authentication
- VPNs
5. The IT team of an organization is updating the policy and procedures regarding recovery controls. What are three examples of recovery controls? (Choose three.)
- firewall deployment
- server clustering
- database shadowing
- monitoring procedures
- backup/restore operations
- intrusion detection system
6. A company has set a policy that employees will be required to report any observed or suspected security issues. Which control type has the company implemented?
- incident controls
- physical controls
- administrative controls
- technical controls
7. A company provides service to process transaction data for clients. The company deals with sensitive customer information of their clients. The improper release of the information poses a serious risk to the business of the company and their clients. The information security team in the company identifies threats coming from accidentally emailing the information to an unintended party. Which two action plans could the company implement to eliminate the risk? (Choose two.)
- Implement a firewall to filter all emails sent to customers.
- Implement a technology to screen and block emails that contain sensitive information.
- Move the business operation to a private cloud and require clients to use the private cloud as well.
- Implement a policy prohibiting employees from including sensitive information in any emails to customers.
- Require employees to use a VPN connection when emailing customers.
8. A cybersecurity consulting company is helping an organization to develop a cybersecurity policy to address a few operational issues and conditions that may require more detailed requirements and directions. Which type of cybersecurity policy are they developing?
- master cybersecurity policy
- issue specific policy
- system specific policy
- general cybersecurity management policy
9. The IT team in a company discovers that some employees are visiting newly established websites that are deemed inappropriate for conducting company business. What is the first action that the IT team should take in terms of the security policies?
- Update the Network Access Policy immediatley and get users to sign it.
- Update the existing Acceptable Use Policy immediately and get all users to sign it.
- Update the Remote Access Policy immediately and get users to sign it.
- Update the incident handling policy immediately and get the employees to sign it.
10. An administrator has been granted top security clearance at a company. One day the administrator finds that certain confidential documents cannot be accessed. The administrator asks the IT team to verify the level of clearance and receives the confirmation that top security clearance is still valid. What could be the reason that the administrator cannot access the respective documents?
- The PKI certificate has been revoked.
- The firewall rules are in conflict with the access rights of the user.
- The PKI key of the user is invalid.
- The principle of least privilege has been applied.
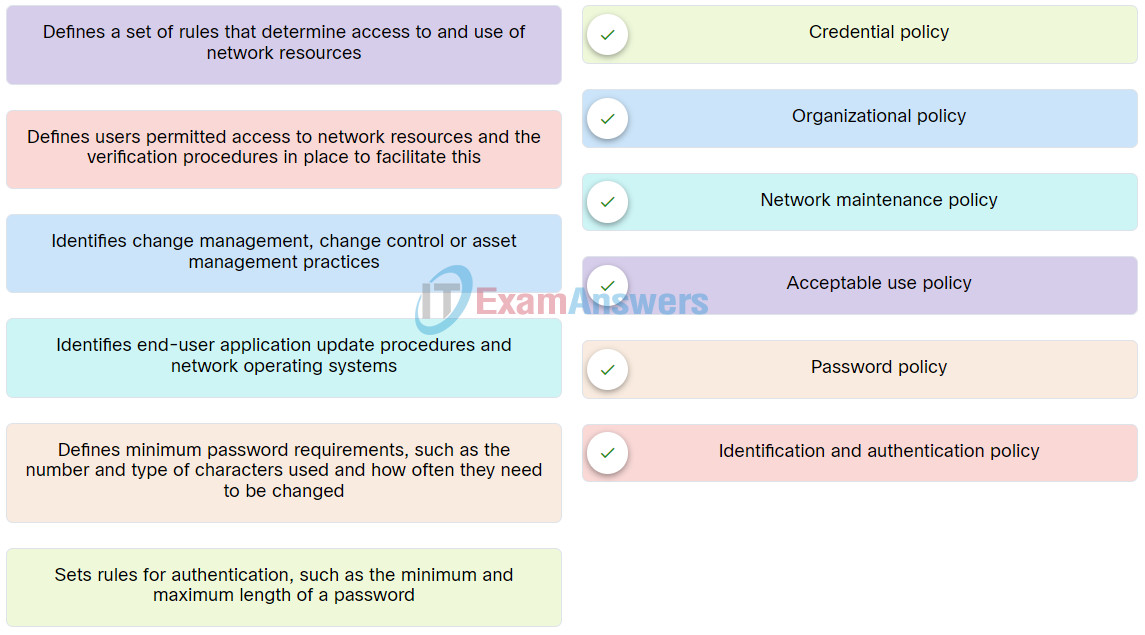
11. Match the security policy to its description.
12. What is the most compressed representation of the IPv6 address 2001:0db8:0000:abcd:0000:0000:0000:0001?
- 2001:db8::abcd:0:1
- 2001:0db8:abcd::1
- 2001:0db8:0000:abcd::1
- 2001:db8:0:abcd::1
- 2001:0db8:abcd::0001
13. A threat actor is using ping to discover hosts on a network. What type of attack is taking place?
- DoS
- address spoofing
- ICMP
- amplification
14. A cyber security analyst is reviewing security alerts in Sguil. What are three pieces of information included in an alert to identify the device generating the alert? (Choose three.)
