1. Which routing protocol enables authentication by default?
- EIGRP
- OSPFv2 with key chains
- Named EIGRP
- No routing protocol enables authentication by default.*
- OSPFv2
2. Which statement about plain-text authentication is true?
- Plain-text authentication is considered to be insecure and should not be used.*
- Plain-text authentication is supported by EIGRP, and OSPFv2.
- Plain-text authentication peers require different passwords to authenticate the routing updates.
- Plain-text authentication use the key and hashing algorithm to produce a signature.
3. Which two authentication methods does EIGRP support? (Choose two.)
- None of the above
- SHA*
- Plain text
- IPsec encryption
- MD5*
4. The output of the show running-configuration command displays the following line: enable secret 4 JpAg4vBxn6wTb6NE3N1p0wfUUZzR6eOcVUKUFftxEyABased on the output, which statement is true regarding the enable password?
- It was encrypted using the password service-encryption command.
- It is encrypted using SHA256.*
- It was encrypted using the service password-encryption command.
- It is encrypted using IPsec.
- It is encrypted using MD5.
5. The output of the show ip ssh command displays “SSH Enabled – version 2”. Based on this output, which statement is true?
- When SSH is enabled, this is the default SSH version.
- This is also known as “compatibility mode” because it supports both SSHvI and SSHv2.
- The device was configured with the ip ssh version 2 command.*
- None of the above.
- This is the original version but has known vulnerabilities.
6. When implementing logging, it is also important that dates and times are accurate and synchronized across all the network infrastructure devices using _______.
- ntp
- NTP
- network time protocol
- Network Time Protocol *
- NETWORK TIME PROTOCOL
7. The _________ privileged EXEC command can be used to manually create an archive of the running configuration file.
- archive config *
8. Which statement about SNMP is true?
- SNMPv1, SNMPv2, and SNMPv3 use community strings. SNMPv2 supports the use of read-write community strings to encrypt SNMP messages.
- SNMPv1 uses community strings to encrypt SNMP messages.
- SNMPv1 is the most secure version to use.
- SNMPv3 can provide authenticity, integrity, and confidentiality.*
9. Refer to the exhibit. Based on the configuration, which statement is true about the archive command?
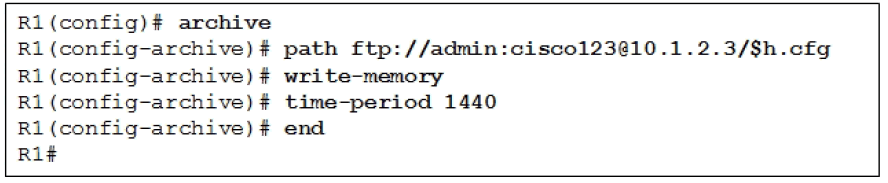
- The startup configuration file is automatically saved every 24 hours.
- The write-memory archive configuration command saves the archive every time the running configuration is saved to NVRAM.
- The FTP path specified has a folder named admin:cisco on a server located at 10.1.2.3.
- To save the configuration, the administrator needs to use the config archive privileged EXEC command.
- The only required parameter is the path archive configuration command.*
10. What does the accept-lifetime 04:00:00 Jan 10 2015 infinite command do?
- specifies that a key is acceptable for use on received packets until January 10, 2015
- specifies that a key is acceptable for use on sent packets from January 10, 2015 onward
- specifies that a key is acceptable for use on received packets from January 10, 2015 onward*
- specifies that a key is acceptable for use on sent packets until January 10, 2015
11. Which VRF-lite statement is true?
- VRF-lite is the deployment of VRF without MPLS.*
- VRF-lite Layer 3 interfaces can belong to more than one VRF at any time.
- VRF-lite cannot be used with Cisco Easy Virtual Network (EVN).
- VRF-lite operates at Layer 3 while VRF operates at Layer 2.
12. Which of the following is an IP-based network solution that takes advantage of existing VRF-lite technology to simplify Layer 3 network virtualization, improve support for shared services, and enhance management and troubleshooting.
- VPN Routing and Trunking (VRT)
- Virtual Routing and Forwarding (VRF)
- Cisco Easy VPN
- Virtual Routing and Trunking (VRT)
- VPN Routing and Forwarding (VRF)
- Cisco Easy Virtual Network (EVN)*
13. Using SSH, implementing logging, and securing SNMP are all tasks related to securing which router operational plane?
- Management plane*
- Protocol plane
- Data plane
- Forwarding plane
- Control plane
- Air plane
14. Using routing protocol authentication is a task related to securing which router operation plane?
- Management plane
- Control plane*
- Forwarding plane
- Protocol plane
- Air plane
- Data plane
15. Refer to the exhibit. Which AAA authentication protocol operation is being illustrated in the exhibit?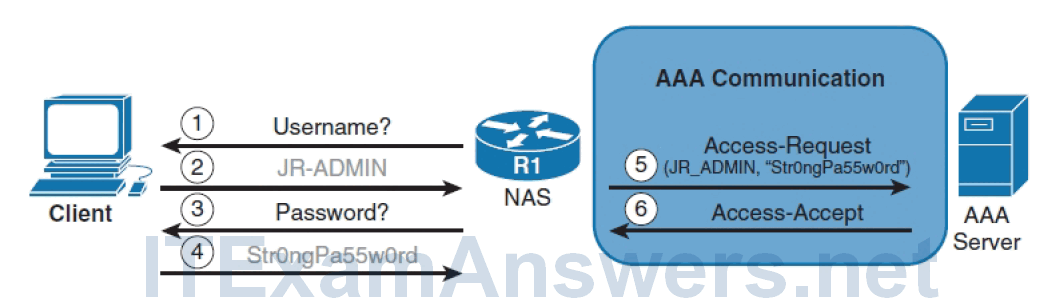
- RADIUS*
- Kerberos
- Local
- TACACS+
- Plain text
Download PDF File below:
