Checkpoint Exam: Network Design and Monitoring Exam Answers
Modules 22 – 24 of the CCNP Enterprise: Core Networking v8.0 (ENCOR)
1. Which network design solution will best extend access layer connectivity to host devices?
- implementing redundancy
- implementing EtherChannel
- implementing wireless connectivity
- implementing routing protocols
2. A network designer must provide a rationale to a customer for a design which will move an enterprise from a flat network topology to a hierarchical network topology. Which two features of the hierarchical design make it the better choice? (Choose two.)
- simpler deployment for additional switch equipment
- easier to provide redundant links to ensure higher availability
- lower bandwidth requirements
- less required equipment to provide the same performance levels
- reduced cost for equipment and user training
3. What are three benefits of employing a hierarchical network design? (Choose three.)
- Use of a hierarchical design allows replacement of redundant devices with high-capacity network equipment.
- The hierarchical model allows the use of high-performance switches at all design layers, thus allowing for a fully-meshed topology.
- Hierarchically designed networks can more easily be expanded to suit future needs.
- Hierarchical design models enhance existing bandwidth through the use of link aggregation.
- A hierarchical design uses firewalls instead of complicated port-based and distribution layer security policies.
- The hierarchical model allows for specialized functionality at each layer, simplifying device management.
4. At the distribution layer of a hierarchical network, what are two advantages of using Layer 3 devices instead of Layer 2 switches? (Choose two.)
- creates fewer IP subnets to configure and manage
- provides connectivity between different VLANs
- enables traffic filtering based on subnet addresses
- provides reliable connectivity to end users
- reduces the number of redundant links required
5. Which three characteristics are typically associated with the core layer in the Cisco hierarchical network design model? (Choose three.)
- packet manipulation
- monitoring of DMZ traffic
- connectivity to the data center
- redundant paths
- rapid forwarding of traffic
6. Refer to the exhibit. Which switching technology would allow each access layer switch link to be aggregated to provide more bandwidth between each Layer 2 switch and the Layer 3 switch?

- HSRP
- EtherChannel
- trunking
- PortFast
7. Refer to the exhibit. Which type of Cisco hierarchical LAN design model is used at school site 1?
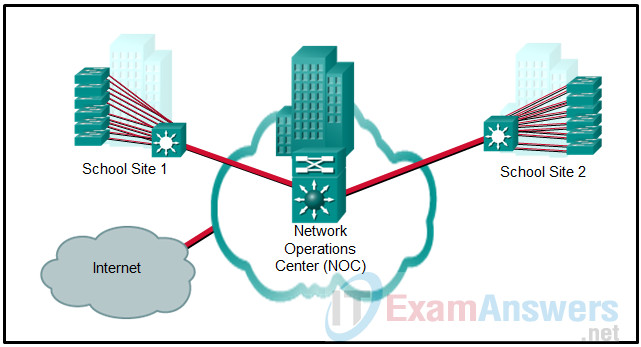
- three-tier
- 7 layer
- 3 layer
- two-tier collapsed core
8. A network engineer is attempting to explain StackWise technology to a client who wants to deploy a simplified campus design. Which explanation accurately describes this technology?
- It allows the switch to deliver power to end devices by using existing Ethernet cabling.
- It allows up to eight ports to be bound together to increase available bandwidth.
- It allows the switch capabilities and ports to be expanded by the addition of line cards.
- It allows multiple switches to function as a single logical switch.
9. On a campus network, personnel who are located in a five site college have access to servers found in one location. In which network block of the campus network architecture would these servers be found?
- WAN edge
- data center
- Internet edge
- network services
10. In a new network design, an organization has decided to manage all of its wireless access points using a wireless network controller. In which network design block of the campus network architecture would the centralized wireless network controllers be found?
- network services
- internet edge
- data center
- WAN edge
11. A network engineer has to decide between a Layer 2 Access Layer (STP-based) and a Layer 3 Access Layer (Routed access) campus design option. Which statement must be considered for a decision to be made?
- The Routed access option is the best cost-effective solution.
