CCNP ENCOR (350-401) Certification Practice Exam
1. Which two statements are true about NTP servers in an enterprise network? (Choose two.)
- NTP servers at stratum 1 are directly connected to an authoritative time source.
- All NTP servers synchronize directly to a stratum 1 time source.
- NTP servers control the mean time between failures (MTBF) for key network devices.
- There can only be one NTP server on an enterprise network.
- NTP servers ensure an accurate time stamp on logging and debugging information.
2. The command ntp server 10.1.1.1 is issued on a router. What impact does this command have?
- identifies the server on which to store backup configurations
- determines which server to send system log files to
- ensures that all logging will have a time stamp associated with it
- synchronizes the system clock with the time source with IP address 10.1.1.1
3. A network engineer has to decide between a Layer 2 Access Layer (STP-based) and a Layer 3 Access Layer (Routed access) campus design option. Which statement must be considered for a decision to be made?
- The STP based option does not require FHRP, whereas the Routed access option does.
- The Routed access option offers easier troubleshooting than the STP-based option.
- The STP based access option supports spanning VLANs across multiple access switches, whereas the Routed access option does not.
- The Routed access option is the best cost-effective solution.
4. Which three functions are performed at the distribution layer of the hierarchical network model? (Choose three.)
- isolates network problems to prevent them from affecting the core layer
- provides a connection point for separate local networks
- forwards traffic that is destined for other networks
- allows end users to access the local network
- transports large amounts of data between different geographic sites
- forwards traffic to other hosts on the same logical network
5. Which SD-Access feature uses telemetry to enable proactive prediction of network-related and security-related risks.
- policy enforcement
- network assurance and analytics
- network virtualization
- network automation
6. Which function is provided by the Cisco SD-Access Architecture management layer?
- It delivers data packets to and from the network devices participating in SD-Access.
- It interconnects all of the network devices, forming a fabric of interconnected nodes.
- It presents all information to the user on a centralized dashboard.
- It provides all of the management subsystems for the management layer.
7. Which SD-WAN solution architecture component authenticates the vSmart controllers and SD-WAN routers and facilitates their ability to join the network?
- vManage Network Management System
- vAnalytics
- vBond orchestrator
- vSmart controller
8. What two factors are used to achieve end-to-end QoS in the DiffServ model? (Choose two.)
- DSCP
- PHB
- PCP
- DEI
- VLAN ID
9. What QoS category level is recommended as the best to be configured on a Cisco WLC for VoIP traffic?
- gold
- bronze
- silver
- platinum
10. What are the two main components of Cisco Express Forwarding (CEF)? (Choose two.)
- adjacency tables
- routing tables
- MAC-address tables
- forwarding information base (FIB)
- ARP tables
11. What is used to pre-populate the adjacency table on Cisco devices that use CEF to process packets?
- the ARP table
- the routing table
- the FIB
- the DSP
12. Which technology is part of the Cisco ENFV and provides centralized and consistent network policies across enterprise branch offices?
- Cisco ENCS
- Cisco UCS
- Cisco DNA center
- Cisco ISE
13. What is an I/O technology that allows multiple VNFs to share the same pNIC?
- PCI Passthrough
- Open vSwitch
- SR-IOV
- OVS-DPDK
14. Which two are functions of LISP? (Choose two.)
- It is an overlay tunneling technology.
- It performs load balancing of SD-WAN routers across vSmart controllers.
- It is an architecture created to address routing scalability problems.
- It provides a permanent control plane connection over a DTLS tunnel.
- It authenticates vSmart controllers and SD-WAN routers.
15. Match the VNF role with its description. (Not all options are used.)

- EMS : responsible for the functional management of the VNFs
- VIM : responsible for hardware resources and virtualized resources
- BSS : operates in tandem with OSS to improve overall customer experiance
16. Which vitualization component allows communication between VMs within a virtual server?
- container engine
- vSwitch
- pNIC
- hypervisor
17. A teacher is explaining the concept of virtual switch (vSwitch) to students in a classroom. What explanation accurately describe a vSwitch?
- A vSwitch is a software-based Layer 3 switch that operates like a physical switch.
- Multiple vSwitches can be created under a virtualized server, allowing network traffic to flow directly from one vSwitch to another within the same host.
- A vSwitch is a cluster of switches forming a virtual switching system (VSS).
- A vSwitch enables VMs to communicate with external physical networks through physical nework interface cards.
18. What are two characteristics of virtual routing that are different from traditional routing? (Choose two.)
- VRF allows for overlapping IP address ranges.
- VRF requires the use of the BGP routing protocol.
- VRF requires creating subinterfaces if VRF is to be enabled.
- Each VRF instance has its own routing table.
- VRF takes advantages of Layer 2 technologies such as spanning tree.
19. What is a key difference between a virtual machine and a virtualized container?
- A virtual machine starts much faster than a virtualized container does.
- A virtual machine uses physical memory to run and a virtualized container uses virtualized memory.
- A virtual machine requires a type 1 hypervisor and a virtualized container requires a type 2 hypervisor.
- A virtual machine contains its own OS and a virtualized container does not.
20. A network engineer wants to increase the overall efficiency and cost-effectiveness of a server by maximizing the use of available resources through virtualization. The engineer is considering VMs or containers. What is the difference between these two types of virtualization?
- VMs take minutes to start, whereas containers take seconds to start.
- VMs do not include a guest OS, whereas containers do.
- VMs require a type 1 hypervisor directly on the system hardware, whereas containers require a type 2 hypervisor.
- VMs share the same operating system, whereas each container requires a dedicated operating system.
21. Refer to the exhibit. A network administrator is verifying the bridge ID and the status of this switch in the STP election. Which statement is correct based on the command output?
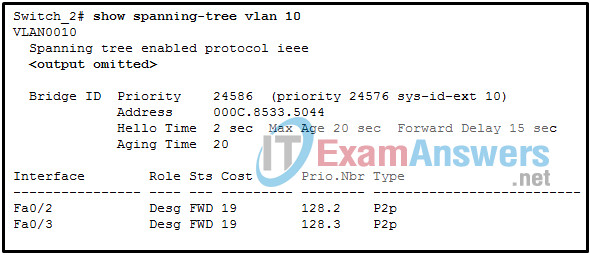
- The bridge priority of Switch_2 has been lowered to a predefined value to become the backup root bridge.
