1. Refer to the exhibit. Which technology generated the event log?
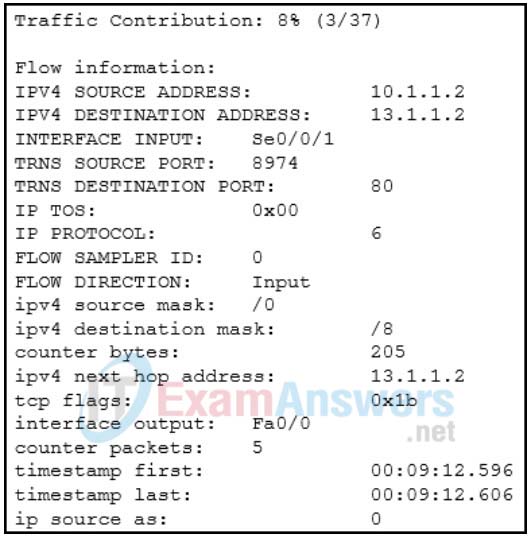
- Wireshark
- web proxy
- syslog
- Netflow
2. A network engineer is using SNMP manager software to monitor and manage network performance. In addition to polling network devices at regular time intervals, the engineer is configuring the devices to generate messages that inform the SNMP manager of specified events. What message type is configured on those devices that allows them to send unsolicited messages?
- trap
- set request
- get-bulk-request
- get-response
3. What is a tool in the Cisco DNA Center that can apply machine learning in order to diagnose network issues and offer guided remediation steps to fix issues?
- DNA Assurance
- ERSPAN
- RSPAN
- SNMP
- syslog
4. Which command can an administrator issue on a Cisco router to send debug messages to the vty lines?
- terminal monitor
- logging console
- logging buffered
- logging synchronous
5. An administrator issued the service password-encryption command to apply encryption to the passwords configured for enable password, vty, and console lines. What will be the consequences if the administrator later issues the no service password-encryption command?
- It will remove encryption from all passwords.
- It will reverse only the vty and console password encryptions.
- It will not reverse any encryption.
- It will reverse only the enable password encryption.
6. What happens when the transport input ssh command is entered on the switch vty lines?
- The SSH client on the switch is enabled.
- Communication between the switch and remote users is encrypted.
- The switch requires a username/password combination for remote access.
- The switch requires remote connections via a proprietary client software.
7. An administrator has configured an access list on R1 to allow SSH administrative access from host 172.16.1.100. Which command correctly applies the ACL?
- R1(config-if)# ip access-group 1 in
- R1(config-if)# ip access-group 1 out
- R1(config-line)# access-class 1 in
- R1(config-line)# access-class 1 out
8. Which technology via the syslog protocol enhances real-time debugging by displaying the date and time associated with each monitored event?
- syslog facilities
- syslog severity levels
- syslog service timestamps
- syslog service identifiers
9. Which two steps are required before SSH can be enabled on a Cisco router? (Choose two.)
- Give the router a host name and domain name.
- Create a banner that will be displayed to users when they connect.
- Generate a set of secret keys to be used for encryption and decryption.
- Set up an authentication server to handle incoming connection requests.
- Enable SSH on the physical interfaces where the incoming connection requests will be received.
10. How do network administrators use IP SLAs to monitor a network and to detect a network failure early?
- by using network protocol analyzers to evaluate errors
- by measuring the CPU and memory usage on routers and switches
- by simulating network data and IP services to collect network performance data in real time
- by taking a snap shot of network performance and comparing with an established baseline
11. Refer to the exhibit. What feature does an SNMP manager need in order to be able to set a parameter on switch ACSw1?
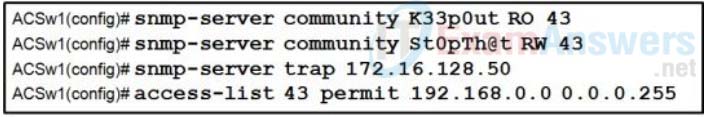
- a manager who is using an SNMP string of K44p0ut
- a manager who is using an Inform Request MIB
- a manager who is using host 192.168.0.5
- a manager who is using authPriv
12. Refer to the exhibit. What configuration would need to be applied to the vty lines in order to use this AAA policy?

- login authentication admin
- login authentication radius
- login authentication local
- No configuration is necessary.
13. A company is designing a network monitoring system and is considering SNMPv3. What are three characteristics of SNMPv3? (Choose three.)
- It uses UDP port 514 to send event notifications to message collectors.
- It uses message integrity to ensure that packets have not been altered in transit.
- It uses expanded error codes to identify different types of error conditions.
- It uses authentication to determine if messages are from a valid source.
- It uses encryption to scramble the content of packets to prevent unauthorized access.
- It uses a flat structure of MIB to improve the speed of access to the information.
14. Which protocol or measure should be used to mitigate the vulnerability of using FTP to transfer documents between a teleworker and the company file server?
- SCP
- TFTP
- ACLs on the file server
- out-of-band communication channel
15. A syslog server has received the message shown.
*Mar 1 00:07:18.783: %SYS-5-CONFIG_I: Configured from console by vty0 (172.16.45.1)
What can be determined from the syslog message?
- The message is a normal notification and should not be reviewed.
- The message is a Log_Alert notification message.
- The message description displays that the console line was accessed locally.
- The message informs the administrator that a user with an IP address of 172.16.45.1 configured this device remotely.
“Do I Know This Already?” Quiz Answers:
1. Which of the following are the default serial terminal settings for a Cisco router or switch? (Choose two.)
- 9600 baud
- 16 data bits
- 1 stop bit
- Parity
2. Which command enables you to define which protocols will be used for remote access to a Cisco device using vty lines?
- transport input
- login
- login local
- exec
3. Which command enables you to specify that SSH access will be authenticated using the local database?
- login
- login local
- login authentication default
- transport input ssh
4. The following command has been typed on a Cisco IOS router:
copy http://10.0.3.8/cisco_ios_files/c3900-universalk9-mz.SPA.156-3.M6a.bin flash:c3900-universalk9-mz.SPA.156-3.M6a.bin
What will this accomplish?
- A configuration file will be copied from a web server to the router.
- An IOS image will be copied from the router to the web server.
- An IOS image will be copied from the web server to the router.
- A configuration file will be copied from a router to a web server.
5. Timestamps are not appearing with syslog messages on your router. What is most likely the reason for this?
- NTP is not configured correctly.
- The router has the wrong time set, according to the show clock output.
- The no service timestamps command was executed on the router.
- You have not used the terminal monitor command.
6. Which of the following is a valid SNMP security level that provides authentication using a hashing algorithm such as SHA and encryption using an encryption algorithm such as AES?
- noAUTHnoPRIV
- AUTHnoPRIV
- AUTHPRIV
- PRIV
7. In which of the following situations would you require an IP SLA responder?
- Testing one-way delay for voice packets
- Testing connectivity for a floating static route
- Testing connectivity for First-Hop Resiliency Protocol
- Testing round-trip time with an ICMP echo
8. Which command is used to verify the version of NetFlow that has been configured on a router?
- show ip flow export
- show ip flow Interface
- show ip flow cache
- show flow record
9. Which command is used to verify the flow exporter that has been assigned to a flow monitor?
- show flow Interface
- show flow exporter
- show flow monitor
- show flow record
10. Which Cisco DNA Center Assurance tool graphically shows the path that applications and services running on a client take through all the devices on the network to reach the destination?
- Application Experience
- Device 360
- Client 360
- Path Trace
