Check answers here:
Chapters 1 – 5: L2 Redundancy Exam Answers
Quiz-summary
0 of 46 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
Information
CCNP ENCOR v8 Chapters 1 – 5: L2 Redundancy Test Online
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 46 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- Answered
- Review
-
Question 1 of 46
1. Question
1 pointsWhat is the goal of Layer 3 switching?Correct
Incorrect
Hint
Switches that perform Layer 3 switching process packets at Layer 2 hardware speeds while providing the scalability of routing. -
Question 2 of 46
2. Question
1 pointsWhich two statements are true about routed ports on a multilayer switch? (Choose two.)Correct
Incorrect
Hint
A switch routed port is a Layer 3 port that requires removal of Layer 2 port functionality with the no switchport interface configuration command. VLANs are associated with switch Layer 2 access and trunk ports. -
Question 3 of 46
3. Question
1 pointsWhich two statements are true about the 802.1Q trunking protocol? (Choose two.)Correct
Incorrect
Hint
802.1Q is a standard trunking protocol where untagged frames are placed on the native VLAN. The native VLAN must be configured the same at both ends of the trunk link. -
Question 4 of 46
4. Question
1 pointsWhich technology does CEF switching use on Cisco hardware-based routers to forward packets?Correct
Incorrect
Hint
CEF switching on Cisco hardware-based routers uses forwarding engines implemented in specialized ASICs to forward packets. Cisco software-based routers use the general-purpose CPU for packet switching. InterVLAN routing using subinterfaces is not a CEF technology, and route processors using stateful switchover is a redundancy technology used by routers. -
Question 5 of 46
5. Question
1 pointsWhat type of specialized memory is used to facilitate high performance switching in Cisco multilayer switches?Correct
Incorrect
Hint
CAM is used by ARP to store MAC and IPv4 address pairs. CEF uses a FIB. -
Question 6 of 46
6. Question
1 pointsWhich protocol is required for Cisco Express Forwarding to be able to successfully forward packets on a multilayer switch?Correct
Incorrect
Hint
In order to forward packets, Cisco Express Forwarding (CEF) requires the MAC address of the next hop provided by ARP. -
Question 7 of 46
7. Question
1 pointsWhich two network design features require Spanning Tree Protocol (STP) to ensure correct network operation? (Choose two.)Correct
Incorrect
Hint
Spanning Tree Protocol (STP) is required to ensure correct network operation when designing a network with multiple interconnected Layer 2 switches or using redundant links to eliminate single points of failure between Layer 2 switches. Routing is a Layer 3 function and does not relate to STP. VLANs do reduce the number of broadcast domains but relate to Layer 3 subnets, not STP. -
Question 8 of 46
8. Question
1 pointsIf left to default configuration settings, what will determine which switch becomes the spanning-tree root bridge in a Layer 2 domain?Correct
Incorrect
Hint
By default, all switches will have the same priority value, so the election of the root bridge will be based on the lowest MAC address. -
Question 9 of 46
9. Question
1 pointsDuring the implementation of Spanning Tree Protocol, all switches are rebooted by the network administrator. What is the first step of the spanning-tree election process?Correct
Incorrect
Hint
After a Cisco switch boots, it will send out BPDUs containing its individual BID and the root ID for the network. By default, the initial root ID at bootup will be the ID of that individual switch. After a root bridge is elected, port states and paths are chosen. -
Question 10 of 46
10. Question