- The bridge priority of Switch_2 has been lowered to a predefined value to become the root bridge.
- The STP instance on Switch_2 is using the default STP priority and the election is based on Switch_2 MAC address.
- The STP instance on Switch_2 is failing due to no ports being blocked and all switches believing they are the root.
22. Which three describe characteristics of a virtual machine? (Choose three.)
- it is an isolated environment for applications
- it includes a guest OS
- it shares the underlying resources of the host OS
- it leverages the kernel of the host OS for quick starts
- it is a virtualized physical server
- it requires a hypervisor
23. What is a characteristic of the PortFast feature?
- PortFast enables a Cisco Catalyst switch to move a port into blocking state when an attached workstation link comes up.
- A trunk port can be configured with PortFast if it connects to a hypervisor host.
- PortFast can only be used for STP host ports.
- PortFast prevents alternative ports from becoming designated ports.
24. Which three spanning tree protocols are industry standards? (Choose three.)
- PVST+
- MSTP
- Rapid PVST+
- STP
- MST
- RSTP
25. Refer to the exhibit. A network administrator issues the show spanning-tree mst configuration command to verify the MST configuration. How many VLANs are assigned to IST?
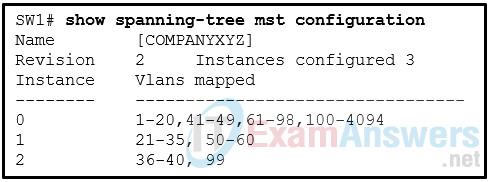
- 4060
- 4062
- 4064
- 4094
26. Refer to the exhibit. A network administrator is verifying the MST configuration on the switch SW2 with the command:
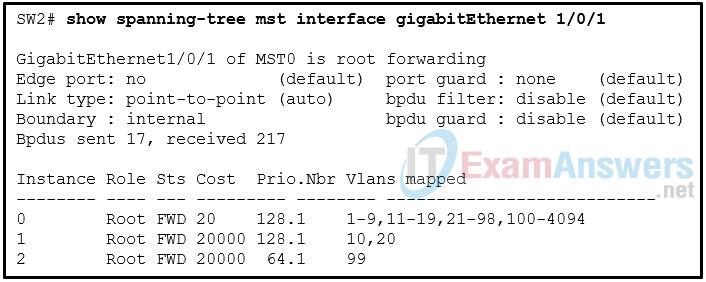
SW2# show spanning-tree mst interface gigabitEthernet 1/0/1
Which three conclusions can be drawn based on the output? (Choose three.)
- The priority value of the gigbitEthernet 1/0/1 port is adjusted for the instance 2.
- The gigbitEthernet 1/0/1 port does not connect to another switch that is out of the region.
- The gigbitEthernet 1/0/1 port connects to the internet through a WAN connection.
- The cost value of the gigbitEthernet 1/0/1 port is adjusted for IST.
- SW2 does not support the BPDU guard feature.
- SW2 does not support the BPDU filter feature.
27. What are two drawbacks to turning spanning tree off and having multiple paths through the Layer 2 switch network? (Choose two.)
- Port security shuts down all of the ports that have attached devices.
- Broadcast frames are transmitted indefinitely.
- The MAC address table becomes unstable.
- Port security becomes unstable.
- The switch acts like a hub.
28. Network users complain that the network is running very slowly. Upon investigation, a network technician discovers 100% link utilization on all the network devices. Also, numerous syslog messages are being generated that note continuous MAC address relearning. What is the most likely cause of the problem?
- The routing protocol has been misconfigured and a routing loop is evident.
- A Layer 2 STP looping condition is present.
- The dynamic routing protocol has not yet converged the network.
- An incorrect encapsulation has been configured on one of the trunks that connect a Layer 2 device to a Layer 3 device within the affected segment.
- Keepalives are expected but do not arrive.
29. Refer to the exhibit. SW1 is the root bridge and SW2 is the backup root bridge. An administrator wants to prevent SW4 and SW5 from ever becoming root bridges, but still allow SW2 to maintain connectivity to SW1 via SW3 if the link connecting SW1 to SW2 fails. On which two ports in this topology should the administrator configure root guard to accomplish this? (Choose two.)
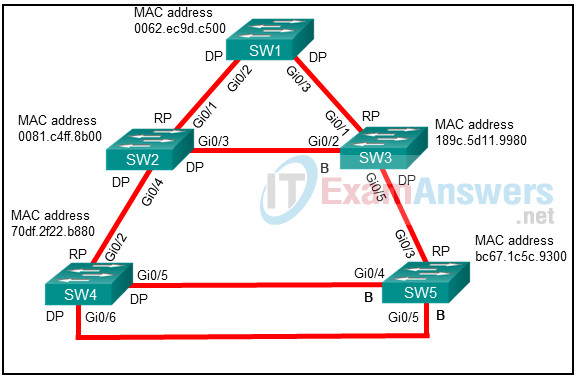
- SW5 Gi0/3 port toward SW3
- SW2 Gi0/4 port toward SW4
- SW3 Gi0/5 port toward SW5
- SW4 Gi0/6 port toward SW5
- SW4 Gi0/2 port toward SW2
30. Refer to the exhibit. A network administrator has connected two switches together using EtherChannel technology. If STP is running, what will be the end result?
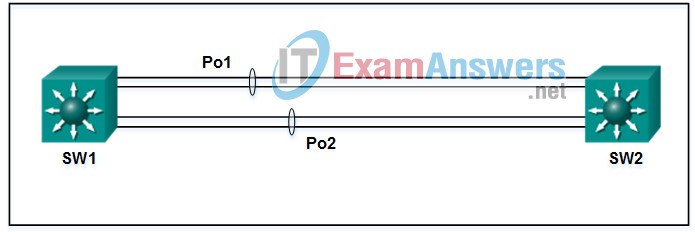
- The resulting loop will create a broadcast storm.
