CCNP Enterprise: Advanced Routing (Version 8.0) – Infrastructure Security and Management Exam
1. Which two characteristics are shared by both standard and extended ACLs? (Choose two.)
- Both kinds of ACLs can filter based on protocol type.
- Both can be created by using either a descriptive name or number.
- Both filter packets for a specific destination host IP address.
- Both include an implicit deny as a final statement.
- Both can permit or deny specific services by port number.
2. What method is used to apply an IPv6 ACL to a router interface?
- the use of the ipv6 traffic-filter command
- the use of the ipv6 access-list command
- the use of the access-class command
- the use of the ip access-group command
3. Refer to the exhibit. A network administrator created an IPv6 ACL to block the Telnet traffic from the 2001:DB8:CAFE:10::/64 network to the 2001:DB8:CAFE:30::/64 network. What is a command the administrator could use to allow only a single host 2001:DB8:CAFE:10::A/64 to telnet to the 2001:DB8:CAFE:30::/64 network?

- permit tcp 2001:DB8:CAFE:10::A/64 2001:DB8:CAFE:30::/64 eq 23
- permit tcp host 2001:DB8:CAFE:10::A 2001:DB8:CAFE:30::/64 eq 23 sequence 5
- permit tcp 2001:DB8:CAFE:10::A/64 eq 23 2001:DB8:CAFE:30::/64
- permit tcp host 2001:DB8:CAFE:10::A eq 23 2001:DB8:CAFE:30::/64
4. Which two statements describe the effect of the access control list wildcard mask 0.0.0.15? (Choose two.)
- The last five bits of a supplied IP address will be ignored.
- The first 32 bits of a supplied IP address will be matched.
- The last four bits of a supplied IP address will be ignored.
- The first 28 bits of a supplied IP address will be ignored.
- The last four bits of a supplied IP address will be matched.
- The first 28 bits of a supplied IP address will be matched.
5. A network administrator is configuring an IPv6 ACL to deny Telnet access from all staff in the branch office to a file server in home office. All branch office staff use addressing from the IPv6 subnet 2001:DB8:100:20::/64. The file server in home office uses the address 2001:DB8:100:50::15/64. Implementing the No-Telnet ACL on the LAN interface of the branch office router requires which three commands? (Choose three.)
- permit tcp any host 2001:DB8:100:20::15 eq 23
- deny tcp host 2001:DB8:100:50::15 any eq 23
- deny tcp any host 2001:DB8:100:50::15 eq 23
- permit ipv6 any any
- deny ipv6 any any
- ip access-group No-Telnet in
- ipv6 traffic-filter No-Telnet in
6. Refer to the exhibit. An administrator is configuring a prefix list to stop advertising 172.18.100.0/24, a secure Branch network, to the internet. After adding the prefix list, the administrator notices that the branch network is still being advertised. How can the administrator fix the error?
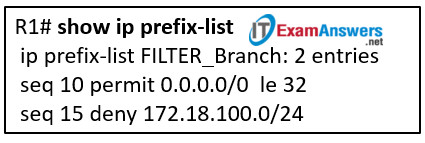
- Modify the order of the statements so that the deny statement is before the permit statement.
- The prefix list needs another statement to permit the advertisement of the default route.
- Modify the permit statement to use ge 32 instead of le 32 .
- Modify the entry with sequence number 10 to be sequence number 5.
- Modify the deny statement to seq 15 deny 172.18.0.0/16.
7. Refer to the exhibit. A network administrator is configuring an ACL to limit the connection to R1 vty lines to only the IT group workstations in the network 192.168.22.0/28. The administrator verifies the successful Telnet connections from a workstation with IP 192.168.22.5 to R1 before the ACL is applied. However, after the ACL is applied to the interface Fa0/0, Telnet connections are denied. What is the cause of the connection failure?
