Assessment – SWITCH Chapter 7 – CCNP SWITCH (Version 6.0) Exam Answers
1. Which three statements are true about Protocol Independent Multicast (PIM) implementation on Cisco routers? (Choose three.)
- Bidir-PIM is suited for multicast with larger numbers of sources.
- In PIM-SM deployment, all routers create only (*,G) entries for the multicast groups.
- In PIM-DM, a multicast sender first registers with the RP, and the data stream begins to flow from sender to RP to receiver.
- Available network bandwidth is overutilized outside of the multicast routing zone because multiple streams of data are required between distant routers in place of a single transmission.
- All routers in the PIM network learn about the active group-to-RP mapping from the RP mapping agent by automatically joining the Cisco-RP-discovery (224.0.1.40) multicast group.
- In a PIM-SM network, the routers have the SPT threshold set to 0 by default which guarantees that the last-hop router switches to SPT mode as soon as the host starts receiving the multicast.
2. What method of QoS gives preferential handling for predefined classes of traffic?
- best-effort services
- differentiated services
- hard QoS services
- integrated services
3. What are two reasons to implement wireless in a network? (Choose two.)
- increased security
- increased mobility
- increased productivity
- increased cost savings
- increased throughput
4. Which configuration-related step is required for IGMP snooping on a Catalyst switch?
- Enable IGMP snooping in global configuration mode.
- Configure the IGMP snooping method.
- Enable multicast routing in global configuration mode.
- None – IGMP snooping is enabled globally by default.
5. Refer to the exhibit. The network has EIGRP configured on all routers and has converged on the routes advertised. PIM sparse mode has been also configured on all routers. The routers between the Source and the rendezvous point (RP) have (S,G) state in the multicast routing table and the routers between the RP and the Receivers have (*,G) state in their multicast routing tables. After the first multicast packet is received by the Receivers and the switchover takes place, how will the multicast traffic continue to flow from the Source to the Receivers?
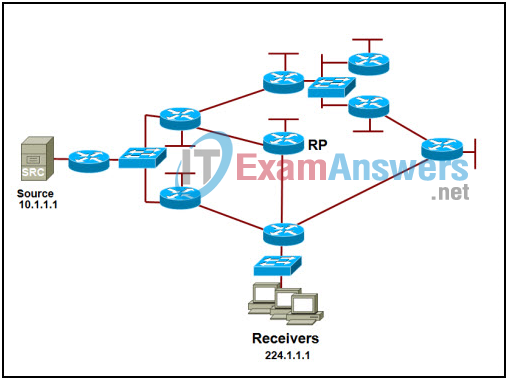
- The traffic will flow via source tree from the Source to the Receivers.
- The traffic will flow via shared tree from the Source to the RP and via shared tree from the RP to the Receivers.
- The traffic will flow via shared tree from the Source to the RP and via source tree from the RP to the Receivers.
- The traffic will flow via source tree from the Source to the RP and via shared tree from the RP to the Receivers.
6. What is the result of the global configuration command ip pim send-rp-discovery Loopback0 scope 3?
- The router sends broadcast group-to-RP mapping messages so that other routers can automatically discover the RP.
- The routers sends group-to-RP mapping messages to 224.0.1.39 so that other routers can automatically discover the RP.
- The router sends group-to-RP mapping messages to 224.0.1.40 so that other routers can automatically discover the RP.
- The router advertises itself as the RP by sending messages to the 224.0.1.39 address.
7. Where should QoS classification and marking be done?
- access layer
- at the first router interface
- core layer
- distribution layer
8. For configuring IP multicast routing, what is the purpose of the global configuration mode command ip pim send-rp-announce 10.1.1.1?
- enables IP multicast routing with router ID 10.1.1.1
- assigns the role of rendezvous point mapping agent to the router with IP address 10.1.1.1
- announces the candidacy of the router with IP address 10.1.1.1 as the rendezvous point for all multicast groups
- enables protocol independent multicast (PIM) with router ID 10.1.1.1
9. What are two reasons to implement voice in a network? (Choose two.)
- cost savings
- increased productivity
- stronger security
- increased data throughput
- easier administration
10. Refer to the exhibit. Router R6 has sent a join message to router R4 requesting multicast traffic for users in the multicast group 224.1.1.1. How will the multicast traffic that is sent from the multicast server SRC through the R1-R3-R5 path be handled at router R6?
