CCNP Enterprise: Advanced Routing (Version 8.0) – CCNP ENARSI (300-410) Certification Practice Exam
1. Refer to the exhibit. Routers R1 and R2 enable EIGRP on all of their interfaces. Which two conclusions can the field engineer draw from the outputs of the show ip route eigrp command on each router? (Choose two.)
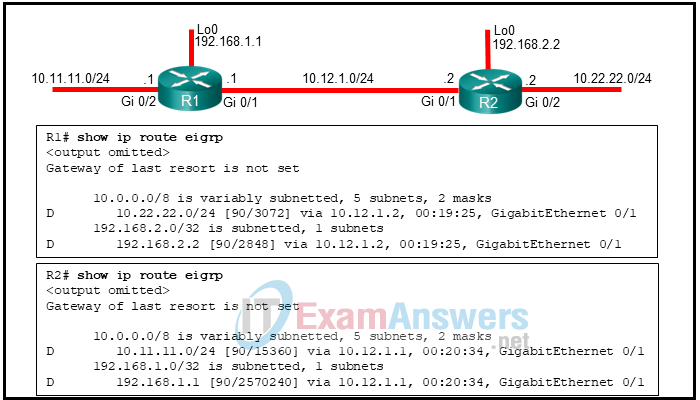
- Both routers are using the same path metric calculation method.
- The path metric calculation used in R2 addresses the scalability with higher-capacity interfaces.
- R1 and R2 are using the same K factors to calculate the path metric.
- An adjacency will be allowed between the routers, as long as all the K factors in both routers are set to default values.
- The EIGRP configuration mode of R1 uses wide metrics calculation.
- R2 is using EIGRP classic configuration mode.
2. Refer to the exhibit. A network administrator is configuring EIGRP AS 20 on Router_2 and has received the error that is shown. What is the cause of the error?
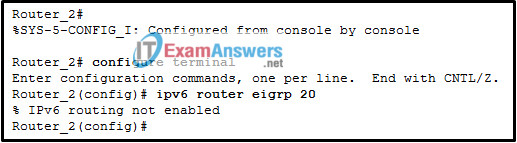
- The autonomous system (AS) number is not the same as the number on other routers in this network.
- The EIGRPv6 interface configuration is incomplete.
- The passive-interface default command has been implemented for EIGRPv6.
- The IPv6 routing process cannot be implemented until IPv6 routing is enabled.
3. An administrator is troubleshooting an adjacency issue between two OSPF routers. Which two neighbor states indicate a stable adjacency between the routers? (Choose two.)
- exstart
- 2way
- full
- exchange
- loading
4. Refer to the exhibit. What destination address will RTB use to advertise LSAs?
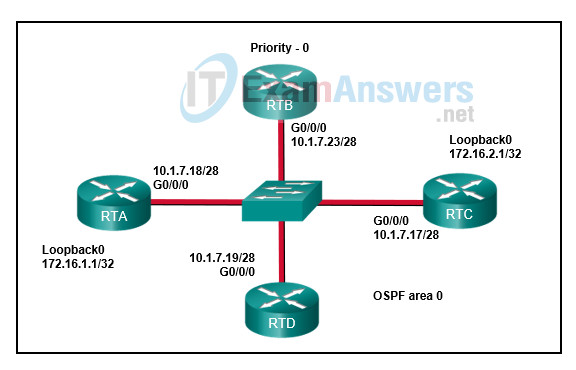
- 255.255.255.255
- 224.0.0.6
- 172.16.1.1
- 224.0.0.5
- 10.1.7.17/28
- 172.16.2.1
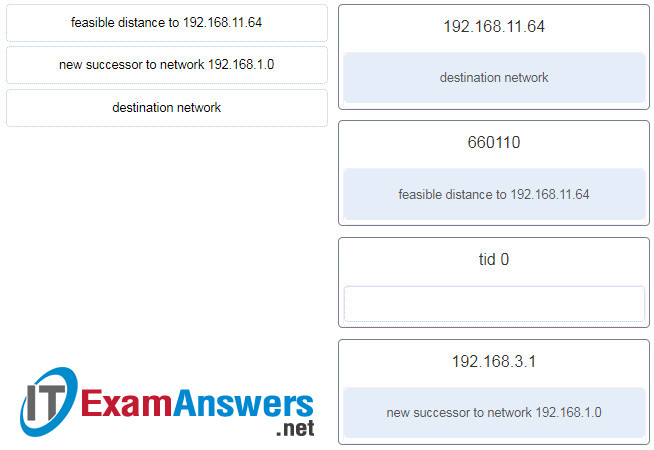
5. Refer to the exhibit. Match the description to the corresponding value used by the DUAL FSM. (Not all options are used.)
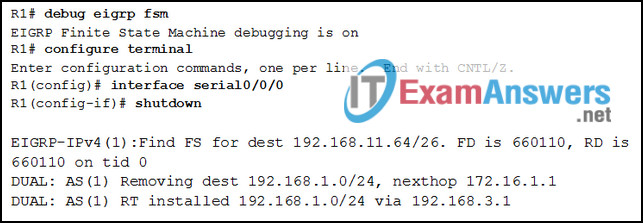
6. Refer to the exhibit. After configuring two-way redistribution, an administrator notices that none of the EIGRP routes are being advertised in the OSPF network. What is a possible reason that the routes are not being advertised?
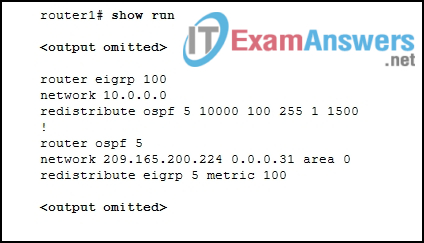
- The wrong EIGRP AS is being redistributed.
- The metric value is wrong for the redistribute command under OSPF.
- The metric value is wrong for the redistribute command under EIGRP.
- The subnets keyword is missing on the redistribute command under OSPF.
7. A network administrator is teaching a junior network engineer about EIGRP stub routers. Which two explanations can be given to the junior engineer about the subject? (Choose two.)
- An EIGRP stub router advertises only connected routes by default.
- An EIGRP stub router receives queries from EIGRP when a route goes active.
- An EIGRP stub router does not advertise routes that it learns from other EIGRP peers.
- An EIGRP stub router announces that it is a stub router within the EIGRP query packet.
- An EIGRP stub router can be configured only to receive routes.
8. A boundary router is performing mutual redistribution between OSPF and EIGRP. What process should be taken to have an external EIGRP route preferred over an OSPF route to the same destination network?
- Modify the administrative distance parameter for the external EIGRP routes to be set to 100.
- Modify the default seed metric to 21 for the source information from OSPF.
- Modify the administrative distance parameter for the internal EIGRP routes to be set to 180.
- Modify the default seed metric to 19 for the source information from OSPF.
9. Which two statements describe OSPF? (Choose two.)
- OSPF must be implemented in a three-layer area hierarchy.
- OSPF routers may have large routing tables if routes are not summarized.
- OSPF uses the SPF algorithm, which requires few CPU cycles.
- OSPF routers within an area have the same link-state information.
- OSPF performs automatic route summarization by default.
10. Refer to the exhibit. Which two conclusions can be derived from the output? (Choose two.)
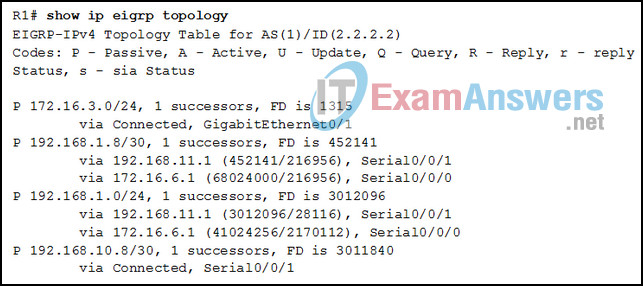
- Router R1 has two successors to the 172.16.3.0/24 network
- There is one feasible successor to network 192.168.1.8/30.
