Check answers here:
Chapters 27 – 29: Virtualization, Automation, and Programmability Exam Answers
Quiz-summary
0 of 39 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
Information
CCNP ENCOR v8 Chapters 27 – 29: Virtualization, Automation, and Programmability Test Online
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 39 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- Answered
- Review
-
Question 1 of 39
1. Question
1 pointsWhich term defines a software emulation of a physical server with an operating system?Correct
Incorrect
Hint
A virtual machine is a software emulation of a physical server including a CPU, memory, network interface, and operating system. -
Question 2 of 39
2. Question
1 pointsWhat component enables VMs within a virtualized server environment to communicate with each other and with external networks?Correct
Incorrect
Hint
In a virtualized server the vSwitch is connected to external networks through physical NICs (pNICs) and to VMs through virtual NICs (vNICs). -
Question 3 of 39
3. Question
1 pointsWhat are three responsibilities of the the NFV virtualized infrastructure manager? (Choose three.)Correct
Incorrect
Hint
Within the ETSI NFV architectural framework, it is the virtualized infrastructure manager that is responsible for managing and controlling the NFVI hardware resources of compute, storage, and network, and the virtualized resources. -
Question 4 of 39
4. Question
1 pointsWhich two components of the ETSI NFV architectural framework make up the NFV management and orchestration (MANO)? (Choose two.)Correct
Incorrect
Hint
In the ETSI NFV architectural framework the NFV orchestrator and VNF manager together are known as NFV management and orchestration (MANO). -
Question 5 of 39
5. Question
1 pointsIn an Open vSwitch (OVS) architecture, which component resides in the kernel space and forwards packets from the network stack to the vNIC of the VM?Correct
Incorrect
Hint
The vSwitch is responsible for moving data from the network stack and sending it to the vNIC of the VM. -
Question 6 of 39
6. Question
1 pointsWhat term is used to define the software process that creates VMs and performs hardware abstraction to support VMs?Correct
Incorrect
Hint
The hypervisor is virtualization software that performs hardware abstraction. It allows multiple VMs to run concurrently in the virtual environment. -
Question 7 of 39
7. Question
1 pointsWhat function does Cisco DNA Center provide as part of a Cisco enterprise NFV solution?Correct
Incorrect
Hint
The Cisco DNA Center provides the VNF management and orchestration (MANO) functionality to the Cisco Enterprise NFV solution. -
Question 8 of 39
8. Question
1 pointsQuestion as presented: Match each VNF term to its description.Correct
Incorrect
-
Question 9 of 39
9. Question
1 pointsWhat is a limitation when PCI Passthrough is deployed?Correct
Incorrect
Hint
PCI Passthrough was developed to increase packet throughput in an OVS environment. However, the downside to PCI Passthrough is that each pNIC is dedicated to a single VNF. -
Question 10 of 39
10. Question
1 pointsWhat is the function provided by the OSS/BSS components of the ETSI NFV architectural framework?Correct
Incorrect
Hint
In the ETSI NFV achitectureal framework, the operations support system (OSS) supports network systems and services while the business support system (BSS) runs business operations. -
Question 11 of 39
11. Question
1 pointsWhich two HTTP functions correspond to the UPDATE function in CRUD? (Choose two.)Correct
Incorrect
Hint
CRUD is an acronym that stands for CREATE, READ, UPDATE, and DELETE. The HTTP functions that correspond to CRUD functions are as follows:- GET -> READ
- POST -> CREATE
- PUT/PATCH -> UPDATE
- DELETE -> DELETE
-
Question 12 of 39
12. Question
1 pointsWhat are two syntax rules for writing a JSON array? (Choose two.)Correct
Incorrect
Hint
A JSON array is a collection of ordered values within square brackets [ ]. The values in the array are separated by a comma. For example “users” : [“bob”, “alice”, “eve”]. -
Question 13 of 39
13. Question
1 pointsRefer to the exhibit. Which data format is used to represent the data for network automation applications?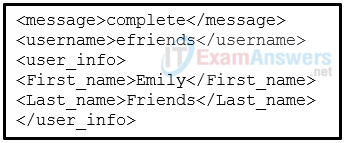 Correct
Correct
Incorrect
Hint