- IP protocol number
- source and destination MAC address
- source and destination Layer 4 port
- source and destination IP address
- Layer 4 segment sequence number
- host domain name
15. Which tool is integrated into the Security Onion and displays full packet captures for analysis?
- Sguil
- Kibana
- Zeek
- Wireshark
16. Refer to the exhibit. A router is configured with a zone-based policy firewall as shown. Which two statements describe how traffic between the LAN and external hosts will be processed? (Choose two.)
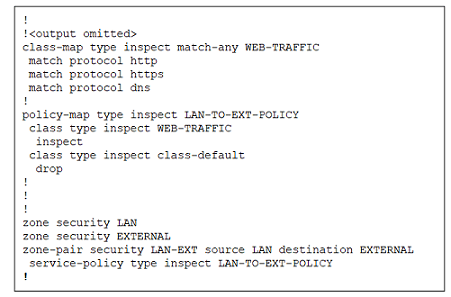
Cybersecurity Pathway Exam Q16
- Any traffic originating from the EXTERNAL zone is inspected and permitted into the LAN zone.
- Traffic originating from the LAN zone that matches the HTTP, HTTPS, or DNS protocols is inspected and permitted.
- HTTP, HTTPS and DNS traffic destined for the router itself is not permitted by this policy.
- All HTTP, HTTPS, and DNS responses originating from the EXTERNAL zone destined for the LAN zone are dropped.
- All traffic sourced from the LAN zone that does not match the HTTP, HTTPS, or DNS protocols is dropped.
17. A technician enters the commands shown to configure a zone-pair between two security zones on a router.
Router(config)# zone-pair security PRIV-PUB source PRIVATE destination PUBLIC Router(config-sec-zone-pair)#
What information must now be entered to specify which traffic can be sent across the zones and associate it with the zone-pair configuration?
- a service policy-map that is to be applied to traffic between the zones
- a list of other security zones that are included in this zone-pair
- a list of interfaces that are configured as members of the two zones
- access list statements that permit or deny specific traffic in and out of the zones
18. What type of attack disrupts services by overwhelming network devices with bogus traffic?
- DDoS
- Port scans
- Zero-day
- Brute force
19. Which of the following are commonly used port scanning applications? (Choose two.)
- Port number
- Sequence number
- Nmap
- Zenmap
20. Which of the following protocols use the Advanced Encryption Standard (AES)? (Choose two.)
- WPA2
- EAP
- WEP
- TKIP
- WPA
21. Which method of wireless authentication can take advantage of identity verification using a Radius server?
- WEP
- WPA2-Enterprise
- Open
- WPA-Personal
22. Because of a pandemic, a company decides to let employees work from home. What security technology should be implemented to ensure that data communications between the employees and the company’s network remain confidential?
- MD5
- SHA-1
- AES
- SHA-3
23. What is a difference between symmetric and asymmetric encryption algorithms?
- Symmetric encrption algorithms are slower then asymmetric encryption algorithms.
- Symmetric encryption algorithms are used to encrypt data and asymmetric encryption algorithms are used to decrypt data.
- Symmetric encryption algorithms have a maximum key length size of 512 bits but asymmetric encryption algorithms maximum key length size is 256 bits.
- Symmetric encryption algorithms use pre-shared keys while asymmetric encryption algorithms use different keys to encrypt and decrypt data.
24. What is a drawback of using a single-root PKI topology?
- It allows for the creation of unsecure hierarchical and cross-certification topologies.
- It can issue insecure certificates to end users and to a subordinate CA.
- It requires de-centralized administration that can lead to multiple points of failure.
- It is difficult to scale to a large environment.
25. What is used by PKI entities to verify the validity of a digital certificate?
- SSL
- CRL
- X.509
- S/MIME
26. A cyberanalyst is looking for an open source malware analysis tool that can run locally on the network. Which tool would meet the needs of the cyberanalyst?