- The switches will load balance and utilize both EtherChannels to forward packets.
- Both port channels will shutdown.
- STP will block one of the redundant links.
31. A new switch is to be added to an existing network in a remote office. The network administrator does not want the technicians in the remote office to be able to add new VLANs to the switch, but the switch should receive VLAN updates from the VTP domain. Which two steps must be performed to configure VTP on the new switch to meet these conditions? (Choose two.)
- Enable VTP pruning.
- Configure all ports of both switches to access mode.
- Configure the existing VTP domain name on the new switch.
- Configure the new switch as a VTP client.
- Configure an IP address on the new switch.
32. An OSPF router is forming an adjacency with a neighbor and sends the neighbor an OSPF DBD packet describing the contents of its link-state database. During which OSPF neighbor state does the router send the packet?
- exchange
- 2-Way
- attempt
- loading
33. Which IPv6 address is used by OSPFv3 DR and BDR routers for sending link-state updates?
- FF02::2
- FF02::5
- FF02::6
- FF02::9
34. A network administrator is configuring the MST instance priority with the command spanning-tree mst 0 prioritypriority. Which two numbers can be used for the priority argument? (Choose two.)
- 2048
- 4096
- 6144
- 12288
- 18432
35. A network administrator is configuring MST on switch SW1 with the commands:
SW1(config)# spanning-tree mode mst SW1(config)# spanning-tree mst 12 root primary
What is the effect after the command is entered?
- The bridge priority on switch SW1 is set to 32768 for MST instance 12.
- The bridge priority on switch SW1 is set to 28672 for MST instance 12.
- The bridge priority on switch SW1 is set to 20480 for MST instance 12.
- The bridge priority on switch SW1 is set to 24576 for MST instance 12.
36. Refer to the exhibit. A network administrator in autonomous system 65100 has set up a dual-homed BGP connection with an ISP. The administrator would like to ensure that all traffic from the ISP enters the autonomous system through the router R1. Which BGP attribute can the administrator configure on routers R1 and R2 to accomplish this?
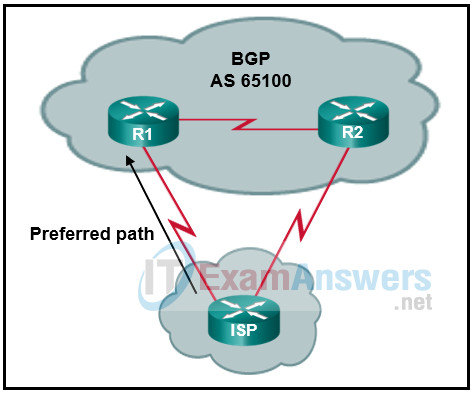
- next-hop
- weight
- aggregate
- multiple-exit discriminator
- local preference
37. A technician is configuring the channel on a wireless router to either 1, 6, or 11. What is the purpose of adjusting the channel?
- to avoid interference from nearby wireless devices
- to disable broadcasting of the SSID
- to enable different 802.11 standards
- to provide stronger security modes
38. Refer to the exhibit. The network administrator configures both switches as displayed. However, host C is unable to ping host D and host E is unable to ping host F. What action should the administrator take to enable this communication?
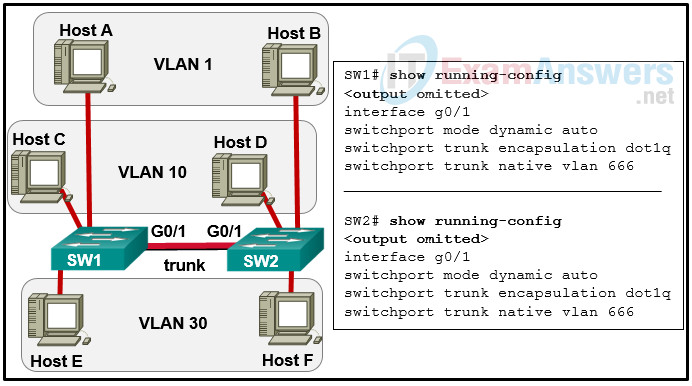
- Configure either trunk port in the dynamic desirable mode.
- Add the switchport nonegotiate command to the configuration of SW2.
- Remove the native VLAN from the trunk.
- Associate hosts A and B with VLAN 10 instead of VLAN 1.
- Include a router in the topology.
39. What is a function of IGMP snooping?
- updating static MAC entries on ports that should receive multicast traffic from certain sources or groups
- learning and maintaining multicast group memberships
- restricting multicast packets for IP multicast groups that have downstream receivers
- updating receiver applications to filter out unwanted traffic
40. Which OSPF packet type contains a summary of the link state database and is sent by an OSPF router as it forms an adjacency with a neighboring OSPF router?
- hello
- link-state ack
- link-state update
- database description
41. An administrator is configuring a pre-shared key for a WLAN environment. The administrator wants to protect the WLAN against any man-in-the-middle attacks occurring during the four-way handshake between the client and the AP. Which WPA3-Personal method will provide the best security?
- Diffie-Hellman method
- not authenticating against a server
- RSA key
- SAE method
42. Which OSPF network type includes the DR/BDR field in OSPF Hello packets and uses a 10 seconds hello and 40 seconds dead interval timer?
- point-to-point
- point-to-multipoint
- broadcast
- nonbroadcast
43. What are two advantages of using multiple OSPF areas? (Choose two.)
- They allow for unequal cost load balancing.
- The link-state database is a more manageable size.
- They permit configuration of route summarization.
- DR/BDR elections are not required.
- All areas share an identical link-state database.
44. Which LSA type is sent by an OSPF DR to advertise attached multiaccess network segments?
- type 2
- type 3
- type 4
- type 5
45. What are two characteristics of OSPF type 3 LSAs? (Choose two.)
- They are originated by DRs and BDRs.
- They are originated by ABRs.
- They advertise specific networks that are external to the OSPF process
- They advertise network prefixes from other areas.