1 pointsAfter the election of the root bridge has been completed, how will switches find the best paths to the root bridge?Correct
Incorrect
Hint
After the election of a root bridge has occurred, each switch will have to determine the best path to the root bridge from its location. The path is determined by summing the individual port costs along the path from each switch port to the root bridge. -
Question 11 of 46
11. Question
1 pointsWhich statement describes the term bridge priority in the operation of STP?Correct
Incorrect
-
Question 12 of 46
12. Question
1 pointsWhich three components are combined to form a bridge ID?Correct
Incorrect
Hint
The three components that are combined to form a bridge ID are bridge priority, extended system ID, and MAC address. -
Question 13 of 46
13. Question
1 pointsIn which two port states does a switch learn MAC addresses and process BPDUs in a PVST network? (Choose two.)Correct
Incorrect
Hint
Switches learn MAC addresses at the learning and forwarding port states. They receive and process BPDUs at the blocking, listening, learning, and forwarding port states. -
Question 14 of 46
14. Question
1 pointsWhich STP priority configuration would ensure that a switch would always be the root switch?Correct
Incorrect
Hint
Although the spanning-tree vlan 10 root primary command will ensure a switch will have a bridge priority value lower than other bridges introduced to the network, the spanning-tree vlan 10 priority 0 command ensures the bridge priority takes precedence over all other priorities. -
Question 15 of 46
15. Question
1 pointsRefer to the exhibit. The network has converged and Switch_6 has been elected root bridge of the STP tree. However, network traffic analysis indicates that Switch_1 would be a better root bridge. How can the network administrator make this change, assuming that the spanning-tree priorities are at the default settings?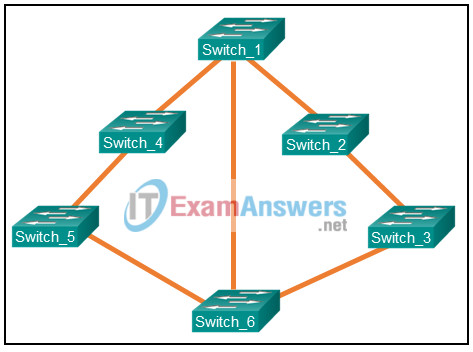 Correct
Correct
Incorrect
Hint
The switch priority is a value between 0-61,440 in increments of 4,096. Switch priority is initially set to 32,768 (the default). Therefore, Switch_1 can become the root bridge if the priority is set to a value between 0-28,672. -
Question 16 of 46
16. Question
1 pointsWhy is it important that the network administrator consider the spanning-tree network diameter when choosing the root bridge?Correct
Incorrect
Hint
The optional diameter keyword in the spanning-tree vlan vlan-id root {primary | secondary} [diameter diameter] command allows for tuning of the STP convergence. The diameter keyword should reference the maximum number of Layer 2 hops that a switch can be from the root bridge and modify the timers accordingly. The timers do not need to be modified on other switches because they are carried throughout the topology through the root bridge BPDUs. -
Question 17 of 46
17. Question
1 pointsA network administrator enters the spanning-tree portfast bpduguard default command. What is the result of this command being issued on a Cisco switch?Correct
Incorrect
Hint
The spanning-tree bpduguard default command will enable BPDU guard on all switch ports that have PortFast-enabled. This will put the port in an error-disabled state if a BPDU from another switch is received on a PortFast-enabled interface. -
Question 18 of 46
18. Question
1 pointsIn what situation would a network administrator most likely implement root guard?Correct
Incorrect
Hint
Root guard in conjunction with PortFast, and BPDU guard is used to prevent an STP manipulation attack. -
Question 19 of 46
19. Question
1 pointsWhich two statements describe the MST internal spanning tree instance? (Choose two)Correct
Incorrect
Hint