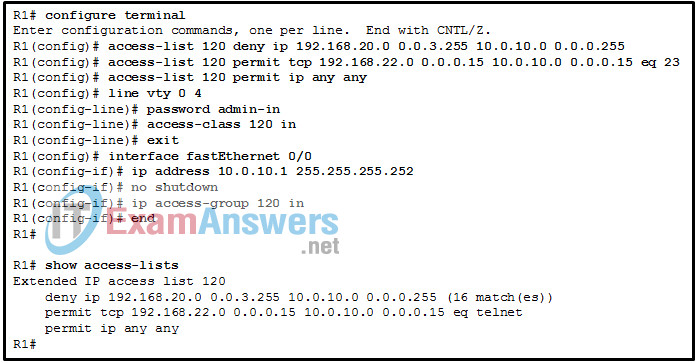
- The IT group network is included in the deny statement.
- The login command has not been entered for vty lines.
- The permit ACE specifies a wrong port number.
- The enable secret password is not configured on R1.
- The permit ACE should specify protocol ip instead of tcp.
8. Which two commands can be used to verify the content and placement of access control lists? (Choose two.)
- show running-config
- show ip route
- show cdp neighbor
- show processes
- show access-lists
9. Which prefix-list entry will be used when multiple entries in a prefix list match a given prefix?
- all matching entries
- entry with the largest sequence number
- entry with the lowest sequence number
- entry with the longest prefix mask length
10. Which feature is unique to IPv6 ACLs when compared to those of IPv4 ACLs?
- an implicit permit of neighbor discovery packets
- the use of named ACL statements
- the use of wildcard masks
- an implicit deny any any statement
11. Refer to the exhibit. The settings to connect to a RADIUS server were issued on router Rtr1. Which conclusion can be drawn if a problem occurs with AAA authentication between Rtr1 and Server1?
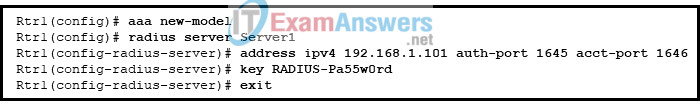
- The RADIUS server configuration requires that port 1813 be used for authentication and port 1812 for authorization.
- The RADIUS server configuration requires that port 49 be used for authentication and authorization.
- The port numbers configured on the router are not identical to those configured on the RADIUS server.
- The configuration will not be active until it is saved and Rtr1 is rebooted.
12. Which mitigation technique would prevent rogue servers from providing false IPv6 configuration parameters to clients?
- enabling DHCPv6 Guard
- enabling RA Guard
- implementing port security on edge ports
- disabling CDP on edge ports
13. Which IPv6 First-Hop Security feature can block IPv6 traffic if this traffic is from an unknown origin?
- RA Guard
- Source Guard
- DHCPv6 Guard
- IPv6 ND inspection/snooping
14. Refer to the exhibit. Router R1 is configured as shown. An administrative user attempts to use Telnet from router R2 to R1 using the interface IP address 10.10.10.1. However, Telnet access is denied. Which conclusion can be drawn from this scenario?
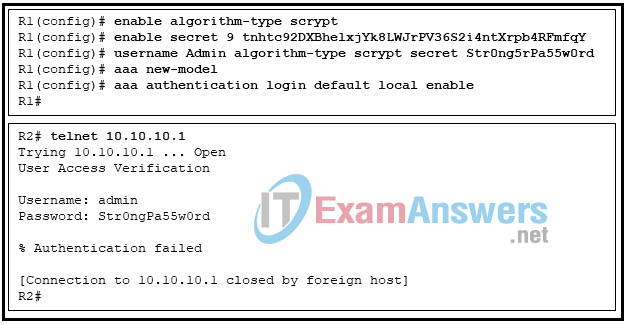
- The vty lines must be configured with the login authentication default command.
- The password was mistyped.
- The administrative user should use the username Admin .
- The aaa local authentication attempts max-fail command must be set to 2 or higher.
15. What happens when a packet does not match any of the defined class maps specified in a policy map?
- The packet is transmitted to a default interface.
- The packet is transmitted to a default gateway.
- The packet is dropped.
- The packet is subject to the policy defined in a default class.
16. Refer to the exhibit. Which piece of information can be obtained from the AAA configuration commands?
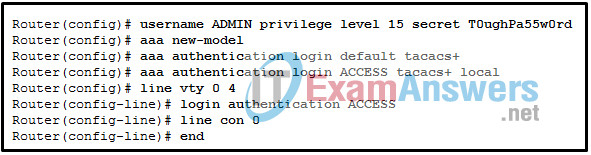
- If the TACACS+ AAA server is not available, no users can establish a Telnet session with the router.
