CCNA Routing and Switching
Routing & Switching Essentials
Practice Skills Assessment Part I – Type A – Type B
A few things to keep in mind while completing this activity:
- Do not use the browser Back button or close or reload any exam windows during the exam.
- Do not close Packet Tracer when you are done. It will close automatically.
- Click the Submit Assessment button in the browser window to submit your work.
Introduction
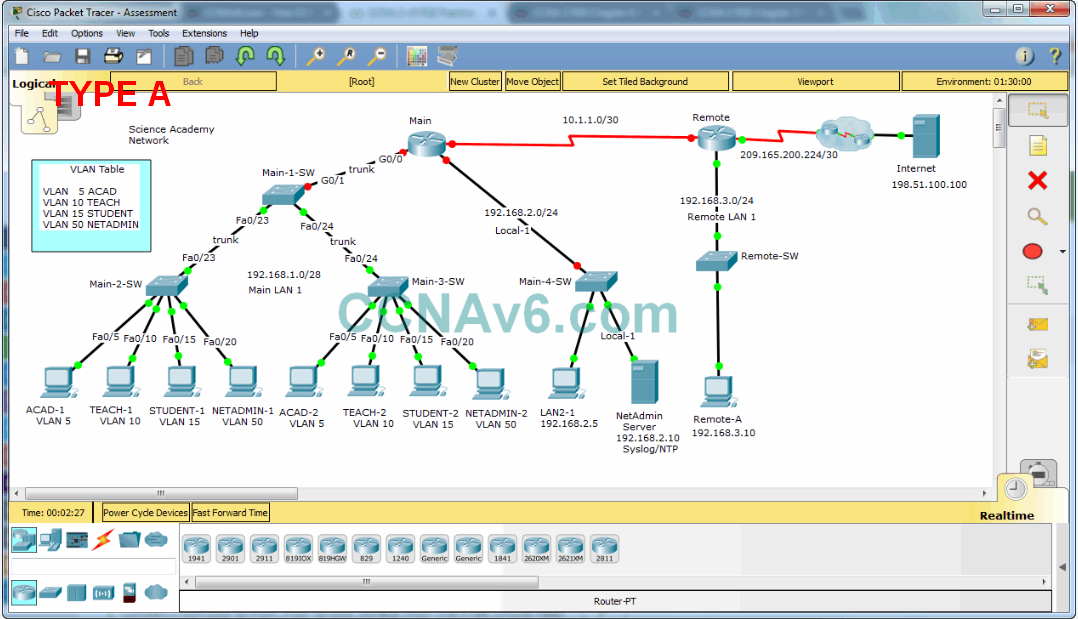
In this practice skills assessment, you will configure the Science Academy network. You will perform basic router configuration tasks, address router interfaces and hosts, and configure VLANs, trunking, and routing between VLANs. You will also configure and customize RIPv2 and control access to router vty lines with a standard named ACL. For a full list of tasks, see below.
You are not required to configure the following:
- Main-4-SW
- Remote-SW
- LAN2-1
- Remote-A
- NetAdmin
- Internet
- Hosts attached to Main-3-SW
All IOS device configurations should be completed from a direct terminal connection to the device console. In addition, many values that are required to complete the configurations have not been given to you. In those cases, create the values that you need to complete the requirements.
You will practice and be assessed on the following skills:
- Configuration of initial device settings
- Interface addressing
- Configuration of VLANs and trunking
- Routing between VLANs
- Dynamic routing with RIPv2
- Configuration of standard ACLs
- Switch port security configuration
- Remote switch management configuration
- Syslog and NTP configuration
You will configure specific devices the following:
Main:
- Basic device configuration
- Interface addressing
- Routing between VLANs
- RIPv2 routing
- Standard numbered ACL on vty
- Syslog logging with NTP timestamping
Remote:
- RIPv2 routing
Main-1-SW:
- VLANs and trunking
- Management interface
Main-2-SW:
- VLANs and trunking
- Port security
- Management interface
Main-3-SW:
- VLANs and trunking
- Management interface
Main-2-SW Hosts:
- IP addresses
- Subnet masks
- Gateways
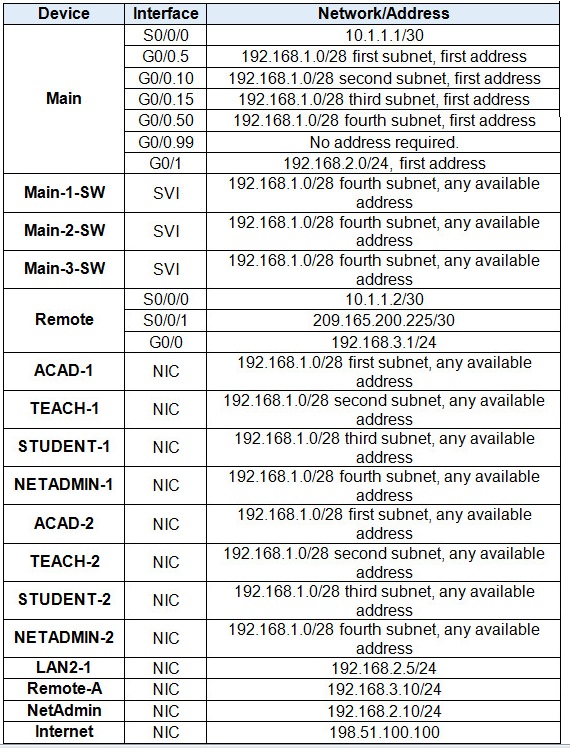
Addressing Table
Use the following addresses to configure the network. Some addresses are preconfigured on devices that you are not required to configure, and are provided for reference purposes only.