- They are contained within the originating area.
46. A company is deploying a wireless network using lightweight APs. What is an advantage of Layer 2 roaming compared with Layer 3 roaming when wireless clients roam around the campus?
- The process of Layer 2 roaming is faster.
- A wireless client can keep the same IP address.
- The roaming does not involve a WLC.
- DHCP service is not required.
47. How is ERSPAN used for troubleshooting?
- to capture network traffic on a remote switch and send a copy of it to the local switch through Layer 2 toward a local port attached to a traffic analyzer
- to capture network traffic on a switch port and send it to a VLAN
- to capture network traffic on a remote device and send it to the local system through Layer 3 toward a local port attached to a traffic analyzer
- to capture local network traffic on a switch and send a copy of it to a local port attached to a traffic analyzer
48. Refer to the exhibit. Which zone-member security command keyword will complete the ZBFW configuration when applied to the GigabitEthernet 0/2 interface?
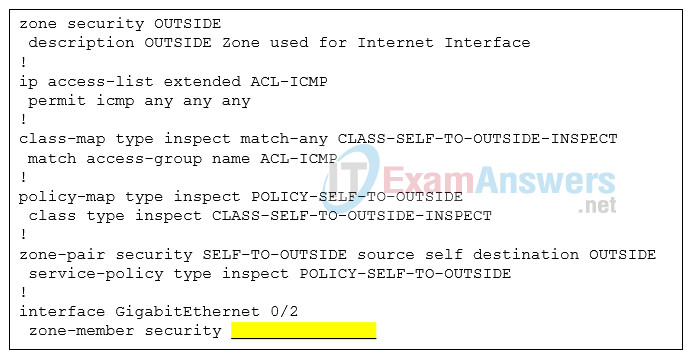
- POLICY-SELF-TO-OUTSIDE
- CLASS-SELF-TO-OUTSIDE-INSPECT
- ACL-ICMP
- OUTSIDE
49. What is a limitation of PACLs?
- They do not support outbound filtering.
- They support only extended ACLs.
- They can filter only Layer 2 traffic.
- They support only numbered ACLs.
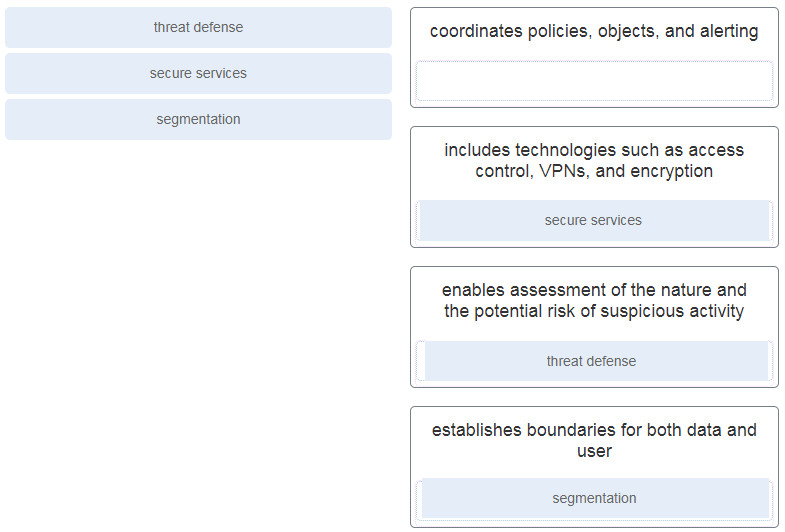
50. Match the Cisco SAFE security concepts with the description. (Not all options are used.)
51. An organization is deploying a network access security policy for end point devices to access the campus network. The IT department has configured multiple network access control mechanisms, such as 802.1x, WebAuth, and MAB. WebAuth and MAB are configured as fallbacks to 802.1x. What is the authentication process when an employee brings a laptop and connects to a switch on the network?
- The switch will initiate authentication by WebAuth protocol. If it fails, the switch will try 802.1x next, then MAB.
- The switch will initiate authentication by 802.1x protocol. If it fails, the switch will try WebAuth next, then MAB.
- The switch will initiate authentication by 802.1x protocol. If it fails, the switch will try MAB next, then WebAuth.
- The switch will initiate authentication by MAB protocol. If it fails, the switch will try 802.1x next, then WebAuth.
52. Refer to the exhibit. BGP sessions are established between all routers. RTC receives route updates for network 209.165.200.224/27 from autonomous system 300 with the weight attribute set to 3000. RTB also learns about network 209.165.200.224/27 from autonomous system 200 with a weight of 2000. Which router will be used by RTA as a next hop to reach this network?
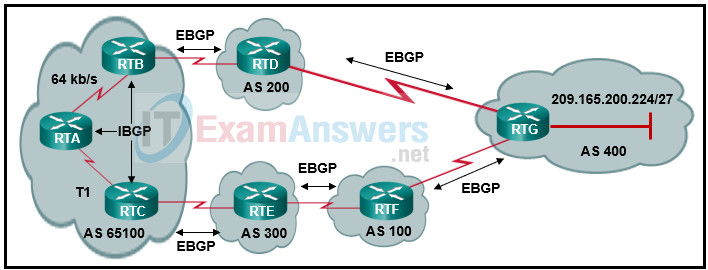
- RTC because of the T1 link
- RTB because of the slow 64 kbps link
- RTB because of the shortest AS_Path
- RTC because of the highest weight
- RTC because of the longest AS_Path
- RTB because of the lowest weight
53. A company plans to deploy the Postman application as a tool to manage network devices. Which two security related best practices should be considered? (Choose two.)
- An SSH connection should be used to connect to the Postman application.
- User accesses must be authenticated to make API calls.
- A dedicated instance for development should be used to ensure that device configurations are valid.
- AAA service should be deployed for user authorization.
- ACLs should be used to verify and filter different types of RUSTFul API calls.
