15.1.2 Lab – Control Routing Updates (Answers)
Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only.
Topology
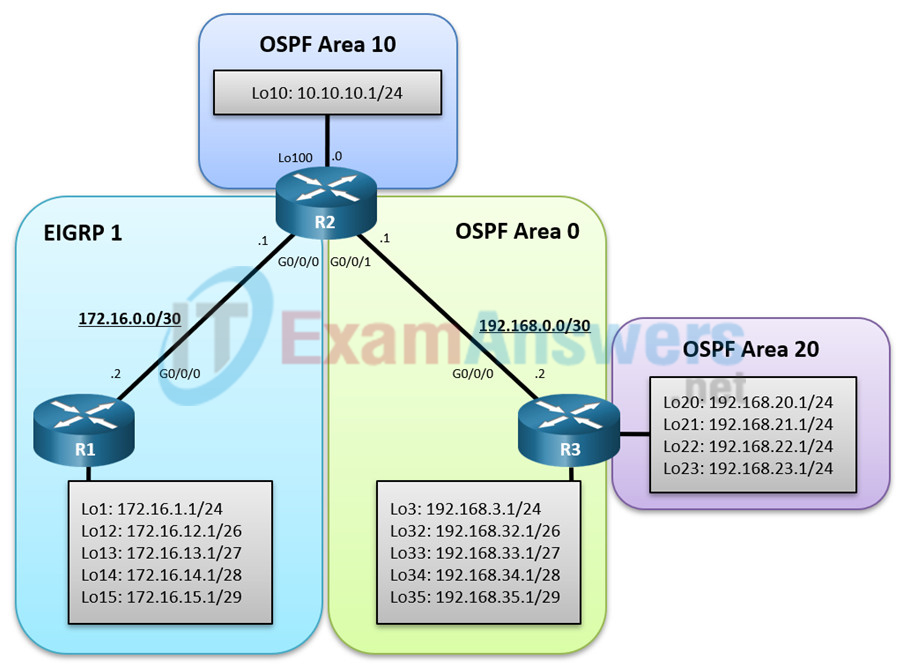
Addressing Table
| Device | Interface | IPv4 Address | Subnet Mask |
|---|---|---|---|
| R1 | G0/0/0 | 172.16.0.2 | 255.255.255.252 |
| Loopback 1 | 172.16.1.1 | 255.255.255.0 | |
| Loopback 12 | 172.16.12.1 | 255.255.255.192 | |
| Loopback 13 | 172.16.13.1 | 255.255.255.224 | |
| Loopback 14 | 172.16.14.1 | 255.255.255.240 | |
| Loopback 15 | 172.16.15.1 | 255.255.255.248 | |
| R2 | G0/0/0 | 172.16.0.1 | 255.255.255.252 |
| G0/0/1 | 192.168.0.1 | 255.255.255.252 | |
| Loopback 10 | 10.10.10.1 | 255.255.255.0 | |
| R3 | G0/0/0 | 192.168.0.2 | 255.255.255.252 |
| Loopback 3 | 192.168.3.1 | 255.255.255.0 | |
| Loopback 20 | 192.168.20.1 | 255.255.255.0 | |
| Loopback 21 | 192.168.21.1 | 255.255.255.0 | |
| Loopback 22 | 192.168.22.1 | 255.255.255.0 | |
| Loopback 23 | 192.168.23.1 | 255.255.255.0 | |
| Loopback 32 | 192.168.32.1 | 255.255.255.192 | |
| Loopback 33 | 192.168.33.1 | 255.255.255.224 | |
| Loopback 34 | 192.168.34.1 | 255.255.255.240 | |
| Loopback 35 | 192.168.35.1 | 255.255.255.248 |
Objectives
In this lab you will learn how to control routing updates in an EIGRP and OSPF redistributed routing network. Specifically, you will:
- Part 1: Build the Network and Configure Basic Device Settings
- Part 2: Configure Routing and Redistribution
- Part 3: Filter Redistributed Routes using a Distribute List and ACL
- Part 4: Filter Redistributed Routes using a Distribute List and Prefix List
- Part 5: Filter Redistributed Routes using a Route Map
Background / Scenario
In this scenario, R1 and R2 are running EIGRP while R2 and R3 are running multi-area OSPF. R2 is the OSPF autonomous system border router (ASBR) consisting of areas 0, 10, and 20. R2 will also redistribute the EIGRP routes into OSPF and the OSPF routes into EIGRP.
Your task is to control routing updates between the two routing domains by using distribute lists, prefix lists, and route maps.
Note: The routers used with CCNP hands-on labs are Cisco 4221 with Cisco IOS XE Release 16.9.4 (universalk9 image). The switches used in the labs are Cisco Catalyst 3650 with Cisco IOS XE Release 16.9.4 (universalk9 image). Other routers, switches, and Cisco IOS versions can be used. Depending on the model and Cisco IOS version, the commands available and the output produced might vary from what is shown in the labs. Refer to the Router Interface Summary Table at the end of the lab for the correct interface identifiers.
Note: Make sure that the routers and switches have been erased and have no startup configurations. If you are unsure, contact your instructor.
Instructor Note: Refer to the Instructor Lab Manual for the procedures to initialize and reload devices.
Required Resources
• 3 Routers (Cisco 4221 with Cisco IOS XE Release 16.9.4 universal image or comparable)
• Console cables to configure the Cisco IOS devices via the console ports
• 1 PC (Choice of operating system with terminal emulation program installed)
• Ethernet cables as shown in the topology
Instructions
Part 1: Build the Network and Configure Basic Device Settings
In Part 1, you will set up the network topology and configure basic settings and interface addressing on routers.