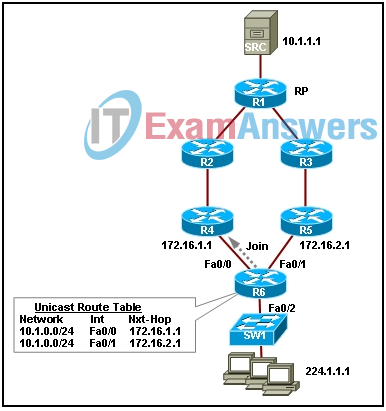
- The multicast traffic will be dropped.
- The multicast traffic will be sent to switch SW1, which will drop the traffic.
- The multicast traffic will be forwarded to all users in the multicast group 224.1.1.1.
- The multicast traffic will be sent back to the rendezvous point (RP) through the R4-R2-R1 path.
11. Which MAC multicast address correctly maps to the IP multicast address 224.10.50.4?
- 01.00.5E.10.32.04
- 01.00.5E.10.50.04
- 01.00.5E.0A.32.04
- 01.00.5E.0A.50.04
12. Which two statements about Protocol Independent Multicast (PIM) are true? (Choose two.)
- PIM does not require an IGP protocol to be configured in the network.
- PIM should be configured only on the first and the last hop routers in the multicast tree.
- PIM should be configured on the device that hosts the source of the muticast traffic.
- PIM Sparse Mode is most useful when there are few senders, many receivers, and the volume of multicast traffic is high.
- PIM is a multicast routing protocol that makes packet-forwarding decisions independent of the unicast IP routing protocol that is running in the network.
- Three of the forwarding modes for PIM are PIM Dense Mode (PIM-DM), PIM Sparse Mode (PIM-SM), and PIM Sparse-Dense Mode.
13. Which two statements about IP multicast addresses are true? (Choose two.)
- IP address 224.0.0.5 identifies the all-routers group.
- All IP multicast group addresses fall in the range from 224.0.0.0 through 254.255.255.255.
- GLOP addresses and limited scope addresses are two types of IP multicast addresses.
- IP addresses between 233.0.0.0 and 233.255.255.255 are reserved link-local addresses.
- IP addresses between 224.0.0.1 and 239.255.255.255 can be assigned to the sources of multicast traffic.
- IP address 224.0.1.1 is a globally scoped address that has been reserved for the Network Time Protocol (NTP).
14. Which statement is true about the split MAC architecture?
- It distributes the processing of 802.11 data and management protocols between a lightweight access point and a centralized WLAN controller.
- Multiple devices can be grouped together to combine total bandwidth.
- The conversation flow can be split between multiple switches.
- The conversation flow can be split between multiple routers.
15. What is the function of a gateway within a VoIP network?
- provides translation between VoIP and non-VoIP networks
- provides connection admission control (CAC), bandwidth control and management, and address translation
- provides real-time connectivity for participants in multiple locations to attend the same video conference or meeting
- provides call control for IP phones, CAC, bandwidth control and management, and address translation
16. What is a major difference between traffic shaping and policing?
- Traffic shaping buffers excessive traffic to smooth traffic whereas policing drops excessive traffic.
- Traffic shaping is preferred for traffic flows such as voice and video whereas policing is better for TCP flows.
- Traffic shaping controls the rate traffic flows through a switch whereas policing controls traffic flows through a router.
- Traffic shaping marks traffic with Layer 2 class of service (CoS) whereas policing marks traffic with the ToS bits in the IP header.
17. The bootstrap router (BSR) mechanism of automating the distribution of rendezvous point (RP) information uses which IP address to disseminate information to all protocol independent multicast (PIM) routers?
- 224.0.0.13
- 224.0.1.13
- 224.1.0.13
- 224.1.1.13
18. What is the IP address for the Cisco-RP-announce multicast group?
- 224.0.1.1
- 224.0.1.39
- 224.0.1.40
- 224.0.0.40
19. What are two best practices when implementing voice in a network? (Choose two.)
- Create a separate VLAN for voice traffic.
- Utilize Power over Ethernet.
- Minimize the volume of the data traffic.
- Remove all QoS policies that are applied in the network.
- Implement access control lists at the distribution layer.
20. What is true about the differences between wireless LANs (WLANs) and LANs?
- A VPN connection that uses IPsec is not possible with WLANs.
- WLANs do not use MAC addresses.
- WLANs use CSMA/CA rather than CSMA/CD because WLANs operate at half-duplex.
- WLANs use CSMA/CA rather than CSMA/CD because WLANs cannot detect collisions.
- WLANs use CSMA/CD rather than CSMA/CA because wireless LANs operate on multiple frequencies.
- WLANs use CSMA/CD rather than CSMA/CA because WLANs operate at full-duplex.