MST uses a special STP instance called the internal spanning tree (IST), which is always the first instance, instance 0. The IST runs on all switch port interfaces for switches in the MST region, regardless of the VLANs associated with the ports. -
Question 20 of 46
20. Question
1 pointsWhat are the two options that describe the effects of the spanning-tree portfast command? (Choose two.)Correct
Incorrect
Hint
The portfast feature is enabled on a specific access port with the spanning-tree portfast command. One of the benefits of the STP portfast feature, is that the access ports bypass the earlier 802.1D STP states (learning and listening) and forward traffic immediately. -
Question 21 of 46
21. Question
1 pointsWhich LACP technology is used for designating a specific number of member interfaces that must remain active in order for the EtherChannel bundle to be usable?Correct
Incorrect
Hint
LACP fast advertises an LACP packet every second and after three seconds of not receiving an LACP packet, removes the link from the EtherChannel bundle. LACP port priority allows an LACP enabled switch to select which member interfaces are active within a port-channel that has more member interfaces than the maximum allowed. LACP system priority allows an LACP enabled switch to be designated as the master switch for a port-channel. LACP min-links is used to configure a required minimum number of physical connections that must be active in order for the EtherChannel to stay active. -
Question 22 of 46
22. Question
1 pointsWhich statement describes the term root port in the operation of STP?Correct
Incorrect
-
Question 23 of 46
23. Question
1 pointsWhat are two configuration parameters that must match for all switches in the same MST region? (Choose two.)Correct
Incorrect
Hint
The mst version number and region name must match for all switches in the same MST region. These parameters can be adjusted through MST configuration. -
Question 24 of 46
24. Question
1 pointsAssuming that all switches in a network have the default bridge priority for each MST instance, what effect does the command spanning-tree mst 10 root seconday have when entered on a single switch?Correct
Incorrect
Hint
In MST configuration, an MST instance priority can be defined in one of two methods: spanning-tree mst instance-number priority priority , where the priority is a value between 0 and 61,440, in increments of 4096 spanning-tree mst instance-number root { primary | secondary }[ diameter diameter ], where the primary keyword sets the priority to 24,576, and the secondary keyword sets the priority to 28,672 -
Question 25 of 46
25. Question
1 pointsRefer to the exhibit. A network administrator issues the show spanning-tree command to verify the MST configuration. Which two conclusions can be drawn based on the output? (Choose two.)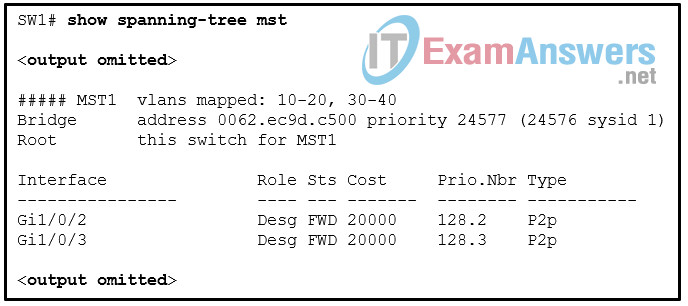 Correct
Correct
Incorrect
Hint
SW1 is running MST, which is IEEE 802.1S standard. IEEE 802.1W is the standard for RSTP. SW1 is the root bridge for instance 1. The instance 1 priority is set as 24576. If it is set through the secondary keyword, it would be 28672. If the portfast feature is enabled on a port, the port type would be P2p Edge. -
Question 26 of 46
26. Question
1 pointsRefer to the exhibit. A network administrator is configuring MST tuning on SW1. The objective is to change the path cost value of the interface Gi1/0/1 to represent a higher-speed bandwidth link. Which value could be used in the command spanning-tree mst 0 cost for this task?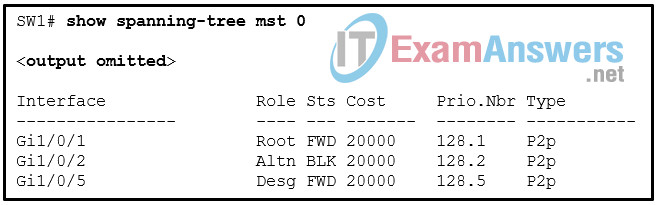 Correct
Correct
Incorrect
Hint
As shown in the output, the interface STP cost is derived from the media speed of the interface using the long-mode method. Using this method, the range of the interface path cost is from 1 to 200000000. A lower path cost represents higher-speed transmission bandwidth. -