Step 1: Cable the network as shown in the topology.
Attach the devices as shown in the topology diagram, and cable as necessary.
Step 2: Configure basic settings for each device.
a. Console into each device, enter global configuration mode, and apply the basic settings. The startup configurations for each device are provided below.
Router R1
hostname R1 no ip domain lookup line con 0 logging sync exec-time 0 0 exit banner motd # This is R1, Controlling Routing Updates # interface g0/0/0 description Connection to R2 ip add 172.16.0.2 255.255.255.252 no shut exit interface Lo1 ip address 172.16.1.1 255.255.255.0 exit interface Lo12 ip address 172.16.12.1 255.255.255.192 exit interface Lo13 ip address 172.16.13.1 255.255.255.224 exit interface Lo14 ip address 172.16.14.1 255.255.255.240 exit interface Lo15 ip address 172.16.15.1 255.255.255.248 end
Router R2
hostname R2 no ip domain lookup line con 0 logging sync exec-time 0 0 exit banner motd # This is R2, Controlling Routing Updates # interface g0/0/0 description Connection to R1 ip add 172.16.0.1 255.255.255.252 no shut exit interface GigabitEthernet0/0/1 description Connection to R3 ip address 192.168.0.1 255.255.255.252 no shut exit int lo10 ip add 10.10.10.1 255.255.255.0 ip ospf network point-to-point end
Router R3
hostname R3 no ip domain lookup line con 0 logging sync exec-time 0 0 exit banner motd # This is R3, Controlling Routing Updates # interface g0/0/0 description Connection to R2 ip add 192.168.0.2 255.255.255.252 no shut exit interface Lo3 ip add 192.168.3.1 255.255.255.0 ip ospf network point-to-point exit interface Lo32 ip add 192.168.32.1 255.255.255.0 ip ospf network point-to-point exit interface Lo33 ip add 192.168.33.1 255.255.255.0 ip ospf network point-to-point exit interface Lo34 ip add 192.168.34.1 255.255.255.0 ip ospf network point-to-point exit interface Lo35 ip add 192.168.35.1 255.255.255.0 ip ospf network point-to-point exit interface Lo20 ip add 192.168.20.1 255.255.255.0 ip ospf network point-to-point exit interface Lo21 ip add 192.168.21.1 255.255.255.0 ip ospf network point-to-point exit interface Lo22 ip add 192.168.22.1 255.255.255.0 ip ospf network point-to-point exit interface Lo23 ip add 192.168.23.1 255.255.255.0 ip ospf network point-to-point end
b. Save the running configuration to startup-config.
Part 2: Configure Routing and Redistribution
In Part 2, you will implement EIGRP and OSPF routing and redistribute the routes into each routing protocols. Although redistribution is not covered in this chapter, it is covered here for example purposes.
Step 1: Configure Routing.
In this step, you will configure EIGRP on R1 and R2, and OSPF on R2 and R3.
a. On R1, advertise the connected networks using EIGRP in autonomous system 1. Assign R1 the router ID of 1.1.1.1.
R1(config)# router eigrp 1 R1(config-router)# eigrp router-id 1.1.1.1 R1(config-router)# network 172.16.0.0 0.0.0.3 R1(config-router)# network 172.16.1.0 0.0.0.255 R1(config-router)# network 172.16.12.0 0.0.0.63 R1(config-router)# network 172.16.13.0 0.0.0.31 R1(config-router)# network 172.16.14.0 0.0.0.15 R1(config-router)# network 172.16.15.0 0.0.0.7 R1(config-router)# end
b. On R3, advertise the connected networks using OSPF process ID 123 for area 0 and area 20.
R3(config)# router ospf 123 R3(config-router)# router-id 3.3.3.3 R3(config-router)# network 192.168.0.0 0.0.0.3 area 0 R3(config-router)# network 192.168.3.0 0.0.0.255 area 0 R3(config-router)# network 192.168.32.0 0.0.0.63 area 0 R3(config-router)# network 192.168.33.0 0.0.0.31 area 0 R3(config-router)# network 192.168.34.0 0.0.0.15 area 0 R3(config-router)# network 192.168.35.0 0.0.0.7 area 0 R3(config-router)# network 192.168.20.0 0.0.3.255 area 20 R3(config-router)# end
Note: The network 192.168.20.0 0.0.3.255 area 20 command enables OSPF for loopbacks 20, 21, 22, and 23.
c. On R2, configure EIGRP and redistribute the OSPF networks into EIGRP AS 1. Then configure OSPF and redistribute and summarize the EIGRP networks into OSPF.
R2(config)# router eigrp 1 R2(config-router)# eigrp router-id 2.2.2.2 R2(config-router)# network 172.16.0.0 0.0.0.3 R2(config-router)# exit *Mar 18 13:08:33.786: %DUAL-5-NBRCHANGE: EIGRP-IPv4 1: Neighbor 172.16.0.2 (GigabitEthernet0/0/0) is up: new adjacency R2(config)# R2(config)# router ospf 123 R2(config-router)# router-id 2.2.2.2 R2(config-router)# network 192.168.0.0 0.0.0.3 area 0 R2(config-router)# network 10.10.10.0 0.0.0.255 area 10 R2(config-router)# end *Mar 18 13:08:36.024: %OSPF-5-ADJCHG: Process 123, Nbr 3.3.3.3 on GigabitEthernet0/0/1 from LOADING to FULL, Loading Done
Step 2: Verify EIGRP and OSPF routing
a. Verify the EIGRP routing table entries on R1. No routes are displayed because R1 is directly connected to all of the EIGRP routes.