- AMP
- ANY.RUN
- Threat Grid Globebox
- Cuckoo Sandbox
27. What is a feature of the ANY.RUN malware sandbox?
- It runs on the local network and can analyze multiple malware samples.
- It is a Cisco tool that can track the trajectory of malware that has entered the network and can roll back network events to obtain a copy of the downloaded malware file.
- It is an online sandbox tool and can capture screenshots of interactive elements of the malware.
- It is an open source tool that can be used to create signatures to prevent the malware file from entering the network again.
28. An organization needs a solution that will generate alerts on malware that has made it through the network perimeter and infected internal systems. What technology would be an appropriate solution for the organization?
- zone-based policy firewall
- sandbox
- host intrusion detection system
- honeypot
29. What are the most effective ways to defend against malware? (Choose two.)
- Update the operating system and other application software
- Install and update antivirus software
- Implement network firewalls
- Implement RAID
- Implement strong passwords
- Implement a VPN
30. A software company uses a public cloud service for hosting software development and deployment services. The company is concerned that software code in development might leak to competitors and result in the loss of intellectual property. Which two security coding techniques can the company implement to address the concern? (Choose two.)
- stored procedure
- obfuscation
- input validation
- normalization
- camouflage
31. A software company uses a public cloud service for hosting development and deployment services. The company is evaluating options to protect against data breaches and compromised login credentials. What two countermeasures should be implemented? (Choose two.)
- Perform a daily backup of data.
- Use an advanced encryption algorithm.
- Develop and implement compliance policies.
- Install host-based intrusion detection software on VMs in the cloud.
- Implement a multi-factor authentication process.
- Deploy development and deployment services across multiple zones.
32. What is a benefit of a Type 1 hypervisor implementation over a Type 2 hypervisor environment?
- Console software on the Type 1 hypervisor host system prevents or limits VM sprawl.
- Machines running Type 1 hypervisors can also run other host-based applications simultaneously.
- Type 1 hypervisor systems are immune to hacker attacks and VM escape exploits.
- Type 1 hypervisors do not require a separate operating system be loaded on the host machine.
33. Refer to the exhibit. What type of software is installed on the host system to support the three virtual machines?
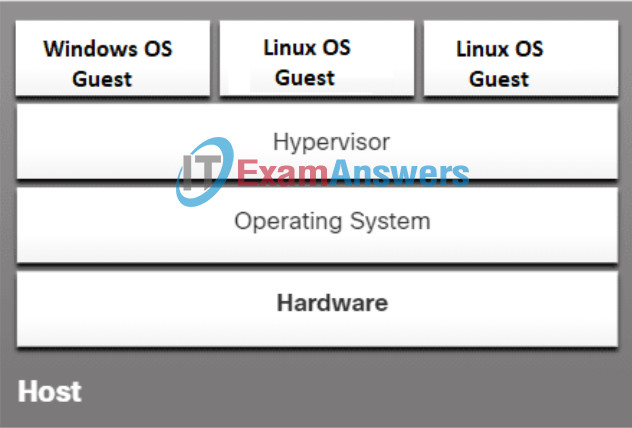
- Type 1 hypervisor software
- edge computing software
- virtual container platform
- Type 2 hypervisor software
34. Refer to the exhibit. The help desk receives a work order describing an issue with a management application running on PC-B. The work order states that the network management application cannot receive syslog messages from the LAN switch after upgrading PC-B to the latest version of Windows 10. A ping request from PC-A to PC-B fails, but both PCs are able to successfully ping the connected switch VLAN1 IP address. The technician temporarily disables the Windows Defender Firewall on PC-B for both the private and public networks. The ping request from PC-A to PC-B succeeds and the application on PC-B can receive the syslog messages from the switch. Which action should the technician perform to correct the reported issue without compromising the security of the LAN?
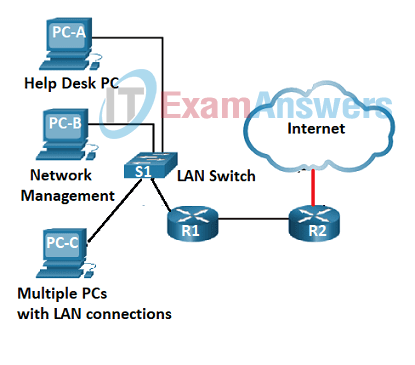
- Create a rule using IPtables to permit syslog and ICMP traffic sourced from private addresses to enter PC-B.
- Leave the Windows Defender Firewall on PC-B disabled for the private network and re-enable it for the public network only.
- Disable the Windows Defender Firewall and install a third-party host-based intrusion detection system.