- The authentication method list used by the console port is named ACCESS.
- The authentication method list used for Telnet is named ACCESS.
- The local database is checked first when console and Telnet access to the router is being authenticated.
- If the TACACS+ AAA server is not available, console access to the router can be authenticated using the local database.
17. A junior engineer is learning how to apply a service policy to a Cisco router control plane. Which piece of information should be considered to perform this configuration?
- If the direction is not applied to a service policy, the direction is input by default.
- Policy map names are not case-sensitive.
- There are Cisco IOS versions which do not support output CoPP.
- The service policy specified in the policy map needs to be attached to a high bandwidth Ethernet interface.
18. What is the recommended action when troubleshooting scenarios for CoPP, where specific source and destination IP addresses are used in the ACL?
- Use the destination IP address as the source IP address and vice-versa.
- Change the IP addresses in the ACL with respective IP broadcast addresses for both source and destination IP addresses.
- Replace the extended ACL with an standard ACL.
- Change the IP addresses in the ACL to any / any .
19. Which action is necessary to provide encrypted transfer of data between a RADIUS server and a AAA-enabled router?
- Configure the preshared key exactly the same way on the server and the router.
- Encrypt usernames and passwords that will be used between the router and the RADIUS server.
- Use identical reserved ports on the server and the router.
- Create a VPN tunnel between the server and the router.
20. A teacher is explaining uRPF to network students in a classroom. Which two statements are accurate about uRPF operation on a Cisco router? (Choose two.)
- It only works if Cisco Express Forwarding is enabled on a router.
- With uRPF, any packets generated by the router and destined to the router are considered valid by default.
- The feature helps eliminate spoofed IP packets on a network by examining the source IP address of an ingress packet.
- It has two possible operation modes: strict and loose.
- The uRPF feature helps limit spoofed IP packets on a network by examining the source and the destination IP addresses of an ingress packet.
21. A network administrator is configuring SSH on a router. When verifying the configuration, the administrator notices that the SSH connection requests fail, but the Telnet connection requests from the same workstation are successful. Which two parts of the router configuration should be checked to try to locate the problem? (Choose two.)
- The transport input command is incorrect on the vty lines.
- An extended ACL that is referencing the port argument for SSH is misconfigured.
- The ip access-class command is missing.
- The password is misconfigured on the console line.
- A standard ACL is possibly blocking the workstation from access to the router.
22. A network technician is configuring SNMPv3 and has set a security level of auth . What is the effect of this setting?
- authenticates a packet by using either the HMAC MD5 or HMAC SHA algorithms and encrypts the packet with either the DES, 3DES or AES algorithms
- authenticates a packet by a string match of the username or community string
- authenticates a packet by using the SHA algorithm only
- authenticates a packet by using either the HMAC with MD5 method or the SHA method
23. Refer to the exhibit. A SNMP manager has IP address 172.16.1.120. The SNMP manager is unable to change configuration variables on the R1 SNMP agent. What could be the problem?
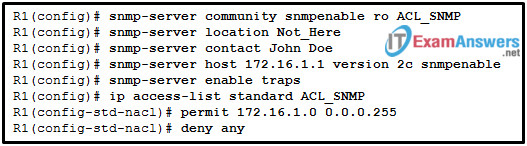
- The SNMP agent is not configured for write access.
- The SNMP agent should have traps disabled.
- The IP address of the SNMP manager must be 172.16.1.1.
- The ACL of ACL_SNMP has not been implemented on an interface yet.
24. Refer to the exhibit. Which SNMP authentication password must be used by the member of the ADMIN group that is configured on router R1?
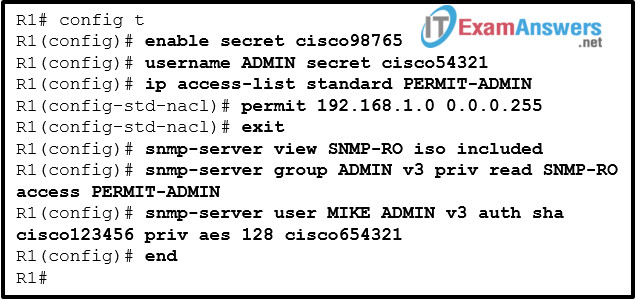
- cisco654321
- cisco54321
- cisco98765
- cisco123456
25. A computer technician is monitoring traffic on a network where users are complaining about slow network performance. The technician is curious as to whether the new network management software is causing the slowdown. Which two port numbers would the technician be looking for in the captured packets for SNMP traffic? (Choose two.)