R1# show ip route eigrp | begin Gateway Gateway of last resort is not set
b. Verify the OSPF routing table entries on R3. R3 has an inter-area route entry for the OSPF area 10 network.
R3# show ip route ospf | begin Gateway
Gateway of last resort is not set
10.0.0.0/24 is subnetted, 1 subnets
O IA 10.10.10.0 [110/2] via 192.168.0.1, 00:04:29, GigabitEthernet0/0/0
c. Verify the EIGRP and OSPF routing table entries on R2. R2 has entries for all of the EIGRP networks and the OSPF networks including the Area 20 networks.
R2# show ip route eigrp | begin Gateway
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 7 subnets, 7 masks
D 172.16.1.0/24
[90/130816] via 172.16.0.2, 00:05:52, GigabitEthernet0/0/0
D 172.16.12.0/26
[90/130816] via 172.16.0.2, 00:05:52, GigabitEthernet0/0/0
D 172.16.13.0/27
[90/130816] via 172.16.0.2, 00:05:52, GigabitEthernet0/0/0
D 172.16.14.0/28
[90/130816] via 172.16.0.2, 00:05:52, GigabitEthernet0/0/0
D 172.16.15.0/29
[90/130816] via 172.16.0.2, 00:05:52, GigabitEthernet0/0/0
R2# show ip route ospf | begin Gateway
Gateway of last resort is not set
O 192.168.3.0/24 [110/2] via 192.168.0.2, 00:12:22, GigabitEthernet0/0/1
O IA 192.168.20.0/24 [110/2] via 192.168.0.2, 00:12:22, GigabitEthernet0/0/1
O IA 192.168.21.0/24 [110/2] via 192.168.0.2, 00:12:22, GigabitEthernet0/0/1
O IA 192.168.22.0/24 [110/2] via 192.168.0.2, 00:12:22, GigabitEthernet0/0/1
O IA 192.168.23.0/24 [110/2] via 192.168.0.2, 00:12:22, GigabitEthernet0/0/1
O 192.168.32.0/24 [110/2] via 192.168.0.2, 00:12:22, GigabitEthernet0/0/1
O 192.168.33.0/24 [110/2] via 192.168.0.2, 00:00:30, GigabitEthernet0/0/1
O 192.168.34.0/24 [110/2] via 192.168.0.2, 00:12:22, GigabitEthernet0/0/1
O 192.168.35.0/24 [110/2] via 192.168.0.2, 00:12:22, GigabitEthernet0/0/1
d. Verify connectivity to an EIGRP and OSPF network using the ping command as shown. R2 has connectivity to the EIGRP and OSPF networks.
R2# ping 172.16.13.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 172.16.13.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms R2# ping 192.168.20.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.20.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
Step 3: Configure Redistribution on R2
In this step, you will configure redistribution between the EIGRP and OSPF routing domains. Redistribution is configured on the router that connects to both domains. In our topology that is R2.
It is important to note that route redistribution is always performed outbound. This means that the routing table of the router doing the redistribution does not change. Only the routing tables of the routers receiving the redistributed routes will be updated.
a. On R2, redistribute the OSPF routes in EIGRP. Routes redistributed into EIGRP require that a metric be assigned.
R2(config)# router eigrp 1 R2(config-router)# redistribute ospf 123 metric 10000 100 255 1 1500 R2(config-router)# exit
b. On R2, redistribute the EIGRP routes in OSPF. Routes redistributed into OSPF are automatically assigned a metric of 20. In our example, you are assigning a higher cost metric of 100 to redistributed routes.
R2(config)# router ospf 123 R2(config-router)# redistribute eigrp 1 subnets metric 100 R2(config-router)# end
Step 4: Verify Redistribution
a. On R2, verify the EIGRP and OSPF routing table. Notice how the R2 routing table has not change.
R2# show ip route eigrp | begin Gateway
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 7 subnets, 7 masks
D 172.16.1.0/24
[90/130816] via 172.16.0.2, 00:14:22, GigabitEthernet0/0/0
D 172.16.12.0/26
[90/130816] via 172.16.0.2, 00:14:22, GigabitEthernet0/0/0
D 172.16.13.0/27
[90/130816] via 172.16.0.2, 00:14:22, GigabitEthernet0/0/0
D 172.16.14.0/28
[90/130816] via 172.16.0.2, 00:14:22, GigabitEthernet0/0/0
D 172.16.15.0/29
[90/130816] via 172.16.0.2, 00:14:22, GigabitEthernet0/0/0
R2# show ip route ospf | begin Gateway
Gateway of last resort is not set
O 192.168.3.0/24 [110/2] via 192.168.0.2, 00:14:32, GigabitEthernet0/0/1
O IA 192.168.20.0/24 [110/2] via 192.168.0.2, 00:14:32, GigabitEthernet0/0/1
O IA 192.168.21.0/24 [110/2] via 192.168.0.2, 00:14:32, GigabitEthernet0/0/1
O IA 192.168.22.0/24 [110/2] via 192.168.0.2, 00:14:32, GigabitEthernet0/0/1
O IA 192.168.23.0/24 [110/2] via 192.168.0.2, 00:14:32, GigabitEthernet0/0/1
O 192.168.32.0/24 [110/2] via 192.168.0.2, 00:14:32, GigabitEthernet0/0/1
O 192.168.33.0/24 [110/2] via 192.168.0.2, 00:14:32, GigabitEthernet0/0/1
O 192.168.34.0/24 [110/2] via 192.168.0.2, 00:14:32, GigabitEthernet0/0/1
O 192.168.35.0/24 [110/2] via 192.168.0.2, 00:14:32, GigabitEthernet0/0/1
b. On R1, verify the EIGRP routing table. Originally the R1 routing table displayed no entries as R1 was directly connected to all EIGRP networks. However, R1 now knows about the external routes redistributed from the R2 OSPF routing domain. The highlighted entries identify all of the OSPF routes.