- Re-enable the firewall for both networks and create a custom inbound rule on PC-B to permit the desired protocols.
35. What Windows utility should be used to configure password rules and account lockout policies on a system that is not part of a domain?
- Active Directory Security tool
- Event Viewer security log
- Local Security Policy tool
- Computer Management
36. An e-commerce website encourages users to authenticate using their individual social media account credentials. What type of a security solution enables users to use the same credentials to login to multiple networks belonging to different enterprises?
- Radius authorization
- public key infrastructure
- federated identity management
- two-factor authentication
37. A Linux administrator creates new user accounts using the useradd command. Which two files on the system contain the new user account information? (Choose two.)
- /etc/shadow
- /etc/passwd
- /users/account
- /etc/users
- /etc/users/groups
38. A cloud service company forms a security team to handle risks of disruption of cloud services caused by cyber-attacks. What should the team do first in the risk management process?
- Frame the risk.
- Monitor the risk.
- Assess the risk.
- Respond to the risk.
39. Match the network testing tool with its description.
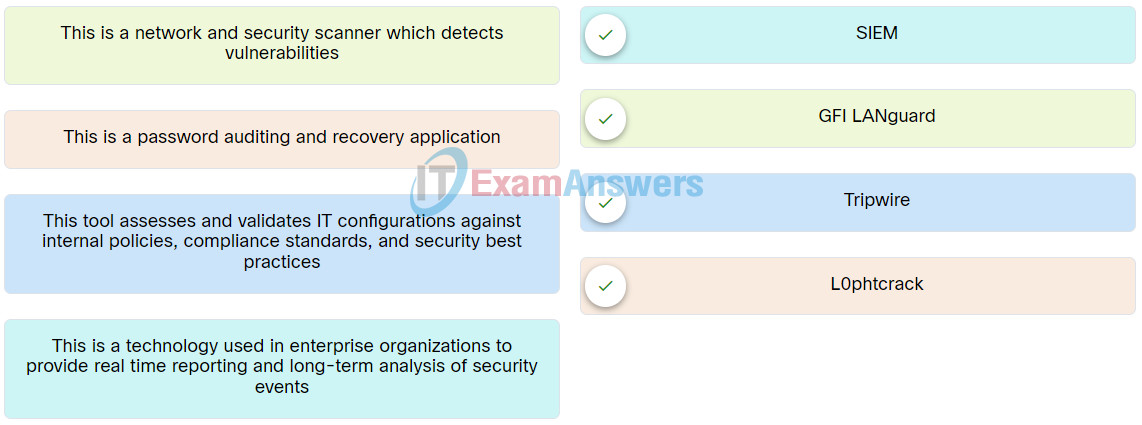
40. A penetration tester wants to collect preliminary knowledge about systems, software, networks, or people without directly engaging the target or its assets. What is this process called?
- non-intrusive scan
- intrusive scan
- brute force attack
- credentialed scan
41. When using a CVSS risk assessment tool, what must be completed first in order for a score to be calculated for the Temporal Metric Group?
- Base Metric Group
- Redemption level
- CVSS calculator
- Enviromental Metric Group
42. Match the criteria for the Base Metric Group Exploitability metrics with its description.
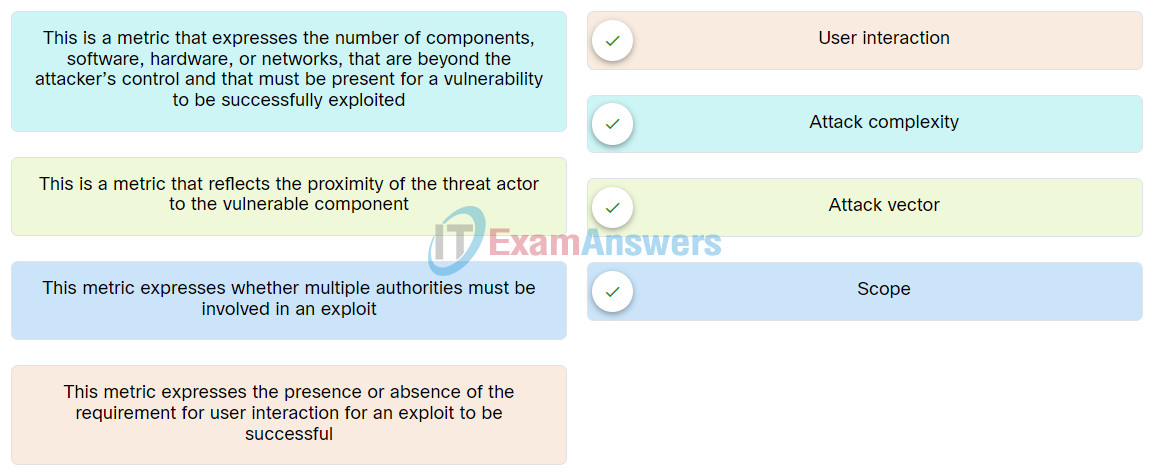
43. The IT security team of an organization is charged with cybersecurity threat assessment and risk management. Which Cisco service would assist the task by providing information about security incident detection rule sets for the Snort.org, ClamAV, and SpamCop network security tools?