- The reported distance to network 192.168.1.0/24 is 41024256
- The neighbor 172.16.6.1 meets the feasibility condition to reach the 192.168.1.0/24 network.
- The network 192.168.10.8/30 can be reached through 192.168.11.1.
11. Refer to the exhibit. A network administrator has configured two-way redistribution on router R1. However, OSPF routes are not being redistributed into the EIGRP domain. What is causing this issue?
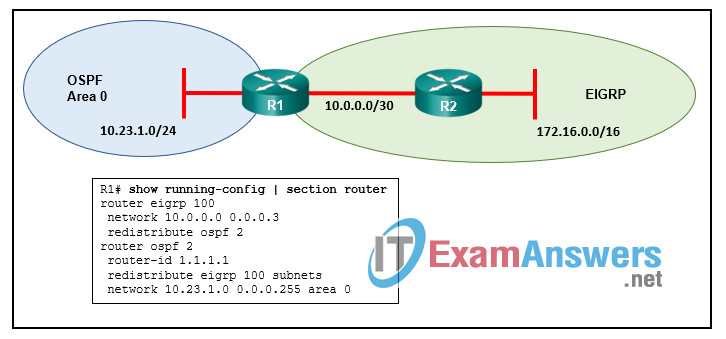
- The EIGRP process ID is incorrect and should be set to 2.
- The subnets keyword from the OSPF configuration should be removed.
- A seed metric is not provided for OSPF routes.
- An OSPF metric type has not been defined.
12. Refer to the exhibit. Router R1 has an OSPF neighbor relationship with the ISP router over the 192.168.0.32 network. The 192.168.0.36 network link should serve as a backup when the OSPF link goes down. The floating static route command ip route 0.0.0.0 0.0.0.0 S0/0/1 100 was issued on R1 and now traffic is using the backup link even when the OSPF link is up and functioning. Which change should be made to the static route command so that traffic will only use the OSPF link when it is up?
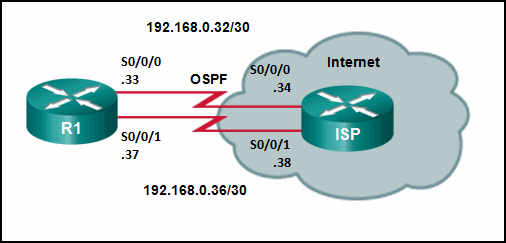
- Change the administrative distance to 120.
- Add the next hop neighbor address of 192.168.0.36.
- Change the destination network to 192.168.0.34.
- Change the administrative distance to 1.
13. Refer to the exhibit. OSPFv2 has been configured on router R1, and the router-id command has not been manually configured. When the network administrator reboots router R1, what will be the value of the OSPF router ID?
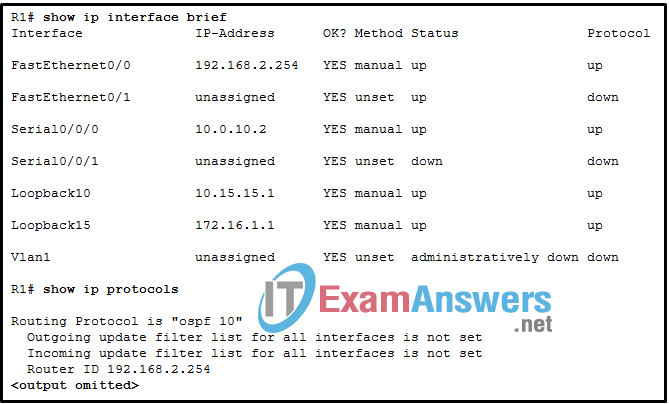
- 10.0.10.2
- 10.15.15.1
- 172.16.1.1
- 192.168.2.254
14. Refer to the exhibit. Based on the output shown, how are the OSPFv3 address families configured this router?
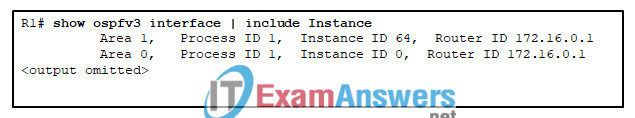
- The IPv6 address family is configured for both Area 0 and Area 1.
- The IPv4 address family is configured for Area 1, IPv6 for Area 0.
- The IPv4 address family is configured for Area 0, IPv6 for Area 1.
- The IPv4 address family is configured for both Area 0 and Area 1.
15. Refer to the exhibit. An administrator wants EIGRP on Router1 to load balance traffic to network 2001:db8:11:10::/64 across two interfaces. Currently traffic is using only interface GigabitEthernet0/1. A second route, not in the routing table, is available with a metric of 264000. What value is needed in the variance command to make EIGRP put the second route into the routing table?
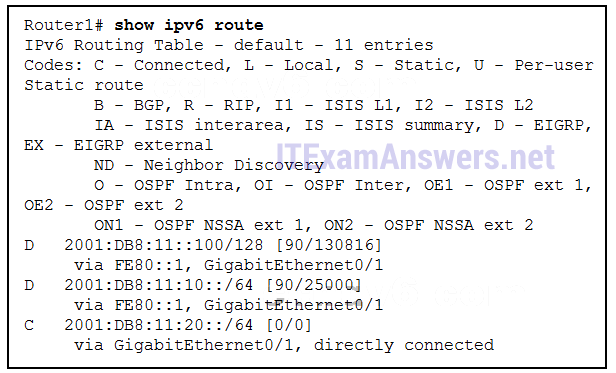
- 4
- 10
- 1
- 11
16. An administrator is troubleshooting failing EIGRP route exchanges on routers R1 and R2. On further investigation it is discovered that the route exchanges were failing because the routers had duplicate router IDs. The router ID for R1 is changed using the eigrp router-id command, but the problem persists. Which additional action must be taken to enable the routers to exchange routes?
- Change the timers on both routers to be the same.
- Change the router ID on R2.
- Clear the EIGRP process.
- Change the link-local address on R1 to a multicast address.
17. Refer to the exhibit. Considering that R2, R3, and R4 are correctly configured, why did R1 not establish an adjacency with R2, R3, and R4?
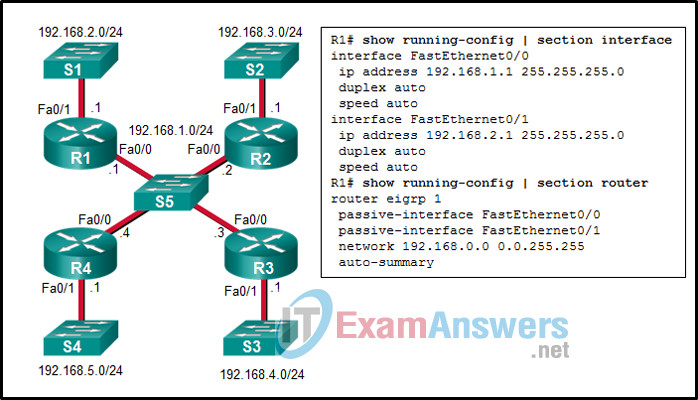
- because the automatic summarization is enabled on R1
- because the IPv4 address on Fa0/0 interface of R1 is incorrect
- because the Fa0/0 interface of R1 is declared as passive for EIGRP
- because there is no network command for the network 192.168.1.0/24 on R1
18. Refer to the exhibit. A network administrator verifies on an enterprise network that EIGRP query packets are delayed because of packet loss. The administrator issues the show ip protocols | include Active command to see the EIGRP active timer on a router. What can the administrator conclude from this output?
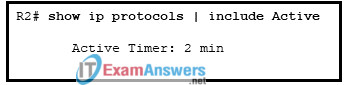
- EIGRP waits 120 seconds before sending a SIA query to neighbors that did not respond.
