1. ACLs are used primarily to filter traffic. What are two additional uses of ACLs? (Choose two.)
- specifying source addresses for authentication
- specifying internal hosts for NAT
- identifying traffic for QoS
- reorganizing traffic into VLANs
- filtering VTP packets
2. Which set of access control entries would allow all users on the 192.168.10.0/24 network to access a web server that is located at 172.17.80.1, but would not allow them to use Telnet?
- access-list 103 deny tcp host 192.168.10.0 any eq 23
access-list 103 permit tcp host 192.168.10.1 eq 80 - access-list 103 permit 192.168.10.0 0.0.0.255 host 172.17.80.1
access-list 103 deny tcp 192.168.10.0 0.0.0.255 any eq telnet - access-list 103 permit tcp 192.168.10.0 0.0.0.255 host 172.17.80.1
access-list 103 deny tcp 192.168.10.0 0.0.0.255 any eq 23 - access-list 103 permit tcp 192.168.10.0 0.0.0.255 any eq 80
access-list 103 deny tcp 192.168.10.0 0.0.0.255 any eq 23
3. Which packet types are implicitly permitted by IPv6 ACLs?
- router solicitation packets
- IPv6 unicast packets
- neighbor discovery packets
- ping packets
4. Which command is used to activate an IPv6 ACL named ENG_ACL on an interface so that the router filters traffic prior to accessing the routing table?
- ipv6 access-class ENG_ACL in
- ipv6 access-class ENG_ACL out
- ipv6 traffic-filter ENG_ACL in
- ipv6 traffic-filter ENG_ACL out
5. Refer to the exhibit. A network administrator wants to create a standard ACL to prevent network 1 traffic from being transmitted to the Research and Development network. On which router interface and in which direction should the standard ACL be applied?
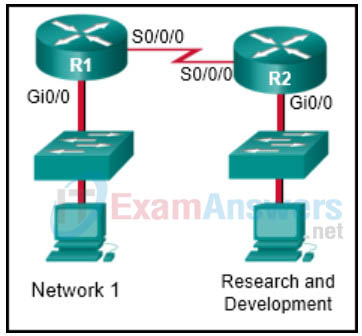
- R1 Gi0/0 inbound
- R1 Gi0/0 outbound
- R1 S0/0/0 outbound
- R2 S0/0/0 inbound
- R2 Gi0/0 outbound
- R2 Gi0/0 inbound
6. Which IPv4 address range covers all IP addresses that match the ACL filter specified by 172.16.2.0 with wildcard mask 0.0.1.255?
- 172.16.2.0 to 172.16.2.255
- 172.16.2.1 to 172.16.3.254
- 172.16.2.0 to 172.16.3.255
- 172.16.2.1 to 172.16.255.255
7. Which two keywords can be used in an access control list to replace a wildcard mask or address and wildcard mask pair? (Choose two.)
- most
- host
- all
- any
- some
- gt
8. Refer to the exhibit. A network administrator is configuring an IPv6 ACL to allow hosts on the 2001:DB8:CAFÉ:10::/64 network to access remote web servers, except for PC1. However, a user on PC1 can successfully access the web server PC2. Why is this possible?
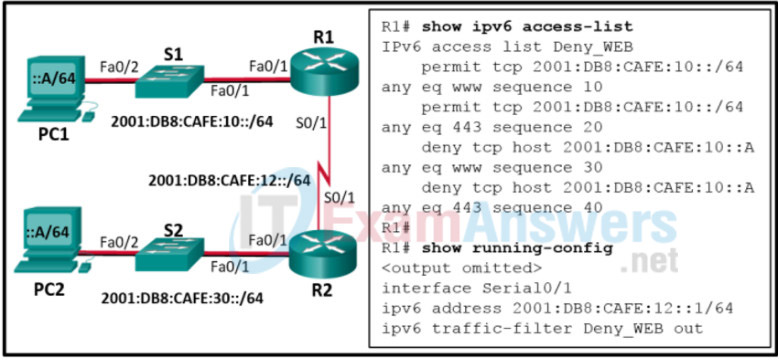
- The IPv6 ACL Deny_WEB is spelled incorrectly when applied to the interface.
- The IPv6 ACL Deny_WEB is applied to the wrong interface of router R1.
- The IPv6 ACL Deny_WEB is applied in the incorrect direction on router R1.
- The IPv6 ACL Deny_WEB is permitting all web traffic before the specific host is blocked.