- 162
- 80
- 161
- 67
- 443
- 68
26. Which two types of probes can be configured to monitor traffic by IP SLA within a network environment? (Choose two.)
- SNMP traps
- syslog messages
- website upload time
- packet loss
- voice quality scores
27. A network administrator has issued the snmp-server user admin1 admin v3 encrypted auth md5 abc789 priv des 256 key99 command. What are two features of this command? (Choose two.)
- It uses the MD5 authentication of the SNMP messages.
- It restricts SNMP access to defined SNMP managers.
- It forces the network manager to log into the agent to retrieve the SNMP messages.
- It allows a network administrator to configure a secret encrypted password on the SNMP server.
- It adds a new user to the SNMP group.
28. When configuring SSH on a router to implement secure network management, a network engineer has issued the login local and transport input ssh line vty commands. What three additional configuration actions have to be performed to complete the SSH configuration? (Choose three.)
- Create a valid local username and password database.
- Set the user privilege levels.
- Manually enable SSH after the RSA keys are generated.
- Generate the asymmetric RSA keys.
- Configure the correct IP domain name.
- Configure role-based CLI access.
29. A technician configured a switch with console, enable secret, and VTY passwords. The service password-encryption command was then used to encrypt all unencrypted passwords. What happens if the technician issues the no service password-encryption command?
- Only the enable secret password will remain encrypted.
- All passwords, including the enable secret password, will be shown in clear text.
- The switch will issue an ‘Invalid Error’ message.
- The passwords will still be encrypted.
30. Which statement correctly describes how an ACL can be used with the access-class command to filter vty access to a router?
- An extended ACL can be used to restrict vty access based on specific source addresses and protocol but the destination can only specify the keyword any .
- It is only possible to apply a standard ACL to the vty lines.
- An extended ACL can be used to restrict vty access based on specific source addresses, destination addresses, and protocol.
- An extended ACL can be used to restrict vty access based on specific source and destination addresses but not on protocol.
31. A network administrator is configuring a prefix list with the ip prefix-list command. Which entry is valid?
- ip prefix-list LIST1 seq 5 permit 192.168.0.0/14 ge 24 le 28
- ip prefix-list LIST1 seq 10 permit 192.168.10.0/15 le 23 ge 27
- ip prefix-list LIST1 seq 1 permit 10.18.0.0/16 ge 12
- ip prefix-list LIST1 seq 10 permit 12.16.10.0/12 le 22 ge 24
32. A network administrator configures uRPF on a Cisco router interface with the ip verify unicast source reachable-via rx allow-default command to eliminate spoofed IP packets on a network. Which conclusion can be drawn from this configuration?
- The security feature uRPF is configured with loose mode, and the route for return traffic is chosen based on a default route.
- The security feature uRPF is configured with strict mode ,and the return path is associated with an interface chosen based on a default route.
- The security feature uRPF is configured with loose mode, and return traffic will take a route other than one based on a default route.
- The security feature uRPF is configured with strict mode, and the return path is associated with an interface other than a default route.
33. Refer to the exhibit. The administrator configured the access to the console and the vty lines of a router. Which conclusion can be drawn from this configuration?
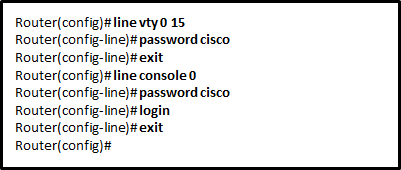
- Access to the vty lines will not be allowed via Telnet by anyone.
- Because the IOS includes the login command on the vty lines by default, access to the device via Telnet will require authentication.
- Unauthorized individuals can connect to the router via Telnet without entering a password.
- Because the login command was omitted, the password cisco command is not applied to the vty lines.

Which two statements describe the effect of the access control list wildcard mask 0.0.0.15? (Choose two.)
Thankyou!