- The SIA state is declared for a neighbor without receiving an SIA reply after 4 minutes.
- Upon receipt of an SIA query from a neighbor router, the router needs to respond within 60 seconds to avoid being SIA state.
- This is the default value of the active timer.
19. When the distribute-list 1 in serial 0/0 command is used, which EIGRP routing updates would be permitted?
- Routing updates that are received on the serial 0/0 interface and permitted by ACL 1.
- Routing updates that are received on the serial 0/0 interface and permitted by prefix-list 1.
- Routing updates that are received on the serial 0/0 interface and permitted by route-map 1.
- Routing updates that are received on the serial 0/0 interface and permitted by offset-list 1.
20. Refer to the exhibit. What can the field engineer conclude about the EIGRP authentication between RouterA and RouterB?
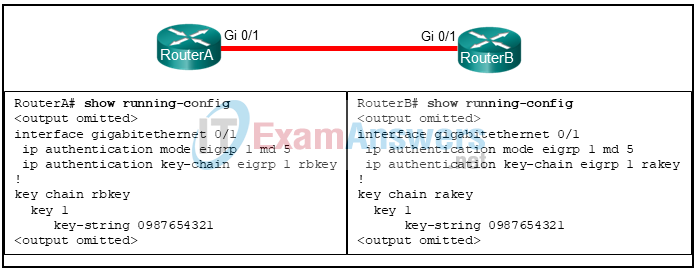
- Authentication will succeed and EIGRP updates can be exchanged.
- Authentication will fail because the key chain names do not match.
- Authentication will fail because the key chain names must match the router names.
- Authentication will fail because only one key is configured.
21. In which situation would a company implement an OSPF NSSA?
- when external routes need to connect to an OSPF area
- when one or more non-OSPF networks connect to an OSPF stub area
- when external routes need to be suppressed throughout all of the OSPF areas
- when one or more non-OSPF networks need to connect to the OSPF backbone
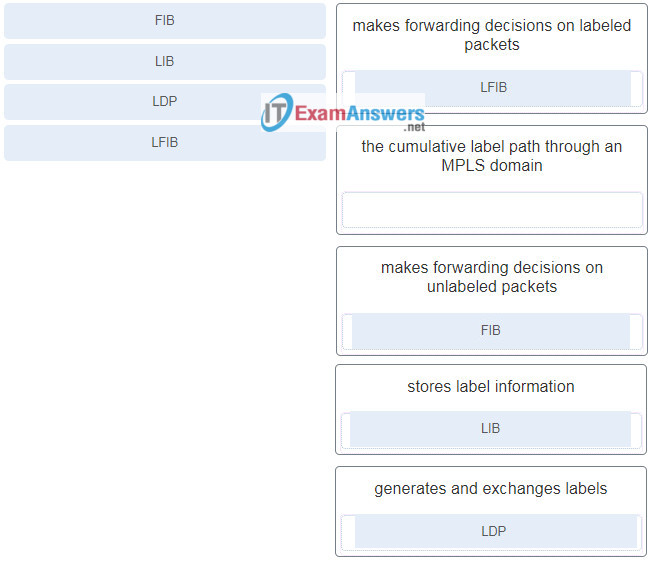
22. Match the LSR component with the description. (Not all options are used.)
23. Refer to the exhibit. Which two routers would perform penultimate hop popping? (Choose two.)
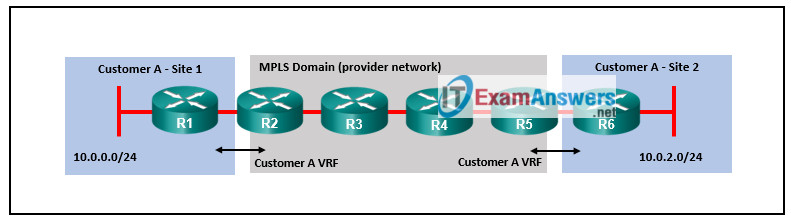
- R5
- R3
- R6
- R1
- R2
- R4
24. Which three protocols are involved in the establishment of an IPsec VPN tunnel? (Choose three.)
- Authentication Header
- Generic Routing Encapsulation
- Internet Key Exchange
- Tunnel Profile
- Encapsulating Security Payload
- Secure Socket Layer
25. A network administrator is teaching a junior engineer about MPLS Layer 3 VPNs. The administrator is explaining that a label stack is required for an MPLS domain to forward traffic. Which statement is accurate about a label stack?
- The LDP label is used by the egress router to determine customer specifics about the packet.
- VPN labels are learned from PE routers over the MP-IBGP peering.
- When the IP packet leaves the egress PE router, the VPN and LDP labels are attached to the IP packet.
- There are two labels attached to the IP packet; the first one is an LDP label, and the second one is the VPN label.
26. An administrator has chosen IPsec to encrypt DMVPN tunnels used to connect remote sites. How does the IPsec AH protocol differ from the IPsec ESP protocol?
- The AH protocol supports the DES and 3DES algorithms, but the ESP protocol only supports the AES algorithm.
- The AH protocol does not support encryption, but the ESP protocol does.
- The AH protocol does not support authentication, but the ESP protocol does.
- The AH protocol uses MD5, while the ESP protocol uses the SHA algorithm.
27. Refer to the exhibit. What is used on router R2 and router R5 to isolate the routes of customer A and B?
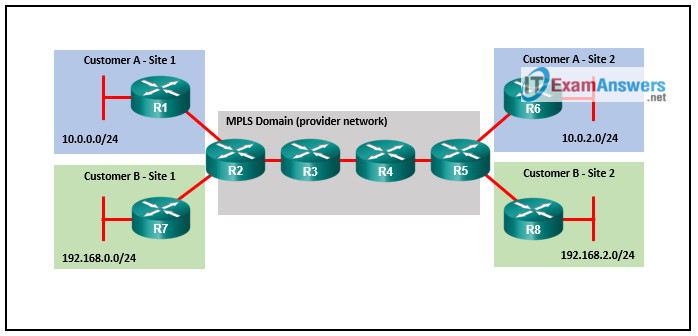
- BGP communities
- VRF instances
- DMVPN tunnels
- MP-BGP address families
28. A network administrator is configuring the tunnel interfaces for an IPv6 DMVPN implementation where IPv6 is going to be the tunneling protocol. What type of IPv6 address should the administrator configure on the tunnel interfaces?
- anycast
- unique local
- link-local
- unique global
29. Match the secure transport element to the description. (Not all options are used.)
30. What happens to an unlabeled IP packet that arrives at an LSR router and the intended outgoing interface is MPLS-enabled?
- A label is added and the packet is forwarded.
- The packet is sent to the LFIB for a forwarding decision.
- The packet is forwarded without a label to the next hop LSR.
- An error code is sent to the source CE router and the packet is dropped.
31. A network administrator reviewing the output of the show dmvpn command notes that the tunnel is in the IKE state. What is indicated by the IKE state?
- The line protocol of the DMVPN tunnel is down.
- IPsec has not established an IKE session.
- The DMVPN spoke router has not registered.
- IPsec security associations are not established.
32. What is an IPsec protocol that provides data confidentiality and authentication for IP packets?
- IKE
- RSA
- ESP
- AH
33. A network administrator is assigned the task of configuring front door VRF on a spoke router. What is the first configuration step the administrator needs to perform?
- Associate the FVRF instance with the DMVPN tunnel.
- Create the FVRF instance.
- Associate an interface with the VRF instance.
- Initialize the IP address family.
34. Refer to the exhibit. Router R1 is configured as shown. An administrative user attempts to use Telnet from router R2 to R1 using the interface IP address 10.10.10.1. However, Telnet access is denied. Which conclusion can be drawn from this scenario?