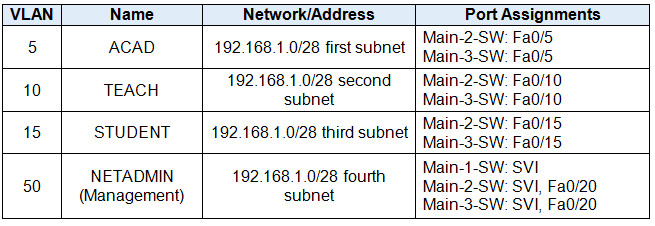
VLAN Table
Step1: Basic Device Configuration
Complete a basic device configuration on the Main router. Perform the following tasks:
- Disable DNS lookup.
- Configure the device with the name shown in the addressing table.
- Configure password encryption.
- Assign the encrypted type of privileged EXEC password.
- Configure a MOTD banner to warn users that unauthorized access is prohibited.
- Configure the console line so that router status messages will not interrupt command line input.
- Configure the console to require a password for access.
- Configure the VTY ports to only accept connections over SSH. Use the following values:
Domain Name: cisco.com
Local Username: admin
User Password: class
Modulus: 1024
Version: 2
The values for your SSH configuration must match these values exactly in order for you to receive credit for your configuration.
Step 2: Interface Addressing Main
Activate and configure the G0/1 and S0/0/0 interfaces of the Main router with the IP addresses given in the Addressing Table. The G0/0 interface will be configured later in the assessment.Configure descriptions for these interfaces.
Step 3: VLANs and Trunking
Configure the Main-1-SW, Main-2-SW, and Main-3-SW switches with VLANs and trunking according to the values in the VLAN table.
- Add the VLANs to the switches.
- Name the VLANs exactly as shown in the VLAN table.
- Configure the links between the Main-1-SW, Main-2-SW, and Main-3-SW switches as trunks. Configure the link between Main-1-SW and Main as a trunk. All trunking interfaces should be statically configured as trunks.
- Assign the appropriate ports to the VLANs.
Step 4: Routing Between VLANs
Configure routing between VLANs on the Main router. Use the information in the addressing and VLAN tables.
Step 5: Access Control List Configuration
Configure a named standard ACL that meets the following requirements:
- The list should be named block15. The name must match this value exactly in order for you to receive credit for your work.
- Prevent any host with an address on the VLAN15subnetwork from accessing the VLAN10 subnetwork.
- All other hosts should be permitted
- The list should have two statements. One statement for each requirement in steps 5b and 5c.
Step 6: Switch Virtual Interface (SVI) Configuration
Configure the switch virtual management interfaces on Main-1-SW, Main-2-SW, and Main-3-SW. Use the information in the addressing and VLAN tables for your configuration. All switches should be reachable from hosts on other networks for the purpose of this assessment.
Step 7: Switch Port Security Configuration
Improve network security by configuring the Main-2-SW switch with the following. You are only required to configure these settings on this one switch for this assessment.
- Disable ALL unused switch ports.
- Activate port security on all ports that have hosts connected.
- Allow only a maximum of two MAC addresses to access the active switch ports.
- Configure the switch ports to automatically learn the two allowed MAC addresses and record the addresses in the running configuration.
- Configure the switch ports so that, if the maximum number of addresses for each port is exceeded, packets with unknown source addresses are dropped until a sufficient number of secure MAC addresses are removed. Notification that a violation has occurred is not required.
Step 8: Dynamic Routing
Configure RIPv2 routing on Main and Remote.
- Configure RIPv2 on Main and Remote so that all networks are reachable.
- Configure all LAN physical interfaces so that RIP updates are not sent out to the LANs.
- Be sure to use the version of RIP that supports classless routing.
- Prevent RIP from automatically summarizing networks.
- Configure RIP to automatically send the default route that is already configured on Remoteto Main.
Step 9: Configure Network Monitoring
Configure NTP and Syslog server logging on Main.
- Activate the logging and debug timestamp services.
- Configure Mainas an NTP client. The NTP server is NetAdmin with the address of 192.168.2.10.
- Configure Syslog to send debug levelmessages to the NetAdmin logging server.
Step 10: Configure Host Addressing
Address the hosts that are connected to Main-2-SW so that they have connectivity to the IP address of the Internet server on the Internet. Use the information provided in the Addressing Table.