- MITRE
- FireEye
- Talos
- AIS
44. A cybersecurity technician sets up a honeypot within a separate DMZ of the enterprise network. What is the purpose of doing this?
- to attract threat actors in order to gather attack-related information that can then be shared with threat intelligence platform subscribers
- to gather virus signatures so that antivirus signature database can be updated
- to set up an audit trail of threat actors who access the platform
- to gather malware signatures so that they can patch the attack surface
45. Forensic procedures must be followed exactly to ensure the integrity of data obtained in an investigation. When making copies of data from a machine that is being examined, which of the following should be done to ensure it is an exact duplicate?
- Perform a cyclic redundancy check using a checksum or hashing algorithm
- Change the attributes of data to make it read-only
- Do nothing — imaging software always makes an accurate image
- Open files on the original media and compare them to the copied data
46. What procedure should be avoided in a digital forensics investigation?
- Secure physical access to the computer under investigation.
- Reboot the affected system upon arrival.
- Make a copy of the hard drive.
- Recover deleted files.
47. A cybersecurity team needs to investigate several incidents. In which step of the NIST incident response life cycle are the tools and assets, required to do this investigation, acquired and deployed?
- detection and analysis
- post-incident activities
- preparation
- containment, eradication, and recovery,
48. In which phase of the NIST Incident Response Life Cycle are the vulnerabilities that have been exploited by the attacker corrected and patched?
- Post-Incident Activities
- Detection and Analysis
- Preparation
- Containment, Eradication, and Recovery
49. Which of the following is the simplest exercise to use for training employees and testing an organization’s disaster recovery plan?
- Tabletop exercise
- A full operational exercise
- A simulation
- Functional test
50. What is an example of a business continuity plan?
- Ensuring critical systems are online during a disaster
- Identifying and analyzing potential events that may negatively impact an organization’s assets
- Identifying critical business processes, resources and relationships between systems by focusing on the consequences of an interruption to critical business functions
- Getting critical systems to another location while the repair of the original facility is underway
51. What is a function of a protocol analyzer?
- monitor network systems for malicious activity or policy violations
- provide real time reporting and long-term analysis of security events
- analyze the value and contents of the protocol fields of captured packets
- permit or deny traffic based on Layer 3 and Layer 4 protocol information
52. A user wants to store data where it is accessible from any computer with internet access. What storage technology meets the needs of the user?
- cloud
- NAS
- RAID
- DAS
53. An organization is implementing security requirements for teleworkers to access the corporate network. What are two examples of technical control for the implementation? (Choose two.)
- Install and configure a VPN appliance.
- Implement smart card usage.
- Move the data center to cloud.
- Enable multi-factor authentication.
- Ask teleworkers to review and sign off on an access control policy.
54. An online store has set a control objective to maintain the highest level of website availability. Which two possible control mechanisms should the online store implement? (Choose two.)
- Configure the web server with the latest CPU product.
- Require the highest internet connection bandwidth from the ISP.
- Ensure that the web server contains the maximum local storage space.
- Implement a server cluster for web services.
- Deploy web services on multiple cloud service providers.
55. Refer to the exhibit. A specialist in the information security team is reviewing the Webroot threat report 2020. Based on the findings in the report, what is a technique used by ransomware attackers that results in making it more difficult for legal teams to track their activities?

Junior Cybersecurity Analyst Career Path Exam Q55
- using an advanced encryption algorithm
- employing cryptocurrency
- using fake antivirus software
- requiring the victim to click a link to clear their system
56. Why does an organization need to conform to a standard data governance framework?
- to provide guidelines on how to select a service provider for cloud data storage
- to ensure that an organization can manage data in a consistent manner and ensure that data is trustworthy
- to define security controls to protect data owned by the organization
- to define the data model for the online applications used by the organization
57. Which two business and technical challenges does implementing virtualization within a data center help businesses to overcome? (Choose two.)