R1# show ip route eigrp | begin Gateway
Gateway of last resort is not set
10.0.0.0/24 is subnetted, 1 subnets
D EX 10.10.10.0
[170/281856] via 172.16.0.1, 00:02:02, GigabitEthernet0/0/0
192.168.0.0/30 is subnetted, 1 subnets
D EX 192.168.0.0
[170/281856] via 172.16.0.1, 00:02:02, GigabitEthernet0/0/0
D EX 192.168.3.0/24
[170/281856] via 172.16.0.1, 00:02:02, GigabitEthernet0/0/0
D EX 192.168.20.0/24
[170/281856] via 172.16.0.1, 00:02:02, GigabitEthernet0/0/0
D EX 192.168.21.0/24
[170/281856] via 172.16.0.1, 00:02:02, GigabitEthernet0/0/0
D EX 192.168.22.0/24
[170/281856] via 172.16.0.1, 00:02:02, GigabitEthernet0/0/0
D EX 192.168.23.0/24
[170/281856] via 172.16.0.1, 00:02:02, GigabitEthernet0/0/0
D EX 192.168.32.0/24
[170/281856] via 172.16.0.1, 00:02:02, GigabitEthernet0/0/0
D EX 192.168.33.0/24
[170/281856] via 172.16.0.1, 00:02:02, GigabitEthernet0/0/0
D EX 192.168.34.0/24
[170/281856] via 172.16.0.1, 00:02:02, GigabitEthernet0/0/0
D EX 192.168.35.0/24
[170/281856] via 172.16.0.1, 00:02:02, GigabitEthernet0/0/0
c. Verify the EIGRP routing table on R3. Previously, R3 only had the Area 10 network in its routing table. R3 now knows about the external EIGRP routes redistributed by R2. Also notice that the redistribution command assigned a metric of 100.
R3# show ip route ospf | begin Gateway
Gateway of last resort is not set
10.0.0.0/24 is subnetted, 1 subnets
O IA 10.10.10.0 [110/2] via 192.168.0.1, 00:16:36, GigabitEthernet0/0/0
172.16.0.0/16 is variably subnetted, 6 subnets, 6 masks
O E2 172.16.0.0/30
[110/100] via 192.168.0.1, 00:02:42, GigabitEthernet0/0/0
O E2 172.16.1.0/24
[110/100] via 192.168.0.1, 00:02:42, GigabitEthernet0/0/0
O E2 172.16.12.0/26
[110/100] via 192.168.0.1, 00:02:42, GigabitEthernet0/0/0
O E2 172.16.13.0/27
[110/100] via 192.168.0.1, 00:02:42, GigabitEthernet0/0/0
O E2 172.16.14.0/28
[110/100] via 192.168.0.1, 00:02:42, GigabitEthernet0/0/0
O E2 172.16.15.0/29
[110/100] via 192.168.0.1, 00:02:42, GigabitEthernet0/0/0
d. From all routers, verify connectivity to all configured destinations using the following TCL script. All pings should be successful. Troubleshoot if necessary.
tclsh
foreach address {
192.168.0.1
192.168.20.1
192.168.21.1
192.168.22.1
192.168.23.1
192.168.3.1
192.168.32.1
192.168.33.1
192.168.34.1
192.168.35.1
10.10.10.1
172.16.0.1
172.16.0.2
172.16.1.1
172.16.12.1
172.16.13.1
172.16.14.1
172.16.15.1
} { ping $address }
Part 3: Filter Redistributed Routes using a Distribute List and ACL.
Routes can be filtered using a variety of techniques including:
• Distribute list and ACL – A distribute list allows an access control lists (ACLs) to be applied to routing updates.
• Distribute list and prefix list – A distribute list with a prefix list is an alternative to ACLs designed to filter routes. Prefix lists are not exclusively used with distribute lists but can also be used with route maps and other commands.
• Route maps – Route maps are complex access lists that allow conditions to be tested against a packet or route, and then actions taken to modify attributes of the packet or route.
In this part, you will filter routes using the distribute list and ACL technique.
Step 1: Configure an ACL and distribute list on R2
In this step, you will use a distribute list and ACL to filter routes being advertised from R2 to R1. Specifically, you will filter the OSPF 20 routes (i.e., 192.168.20.0/22) from being advertised by R2 to R1.
a. On R1, verify the routing table entry for the 192.168.20.0/22 route. R1 displays the entry for the 192.169.20.0 network.
R1# show ip route 192.168.20.0
Routing entry for 192.168.20.0/24
Known via "eigrp 1", distance 170, metric 28416, type external
Redistributing via eigrp 1
Last update from 172.16.0.1 on GigabitEthernet0/0/0, 01:54:32 ago
Routing Descriptor Blocks:
* 172.16.0.1, from 172.16.0.1, 01:54:32 ago, via GigabitEthernet0/0/0
Route metric is 28416, traffic share count is 1
Total delay is 1010 microseconds, minimum bandwidth is 10000 Kbit
Reliability 255/255, minimum MTU 1500 bytes
Loading 1/255, Hops 1
b. You will filter the Area 20 networks from being advertised into the EIGRP domain. Although a distribute list could be implemented on the receiving router (i.e., R1), it is usually best to filter routes from the redistributing router. Therefore, on R2, create a standard named ACL called OSPF20-FILTER that denies the 192.168.20.0/22 route. The ACL must also permit all other routes otherwise, no OSPF routes would be redistributed into EIGRP.