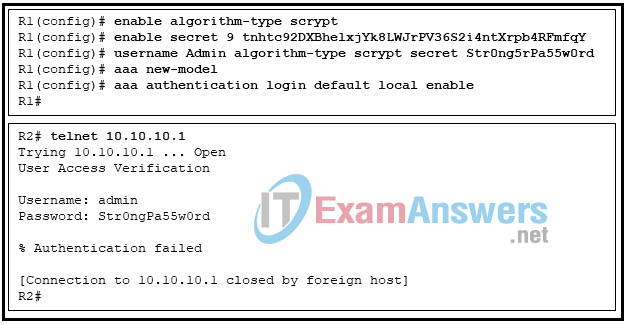
- The vty lines must be configured with the login authentication default command.
- The password was mistyped.
- The administrative user should use the username Admin .
- The aaa local authentication attempts max-fail command must be set to 2 or higher.
35. Refer to the exhibit. A network administrator configured a class map as shown, but the traffic is not being classified as desired. Which conclusion can be drawn from this configuration?

- The traffic would be subject to the implicit default class.
- The ACL-EIGRP is permitting the wrong IP multicast address.
- The traffic would never match the CoPP-CLASS class map.
- The ACL-ICMP access-list should be in a separate class map because it is not a routing protocol.
36. Which IPv6 First-Hop Security feature can block IPv6 traffic if this traffic is from an unknown origin?
- RA Guard
- Source Guard
- DHCPv6 Guard
- IPv6 ND inspection/snooping
37. Which mitigation technique would prevent rogue servers from providing false IPv6 configuration parameters to clients?
- enabling DHCPv6 Guard
- enabling RA Guard
- implementing port security on edge ports
- disabling CDP on edge ports
38. A network administrator is configuring a prefix list with the command
ipv6 prefix-list IPV6-1 seq 5 permit 2001:db8:abcd:20::/59 ge 62
Which network matches the prefix match specification?
- 2001:db8:ab:20::/62
- 2001:db8:abcd:2::/59
- 2001:db8:abcd:36::/62
- 2001:db8:abcd:60::/64
39. Which network prefix matches the prefix match pattern 2001:db8:cafe::/48 ge 48 le 52
- 2001:db80:cafe:12::/52
- 2001:db8:cafe:1001:/48
- 2001:db8:feed::/48
- 2001:db8::/52
40. A network administrator wants to verify the number of packets that have conformed to a specific class map used for CoPP. Which command should the administrator use?
- show class-map
- show access-list
- show policy-map
- show policy-map control-plane
41. Which two UDP port numbers may be used for server-based AAA RADIUS authentication? (Choose two.)
- 1812
- 1645
- 1813
- 1646
- 49
42. A junior network engineer needs to configure uRPF on a Cisco router interface to eliminate spoofed IP packets on a network. Which command should be used to configure uRPF mode when using asymmetric routing?
- ip verify unicast source reachable-via any
- ip verify unicast source reachable-via rx
- ip verify unicast source reachable-via rx allow-self-ping
- ip verify unicast source reachable-via rx allow-default
43. A network administrator is configuring a prefix list with the command
ipv6 prefix-list IPV6-1 seq 5 permit 2001:db8:abcd:30::/60 ge 61 le 63
Which two networks match the prefix match specification? (Choose two.)
- 2001:db8:abcd:30::/60
- 2001:db8:abcd:34::/62
- 2001:db8:abcd:20::/62
- 2001:db8:abcd:36::/63
- 2001:db8:abcd:60::/64
44. Which is the correct order of the four steps to configure CoPP on a Cisco router?
1) Configure extended ACLs to identify specific granular traffic.
2) Configure the class map to define interesting traffic.
3) Configure a policy map to apply actions to the identified traffic.
4) Configure a service policy to identify which interface should be activated for the service.
1) Configure a service policy to identify which interface should be activated for the service.
2) Configure extended ACLs to identify specific granular traffic.
3) Configure the class map to define interesting traffic.
4) Configure a policy map to apply actions to the identified traffic.
1) Configure extended ACLs to identify specific granular traffic.
2) Configure the class map to define interesting traffic.
3) Configure a service policy to identify which interface should be activated for the service.
4) Configure a policy map to apply actions to the identified traffic.
1) Configure a policy map to apply actions to the identified traffic.
2) Configure a service policy to identify which interface should be activated for the service.
3) Configure extended ACLs to identify specific granular traffic.
4) Configure the class map to define interesting traffic.
45. Which IPv6 First-Hop security feature learns and populates the binding table for stateless autoconfiguration addresses?
- DHCPv6 Guard
- IPv6 neighbor discovery inspection
- RA Guard
- Source Guard
46. Refer to the exhibit. PC-A is unable to receive an IPv6 address from the stateful DHCPv6 server. What is the problem?
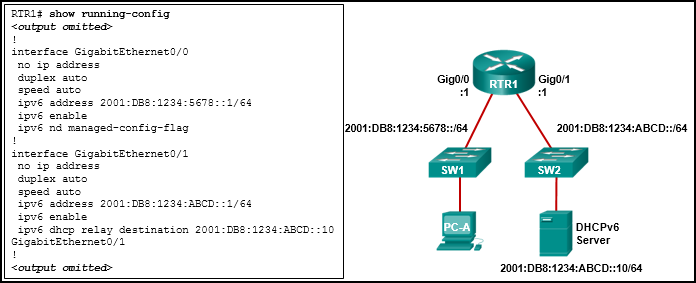
- The ipv6 dhcp relay command should be applied to interface Gig0/0.
- The ipv6 nd managed-config-flag should be applied to interface Gig0/1.
- The ipv6 dhcp relay command should use the link-local address of the DHCP server.
- The ipv6 nd managed-config-flag command should be ipv6 nd other-config-flag .
47. Refer to the exhibit. A network administrator is implementing stateful DHCPv6 operation for the company. However, the clients are not using the prefix and prefix-length information that is configured in the DHCP pool. The administrator issues a show ipv6 interface command. What could be the cause of the problem?
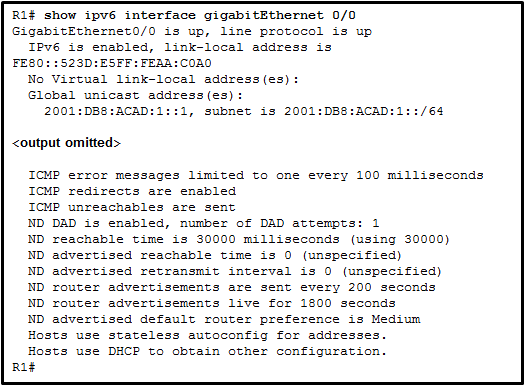
- No virtual link-local address is configured
- The Duplicate Address Detection feature is disabled
- The router is configured for SLAAC DHCPv6 operation
- The router is configured for stateless DHCPv6 operation
48. A network administrator is configuring SSH on a router. When verifying the configuration, the administrator notices that the SSH connection requests fail, but the Telnet connection requests from the same workstation are successful. Which two parts of the router configuration should be checked to try to locate the problem? (Choose two.)
- The transport input command is incorrect on the vty lines.
- An extended ACL that is referencing the port argument for SSH is misconfigured.
- The ip access-class command is missing.
- The password is misconfigured on the console line.
- A standard ACL is possibly blocking the workstation from access to the router.
49. Refer to the exhibit. Which two conclusions can be drawn from the syslog message that was generated by the router? (Choose two.)

- This message resulted from an unusual error requiring reconfiguration of the interface
- This message indicates that service timestamps have been configured
- This message indicates that the interface changed state five times
- This message is a level 5 notification message
- This message indicates that the interface should be replaced
50. Refer to the exhibit. A SNMP manager has IP address 172.16.1.120. The SNMP manager is unable to change configuration variables on the R1 SNMP agent. What could be the problem?