54. Which tool can be used to identify wireless RF signal strength and interference?
- WLAN controller
- packet analyzer
- packet sniffer
- spectrum analyzer
55. When JSON data format is being used, what characters are used to hold objects?
- double braces { }
- double brackets [ ]
- double quotations ” “
- double colons : :
56. What is a characteristic of PIM dense mode?
- It relies on a unicast routing protocol to perform Reverse Path Check.
- It is not recommended for production environments.
- Prunes are sent out on all RPF interfaces.
- Prunes are not sent out of non-RPF interfaces.
57. Which automation tool is agentless and uses playbooks to deploy configuration changes or retrieve information from hosts within a network?
- Ansible
- Puppet
- SaltStack
- Chef
58. A network administrator is configuring the MST instance priority with the command spanning-tree mst 0 priority priority . Which two numbers can be used for the priority argument? (Choose two.)
- 2048
- 4096
- 6144
- 12288
- 18432
59. What is a requirement to configure a trunking EtherChannel between two switches?
- The participating interfaces must be on the same module on a switch.
- The allowed range of VLANs must be the same on both switches.
- The participating interfaces must be assigned the same VLAN number on both switches.
- The participating interfaces must be physically contiguous on a switch.
60. Which three packet types are exchanged between EIGRP neighbors? (Choose three.)
- LSU
- database descriptor
- link-state ACK
- hello
- query
- request
61. Refer to the exhibit. Which two statements describe the results of entering these commands? (Choose two.)
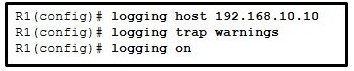
- R1 will send system messages of levels 0 (emergencies) to level 4 (warnings) to a server.
- The syslog server has the IPv4 address 192.168.10.10.
- R1 will not send critical system messages to the server until the command debug all is entered.
- R1 will reset all the warnings to clear the log.
- R1 will output the system messages to the local RAM.
62. Refer to the exhibit. The total number of packet flows is not consistent with what is expected by the network administrator. The results show only half of the flows that are typically captured for the interface. Pings between the router and the collector are successful. What is the reason for the unexpected results?
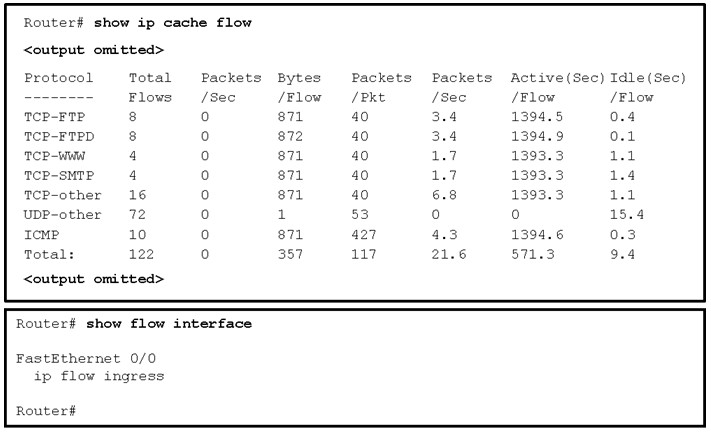
- Interface Fa0/0 is not configured as the source of the packets sent to the collector.
- The interface is shutdown.
- The Netflow collector IP address and UDP port number are not configured on the router.
- The router is not configured to monitor outgoing packets on the interface.
63. Refer to the exhibit. Based on the output generated by the show monitor session 1 command, how will SPAN operate on the switch?
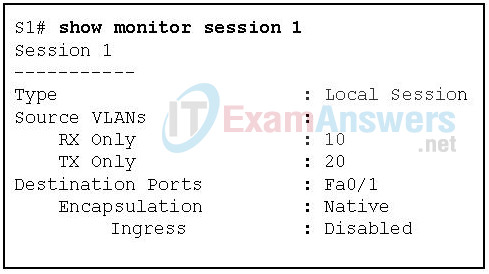
- All traffic transmitted from VLAN 10 or received on VLAN 20 is forwarded to FastEthernet 0/1.
- Native VLAN traffic received on VLAN 10 or transmitted from VLAN 20 is forwarded to FastEthernet 0/1.
- Native VLAN traffic transmitted from VLAN 10 or received on VLAN 20 is forwarded to FastEthernet 0/1.
- All traffic received on VLAN 10 or transmitted from VLAN 20 is forwarded to FastEthernet 0/1.
64. Which two statements describe items to be considered in configuring NetFlow? (Choose two.)
- NetFlow consumes additional memory.
- Netflow requires UDP port 514 for notification messages.
- NetFlow can only be used if all devices on the network support it.
- Netflow requires both management and agent software.
- Netflow can only be used in a unidirectional flow.
65. Which three statements describe SPAN and RSPAN? (Choose three.)
- SPAN can send a copy of traffic to a port on another switch.
- SPAN can be configured to send a copy of traffic to a destination port on the same switch.
- RSPAN is required to copy traffic on a source VLAN to a destination port on the same switch.
- RSPAN can be used to forward traffic to reach an IPS that is analyzing traffic for malicious behavior.
- RSPAN is required for syslog and SNMP implementation.
- SPAN can copy traffic on a source port or source VLAN to a destination port on the same switch.
66. Refer to the exhibit. A network administrator is configuring BGP on the router RT1. Which command set will allow RT1 to establish a neighbor relationship with RT2?
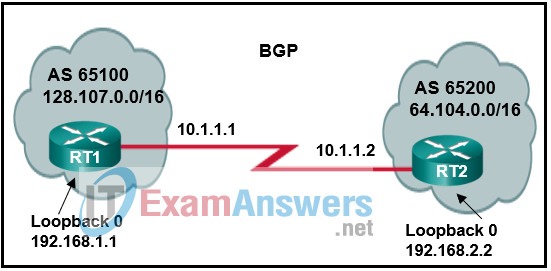
RT1(config)# router bgp 65100
RT1(config-router)# network 128.107.0.0 mask 255.255.0.0
RT1(config-router)# neighbor 10.1.1.1 remote-as 65200
RT1(config)# router bgp 65100
RT1(config-router)# network 128.107.0.0 mask 255.255.0.0
RT1(config-router)# neighbor 192.168.2.2 remote-as 65200
RT1(config)# router bgp 65100
RT1(config-router)# network 128.107.0.0 mask 255.255.0.0
RT1(config-router)# neighbor 10.1.1.2 remote-as 65200
RT1(config)# router bgp 65200
RT1(config-router)# network 64.104.0.0 mask 255.255.0.0
RT1(config-router)# neighbor 10.1.1.2 remote-as 65100
67. A large shopping mall is planning to deploy a wireless network for customers. The network will use a lightweight AP topology. The network designers are considering the roaming by wireless clients. Which statement describes a difference between Layer 2 roaming and Layer 3 roaming?