R2(config)# ip access-list standard OSPF20-FILTER R2(config-std-nacl)# remark Used with DList to filter OSPF 20 routes R2(config-std-nacl)# deny 192.168.20.0 0.0.3.255 R2(config-std-nacl)# permit any R2(config-std-nacl)# exit
c. Next configure a distribute list under the EIGRP process to filter routes propagated to R1 using the pre-configured ACL.
R2(config)# router eigrp 1 R2(config-router)# distribute-list OSPF20-FILTER out ospf 123 R2(config-router)# end
Step 2: Verify the configuration
a. On R1, verify if the 192.168.20.0 route is now missing from the R1 routing table. The output confirms that the 192.168.20.0/24, 192.168.21.0/24, 192.168.22.0/24, 192.168.23.0/24 (192.168.20.0/22) routes are no longer in the routing table of R1.
R1# show ip route 192.168.20.0
% Network not in table
R1# show ip route eigrp | begin Gateway
Gateway of last resort is not set
10.0.0.0/24 is subnetted, 1 subnets
D EX 10.10.10.0
[170/281856] via 172.16.0.1, 01:56:57, GigabitEthernet0/0/0
192.168.0.0/30 is subnetted, 1 subnets
D EX 192.168.0.0
[170/281856] via 172.16.0.1, 01:56:57, GigabitEthernet0/0/0
D EX 192.168.3.0/24
[170/281856] via 172.16.0.1, 01:56:57, GigabitEthernet0/0/0
D EX 192.168.32.0/24
[170/281856] via 172.16.0.1, 01:56:57, GigabitEthernet0/0/0
D EX 192.168.33.0/24
[170/281856] via 172.16.0.1, 01:56:57, GigabitEthernet0/0/0
D EX 192.168.34.0/24
[170/281856] via 172.16.0.1, 01:56:57, GigabitEthernet0/0/0
D EX 192.168.35.0/24
[170/281856] via 172.16.0.1, 01:56:57, GigabitEthernet0/0/0
Note: If additional router filtering was required, only the OSPF20-FILTER ACL on R2 would need to be altered.
Part 4: Filter Redistributed Routes using a Distribute List and Prefix List
In this part, you will filter routes using the distribute list and prefix list technique.
Using a distribute list with an ACL or with a prefix list basically achieves the same result of filtering routes. However, in large enterprise networks, route filtering can be quite complex. The ACLs can be very extensive and therefore taxing on router resources. For this reason, prefix lists should be used instead of ACLs since they are more efficient and less taxing on router resources than ACLs.
Note: Prefix lists are not exclusively used with distribute lists but can also be used with route maps and other commands.
Step 1: Filter redistributed routes using a distribute list and prefix list.
In this step, a prefix list will be configured with a distribute list to filter R1 routes being advertised from R2 to R3.
a. On R3, verify the routing table entry for the routes learned externally identified with the O E2 source entry. The output displays route entries for the EIGRP networks connected to R1.
R3# show ip route ospf | include O E2 O E2 172.16.0.0/30 O E2 172.16.1.0/24 O E2 172.16.12.0/26 O E2 172.16.13.0/27 O E2 172.16.14.0/28 O E2 172.16.15.0/29
b. Configure R2 with a prefix list identifying which networks to advertise to R3. Specifically, only the networks with the first two octets being 172.16 (i.e., 172.16.0.0/16) with a subnet mask of /24 or less will be advertised.
R2(config)# ip prefix-list EIGRP-FILTER permit 172.16.0.0/16 le 24
c. Configure a distribute list under the OSPF process to filter routes propagated to R3 using the pre-configured prefix list.
R2(config)# router ospf 123 R2(config-router)# distribute-list prefix EIGRP-FILTER out eigrp 1 R2(config-router)# exit
Note: If additional router filtering was required, only the EIGRP-FILTER prefix list on R2 would need to be altered.
d. On R3, verify which EIGRP redistributed routes have been learned from R2. Notice how only the 172.16.1.0/24 route is listed because all other routes have subnet masks greater than /24.
R3# show ip route ospf | include O E2 O E2 172.16.1.0 [110/100] via 192.168.0.1, 02:07:51, GigabitEthernet0/0/0
e. To observe how a prefix list can be used to filter routes, remove the previously configured prefix list and change the prefix list on R2 advertise only EIGRP networks with subnet masks of /26 or greater.
R2(config)# no ip prefix-list EIGRP-FILTER permit 172.16.0.0/16 le 24 R2(config)# ip prefix-list EIGRP-FILTER permit 172.16.0.0/16 ge 26
f. Verify the change on R3 as shown. Now only the 172.16.1.0/24 route is not listed as all other routes have subnet masks greater than or equal to /26.
R3# show ip route ospf | include O E2 O E2 172.16.0.0/30 O E2 172.16.12.0/26 O E2 172.16.13.0/27 O E2 172.16.14.0/28 O E2 172.16.15.0/29
g. Now change the prefix list on R2 to advertise only networks with subnet masks of /28 or less.
R2(config)# no ip prefix-list EIGRP-FILTER permit 172.16.0.0/16 ge 26 R2(config)# ip prefix-list EIGRP-FILTER permit 172.16.0.0/16 le 28
h. Verify the output on R3 as shown. Notice how the 172.16.0.0/30 and 172.16.15.0/29 are no longer advertised as their subnet masks are greater than /28.
R3# show ip route ospf | include O E2 O E2 172.16.1.0/24 O E2 172.16.12.0/26 O E2 172.16.13.0/27 O E2 172.16.14.0/28
Part 5: Filter Redistributed Routes using a Route Map.