Question 27 of 46
27. Question
1 pointsWhat are two misconfigurations within an MST region that might introduce port blocking unintentionally? (Choose two.)Correct
Incorrect
Hint
VLAN assignment to the IST and trunk link pruning are two common misconfigurations within the MST region. A misconfigured region name or misconfigured revision number will cause the failure in forming the MST region. -
Question 28 of 46
28. Question
1 pointsHow does an MST region send VLAN information through the PVST simulation mechanism to a switch that runs PVST+?Correct
Incorrect
Hint
The PVST simulation mechanism sends out PVST+ including RSTP BPDUs, one for each VLAN, using the information derived from the internal spanning tree (IST). This requires a mapping of one topology in IST to multiple VLANs toward the PVST link. -
Question 29 of 46
29. Question
1 pointsWhich two VTP modes allow for the creation, modification, and deletion of VLANs on the local switch? (Choose two.)Correct
Incorrect
Hint
The three VTP modes are server, client, and transparent. In server VTP mode, the switch can create, modify, and delete VLANs and send this information on to other switches that are in the same VTP domain. Switches in transparent VTP mode can do the same except that information is not transmitted to other switches. -
Question 30 of 46
30. Question
1 pointsGiven the following configuration, which two statements are true? (Choose two.)switch(vlan)# vtp version 2 switch(vlan)# vtp mode server switch(vlan)# vtp domain Cisco switch(vlan)# vtp password mypassword
Correct
Incorrect
Hint
A switch in VTP server mode can create, modify, and delete VLANs as well as transmit that information (if the switch has the highest VTP configuration revision number) to other switches in the same VTP domain. -
Question 31 of 46
31. Question
1 pointsWhich Cisco proprietary protocol is used for dynamically forming a trunk connection between two switches?Correct
Incorrect
Hint
Dynamic Trunking Protocol (DTP) is a Cisco proprietary protocol used for dynamically negotiating a trunk connection between two Cisco switches. -
Question 32 of 46
32. Question
1 pointsWhich is a characteristic of EtherChannel?Correct
Incorrect
Hint
Because EtherChannel creates one logical link out of a number of physical ports, STP will treat the one logical link as an individual connection. When a physical port that is part of the logical link fails, the link will stay active and STP will not recalculate. -
Question 33 of 46
33. Question
1 pointsRefer to the exhibit. The administrator tried to create an EtherChannel between S1 and the other two switches via the commands that are shown, but was unsuccessful. What is the problem?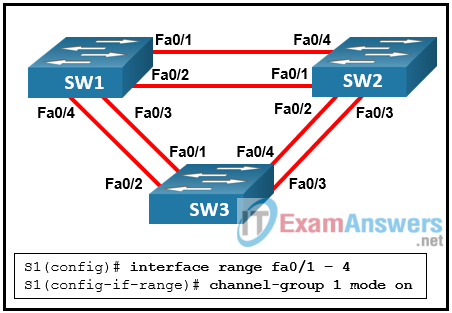 Correct
Correct
Incorrect
Hint
An EtherChannel link can only be created between two switches or between an EtherChannel-enabled server and a switch. Traffic cannot be sent to two different switches through the same EtherChannel link. -
Question 34 of 46
34. Question
1 pointsRefer to the exhibit. An EtherChannel was configured between switches S1 and S2, but the interfaces do not form an EtherChannel. What is the problem?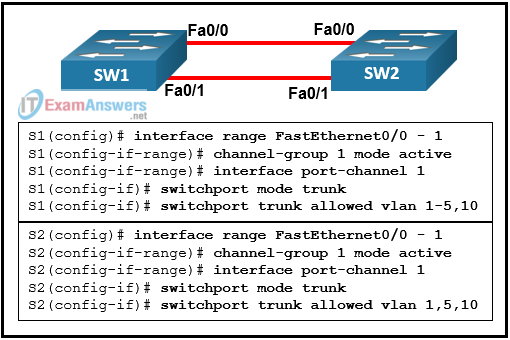 Correct
Correct
Incorrect
Hint
The guidelines for configuring an EtherChannel link are as follows:- Interfaces which form an EtherChannel can be physically discontiguous, and on different modules.
- Interfaces in an EtherChannel have to operate at the same speed and in the same duplex mode.
- Interfaces in the EtherChannel must be assigned to the same VLAN, or be configured as a trunk.
- Interfaces in the EtherChannel have to support the same allowed range of VLANs.