- Layer 2 roaming occurs between two APs configured with the same VLAN and IP subnet, whereas Layer 3 roaming occurs between two APs configured with different VLANs and IP subnets.
- Layer 2 roaming does not require the client to contact a DHCP server, whereas Layer 3 roaming requires the client to contact a DHCP server.
- Layer 2 roaming does not require communicating to a WLC through CAPWAP, whereas Layer 3 roaming does.
- Layer 2 roaming occurs between two APs that are bound to the same WLC, whereas Layer 3 roaming occurs between two APs that are bound to different WLCs.
68. Which two types of probes can be configured to monitor traffic by IP SLA within a network environment? (Choose two.)
- voice quality scores
- website upload time
- SNMP traps
- packet loss
- syslog messages
69. What is the function of the Diffie-Hellman algorithm within the IPsec framework?
- provides strong data encryption
- guarantees message integrity
- allows peers to exchange shared keys
- provides authentication
70. Refer to the exhibit. Which IP address would be configured on the tunnel interface of the destination router?
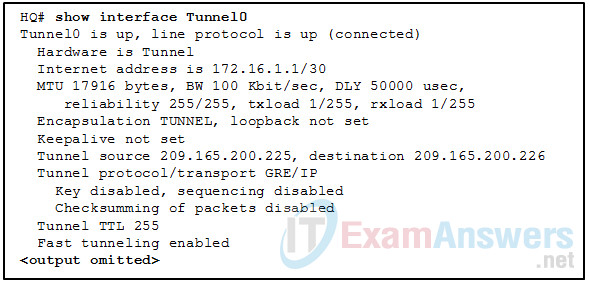
- 209.165.200.226
- 172.16.1.1
- 172.16.1.2
- 209.165.200.225
71. What is the purpose of the generic routing encapsulation tunneling protocol?
- to provide fixed flow-control mechanisms with IP tunneling between remote sites
- to support basic unencrypted IP tunneling using multivendor routers between remote sites
- to manage the transportation of IP multicast and multiprotocol traffic between remote sites
- to provide packet level encryption of IP traffic between remote sites
72. Which three services are critical functions of the IPsec service? (Choose three.)
- accounting
- data integrity
- speed
- authentication
- authorization
- confidentiality
73. Which three functions are provided by the syslog logging service? (Choose three.)
- gathering logging information
- authenticating and encrypting data sent over the network
- retaining captured messages on the router when a router is rebooted
- specifying where captured information is stored
- distinguishing between information to be captured and information to be ignored
- setting the size of the logging buffer
74. What are two operational characteristics of the ZBFW default zone? (Choose two.)
- By default, interfaces in this zone are permitted to communicate with interfaces of other security zones.
- It includes interfaces that are not members of other security zones.
- It is a system-built zone.
- It includes all IP addresses on a router.
- All traffic to and from this zone is permitted by default.
75. Which password type uses a Cisco proprietary Vigenere cypher encryption algorithm and is considered easy to crack?
- type 5
- type 7
- type 8
- type 9
76. Which threat protection capability is provided by Cisco ESA?
- web filtering
- cloud access security
- spam protection
- Layer 4 traffic monitoring
77. Which industry standard provides for port-based network access control?
- 802.1Q
- RADIUS
- LISP
- 802.1x
78. Refer to the exhibit. A network administrator configures AAA authentication on R1. When the administrator tests the configuration by telneting to R1 and no ACS servers can be contacted, which password should the administrator use in order to login successfully?
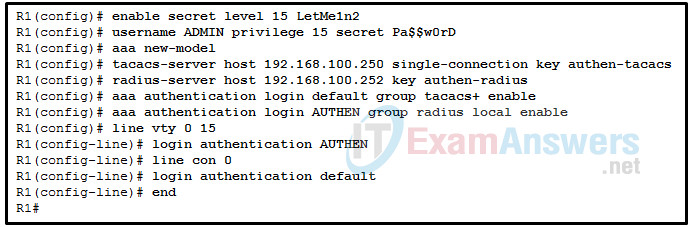
- authen-radius
- LetMe1n2
- Pa$$w0rD
- authen-tacacs
79. What is the one major difference between local AAA authentication and using the login local command when configuring device access authentication?
- The login local command requires the administrator to manually configure the usernames and passwords, but local AAA authentication does not.
- Local AAA authentication allows more than one user account to be configured, but login local does not.
- Local AAA authentication provides a way to configure backup methods of authentication, but login local does not.
- The login local command uses local usernames and passwords stored on the router, but local AAA authentication does not.
80. Refer to the exhibit. The ACL statement is the only one explicitly configured on the router. Based on this information, which two conclusions can be drawn regarding remote access network connections? (Choose two.)

- SSH connections from the 192.168.2.0/24 network to the 192.168.1.0/24 network are allowed.
- SSH connections from the 192.168.1.0/24 network to the 192.168.2.0/24 network are allowed.
- Telnet connections from the 192.168.2.0/24 network to the 192.168.1.0/24 network are allowed.
- SSH connections from the 192.168.1.0/24 network to the 192.168.2.0/24 network are blocked.
- Telnet connections from the 192.168.1.0/24 network to the 192.168.2.0/24 network are blocked.
- Telnet connections from the 192.168.1.0/24 network to the 192.168.2.0/24 network are allowed.