Route maps can also be used to filter routes. A route map works like an access list because it has multiple deny and permit statements that are read in a sequential order. However, route maps can match and set specific attributes and therefore provide additional options and more flexibility when redistributing routes.
Route maps can be used for:
– Redistribution – Route maps provide more options and flexibility to the redistribute command.
– Policy-based routing (PBR) – PBR allows an administrator to define routing policy other than basic destination-based routing using the routing table. The route map is applied to an interface using the ip policy route-map interface configuration command.
– BGP – Route maps are the primary tools for implementing BGP policy and allows an administrator to do path control and provide sophisticated manipulation of BGP path attributes. The route map is applied using the BGP neighbor router configuration command.
Step 1: Filter redistributed routes using a route map.
In this step, you will configure R2 to filter the R3 loopback 34 and 35 networks so that they are not redistributed into EIGRP.
a. On R1, display the current routing table.
R1# show ip route eigrp | begin Gateway
Gateway of last resort is not set
10.0.0.0/24 is subnetted, 1 subnets
D EX 10.10.10.0
[170/281856] via 172.16.0.1, 02:51:47, GigabitEthernet0/0/0
192.168.0.0/30 is subnetted, 1 subnets
D EX 192.168.0.0
[170/281856] via 172.16.0.1, 02:51:47, GigabitEthernet0/0/0
D EX 192.168.3.0/24
[170/281856] via 172.16.0.1, 02:51:47, GigabitEthernet0/0/0
D EX 192.168.32.0/24
[170/281856] via 172.16.0.1, 02:51:47, GigabitEthernet0/0/0
D EX 192.168.33.0/24
[170/281856] via 172.16.0.1, 02:51:47, GigabitEthernet0/0/0
D EX 192.168.34.0/24
[170/281856] via 172.16.0.1, 02:51:47, GigabitEthernet0/0/0
D EX 192.168.35.0/24
[170/281856] via 172.16.0.1, 02:51:47, GigabitEthernet0/0/0
b. Route maps can be used to filter redistributed traffic in multiple ways. In this step, you will filter and deny the R3 Lo 34 and Lo 35 networks (i.e., 192.168.34.0/28 and 192.168.35.0/29) from being redistributed into the EIGRP routing domain. All other networks connected to R1 will be redistributed.
On R2, create a standard named ACL called R3-ACL that identifies the R3 Lo 34 and Lo 35 networks (i.e., 192.168.34.0/28 and 192.168.35.0/29) as shown.
R2(config)# ip access-list standard R3-ACL R2(config-std-nacl)# remark ACL used with the R3-FILTER route map R2(config-std-nacl)# permit 192.168.34.0 0.0.0.15 R2(config-std-nacl)# permit 192.168.35.0 0.0.0.7 R2(config-std-nacl)# exit
c. Configure a route map with a statement that denies traffic based on a match with the named ACL. Then add a permit statement without a match statement to provide an explicit “permit all”.
R2(config)# route-map R3-FILTER deny 10 R2(config-route-map)# description RM filters R3 OSPF routes R2(config-route-map)# match ip address R3-ACL R2(config-route-map)# exit R2(config)# route-map R3-FILTER permit 20 R2(config-route-map)# description RM permits all other R3 OSPF routes R2(config-route-map)# exit
d. Apply this route map to EIGRP by reentering the redistribute command using the route-map keyword.
R2(config)# router eigrp 1 R2(config-router)# redistribute ospf 123 route-map R3-FILTER metric 1000000 100 255 1 1500
e. Verify that the two R3 networks are filtered out in the R1 routing table. Notice that the 192.168.34.0/28 and 192.168.35.0/29 networks are no longer in the R1 routing table.
R1# show ip route eigrp | begin Gateway
Gateway of last resort is not set
10.0.0.0/24 is subnetted, 1 subnets
D EX 10.10.10.0 [170/28416] via 172.16.0.1, 00:00:14, GigabitEthernet0/0/0
192.168.0.0/30 is subnetted, 1 subnets
D EX 192.168.0.0
[170/28416] via 172.16.0.1, 00:00:14, GigabitEthernet0/0/0
D EX 192.168.3.0/24
[170/28416] via 172.16.0.1, 00:00:14, GigabitEthernet0/0/0
D EX 192.168.32.0/24
[170/28416] via 172.16.0.1, 00:00:14, GigabitEthernet0/0/0
D EX 192.168.33.0/24
[170/28416] via 172.16.0.1, 00:00:14, GigabitEthernet0/0/0
Step 2: Filter redistributed routes and set attributes using a route map.
The preceding step was a simple example of using a route map to filter redistributed routes. However, route maps can be used to do much more.
In this step, you will filter the 172.16.13.0/27 network from R1 and change its OSPF metric to 25 instead of 100 like all other redistributed routes. You will also change its metric type from an external type 2 route (i.e., O E2), to an external type 1 route (i.e., O E1).
a. On R3, verify the routing table entry for the routes learned externally identified with the 0 E2 source entry. The 172.16.13.0/27 route will be configured with additional attributes.
R3# show ip route ospf | begin Gateway
Gateway of last resort is not set
10.0.0.0/24 is subnetted, 1 subnets
O IA 10.10.10.0 [110/2] via 192.168.0.1, 03:42:32, GigabitEthernet0/0/0
172.16.0.0/16 is variably subnetted, 4 subnets, 4 masks
O E2 172.16.1.0/24
[110/100] via 192.168.0.1, 01:17:56, GigabitEthernet0/0/0
O E2 172.16.12.0/26
[110/100] via 192.168.0.1, 01:20:12, GigabitEthernet0/0/0
O E2 172.16.13.0/27
[110/100] via 192.168.0.1, 01:20:12, GigabitEthernet0/0/0
O E2 172.16.14.0/28
[110/100] via 192.168.0.1, 01:20:12, GigabitEthernet0/0/0
b. Although an ACL could be used, this example will use a prefix list. Configure a prefix list identifying the route to be filtered.