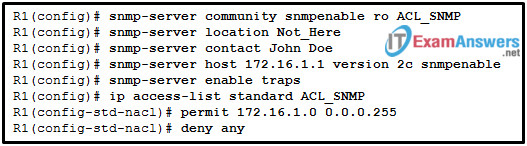
- The ACL of ACL_SNMP has not been implemented on an interface yet.
- The SNMP agent should have traps disabled.
- The IP address of the SNMP manager must be 172.16.1.1.
- The SNMP agent is not configured for write access.
51. Refer to the exhibit. The total number of packet flows is not consistent with what is expected by the network administrator. The results show only half of the flows that are typically captured for the interface. Pings between the router and the collector are successful. What is the reason for the unexpected results?
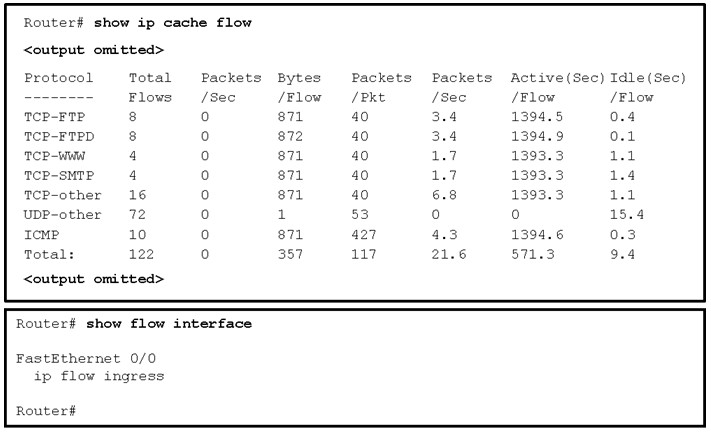
- Interface Fa0/0 is not configured as the source of the packets sent to the collector.
- The interface is shutdown.
- The Netflow collector IP address and UDP port number are not configured on the router.
- The router is not configured to monitor outgoing packets on the interface.
52. A host PC is attempting to lease an address through DHCP. What message is sent by the server to let the client know it is able to use the provided IP information?
- DHCPDISCOVER
- DHCPOFFER
- DHCPREQUEST
- DHCPACK
- DHCPNACK
53. A network technician opens PuTTY to connect to a Cisco switch. The technician sets PuTTY with the IP address of the switch and port 23. However, connections to the switch are always declined. What is a possible cause for this issue?
- The transport input ssh command has been configured on vty lines.
- Only Telnet is allowed to connect to the switch.
- The domain name of the switch should be used in PuTTY.
- An ACL is applied on the console port that blocks the PC that the technician uses.
54. Which two types of probes can be configured to monitor traffic by IP SLA within a network environment? (Choose two.)
- voice quality scores
- website upload time
- SNMP traps
- packet loss
- syslog messages
55. A network administrator has verified that timestamps are not appearing with syslog messages on a router. What is the most likely reason for this?
- The router has the wrong time set, according to the output of the show clock command.
- The terminal monitor command was not issued on the router.
- The no service timestamps command was executed on the router.
- Syslog was not correctly configured.
56. Refer to the exhibit. A network administrator has configured router R1 to send syslog messages to the syslog server. Why is the syslog server unable to receive any logging messages?
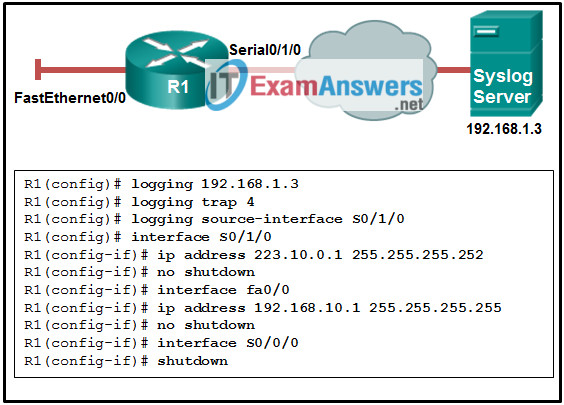
- The IP address of the server is not configured properly.
- The source interface is not configured correctly.
- The syslog server should be directly connected.
- The logging level should be set to 5.
57. Refer to the exhibit. Router R1 was configured by a network administrator to use SNMP version 2. The following commands were issued:
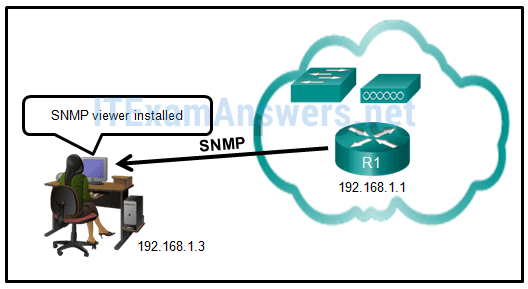
R1(config)# snmp-server community batonaug ro SNMP_ACL
R1(config)# snmp-server contact Wayne World
R1(config)# snmp-server host 192.168.1.3 version 2c batonaug
R1(config)# ip access-list standard SNMP_ACL
R1(config-std-nacl)# permit 192.168.10.3
Why is the administrator not able to get any information from R1?
- The snmp-server enable traps command is missing.
- There is a problem with the ACL configuration.
- The snmp-server community command needs to include the rw keyword.
- The snmp-server location command is missing.
58. A company uses the method SLAAC to configure IPv6 addresses for the workstations of the employees. A network administrator configured the IPv6 address on the LAN interface of the router. The interface status is UP. However, the workstations on the LAN segment did not obtain the correct prefix and prefix length. What else should be configured on the router that is attached to the LAN segment for the workstations to obtain the information?
- R1(config)# ipv6 dhcp pool
- R1(config-if)# ipv6 enable
- R1(config)# ipv6 unicast-routing
- R1(config-if)# ipv6 nd other-config-flag
59. Refer to the exhibit. A SNMP manager is using the community string of snmpenable and is configured with the IP address 172.16.10.1. The SNMP manager is unable to read configuration variables on the R1 SNMP agent. What could be the problem?
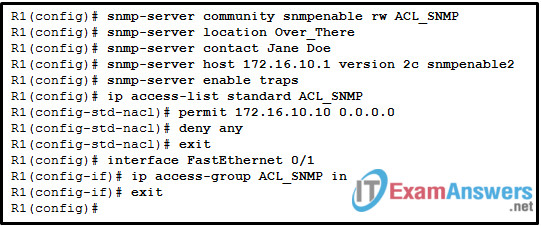
- The incorrect community string is configured on the SNMP manager.
- The community of snmpenable2 is incorrectly configured on the SNMP agent.
- The ACL is not permitting access by the SNMP manager.
- The SNMP agent is not configured for read-only access.
60. A network student intern is asked to clean the system settings and upgrade the IOS on a Cisco router. The student uses a Windows 10 laptop and a rollover cable to connect to the console port of the router. The student powers on the router and opens the TeraTerm program. However, the program does not receive any response from the router. What are two possible causes for this problem? (Choose two.)
- The IP address was misconfigured in TeraTerm.
- The communication settings were misconfigured on TeraTerm.
- The wrong password was used to connect to the console port.
- The student entered an incorrect enable password.
- The wrong COM port was selected in TeraTerm.
61. A network administrator has configured a router for stateless DHCPv6 operation. However, users report that workstations are not receiving DNS server information. Which two router configuration lines should be verified to ensure that stateless DHCPv6 service is properly configured? (Choose two.)
- The domain-name line is included in the
ipv6 dhcp poolsection. - The dns-server line is included in the
ipv6 dhcp poolsection. - The
ipv6 nd other-config-flagis entered for the interface that faces the LAN segment. - The address prefix line is included in the
ipv6 dhcp poolsection. - The
ipv6 nd managed-config-flagis entered for the interface that faces the LAN segment.