- The STP based access option supports spanning VLANs across multiple access switches, whereas the Routed access option does not.
- The Routed access option offers easier troubleshooting than the STP-based option.
- The STP based option does not require FHRP, whereas the Routed access option does.
12. What is the description for a Syslog Level 3 event?
- error condition
- critical condition
- immediate action needed
- warning condition
13. Match the SD-Access fabric device role to the description. (Not all options are used.)
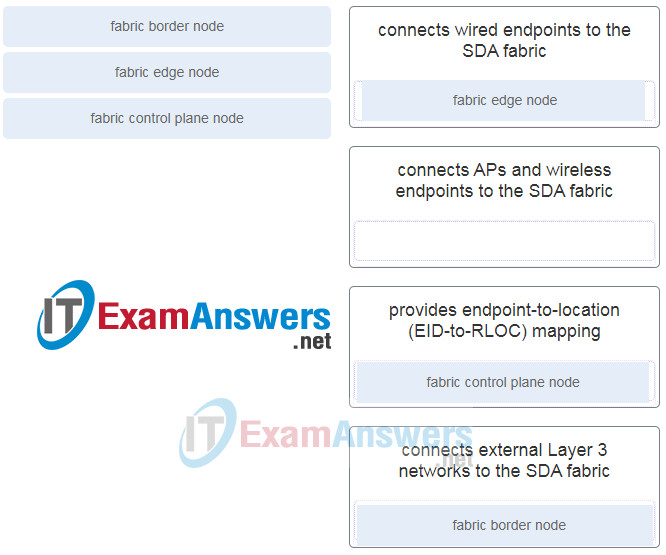
- fabric edge node : connects wired endpoints to the SDA fabric
- connects APs and wireless endpoints to the SDA fabric
- fabric control plane node : provides endpoint-to-location (EID-to-RLOC) mapping
- fabric border node : connects external Layer 3 networks to the SDA fabric
14. Which protocol or service can be configured to send unsolicited messages to alert the network administrator about a network event such as an extremely high CPU utilization on a router?
- syslog
- SNMP
- NTP
- NetFlow
15. An administrator issued the following commands on router R1:
R1(config)# logging 192.168.10.2 R1(config)# logging trap 5
What conclusion can be drawn from this configuration?
- The only messages that appear on the syslog server are those with severity level of 5.
- Messages with severity level of 6 or higher appear only on the router console output.
- Messages with severity level of 5 or higher appear on the router console output and are sent to the syslog server.
- The only messages that appear on the syslog server are those with severity level of 4 or lower.
16. What is the description for a Syslog Level 1 event?
- system unusable
- immediate action needed
- error condition
- critical condition
17. What is the purpose of ERSPAN?
- to mirror traffic from a remote location
- to log information from monitored network devices
- to provide standardization for traffic sent from network devices to a logging server
- to analyze the type and frequency of specific data types for QoS purposes
18. What is a primary function of the Cisco IOS IP Service Level Agreements feature?
- to measure network performance and discover a network failure as early as possible
- to detect potential network attacks
- to adjust network device configurations to avoid congestion
- to provide network connectivity for customers
19. What is a tool in the Cisco DNA Center that can apply machine learning in order to diagnose network issues and offer guided remediation steps to fix issues?
- DNA Assurance
- syslog
- RSPAN
- SNMP
- ERSPAN
20. What is the description for a Syslog Level 5 event?
- normal, but significant condition
- debugging message
- warning condition
- informational message
21. What is the description for a Syslog Level 6 event?
- normal, but significant condition
- informational message
- debugging message
- warning condition
22. Which layer of the Cisco SD-Access Architecture contains the underlay and the overlay networks?
- controller
- network
- management
- physical
23. Which two statements describe the SD-Access overlay network? (Choose two.)
- It provides underlay and fabric automation and orchestration.
- It is a virtualized network interconnecting all network devices.
- It has three planes of operation: control, data, and policy.
- It is the underlying physical layer transporting data between network devices.
- It includes all devices that actively participate in the SD-Access fabric.