R2(config)# ip prefix-list R1-PL permit 172.16.13.0/27
c. Configure a route map matching the identified route in the prefix list and assign the OSPF metric cost of 25 and change the metric type to External Type 1. Then add a permit statement without a match statement acting as an explicit “permit all”.
R2(config)# route-map R1-FILTER permit 10 R2(config-route-map)# description RM filters 172.16.13.0/27 R2(config-route-map)# match ip address prefix-list R1-PL R2(config-route-map)# set metric 25 R2(config-route-map)# set metric-type type-1 R2(config-route-map)# exit R2(config)# route-map R1-FILTER permit 20 R2(config-route-map)# description RM permits all other R1 OSPF routes R2(config-route-map)# exit
d. Apply this route map to OSPF by reentering the redistribute command using the route-map keyword.
R2(config)# router ospf 123 R2(config-router)# redistribute eigrp 1 metric 100 subnets route-map R1-FILTER R2(config-router)# exit
e. Verify that the two R3 networks are filtered out in the R1 routing table. Notice that only the 172.16.13.0/27 route is an OSPF External Type 1 route (i.e., O E1) with a cost metric of 26 (i.e., the assigned metric cost of 25 plus the cost of 1 for the R2 to R3 link).
R3# show ip route ospf | begin Gateway
Gateway of last resort is not set
10.0.0.0/24 is subnetted, 1 subnets
O IA 10.10.10.0 [110/2] via 192.168.0.1, 03:48:26, GigabitEthernet0/0/0
172.16.0.0/16 is variably subnetted, 4 subnets, 4 masks
O E2 172.16.1.0/24
[110/100] via 192.168.0.1, 01:23:50, GigabitEthernet0/0/0
O E2 172.16.12.0/26
[110/100] via 192.168.0.1, 01:26:06, GigabitEthernet0/0/0
O E1 172.16.13.0/27
[110/26] via 192.168.0.1, 00:00:04, GigabitEthernet0/0/0
O E2 172.16.14.0/28
[110/100] via 192.168.0.1, 01:26:06, GigabitEthernet0/0/0
Router Interface Summary Table
| Router Model | Ethernet Interface #1 | Ethernet Interface #2 | Serial Interface #1 | Serial Interface #2 |
|---|---|---|---|---|
| 1800 | Fast Ethernet 0/0 (F0/0) | Fast Ethernet 0/1 (F0/1) | Serial 0/0/0 (S0/0/0) | Serial 0/0/1 (S0/0/1) |
| 1900 | Gigabit Ethernet 0/0 (G0/0) | Gigabit Ethernet 0/1 (G0/1) | Serial 0/0/0 (S0/0/0) | Serial 0/0/1 (S0/0/1) |
| 2801 | Fast Ethernet 0/0 (F0/0) | Fast Ethernet 0/1 (F0/1) | Serial 0/1/0 (S0/1/0) | Serial 0/1/1 (S0/1/1) |
| 2811 | Fast Ethernet 0/0 (F0/0) | Fast Ethernet 0/1 (F0/1) | Serial 0/0/0 (S0/0/0) | Serial 0/0/1 (S0/0/1) |
| 2900 | Gigabit Ethernet 0/0 (G0/0) | Gigabit Ethernet 0/1 (G0/1) | Serial 0/0/0 (S0/0/0) | Serial 0/0/1 (S0/0/1) |
| 4221 | Gigabit Ethernet 0/0/0 (G0/0/0) | Gigabit Ethernet 0/0/1 (G0/0/1) | Serial 0/1/0 (S0/1/0) | Serial 0/1/1 (S0/1/1) |
| 4300 | Gigabit Ethernet 0/0/0 (G0/0/0) | Gigabit Ethernet 0/0/1 (G0/0/1) | Serial 0/1/0 (S0/1/0) | Serial 0/1/1 (S0/1/1) |
Note: To find out how the router is configured, look at the interfaces to identify the type of router and how many interfaces the router has. There is no way to effectively list all the combinations of configurations for each router class. This table includes identifiers for the possible combinations of Ethernet and Serial interfaces in the device. The table does not include any other type of interface, even though a specific router may contain one. An example of this might be an ISDN BRI interface. The string in parenthesis is the legal abbreviation that can be used in Cisco IOS commands to represent the interface.