62. Refer to the exhibit. From what location have the syslog messages been retrieved?
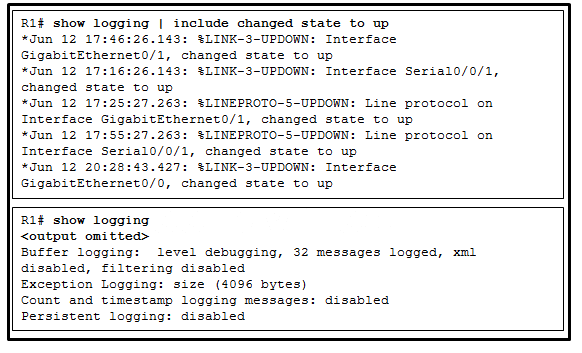
- syslog server
- syslog client
- router RAM
- router NVRAM
63. Refer to the exhibit. A network administrator issues the show run | section username|aaa|line|radius command to verify an AAA configuration on a Cisco router. Which two conclusions can be drawn from the command output? (Choose two.)
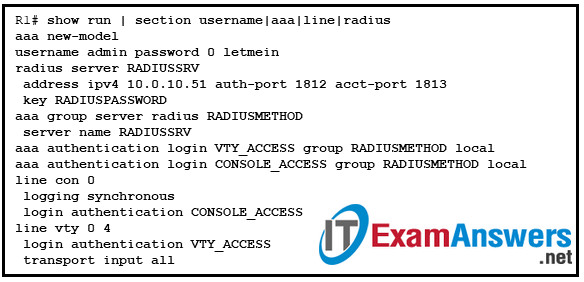
- The router must use Cisco default ports for authentication and accounting to connect to a RADIUS server.
- Authentication for the vty lines is using the default authentication method.
- Authentication for the console line will use local authentication as a fallback method if the RADIUS server is not available.
- A missing ip radius source-interface command on RADIUS server settings may prevent the router from using the services of the server.
- The Cisco router can use the radiuspassword pre-shared key to connect to a RADIUS server.
64. Which IPv6 First-Hop Security feature is used to block unwanted advertisement messages from unauthorized routers?
- IPv6 ND inspection
- DHCPv6 Guard
- Source Guard
- RA Guard
65. An administrator is configuring an extended ACL for BGP route selection. Which ACE should the administrator issue to permit only 10.0.0.0 networks with a /16 through /32 prefix?
- permit ip 10.0.0.0 255.255.255.255 255.255.255.0 0.0.0.255
- permit ip 10.0.0.0 0.0.255.255 255.255.255.0 0.0.0.255
- permit ip 10.0.0.0 0.0.0.255 0.0.0.255 255.255.255.0
- permit ip 10.0.0.0 0.0.255.255 255.255.0.0 0.0.0.255
66. Refer to the exhibit. The administrator can ping the S0/0/1 interface of RouterB but is unable to gain Telnet access to the router by using the password cisco123. What is a possible cause of the problem?
- AAA authorization is not configured.
- The administrator does not have enough rights on the PC that is being used.
- The administrator has used the wrong password.
- The wrong vty lines are configured.
67. Which command, if applied on an OSPF router, would give a Gigabit Ethernet interface a lower cost than a Fast Ethernet interface?
- (config-router)# auto-cost reference-bandwidth 1000
- (config-if)# bandwidth 100
- (config-if)# ip ospf priority 1
- (config-if)# ip ospf cost 100
68. Refer to the exhibit. Which two routes will be advertised to the router ISP if autosummarization is disabled? (Choose two.)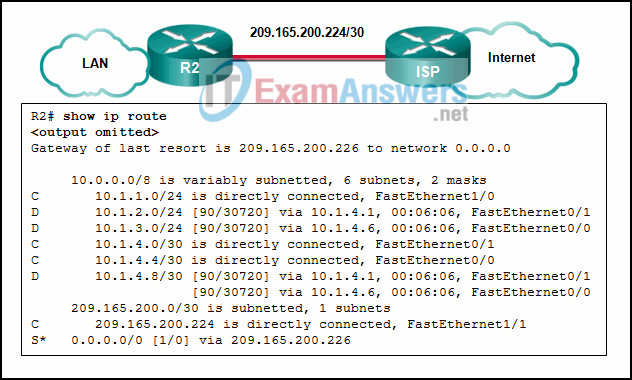
- 10.1.0.0/16
- 10.1.2.0/24
- 10.1.4.0/24
- 10.1.4.0/28
- 10.1.4.0/30
69. Refer to the exhibit. A network administrator issues the show bgp ipv4 unicast 10.1.1.128 command on router R2 to verify the network 10.1.1.128 in the BGP table. The administrator notices that there are two paths to reach the network and the path through the neighbor 1.1.1.1 is the best-path. Which configuration step will allow the administrator to change the best path to use neighbor 3.3.3.3?
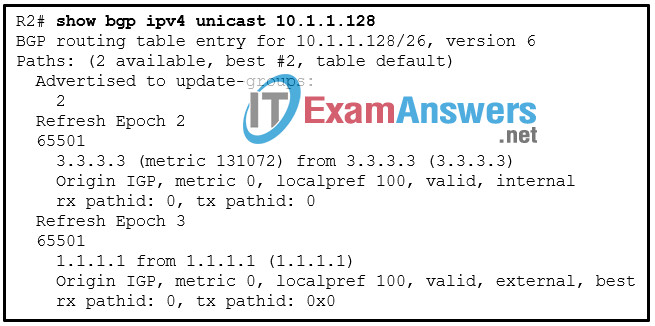
- Set the multi-exit discriminator to 75 for the path through 3.3.3.3.
- Set the origin code to i for the path through 3.3.3.3.
- Set the local preference to 200 for the path through 3.3.3.3.
- Change the metric value from 131072 to 32768 for the path through 3.3.3.3.
70. The show ip eigrp topology command output on a router displays a successor route and a feasible successor route to network 192.168.1.0/24. In order to improve network convergence, what does EIGRP do when the primary route to this network fails?
- The router sends query packets to all EIGRP neighbors for a better route to network 192.168.1.0/24.
- DUAL immediately recomputes the algorithm to calculate the next backup route.
- Packets that are destined for network 192.168.1.0/24 are sent out the default gateway instead.
- The backup route to network 192.168.1.0/24 is installed in the routing table.
71. Refer to the exhibit. A network engineer has issued the verification command while troubleshooting a routing loop on the network. What is the error in the configuration?
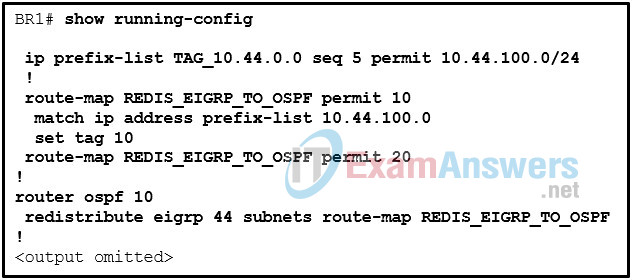
- The route-map is dropping all other routes that do not match the prefix list TAG_10.44.100.0.
- The match ip address command refers to the incorrect prefix list.
- The redistribute command is configured to filter routes using the route map instead of the prefix list.
- The route-map sequence 20 is missing the match and set statements.
72. Refer to the exhibit. An administrator is trying to configure R1 to run OSPFv3 but the neighbor adjacency is not forming with the router connected to Fa0/0. What is the cause of the problem?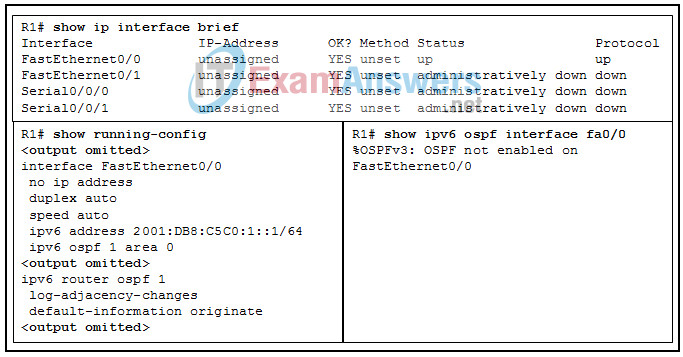
- No router ID has been configured.