24. What is the role of the fabric edge node in the SD-Access fabric overlay?
- connecting wired endpoints to the SDA fabric
- providing endpoint-to-location (EID-to-RLOC) mapping to the SDA fabric
- connecting APs and wireless endpoints
- connecting external Layer 3 networks to the SDA fabric
25. Match the layer of the Cisco SD-Access Architecture with the description.
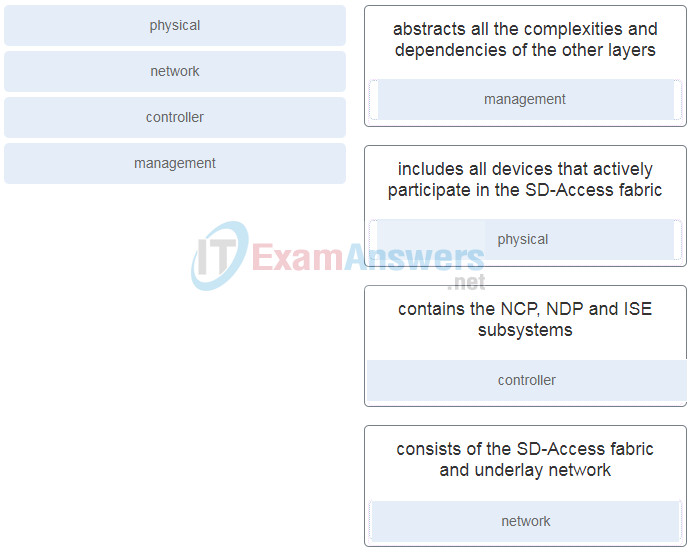
- abstracts all the complexities and dependencies of the other layers
- includes all devices that actively participate in the SD-Access fabric
- contains the NCP, NDP and ISE subsystems
- consists of the SD-Access fabric and underlay network
26. Which IGP is used in the automated underlay model of the Cisco SD-Access architecture?
- OSPF
- BGP
- IS-IS
- EIGRP
27. Which tunneling technology is used by the SD-Access fabric data plane to create the overlay network for the SD-Access fabric?
- VXLAN
- MPLS
- LISP
- GRE
28. What is the responsibility of the ISE subsystem within the Cisco SD-Access Architecture controller layer?
- It provides all the underlay and fabric automation and orchestration services for the physical and network layers.
- It provides all the identity and policy services for the physical layer and network layer.
- It analyzes and correlates network events and identifies historical trends.
- It provides network operational status and other information to the management layer.
1.23.3 SD-Access Architecture
29. What function is provided by the vManage Network Management System in the Cisco SD-WAN solution?
- Providing the single pane of glass (GUI) for the SD-WAN solution.
- Managing software images, maintenance updates, version compliance, and the deployment of device images.
- Providing the best application quality of experience (QoE) for SaaS applications.
- Authenticating the vSmart controllers and the SD-WAN routers and orchestrates connectivity between them.
30. What are three functions of the Cisco SD-WAN vBond orchestrator? (Choose three.)
- delivering quality of experience (QoE) for SaaS applications
- providing a single pane of glass network management system
- providing a control plane connection over DTLS tunnels to communicate with SD-WAN routers
- forecasting and what-if analysis
- providing NAT traversal between SD-WAN routers
- providing load balancing of SD-WAN routers
31. In a domain with multiple vSmart controllers, which Cisco SD-WAN solution performs automatic load balancing of SD-WAN routers across multiple controllers?
- vBond orchestrator
- vManage Network Management System
- vSmart controller
- Cloud OnRamp
32. Refer to the exhibit. A junior network engineer is handed a print-out of the network information shown. Which protocol or service originated the information shown in the graphic?
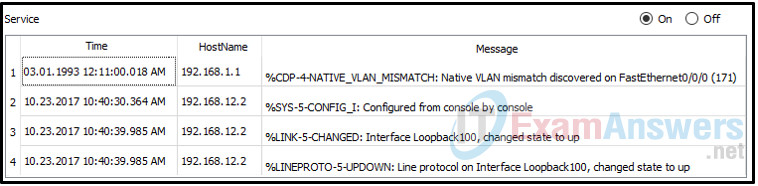
- Syslog
- RADIUS
- NetFlow
- TACACS+
33. Refer to the exhibit. Host H3 is having trouble communicating with host H1. The network administrator suspects a problem exists with the H3 workstation and wants to prove that there is no problem with the R2 configuration. What tool could the network administrator use on router R2 to prove that communication exists to host H1 from the interface on R2, which is the interface that H3 uses when communicating with remote networks?
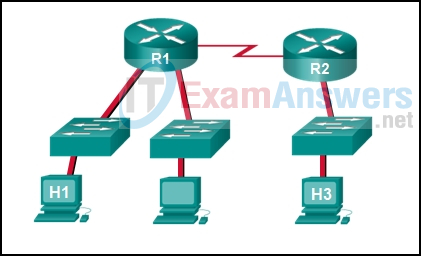
- Telnet
- show cdp neighbors
- an extended ping
- traceroute
34. In the data gathering process, which type of device will listen for traffic, but only gather traffic statistics?
- NetFlow collector
- SNMP agent
- NMS
- syslog server
35. Which type of information can an administrator obtain with the show ip cache flow command?
- the NetFlow version that is enabled
- the protocol that uses the largest volume of traffic
- whether NetFlow is configured on the correct interface and in the correct direction
- the configuration of the export parameters
36. Which network monitoring tool can provide a complete audit trail of basic information of all IP flows on a Cisco router and forward the data to a device?
- NetFlow
- SIEM
- SPAN
- Wireshark
37. Which monitoring technology mirrors traffic flowing through a switch to an analysis device connected to another switch port?
- SIEM
- SPAN
- NetFlow
- SNMP
38. Refer to the exhibit. Which command or set of commands will configure SW_A to copy all traffic for the server to the packet analyzer?
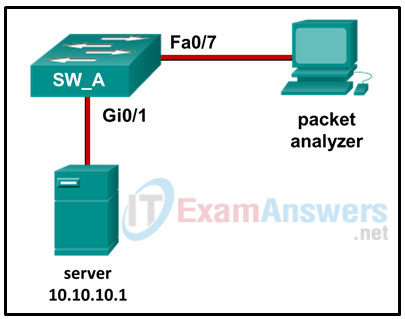
Sw_A(config)# monitor session 5 source interface gi0/1
Sw_A(config)# monitor session 6 destination interface fa0/7
Sw_A(config)# monitor session 1 destination interface fa0/7
Sw_A(config)# monitor session 5 source interface gi0/1
Sw_A(config)# monitor session 5 destination interface fa0/7
Sw_A(config)# monitor session 1 destination interface gi0/1
Sw_A(config)# monitor session 1 source interface fa0/1
Sw_A(config)# monitor session 1 source interface fa0/7
39. Refer to the exhibit. The RSPAN configuration for each switch is shown. The network administrator has configured RSPAN to allow the monitoring of traffic to a corporate server. Unfortunately, the administrator is unable to sniff any traffic from the link. Why is the administrator unable to sniff traffic?
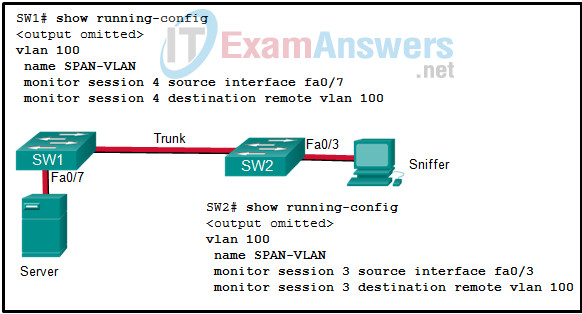
- VLAN 100 has not been properly configured as an RSPAN VLAN.
- Only VLAN 1 can be used as the RSPAN VLAN.
- The source and destination interfaces are reversed on SW2.
- The session numbers on the two switches do not match.
- The remote interface on SW1 should be identified as fa0/3.