81. Consider the configured access list.
R1# show access-lists extended IP access list 100 deny tcp host 10.1.1.2 host 10.1.1.1 eq telnet deny tcp host 10.1.2.2 host 10.1.2.1 eq telnet permit ip any any (15 matches)
What are two characteristics of this access list? (Choose two.)
- The 10.1.2.1 device is not allowed to telnet to the 10.1.2.2 device.
- The access list has been applied to an interface.
- Any device can telnet to the 10.1.2.1 device.
- A network administrator would not be able to tell if the access list has been applied to an interface or not.
- Only the 10.1.1.2 device can telnet to the router that has the 10.1.1.1 IP address assigned.
- Any device on the 10.1.1.0/24 network (except the 10.1.1.2 device) can telnet to the router that has the IP address 10.1.1.1 assigned.
82. Refer to the exhibit. An extended access list has been created to prevent human resource users from gaining access to the accounting server. All other network traffic is to be permitted. When following the ACL configuration guidelines, on which router, interface, and direction should the access list be applied?
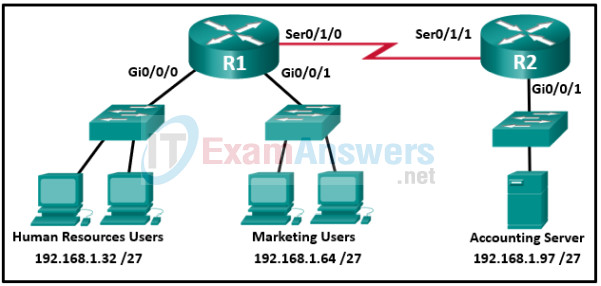
- router R1, interface S0/1/0, outbound
- router R2, interface Gi0/0/1, outbound
- router R2, interface Gi0/0/1, inbound
- router R1, interface Gi0/0/0, inbound
- router R2, interface S0/1/1, inbound
- router R1, interface Gi0/0/0, outbound
83. Refer to the exhibit. Which data format is used to represent the data for network automation applications?
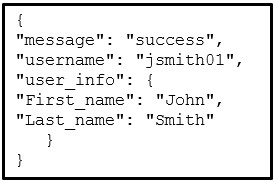
- XML
- YAML
- HTML
- JSON
84. Which Python function is used for console output?
- for
- from
- return
85. What are two characteristics of the Python programming language? (Choose two.)
- It only runs in the interactive mode.
- It requires a compiler to be installed.
- The code is easy to read.
- It runs without conversion to machine-language.
- It uses the & symbol to indicate that the interactive mode is ready to accept commands.
86. What term is used to describe the files that contain Python definitions and statements?
- function
- file
- module
- script
87. Which characteristic is common to both Chef and Puppet?
- Both function in a peer-to-peer model.
- Both use the push model for configuration management.
- Both have free open source versions.
- Both are Cisco proprietary.
88. Question as presented: Match the automation tool to the architecture components.
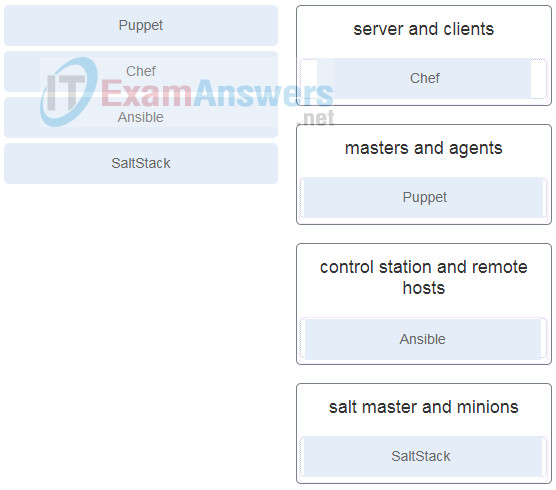
- server and clients
- masters and agents
- control station and remote hosts
- salt master and minions
89. Which data format is expected by Cisco DNA Center for all incoming data from the REST API?
- YAML
- HTTP
- JSON
- XML
90. Which three orchestration tools require agent software on client machines to be managed? (Choose three.)
- Chef
- Ansible
- EEM
- Puppet Bolt
- SaltStack
- Puppet
91. Which three are components of puppet modules? (Choose three.)
- files
- recipes
- manifests
- pillars
- playbooks
- templates
92. What are the key difference between a type 1 hypervisor and a type 2 hypervisor?
- A type 1 hypervisor runs on specialized systems and a type 2 hypervisor runs on desktop computers.
- A type 1 hypervisor runs directly on the system hardware and a type 2 hypervisor requieres a host OS to run.
- A type 1 hypervisor supports all server OS virtualization and a type 2 hypervisor supports Linux and Mac virtualization.
- A type 1 hypervisor supports server virtualization and a type 2 hypervisor supports workstation virtualization.
93. A network administrator issues the show bgp ipv4 unicast summary command to verify BGP session after basic BGP configuration is completed. Which three pieces of information are found in the BGP session summary? (Chose three.)
- the number of exchanged prefixes with a neighbor
- the BGP router ID of peers
- the routes that are redistributed into BGP
- the peer synchronization configuration
- the AS number of the peer
- the IGP that is configured on the BGP peer
94. A network administrator uses the spanning-tree portfast bpduguard default global configuration command to enable BPDU guard on switch. However, BPDU guard is not activated on all access ports. What is the couse of the issue?
- BPDU guard needs to be activated on the interface configuration command mode.
- PortFast is not configured on all access ports.
- Access ports configured with root guard cannot be configured with BPDU GURAD.
- Access ports belong to different VLANs.
95. What is the key difference between a type 1 hypervisor and a type 2 hypervisor?
- A type 1 hypervisor supports all server OS virtualization and a type 2 hypervisor supports Linux and Mac virtualization.
- A type 1 hypervisor runs directly on the system hardware and a type 2 hypervisor requires a host OS to run.
- A type 1 hypervisor runs on specialized systems and a type 2 hypervisor runs on desktop computers.
- A type 1 hypervisor supports server virtualizations and a type 2 hypervisor only supports workstation virtualization.