- FastEthernet0/0 has been configured as a passive interface.
- A link-local address has not been configured on interface FastEthernet0/0.
- The OSPF process ID and area values are backwards in the interface configuration.
73. A network administrator is configuring a BGP router with the neighbor 10.12.1.2 maximum-prefix 20 75 command. What will happen when the peer at 10.12.1.2 advertises 15 routes?
- The router moves the peer to the Idle state and closes the BGP session.
- The router transitions to listening mode and does not install any new routes into the BGP table.
- The router drops any further advertisements from the peer.
- The router sends a warning message to the peer.
74. Refer to the exhibit. A network engineer has issued the commands shown on a boundary router. What are two results of the network engineer issuing this command? (Choose two.)

- The internal administrative distance for EIGRP AS 66 has been changed to 66.
- The internal administrative distance has changed to 66 and the external administrative distance has changed to 90 for routes sourced from the router with IP 172.16.55.1.
- The router has created the EIGRP autonomous system of 66.
- The network 172.16.55.0 has a modified internal metric of 66.
- The internal administrative distance has been changed to 66 for routes sourced from the router with IP 172.16.55.1 and matching ACL 90.
75. A router is participating in an OSPFv2 domain. What will always happen if the dead interval expires before the router receives a hello packet from an adjacent DROTHER OSPF router?
- OSPF will run a new DR/BDR election.
- SPF will run and determine which neighbor router is “down”.
- A new dead interval timer of 4 times the hello interval will start.
- OSPF will remove that neighbor from the router link-state database.
Explanation: On Cisco routers the default dead interval is 4 times the hello interval, and this timer has expired in this case. SPF does not determine the state of neighbor routers; it determines which routes become routing table entries. A DR/DBR election will not always automatically run; this depends on the type of network and on whether or not the router no longer up was a DR or BDR.
76. Which type of OSPF LSA(s) can be represented with the label O*E2 in a routing table?
- type 1 and type 2 LSAs
- type 3 and type 4 LSAs
- type 5 LSA only
- type 4 and type 5 LSAs
77. In addition to configuring an IPv4 address and mask, and issuing the no shutdown command, which two additional commands does a network technician have to issue on the interface of a Cisco router to enable OSPFv3 address families for IPv4 on that interface? (Choose two.)
- router ospfv3 1
- ipv6 ospf 1
- ipv6 enable
- ipv6 router ospf 1
- ospfv3 1 area 0 ipv4
- router ospf 1
78. Which two statements correctly describe OSPF type 3 LSAs? (Choose two.)
- Type 3 LSAs are known as autonomous system external LSA entries.
- Type 3 LSAs are known as router link entries.
- Type 3 LSAs are used for routes to networks outside the OSPF autonomous system.
- Type 3 LSAs are used to update routes between OSPF areas.
- Type 3 LSAs are generated without requiring a full SPF calculation.
79. Which two OSPFv3 LSA types are used to advertise IPv6 prefixes to neighbors? (Choose two.)
- LSA type 4 – interarea router
- LSA type 5 – AS-external
- LSA type 7 – NSSA
- LSA type 8 – link-local LSA
- LSA type 9 – intra-area prefix LSA
80. Refer to the exhibit. What is the function of the Null0 route in the outputs displayed for R1 and R2?
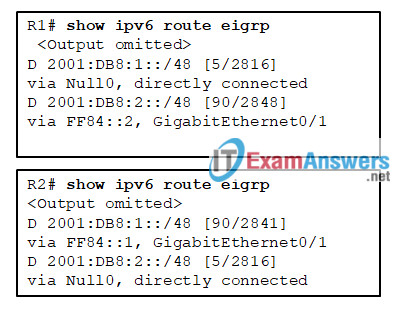
- to advertise the local /48 summary route
- to force advertisements of only the /64 route entries to the neighbor routers
- to force advertisements of only the /128 route entries to the neighbor routers
- to invoke the split horizon rule to prevent routing loops
81. Which technology creates a mapping of public IP addresses for remote tunnel spokes in a DMVPN configuration?
- NHRP
- IPsec
- NAT
- ARP
82. A network administrator needs to learn information about EIGRP load balancing to configure an EIGRP network. Which piece of information is accurate about this subject?
- The variance multiplier is obtained by dividing the successor route metric by the feasible successor metric.
- Any feasible distance of a feasible successor with a metric above the EIGRP variance value is installed into the RIB.
- The maximum equal-cost multipathing routing for EIGRP is four routes.
- The EIGRP variance value is the feasible distance for a route multiplied by the EIGRP variance multiplier.
83. Refer to the exhibit. Directly connected networks configured on router R1 are not being shared with neighboring routers through OSPFv3. What is the cause of the issue?

- IPv6 OSPF routing is not enabled.
- The routes are not enabled in the OSPF advertisement.
- There are no IPv4 addresses configured on the interfaces.
- There are no network statements for the routes in the OSPF configuration.
84. Refer to the exhibit. R2 uses loopback0 interface 2.2.2.2 and R5 uses loopback0 interface 5.5.5.5 in the neighbor ip_address remote-as as_number statement in their respective configurations. A network administrator issues the show bgp ipv4 unicast summary command on R2. Which statement describes the adjacency state of R5?
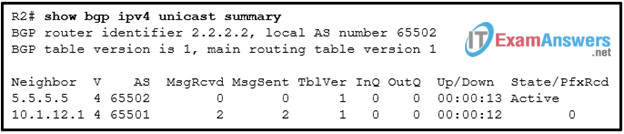
- R2 uses the default route to reach R5.
- There is no route in the routing table of R2 to reach R5.
- An adjacency is formed between R2 and R5, but there is no message transmitted.
- An open message is sent to R5, but no response is received.
85. Refer to the exhibit. A network administrator is configuring BGP on router RT2, but RT2 cannot establish a peer relationship with RT1. What is the cause of the problem?
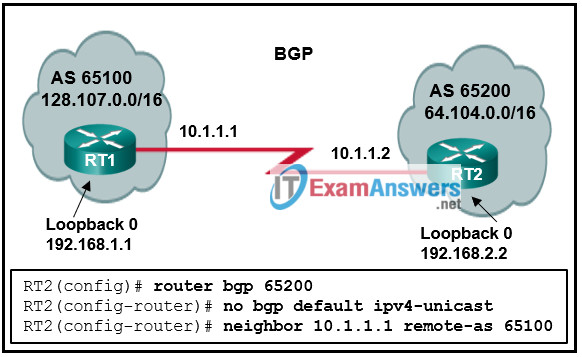
- An IPv4 multicast address should be used in the neighbor statement.
- The network statement for the network 192.168.2.2/32 is missing.
- The network statement for the network 17.0.0.0/16 is missing.
- The IPv4 address family has not been activated.
86. In order to limit spoofed packets on a network, a network administrator is configuring uRPF on a Cisco router interface with the ip verify unicast source reachable-via rx command. After the configuration is completed, the administrator observes that valid packets are being dropped. What may be causing this packet discard?
- The uRPF is configured with loose mode and asymmetric routing occurs.
- The uRPF is configured with strict mode and symmetric routing occurs.
- The return traffic used a different path to that used by the source traffic.
- The same path is used for the source traffic and the return traffic.
87. A network engineer is implementing redistribution of two routing protocols across a network topology. Under which situation would there be minimal concern of network visibility being hidden from the destination routing source?