Common data formats that are used in many applications including network automation and programmability include these: JavaScript Object Notation (JSON) – In JSON, the data known as an object is one or more key/value pairs enclosed in braces { }. Keys must be strings within double quotation marks ” “. Keys and values are separated by a colon. eXtensible Markup Language (XML) – In XML, the data is enclosed within a related set of tags data. YAML Ain’t Markup Language (YAML) – In YAML, the data known as an object is one or more key value pairs. Key value pairs are separated by a colon without the use of quotation marks. YAML uses indentation to define its structure, without the use of brackets or commas. -
Question 14 of 39
14. Question
1 pointsWhich API does the Cisco DNA Center controller use for user authentication?Correct
Incorrect
Hint
The HTTP POST function is used to send the credentials to the Cisco DNA Center controller. The Cisco DNA Center uses basic authentication to pass a username and password to the Cisco DNA Center Token API to authenticate users. -
Question 15 of 39
15. Question
1 pointsRefer to the exhibit. What is the meaning of the config false statement under the observed-speed leaf node?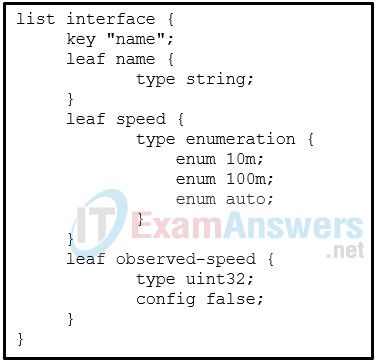 Correct
Correct
Incorrect
Hint
The leaf named observed-speed cannot be configured due to the config false command. The speeds in this leaf are auto-detected (observed); hence, it is not a configurable leaf. -
Question 16 of 39
16. Question
1 pointsWhich statement describes the function of GitHub?Correct
Incorrect
Hint
GitHub is a hosted web-based repository for code. It has capabilities for bug tracking, version control, and task management. Using GitHub is one of the easiest ways to track changes in program files, collaborate with other developers, and share code with the online community. -
Question 17 of 39
17. Question
1 pointsWhich type of API is used to carry configuration changes from a network controller to individual network devices in network automation applications?Correct
Incorrect
Hint
In network automation applications, when a network operator makes a change to the configuration of a network device in the management software of the controller, those changes are pushed down to the individual devices by using a southbound API. These devices can be routers, switches, or even wireless access points. -
Question 18 of 39
18. Question
1 pointsRefer to the exhibit. Which data format is used to represent the data for network automation applications?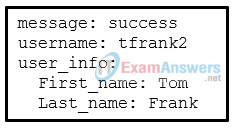 Correct
Correct
Incorrect
Hint
Common data formats that are used in many applications including network automation and programmability include these: – JavaScript Object Notation (JSON) – In JSON, the data known as an object is one or more key/value pairs enclosed in braces { }. Keys must be strings within double quotation marks ” “. Keys and values are separated by a colon. – eXtensible Markup Language (XML) – In XML, the data is enclosed within a related set of tagsdata
. – YAML Ain’t Markup Language (YAML) – In YAML, the data known as an object is one or more key value pairs. Key value pairs are separated by a colon without the use of quotation marks. YAML uses indentation to define its structure, without the use of brackets or commas. -
Question 19 of 39
19. Question
1 pointsA network administrator is checking and making configuration changes on a network device from home. What are two ways to secure the connection between the command-line interface (CLI) of the network device and the remote workstation used by the administrator? (Choose two.)Correct
Incorrect
Hint
The connection between a remote workstation and a network device in a company location can be secured by establishing an SSH or VPN connection first, because both solutions provide encrypted data transmission. -
Question 20 of 39
20. Question
1 pointsWhat is the characteristic of the Postman application that relates to using APIs?Correct
Incorrect
Hint
Postman is an application that makes it possible to interact with APIs using a console-based approach. Postman allows for the use of various data types and formats to interact with REST-based APIs. -
Question 21 of 39
21. Question
1 pointsThe following program was created in Python.user_input = int( input(" What is 3 * 2? ")) if (user_input = 6): print (" Correct!") else: print (" Incorrect...")Why does the program result in an error?Correct
Incorrect
Hint
A single equal sign is used to assign a variable. This program should use double equal signs to check equality. -
Question 22 of 39
22. Question
1 pointsIn a hosted Chef type of deployment, where is the Chef server located?Correct
Incorrect
Hint