- virus and spyware attacks
- operating system license requirements
- server hardware needs
- power and air conditioning
- physical footprint
58. Match the alert classification to the description.
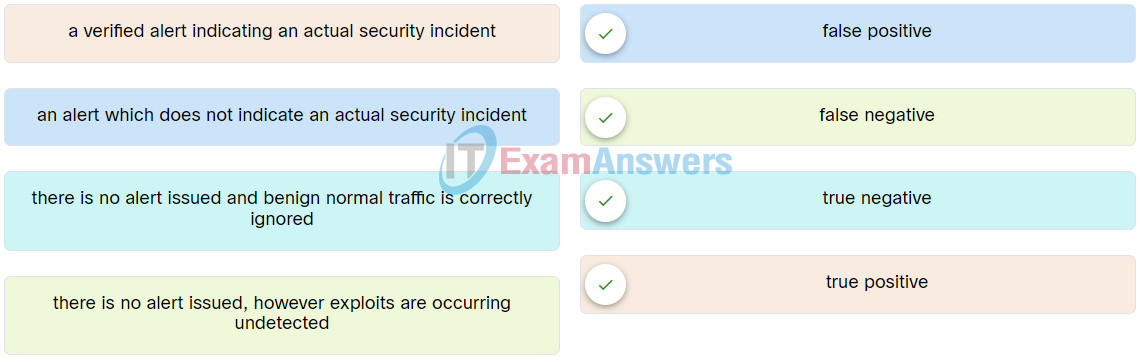
59. What type of activity occurs during the deployment phase of the asset lifecycle?
- Modifications and maintenance are performed on an asset.
- An asset is added to the inventory of the organization.
- An asset is moved from inventory to in-use.
- Upgrades, patches, and new licenses are applied to an asset.
60. Refer to the exhibit. The wireless router firewall is configured as shown. What action will be taken when packets that originate from the internet and have a destination IP address of 192.168.1.101 are received by the firewall?
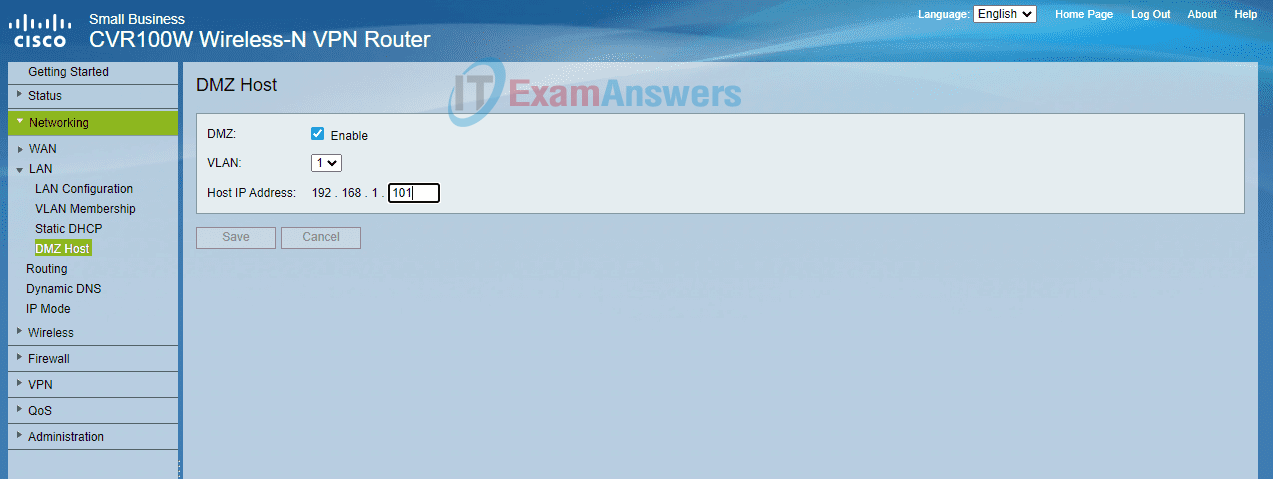
- Only inbound traffic that is addressed to HTTP ports is forwarded to the server.
- The detected inbound traffic is forwarded to the switch port where the server is connected.
- All devices on the network receive the traffic, but only the server is permitted to respond.
- Any traffic that is not in response to requests originating from the server is dropped.