96. A network administrator issues the show bgp ipv4 unicast summary command to verify the BGP session after basic BGP configuration is completed. Which three pieces of information are found in the BGP session summary? (Choose three.)
- the routes that are redistributed into BGP
- the IGP that is configured on the BGP peer
- the number of exchanged prefixes with a neighbor
- the AS number of the peer
- the peer synchronization configuration
- the BGP router ID of the peers
97. Refer to the exhibit. A network administrator issues the show bgp ipv4 unicast | begin Network command to check the routes in the BGP table. What does the symbol ? at the end of a route indicate?
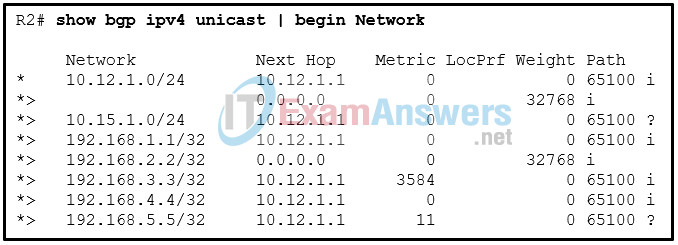
- The route is learned through a static route.
- The route is originated from a connected network to the router.
- The route is redistributed into BGP.
- The route is the best route for the network prefix
98. Which two OSPFv3 LSA types are used to advertise IPv6 prefixes to neighbors? (Choose two.)
- LSA type 4 – interarea router
- LSA type 5 – AS-external
- LSA type 7 – NSSA
- LSA type 8 – link-local LSA
- LSA type 9 – intra-area prefix LSA
99. Refer to the exhibit. Spanning-tree port priorities are listed beneath each interface. The network administrator enters the spanning-tree vlan 1 root primary command on S4. What is the effect of the command?
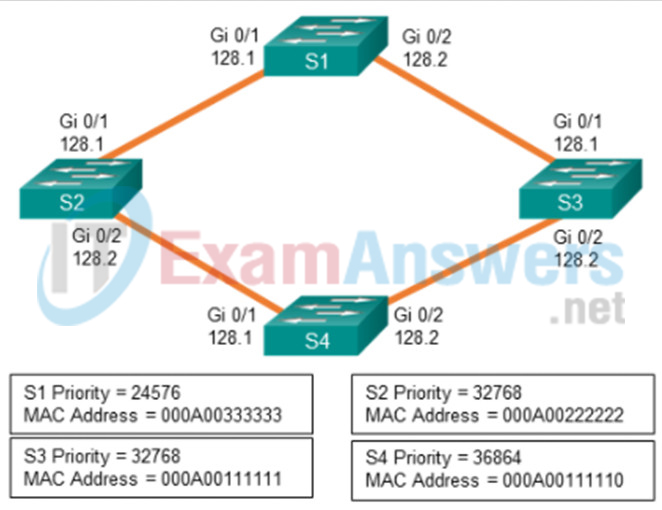
- Port priority makes Gi0/2 on S1 a root port.
- S3 Gi0/2 transitions from designated port to root port because of path cost changes caused by the root change.
- Spanning tree blocks Gi0/1 on S3 to prevent a redundant path from S1.
- S4 is already the root bridge, so there are no port changes.
- S2 Gi0/1 becomes a nondesignated port because Gi0/2 has a lower path cost to S4.
100. Refer to the exhibit. A network administrator is configuring an EtherChannel link between two switches, SW1 and SW2. Which statement describes the effect after the commands are issued on SW1 and SW2?
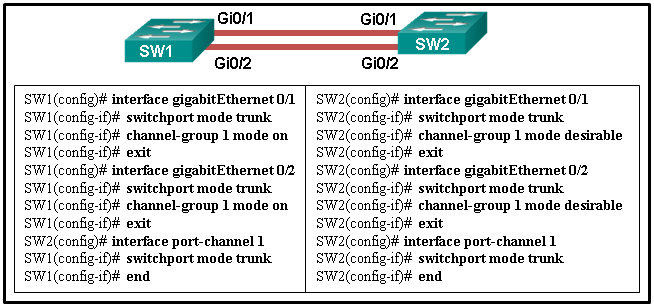
- The EtherChannel is established after SW2 initiates the link request.
- The EtherChannel is established after SW1 initiates the link request.
- The EtherChannel is established without negotiation.
- The EtherChannel fails to establish.

Has anybody used this recently?
I ask because I notice it’s no longer in the main menu anymore, but it appears to still be getting updated?
Which two OSPFv3 LSA types are used to advertise IPv6 prefixes to neighbors? (Choose two.)
Thanks for sharing!
Can anyone please tell me the difference between ccnp v8 & encor 350-401?
What are the key difference between a type 1 hypervisor and a type 2 hypervisor?
– A type 1 hypervisor runs on specialized systems and a type 2 hypervisor runs on desktop computers.
– A type 1 hypervisor runs directly on the system hardware and a type 2 hypervisor requieres a host OS to run. (correct one)
– A type 1 hypervisor supports all server OS virtualization and a type 2 hypervisor supports Linux and Mac virtualization.
– A type 1 hypervisor supports server virtualization and a type 2 hypervisor supports workstation virtualization.
Added all, thanks for your sharing!!
A network administrator issues the show bgp ipv4 unicast summary command to verify BGP session after basic BGP configuration is completed. Which three pieces of information are found in the BGP session summary? (Chose three.)
o the number of exchanged prefixes with a neighbor (THIS)
o the BGP router ID of peers (THIS)
o the routes that are redistributed into BGP
o the peer synchronization configuration
o the AS number of the peer (THIS)
o the IGP that is configured on the BGP peer
A network administrator uses the spanning-tree portfast bpduguard default global configuration command to enable BPDU guard on switch. However, BPDU guard is not activated on all access ports. What is the couse of the issue?
x BPDU guard needs to be activated on the interface configuration command mode.
x PortFast is not configured on all access ports. (CORRECT)
x Access ports configured with root guard cannot be configured with BPDU GURAD.
X Access ports belong to different VLANs.