There are several types of deployment models for the Chef server. Chef Solo: The Chef server is hosted locally on the workstation. Chef client and server: This is a typical Chef deployment with distributed components. Hosted Chef: The Chef server is hosted in the cloud. Private Chef: All Chef components are within the same enterprise network. -
Question 23 of 39
23. Question
1 pointsWhich term is used to describe a set of instructions for execution by the configuration management tool Puppet?Correct
Incorrect
Hint
The configuration management tool Puppet uses the name Manifest to describe the set of instructions to be executed. -
Question 24 of 39
24. Question
1 pointsQuestion as presented: Match the automation tool with the description.Correct
Incorrect
-
Question 25 of 39
25. Question
1 pointsWhat is the SaltStack agent called that runs on nodes?Correct
Incorrect
Hint
The SaltStack agent that runs on nodes is called a minion. SaltStack grains run on the minions to gather information and report back to the SaltStack master. -
Question 26 of 39
26. Question
1 pointsA student is studying in preparation for an interview for a job in programming and network automation. What is a characteristic of Ansible ?Correct
Incorrect
-
Question 27 of 39
27. Question
1 pointsWhich statement describes the Cisco Embedded Event Manager?Correct
Incorrect
Hint
The Cisco Embedded Event Manager (EEM) is a Cisco IOS tool that uses software applets to automate tasks on a Cisco device. EEM is completely contained within the local device and needs no external scripting or monitoring device. -
Question 28 of 39
28. Question
1 pointsWhich configuration management tool uses an agentless approach?Correct
Incorrect
Hint
Ansible uses an agentless approach. Chef, Puppet, and SaltStack are agent-based. -
Question 29 of 39
29. Question
1 pointsQuestion as presented: Match the Ansible Playbook structure component to the use case.Correct
Incorrect
-
Question 30 of 39
30. Question
1 pointsIn which type of deployment is the Chef server hosted in the cloud?Correct
Incorrect
Hint
There are several types of deployment models for the Chef server. Chef Solo: The Chef server is hosted locally on the workstation. Chef Client and Server: This is a typical Chef deployment with distributed components. Hosted Chef: The Chef server is hosted in the cloud. Private Chef: All Chef components are within the same enterprise network. -
Question 31 of 39
31. Question
1 pointsWhat is a characteristic of the Cisco Embedded Event Manager?Correct
Incorrect
Hint
The Cisco Embedded Event Manager (EEM) is a Cisco IOS tool that uses software applets to automate tasks on a Cisco device. EEM is completely contained within the local device and needs no external scripting or monitoring device. -
Question 32 of 39
32. Question
1 pointsWhich language is used to write Ansible playbooks?Correct
Incorrect
Hint
Ansible playbooks are written in YAML, which uses dictionaries similar to JSON in the use of key/value pairs. -
Question 33 of 39
33. Question
1 pointsA student is studying in preparation for an interview for a job in programming and network automation. What is a characteristic of Chef?Correct
Incorrect
-
Question 34 of 39
34. Question
1 pointsA student is studying in preparation for an interview for a job in programming and network automation. What is a characteristic of GitHub ?Correct
Incorrect
-
Question 35 of 39
35. Question
1 pointsA student is studying in preparation for an interview for a job in programming and network automation. What is a characteristic of CRUD ?Correct
Incorrect
Hint
CRUD is an acronym that stands for CREATE, READ, UPDATE, and DELETE. For example, in a SQL database, the CRUD functions are used to interact with or manipulate thedata stored in the database. -
Question 36 of 39
36. Question
1 pointsWhat is a characteristic of a virtual machine?Correct
Incorrect
Hint
A virtual machne ts a software emulation of a physical server including a CPU, memory, network interface, and guest operating system -
Question 37 of 39
37. Question
1 pointsvCorrect
Incorrect
Hint
JavaScript Object Notation (JSON) is a data format used by applications to store and transport data. -
Question 38 of 39
38. Question
1 pointsA student is studying in preparation for an interview for a job in programming and network automation. What is a characteristic of SaltStack SSH ?Correct
Incorrect
-
Question 39 of 39
39. Question
1 pointsA student is studying in preparation for an interview for a job in programming and network automation. What is a characteristic of Puppet ?Correct
Incorrect

Question 37 is incomplete