61. What names are given to a database where all cryptocurrency transactions are recorded? (Choose two.)
- Table
- Blockchain
- Spreadsheet
- Ledger
62. What are the two important components of a public key infrastructure (PKI) used in network security? (Choose two.)
- pre-shared key generation
- digital certificates
- intrusion prevention system
- symmetric encryption algorithms
- certificate authority
63. You are asked for advice on how to best prevent unauthorized hosts from accessing the home network of employees. Which of the following security measures do you think would be most effective?
- Implementing a VLAN
- Implementing a firewall
- Implementing a RAID
- Implementing instruction detection systems
64. A SOHO company is planning to use public cloud computing for hosting an online ordering application. The company is evaluating options to prevent sensitive data loss from cloud storage. What two countermeasures could be implemented to address the issue? (Choose two.)
- Deploy the application and data across multiple zones.
- Implement multi-factor authentication processes.
- Install antivirus and host-based intrusion detection software on VMs in the cloud.
- Develop and implement compliance policies.
- Perform a daily backup of data.
65. Which type of DNS attack involves a threat actor creating multiple bogus sub-domains under a legitimate parent domain?
- DNS Tunneling attacks
- DNS Stealth attacks
- DNS Domain Shadowing attacks
- DNS Open Resolver attacks
66. A network technician is assigned the task of hardening a Cisco switch before placing it into the LAN. The technician configures and encrypts the user and privilege mode passwords, creates a new management VLAN, and verifies that the IOS is up-to-date. What action should the technician take to ensure that remote access to the system is secure during transmission?
- Restrict VTY ports to only accept SSH connections.
- Configure local users and encrypt their passwords.
- Shutdown all unused Ethernet ports on the switch.
- Configure port security on all Ethernet ports.
67. A network security technician is configuring account settings on Windows laptops that will be used by employees from their homes. Which Local Security Policy setting can prevent or discourage brute-force password attacks?
- User Rights Assignment
- Account Lockout Policy
- Software Restriction Policies
- Password Policy
68. A cloud service company provides web service to clients. The company is assessing the risk of service disruption due to hardware failure. The company decides to add another data center in a different building. Which risk management action level is the company implementing?
- mitigation
- transfer
- avoidance
- accept
69. What is the purpose of penetration testing?
- It involves hacking a website, network or server with the permission of the respective organization.
- It fixes issues found by a vulnerability scanner.
- It is used to audit enterprise patch management.
- It is used to passively scan OS attack platforms.
70. What tool is used to lure an attacker so that an administrator can capture, log and analyze the behavior of the attack?
- IDS
- Honeypot
- NetFlow
- Nmap
71. Match the security control type to the appropriate description.
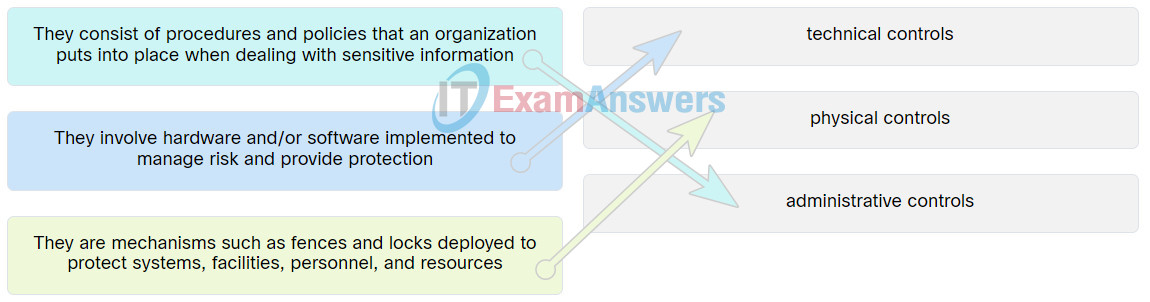
72. The results of an audit on cybersecurity practices revealed that several company servers were not updated with the latest patches. The audit also revealed that several user accounts had escalated privileges and were allowed unauthorized network resource access. Which two security policies should be enforced to address these issues? (Choose two.)
- data policy
- organizational policy
- network maintainance policy
- credential policy
- identification and authentication policy
73. What type of cipher encrypts plaintext one byte or one bit at a time?
- block
- enigma
- elliptical
- stream
- hash
74. A network technician is preparing a number of laptops to be loaned to employees while they are traveling. These employees will not be logging into the corporate directory server when they are away from the office. Which type of software should be configured on the laptops in order to filter incoming and outgoing network connections?
- host-based firewall
- virus and malware scanner
- host intrusion detection system
- IOS stateful firewall
75. The administrator of a Linux server uses the chmod 777 /usr/phones.txt command to assign permissions to a file that contains the company phone directory. What permissions are assigned with this command?