Device Configs – Final
Router R1
R1# show run Building configuration... Current configuration : 1754 bytes ! version 16.9 service timestamps debug datetime msec service timestamps log datetime msec platform qfp utilization monitor load 80 no platform punt-keepalive disable-kernel-core ! hostname R1 ! boot-start-marker boot-end-marker ! no aaa new-model ! no ip domain lookup ! login on-success log ! subscriber templating ! multilink bundle-name authenticated ! spanning-tree extend system-id ! redundancy mode none ! interface Loopback1 ip address 172.16.1.1 255.255.255.0 ! interface Loopback12 ip address 172.16.12.1 255.255.255.192 ! interface Loopback13 ip address 172.16.13.1 255.255.255.224 ! interface Loopback14 ip address 172.16.14.1 255.255.255.240 ! interface Loopback15 ip address 172.16.15.1 255.255.255.248 ! interface GigabitEthernet0/0/0 description Connection to R2 ip address 172.16.0.2 255.255.255.252 negotiation auto ! interface GigabitEthernet0/0/1 no ip address negotiation auto ! interface Serial0/1/0 no ip address ! interface Serial0/1/1 no ip address ! router eigrp 1 network 172.16.0.0 0.0.0.3 network 172.16.1.0 0.0.0.255 network 172.16.12.0 0.0.0.63 network 172.16.13.0 0.0.0.31 network 172.16.14.0 0.0.0.15 network 172.16.15.0 0.0.0.7 eigrp router-id 1.1.1.1 ! ip forward-protocol nd no ip http server ip http secure-server ! control-plane ! banner motd ^C This is R1, Controlling Routing Updates ^C ! line con 0 exec-timeout 0 0 logging synchronous transport input none stopbits 1 line aux 0 stopbits 1 line vty 0 4 login ! end
Router R2
R2# show run Building configuration... Current configuration : 2513 bytes ! version 16.9 service timestamps debug datetime msec service timestamps log datetime msec platform qfp utilization monitor load 80 no platform punt-keepalive disable-kernel-core ! hostname R2 ! boot-start-marker boot-end-marker ! no aaa new-model ! no ip domain lookup ! login on-success log ! subscriber templating ! multilink bundle-name authenticated ! spanning-tree extend system-id ! redundancy mode none ! interface Loopback10 ip address 10.10.10.1 255.255.255.0 ip ospf network point-to-point ! interface GigabitEthernet0/0/0 description Connection to R1 ip address 172.16.0.1 255.255.255.252 negotiation auto ! interface GigabitEthernet0/0/1 description Connection to R3 ip address 192.168.0.1 255.255.255.252 negotiation auto ! router eigrp 1 distribute-list OSPF20-FILTER out ospf 123 network 172.16.0.0 0.0.0.3 redistribute ospf 123 metric 1000000 100 255 1 1500 route-map R3-FILTER eigrp router-id 2.2.2.2 ! router ospf 123 router-id 2.2.2.2 redistribute eigrp 1 metric 100 subnets route-map R1-FILTER network 10.10.10.0 0.0.0.255 area 10 network 192.168.0.0 0.0.0.3 area 0 distribute-list prefix EIGRP-FILTER out eigrp 1 ! ip forward-protocol nd no ip http server ip http secure-server ! ip prefix-list EIGRP-FILTER seq 5 permit 172.16.0.0/16 le 28 ! ip prefix-list R1-PL seq 5 permit 172.16.13.0/27 ! ip access-list standard OSPF20-FILTER remark Used with DList to filter OSPF 20 routes deny 192.168.20.0 0.0.3.255 permit any ip access-list standard R3-ACL remark ACL used with the R3-FILTER route map permit 192.168.34.0 0.0.0.15 permit 192.168.35.0 0.0.0.7 ! route-map R3-FILTER deny 10 description RM filters R3 OSPF routes match ip address R3-ACL ! route-map R3-FILTER permit 20 description RM permits all other R3 OSPF routes ! route-map R1-FILTER permit 10 description RM filters 172.16.13.0/27 match ip address prefix-list R1-PL set metric 25 set metric-type type-1 ! route-map R1-FILTER permit 20 description RM permits all other R1 OSPF routes ! control-plane ! banner motd ^C This is R2, Controlling Routing Updates ^C ! line con 0 exec-timeout 0 0 logging synchronous transport input none stopbits 1 line aux 0 stopbits 1 line vty 0 4 login ! end
Router R3
R3# show run Building configuration... Current configuration : 2400 bytes ! version 16.9 service timestamps debug datetime msec service timestamps log datetime msec platform qfp utilization monitor load 80 no platform punt-keepalive disable-kernel-core ! hostname R3 ! boot-start-marker boot-end-marker ! no aaa new-model ! no ip domain lookup ! login on-success log ! subscriber templating ! multilink bundle-name authenticated ! spanning-tree extend system-id ! redundancy mode none ! interface Loopback3 ip address 192.168.3.1 255.255.255.0 ip ospf network point-to-point ! interface Loopback20 ip address 192.168.20.1 255.255.255.0 ip ospf network point-to-point ! interface Loopback21 ip address 192.168.21.1 255.255.255.0 ip ospf network point-to-point ! interface Loopback22 ip address 192.168.22.1 255.255.255.0 ip ospf network point-to-point ! interface Loopback23 ip address 192.168.23.1 255.255.255.0 ip ospf network point-to-point ! interface Loopback32 ip address 192.168.32.1 255.255.255.0 ip ospf network point-to-point ! interface Loopback33 ip address 192.168.33.1 255.255.255.0 ip ospf network point-to-point ! interface Loopback34 ip address 192.168.34.1 255.255.255.0 ip ospf network point-to-point ! interface Loopback35 ip address 192.168.35.1 255.255.255.0 ip ospf network point-to-point ! interface GigabitEthernet0/0/0 description Connection to R2 ip address 192.168.0.2 255.255.255.252 negotiation auto ! interface GigabitEthernet0/0/1 no ip address negotiation auto ! interface Serial0/1/0 no ip address ! interface Serial0/1/1 no ip address ! router ospf 123 router-id 3.3.3.3 network 192.168.0.0 0.0.0.3 area 0 network 192.168.3.0 0.0.0.255 area 0 network 192.168.20.0 0.0.3.255 area 20 network 192.168.32.0 0.0.0.63 area 0 network 192.168.33.0 0.0.0.31 area 0 network 192.168.34.0 0.0.0.15 area 0 network 192.168.35.0 0.0.0.7 area 0 ! ip forward-protocol nd no ip http server ip http secure-server ! control-plane ! banner motd ^C This is R3, Controlling Routing Updates ^C ! line con 0 exec-timeout 0 0 logging synchronous transport input none stopbits 1 line aux 0 stopbits 1 line vty 0 4 login ! end