-
Question 35 of 46
35. Question
1 pointsWhich two DTP mode combinations will form a trunk link between two switches? (Choose two.)Correct
Incorrect
Hint
There are five DTP mode combinations that will result in successful trunk link negotiation between two switches. dynamic auto and dynamic desirable dynamic desirable and dynamic desirable trunk and trunk trunk and dynamic auto trunk and dynamic desirable -
Question 36 of 46
36. Question
1 pointsWhich statement is true about the port roles of the 802.1w Rapid Spanning Tree Protocol?Correct
Incorrect
Hint
In order to create a loop-free topology, 802.1w RSTP has the following port roles: root, designated, alternate, edge, and backup. RSTP is able to actively confirm that a port can safely transition to the forwarding state without having to rely on a timer configuration. -
Question 37 of 46
37. Question
1 pointsWhich technology is used to protect the switched infrastructure from problems caused by receiving BPDUs on ports that should not be receiving them?Correct
Incorrect
Hint
To form a single path through a Layer 2 network, Layer 2 devices communicate with one another by the use of bridge protocol data units (BPDUs) as part of the Spanning Tree Protocol (STP). An attacker manipulates STP by spoofing the root bridge so that a device that is controlled by the attacker becomes a root bridge. The attacker can then obtain more information about the network or networks. BPDU guard can be used on ports that connect to user devices that are configured with PortFast so that BPDUs will not be accepted through that port. -
Question 38 of 46
38. Question
1 pointsWhich statement describes the term blocking in the operation of STP?Correct
Incorrect
-
Question 39 of 46
39. Question
1 pointsThe network administrator wants to configure a switch to pass VLAN update information to other switches in the domain but not update its own local VLAN database. Which two steps should the administrator perform to achieve this? (Choose two.)Correct
Incorrect
Hint
Besides the VTP domain name and mode needing to be configured, the switch must connect to other switches in the same VTP domain through a trunk in order to transmit/receive VTP information. -
Question 40 of 46
40. Question
1 pointsWhich LACP technology is used for designating whuch member interfaces will be active in a port-channel configuration where there are more member interfaces than the maximum allowed?Correct
Incorrect
-
Question 41 of 46
41. Question
1 pointsWhich LACP technology can identify and remove a LACP enabled link from an EtherChannel within three seconds when the link is experiencing connectivity issues?Correct
Incorrect
-
Question 42 of 46
42. Question
1 pointsWhich two statements descibe the MST internal spanning tree instance? (Choose two)Correct
Incorrect
-
Question 43 of 46
43. Question
1 pointsWhich statement describes the term root bridge in the operation of STP?Correct
Incorrect
-
Question 44 of 46
44. Question
1 pointsRefer to the exhibit. Access1 is a new switch that is to be connected as a VTP client to the network once it has been configured. Given the output generated by the VTP server switch Dist-2, which series of configuration commands would successfully introduce the client switch into the VTP domain?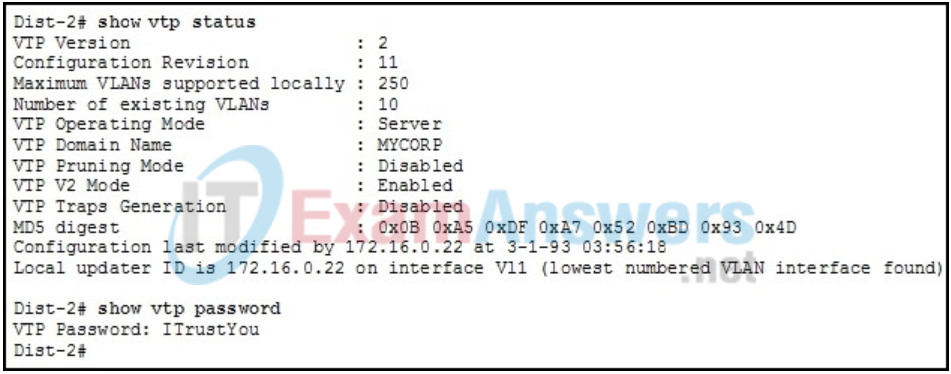 Correct
Correct
Incorrect
-
Question 45 of 46
45. Question
1 pointsWhich LACP technology is used for designating which member interfaces will be active in a port-channel configuration where there are more member interfaces than the maximum allowed?Correct
Incorrect
-
Question 46 of 46
46. Question
1 pointsWhich statement describes the term root guard in the operation of STP?Correct
Incorrect

Correction to question number 10 answers:
After the election of the root bridge has been completed, how will switches find the best paths to the root bridge?
good
wow very nice