- All users have read, write and execute permissions to the file.
- Only members of the administrators group can read, write, and execute the file.
- No users have write permission to the file, other than root.
- All users have read permission to the file, but not write or execute.
76. Which control should an organization use to restore a system back to its normal state?
- Compensative
- Corrective
- Preventive
- Detective
77. A network administrator notices that several company wireless access points are using WEP for encryption and authentication. The administrator needs to update the encryption and authentication configurations. Which security policy would address the process of updating AP configurations?
- credential policy
- network maintenance policy
- identification and authentication policy
- organizational policy
78. An organization needs to implement a solution that would enable them to determine the order of security events occurring on the network. What technology should be implemented?
- NAT
- DHCP
- SNMP
- NTP
79. What statement describes a function that the Diffie-Hellman algorithm provides to IPsec VPNs?
- It is used to identify the source of data that is sent through the VPN.
- It is an encryption algorithm that is used to ensure that data cannot be intercepted.
- It ensures that data has not been changed between the sender and receiver.
- It allows two parties to establish a shared secret key over an unsecured channel.
80. A small company uses a public cloud service provider to host an online store. The online store uses a web application as the front end and a database as the backend. When a customer places an order in the web form, the request is then sent to the database to check the inventory, current price, and customer information thereby completing the order. The IT manager is learning that threat attackers may launch attacks by injecting malformed data into the web application. What is a security coding technique that the company can use to minimize such attacks?
- multi-factor authentication
- obfuscation
- input validation
- encryption
81. What security tool allows an organization to collect data about security threats from various sources, and respond to low-level events without human intervention?
- SOAR
- Nessus
- GFI LanGaurd
- SIEM
82. Which parameter is used to identify applications when a user sends a service request to a remote server?
- destination port number
- TCP sequence number
- server IP address
- source port number
83. A network technician is charged with researching and collecting information regarding recent cybersecurity incidents. The technician decides to start with web sites that are opensource intelligence (OSINT). Which two statements describes OSINT types of web sites? (Choose two.)
- Their operations are in compliance with government regulations and policies.
- Most of them provide free access to their database.
- They are all run by government agencies.
- They collect information that is available to the general public.
- They usually require user registration and a small monthly fee.
84. What are three actions taken in the Detection & Analysis phase of the NIST Incident Response Life Cycle? (Choose three.)
- The CSIRT is created and trained.
- The effectiveness of the incident handling process is reviewed and any necessary hardening for existing security controls and practices is identified.
- The type of incident and the extent of the effects are determined.
- The appropriate stakeholders and outside parties are notified so that all who need to be involved can play their role.
- The incident is contained and subsequent actions are determined.
- The CSIRT performs an initial analysis to determine the incident’s scope, such as which networks, systems, or applications are affected, who or what originated the incident, and how the incident is occurring.
85. Refer to the exhibit. What type of traffic will the policy be applied to when the router is configured with the class-map and policy-map shown?
class-map type inspect match-all INTERNAL-WEB match protocol https match access-group 101 ! policy-map type inspect SEC-INT-WEB class type inspect INTERNAL-WEB inspect ! access-list 101 permit tcp 192.168.10.0 0.0.0.255 host 192.168.100.10
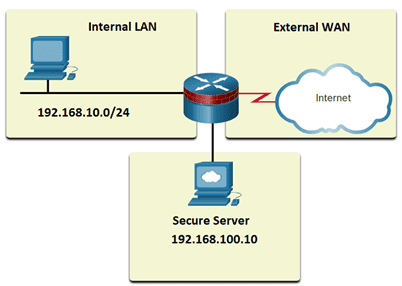
- only HTTPS traffic sourced from any internal or external source address destined for the secure server
- only HTTPS traffic sourced from the internal LAN IP address range destined for the secure server
- all traffic that is using either the HTTP protocol or is sourced from the internal LAN IP address range
- all traffic from the internal LAN IP address range to the secure server using any TCP protocol
86. What key considerations does a business impact analysis (BIA) examine? Choose four correct answers
- Recovery time objectives (RTOs)
- Recovery point objectives (RPOs)
- Recovery point times (RPTs)
- Mean time between objectives (RBOs)
- Mean time between failures (MTBF)
- Mean time to repair (MTTR)

What key considerations does a business impact analysis (BIA) examine? Choose four correct answers
Recovery time objectives (RTOs)
Recovery point objectives (RPOs)
Recovery point times (RPTs)
Mean time between objectives (RBOs)
Mean time between failures (MTBF)
Mean time to repair (MTTR)
I added. Thank you.