- when there is only one point of redistribution between two sources
- while performing multipoint redistribution between multiple protocols
- while performing multipoint redistribution between a single routing protocol of varying process-id or autonomous-system number
- when there are at least two points of redistribution in the network
88. Which two network prefixes match the prefix match pattern of 172.16.0.0/12 ge 16? (Choose two.)
- 172.16.127.0/12
- 172.31.0.0/16
- 172.16.0.0/16
- 172.16.0.0/12
- 172.16.96.0/24
89. Refer to the exhibit. A junior administrator issues the show ip protocol command while troubleshooting missing NSSA OSPF routes. What is the most likely cause for the missing OSPF routes?
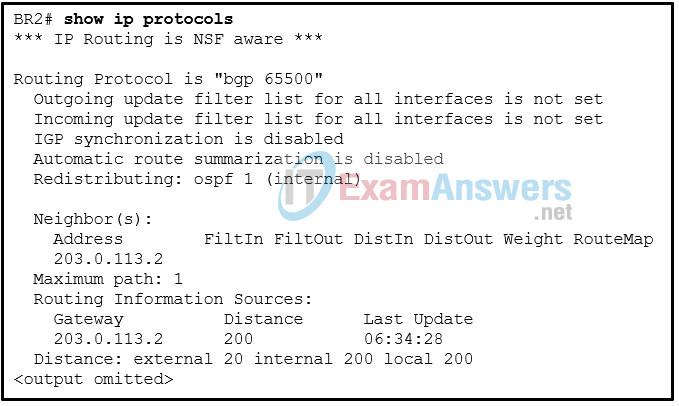
- The BGP configuration is not using automatic summarization.
- The BGP configuration is configured for IBGP instead of EBGP.
- The redistribute command is not issued with a match keyword.
- The redistribute command is not issued with a metric keyword.
90. Refer to the exhibit. Router R1 is seeing routes that are advertised by router R2, and R2 is seeing routes that are advertised by R1. OSPF is being used by the company that owns and controls routers R1 and R2. Which two situations are evident with this L3 MPLS VPN topology? (Choose two.)
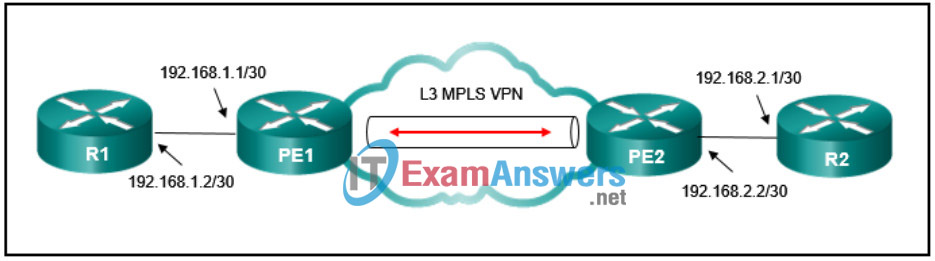
- Router R1 has an established OSPF neighbor relationship with R2.
- Any other P routers within the cloud that are part of the MPLS domain between R1 and R2 use BGP as a routing protocol.
- Router R1 has an established OSPF neighbor relationship with PE1.
- Routers R1 and R2 redistribute routes into MP-BGP.
- The PE routers use MP-IBGP to exchange the routes between R1 and R2.
91. Refer to the exhibit. A two-way redistribution is configured on router R2 between the EIGRP and the OSPF domains. The show ip route command output taken on R3 reveals that the network 10.10.10.16/28 is not installed in the routing table. What could be the problem?
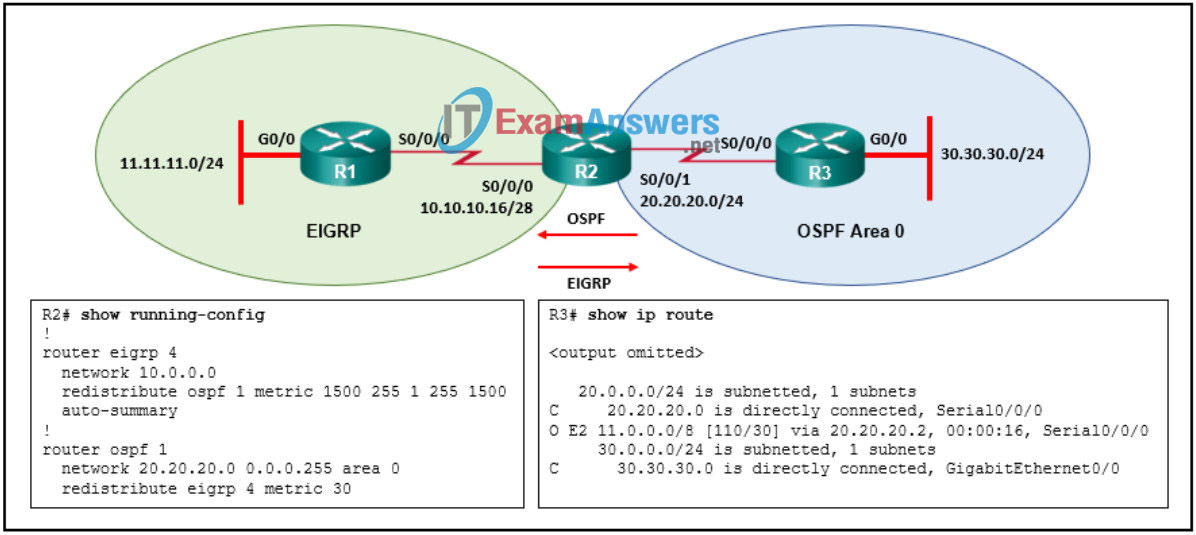
- A summary-address command should be given under the OSPF routing process.
- A metric-type command is missing from the redistribution statement under OSPF routing process on R2.
- A no auto-summary command should be used under the EIGRP configuration on R2.
- A subnets command keyword is missing from the redistribution statement under the OSPF routing process on R2.
92. A network student has to prepare a paper about EIGRP network summarization, but the student does not know much about summarization metrics. What piece of information is accurate about EIGRP summarization?
- The summarizing router uses the highest metric of the component routes in the summary aggregate prefix.
- The path metric for the summary aggregate is based on an average of the path attributes of the component routers.
- Every time a matching component route for the summary aggregate is added or removed, downstream routes must run the DUAL again.
- EIGRP path attributes are inserted into the summary route so that downstream routers can calculate the correct path metric for the summarized prefix.
93. Refer to the exhibit. A network administrator has configured OSPF in the topology as shown. What is the preferred path to get from the LAN network that is connected to R1 to the LAN network that is connected to R7?
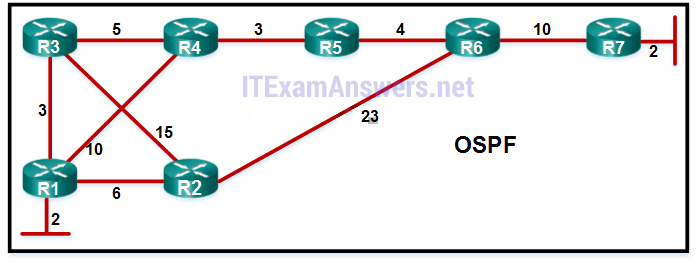
- R1-R2-R6-R7
- R1-R3-R4-R5-R6-R7
- R1-R4-R5-R6-R7
- R1-R3-R2-R6-R7

A network engineer is implementing redistribution of two routing protocols across a network topology. Under which situation would there be minimal concern of network visibility being hidden from the destination routing source?
o while performing multipoint redistribution between a single routing protocol of varying process-id or autonomous-system number
o when there are at least two points of redistribution in the network
o while performing multipoint redistribution between multiple protocols
o when there is only one point of redistribution between two sources
Added, thanks for your sharing
Admin
Do you have an update as to what happened to this site? We used to be able to post and notify people if the questions were still valid and now I don’t see that page anymore.
it is a valid ? or any update
any updates
Can we expect any update soon?
Hi,
Are there any updates regarding the sump ?
Regards,
Mina Kozman