40. Refer to the exhibit. Host A is monitoring data and RSPAN is configured on Sw_A with the following commands:
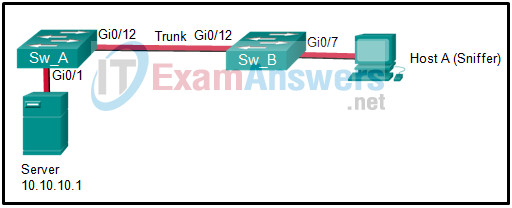
Sw_A# show running-config ...output omitted... monitor session 5 source interface gi0/1 monitor session 5 destination remote vlan 75 ...output omitted... vlan 75 name RSPAN remote span
Which set of commands would complete the RSPAN configuration?
Sw_B(config)# monitor session 5 source remote vlan 75
Sw_B(config)# monitor session 5 destination interface gi0/12
Sw_B(config)# vlan 75
Sw_B(config-vlan)# name RSPAN
Sw_B(config-vlan)# remote-span
Sw_B(config)# monitor session 5 source interface gi0/12
Sw_B(config)# monitor session 5 destination remote vlan 75
Sw_B(config)# vlan 75
Sw_B(config-vlan)# name RSPAN
Sw_B(config-vlan)# remote-span
Sw_B(config)# monitor session 5 source interface Gi0/1
Sw_B(config)# monitor session 5 destination remote vlan 75
Sw_B(config)# vlan 75
Sw_B(config-vlan)# name RSPAN
Sw_B(config-vlan)# remote-span
Sw_B(config)# monitor session 5 source remote vlan 75
Sw_B(config)# monitor session 5 destination interface gi0/7
Sw_B(config)# vlan 75
Sw_B(config-vlan)# name RSPAN
Sw_B(config-vlan)# remote-span
41. A network administrator is using the Cisco DNA Center to monitor network health and to troubleshoot network issues. Which area should the administrator use to perform these tasks?
- ASSURANCE
- PROVISION
- PLATFORM
- POLICY
42. Refer to the exhibit. Based on the output generated by the show monitor session 1 command, how will SPAN operate on the switch?
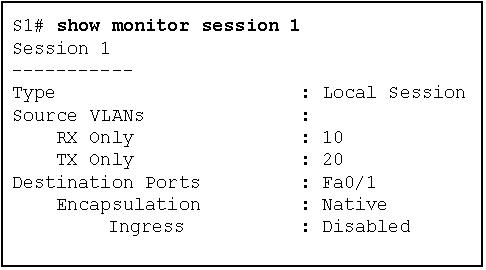
1.JPG
- All traffic received on VLAN 10 or transmitted from VLAN 20 is forwarded to FastEthernet 0/1.
- All traffic transmitted from VLAN 10 or received on VLAN 20 is forwarded to FastEthernet 0/1.
- Native VLAN traffic received on VLAN 10 or transmitted from VLAN 20 is forwarded to FastEthernet 0/1.
- Native VLAN traffic transmitted from VLAN 10 or received on VLAN 20 is forwarded to FastEthernet 0/1.
43. What is the description for a Syslog Level 0 event?
- error condition
- critical condition
- system unusable
- immediate action needed
44. What is the description for a Syslog Level 4 event?
- normal, but significant condition
- Error condition
- warning condition
- Immediate action needed
45. What is the description for a Syslog Level 7 event?
- debugging message
- normal, but significant condition
- informational message
- warning condition

What is the description for a Syslog Level 4 event?
Thank for your sharing!
New question 03/14/2022
What is the description for a Syslog Level 7 event?
new question 04/03/2021
Added, thanks for your sharing!
Refer to the exhibit. Based on the output generated by the show monitor session 1 command, how will SPAN operate on the switch?
Explanation: The show monitor session command is used to verify how SPAN is configured (what ports are involved in the traffic mirroring).
This item references content from the following areas:
CCNPv8 ENCOR
Many thanks for sharing!
What is a tool in the Cisco DNA Center that can apply machine learning in order to diagnose network issues and offer guided remediation steps to fix issues?
Added all, many thanks for your sharing!
What is the description for a Syslog Level 5 event?