1. Match the commands to the task.
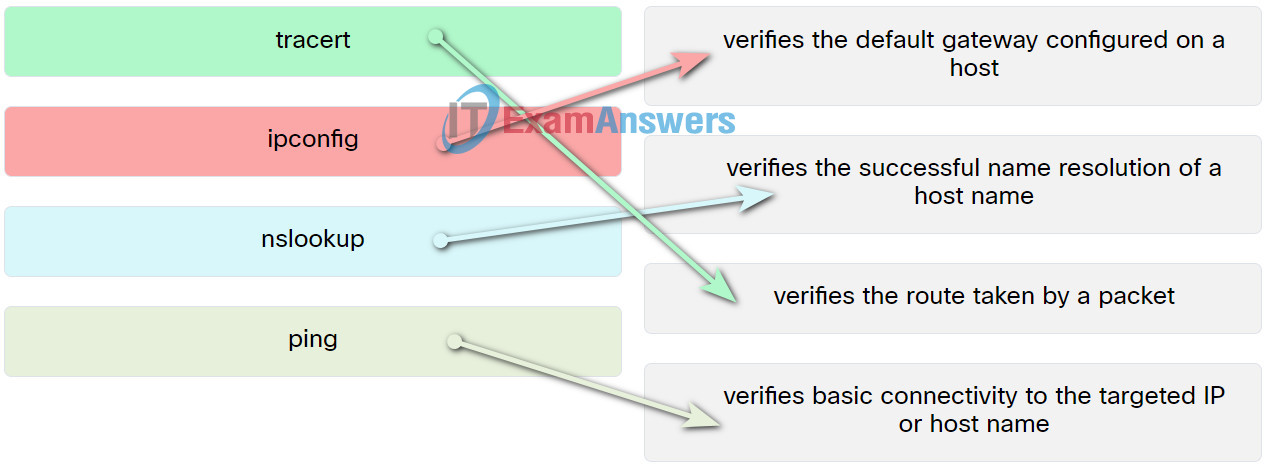
- ping —> verifies basic connectivity to the targeted IP or host name
- nslookup —> verifies the successful name resolution of a host name
- tracert —> verifies the route taken by a packet
- ipconfig —> verifies the default gateway configured on a host
2. In which folder are application files for 32-bit programs typically located on a computer that is running a 64-bit edition of Windows 7?
- C:\Application Data
- C:\Program Files
- C:\Users
- C:\Program Files (x86)
3. A user notices that some of the programs that are installed before upgrading to Windows 7 no longer function properly. What can the user do to fix this problem?
- Change the file system to FAT16.
- Lower the UAC setting in the Change User Account Control settings dialog box of the User Accounts control.
- Reinstall the programs in Compatibility Mode.
- Update the driver for the graphics card.
4. A corporation has expanded to include multiple remote offices around the globe. Which technology should be used to allow the remote offices to communicate and share network resources privately?
- Remote Desktop
- Remote Assistance
- administrative share
- VPN
5. Why would an administrator use Windows Remote Desktop and Windows Remote Assistant?
- to provide secure remote access to resources on another network
- to connect to a remote computer over the network to control its applications and data
- to enable sharing of files and presentations with a group of users over the Internet
- to connect to an enterprise network across an unsecured connection and act as a local client of that network
6. How many Libraries are created for each user by default on a new Windows 10 installation?
- 6
- 4
- 5
- 2
7. Which two issues are likely to cause BSOD errors? (Choose two.)
- power supply failure
- lack of antivirus software
- device driver errors
- RAM failing
- out-of-date browser
8. A user wants to configure a password on a Windows 10 PC when the PC is woken from hibernation. Where can the user configure this?
- Control Panel, Power Options
- Settings, Privacy
- Settings, Accounts
- Control Panel, User Accounts
9. Which Windows utility can be used to schedule a regular backup for preventive maintenance?
- Windows Task Manager
- Disk Cleanup
- System Restore
- Windows Task Scheduler
10. Which TCP port number would be used for remotely connecting to a network switch and configuring it via an unencrypted connection?
- 20
- 22
- 3389
- 443
11. What are two file attributes in the Windows environment? (Choose two.)
- read-only
- archive
- security
- general
- details
12. A technician notices that an application is not responding to commands and that the computer seems to respond slowly when applications are opened. What is the best administrative tool to force the release of system resources from the unresponsive application?
- Event Viewer
- Add or Remove Programs
- System Restore
- Task Manager
13. What is true about restore points?
- Restore points should always be created before making changes to a system.
- Restore points back up personal data files.
- Once System Restore is used to restore a system, the change is irreversible.
- Restore points recover corrupted or deleted data files.
14. After solving a problem on a computer, a technician checks the event log to ensure that there are no new error messages. At which step of the troubleshooting process is this action taking place?
- Determine an exact cause.
- Establish a theory of probable cause.
- Verify the solution and full system functionality.
- Document the findings.
15. A user logs into Active Directory on a workstation and the user home directory does not redirect to a network share on a file server. A technician suspects that the group policy setting is incorrect. Which command can the technician use to verify the group policy settings?
- rstrui
- tasklist
- runas
- gpupdate
- gpresult
16. A help desk technician is talking to a user to clarify a technical problem that the user is having. What are two examples of open-ended questions that the technician might use to help determine the issue? (Choose two.)
- What updates have you performed lately?
- Can you boot the operating system?
- Has anyone else used the computer recently?
- Can you boot up in safe mode?
- What happens when you try to access your files?
17. What are three common causes of operating systems problems? (Choose three.)
- a corrupted registry
- loose cable connections
- virus infection
- CMOS battery problem
- incorrect IP addressing information
- failed service pack installation
18. A technician is designing a hardware preventive maintenance plan for a company. Which strategy should be included in the plan?
- Only clean equipment that is requested by the customer.
- Avoid performing maintenance operations on plug and play devices that are controlled by the operating system.
- Schedule and document routine maintenance tasks.
- Omit performing maintenance operations on components until the equipment malfunctions.
19. Which utility would be used to find the default gateway configured on a host?
- ipconfig
- ping
- nslookup
- tracert