9. Which IPv6 ACL command entry will permit traffic from any host to an SMTP server on network 2001:DB8:10:10::/64?
- permit tcp any host 2001:DB8:10:10::100 eq 25
- permit tcp host 2001:DB8:10:10::100 any eq 25
- permit tcp any host 2001:DB8:10:10::100 eq 23
- permit tcp host 2001:DB8:10:10::100 any eq 23
10. What is the purpose of using prefix lists?
- to filter routes based on matching subnet masks
- to filter traffic based on a range of protocols or port numbers
- to assign quality of service markings to filtered traffic
- to expand the range of private addresses using PAT
- to implicitly permit neighbor discovery protocol packets
11. A network administrator is configuring a prefix list to match networks for BGP route filtering. Which network matches the prefix match specification 10.160.0.0/14 ge 22?
- 10.158.0.0/22
- 10.162.0.0/14
- 10.163.0.0/24
- 10.128.0.0/28
12. A network administrator is configuring a prefix list with the ip prefix-list command. How does the IOS process the prefix list if the administrator does not specify a sequence number?
- It will present a prompt to ask the administrator to enter one.
- It will present an error message that indicates the entry fails.
- It automatically increments by 5 based on the highest sequence number.
- It automatically increments by 10 based on the highest sequence number.
“Do I Know This Already?” Quiz Answers:
1. What is the correct order of operations for an IPv4 ACL?
- Top-down processing, execute upon the longest match, implicit deny all
- Execute upon the longest match, top-down processing, implicit deny all
- Implicit deny all, immediate execution upon a match, top-down processing
- Top-down processing, immediate execution upon a match, implicit deny all
2. What occurs to a packet when an ACL is applied to an interface but the packet does not match any of the entries in the ACL?
- It is forwarded.
- It is flooded.
- It is dropped.
- It is buffered.
3. What does the following ACL entry accomplish when applied to an interface: 20 permit tcp 10.1.1.0 0.0.0.63 host 192.0.2.1 eq 23?
- Permits Telnet traffic from the device with IP address 192.0.2.1 going to any device with an IP address from 10.1.1.0 to 10.1.1.63
- Permits Telnet traffic from any device with IP address from 10.1.1.0 to 10.1.1.63 going to the device with IP address 192.0.2.1
- Permits SSH traffic from any device with IP address from 10.1.1.0 to 10.1.1.63 going to the device with IP address 192.0.2.1
- Permits SSH traffic from the device with IP address 192.0.2.1 going to any device with IP address from 10.1.1.0 to 10.1.1.63
4. Which command successfully filters ingress traffic using ACL 100 on an interface?
- access-group 100 in
- access-class 100 in
- ip access-group 100 in
- ip traffic-filter 100 in
5. What is the correct order of operations for an IPv6 ACL?
- Immediate execution upon a match, implicit permit icmp nd, implicit deny all, top-down processing
- Top-down processing, immediate execution upon a match, implicit permit icmp nd, implicit deny all
- Top-down processing, implicit permit icmp nd, immediate execution upon a match, implicit deny all
- Implicit permit icmp nd, top-down processing, immediate execution upon a match, implicit deny all
6. What happens if you add the following entry to the end of an IPv6 ACL: deny ipv6 any any log? (Choose two.)
- All traffic is denied and logged.
- All traffic that does not match an entry in the ACL is denied and logged.
- ICMP Neighbor Discovery messages are implicitly permitted.
- ICMP Neighbor Discovery messages are denied.
7. Which command successfully filters egress traffic using an IPv6 ACL named ENARSI on an interface?
- access-group ENARSI out
- access-class ENARSI out
- ipv6 access-group ENARSI out
- ipv6 traffic-filter ENARSI out
8. Which IP prefix list matches only the default route?
- ip prefix-list ENARSI permit 0.0.0.0/0 le 32
- ip prefix-list ENARSI permit 0.0.0.0/0 ge 32
- ip prefix-list ENARSI permit 0.0.0.0/0 ge 1
- ip prefix-list ENARSI permit 0.0.0.0/0
9. Which IP prefix list matches all routes?
- ip prefix-list ENARSI permit 0.0.0.0/0 le 32
- ip prefix-list ENARSI permit 0.0.0.0/0 ge 32
- ip prefix-list ENARSI permit 0.0.0.0/0 ge 1
- ip prefix-list ENARSI permit 0.0.0.0/0
10. What routes match the following prefix list: ip prefix-list ENARSI seq 35 deny 192.168.0.0/20 ge 24 le 28?
- Routes with an address from 192.168.0.0 to 192.168.15.255 with a subnet mask of 24 to 28
- Routes within the 192.168.0.0/20 subnet with a subnet mask greater than 24 and less than 28
- Routes with the subnet ID and mask 192.168.0.0/20
- Routes with an address from 192.168.0.0 to 192.168.15.255 with a subnet mask of 24 or 28