Intructions- Answers Script - Type A
Main - Router
enable configure terminal no ip domain-lookup hostname Main service password-encryption enable secret class banner motd $users that unauthorized access is prohibited$ line console 0 logging synchronous password cisco login exit ip domain-name cisco.com username admin password class crypto key generate rsa yes 1024 ip ssh version 2 line vty 0 15 transport input ssh login local exit interface gigabitEthernet 0/1 ip address 192.168.2.1 255.255.255.0 no shutdown description Local-1 int s0/0/0 ip address 10.1.1.1 255.255.255.252 no shutdown description Connection-to-Local exit interface g0/0.5 encapsulation dot1Q 5 ip address 192.168.1.1 255.255.255.240 interface g0/0.10 encapsulation dot1Q 10 ip address 192.168.1.17 255.255.255.240 interface g0/0.15 encapsulation dot1Q 15 ip address 192.168.1.33 255.255.255.240 interface g0/0.50 encapsulation dot1Q 50 ip address 192.168.1.49 255.255.255.240 exit int g0/0 no sh no shutdown exit ip access-list standard block15 deny 192.168.1.32 0.0.0.15 permit any line vty 0 4 access-class block15 in int g0/0.10 ip access-group block15 out exit Router rip version 2 network 10.1.1.0 network 192.168.1.0 network 192.168.1.16 network 192.168.1.32 network 192.168.1.48 network 192.168.2.0 no auto-summary passive-interface g0/0.5 passive-interface g0/0.10 passive-interface g0/0.15 passive-interface g0/0.50 passive-interface g0/0 passive-interface g0/1 exit service timestamps log datetime msec service timestamps debug datetime msec ntp server 192.168.2.10 logging 192.168.2.10 logging trap debugging ntp update-calendar
Remote - Router
en conf ter router rip version 2 network 10.1.1.0 network 192.168.3.0 default-information originate no auto-summary passive-interface s0/0/1 passive-interface g0/0
Main-1-SW (Switch)
enable configure terminal vlan 5 name ACAD vlan 10 name TEACH vlan 15 name STUDENT vlan 50 name NETADMIN exit interface f0/23 switchport mode trunk interface f0/24 switchport mode trunk interface g0/1 switchport mode trunk exit int vlan 50 ip address 192.168.1.50 255.255.255.240 no shutdown exit ip default-gateway 192.168.1.49
Main-2-SW
enable configure terminal vlan 5 name ACAD vlan 10 name TEACH vlan 15 name STUDENT vlan 50 name NETADMIN exit int f0/23 switchport mode trunk int f0/5 switchport mode access switchport access vlan 5 switchport port-security switchport port-security maximum 2 switchport port-security mac-address sticky switchport port-security violation protect int f0/10 switchport mode access switchport access vlan 10 switchport port-security switchport port-security maximum 2 switchport port-security mac-address sticky switchport port-security violation protect switchport port-security mac-address sticky 0001.C933.4067 int f0/15 switchport mode access switchport access vlan 15 switchport port-security switchport port-security maximum 2 switchport port-security mac-address sticky switchport port-security violation protect switchport port-security mac-address sticky 0090.211A.8676 int f0/20 switchport mode access switchport access vlan 50 switchport port-security switchport port-security maximum 2 switchport port-security mac-address sticky switchport port-security violation protect switchport port-security mac-address sticky 0001.C70C.EC63 exit int vlan 50 ip address 192.168.1.51 255.255.255.240 no shutdown exit ip default-gateway 192.168.1.49 int range f0/1-4 shutdown int range f0/6-9 shutdown int range f0/11-14 shutdown int range f0/16-19 shutdown int range f0/21-22 shutdown int f0/24 shutdown int range g0/1-2 shutdown
Main-3-SW
enable configure terminal vlan 5 name ACAD vlan 10 name TEACH vlan 15 name STUDENT vlan 50 name NETADMIN exit int f0/24 switchport mode trunk exit interface f0/5 switchport mode access switchport access vlan 5 interface f0/10 switchport mode access switchport access vlan 10 interface f0/15 switchport mode access switchport access vlan 15 interface f0/20 switchport mode access switchport access vlan 50 int vlan 50 ip add 192.168.1.52 255.255.255.240 no sh exit ip default-gateway 192.168.1.49 interface FastEthernet0/24 switchport mode trunk
Host Addressing
| Hosts | ACAD-1 | TEACH-1 | STUDENT-1 | NETADMIN-1 |
| IP Address | 192.168.1.10 | 192.168.1.26 | 192.168.1.42 | 192.168.1.58 |
| Subnet mask | 255.255.255.240 | 255.255.255.240 | 255.255.255.240 | 255.255.255.240 |
| Default gateway | 192.168.1.1 | 192.168.1.17 | 192.168.1.33 | 192.168.1.49 |
A few things to keep in mind while completing this activity:
- Do not use the browser Back button or close or reload any exam windows during the exam.
- Do not close Packet Tracer when you are done. It will close automatically.
- Click the Submit Assessment button in the browser window to submit your work.
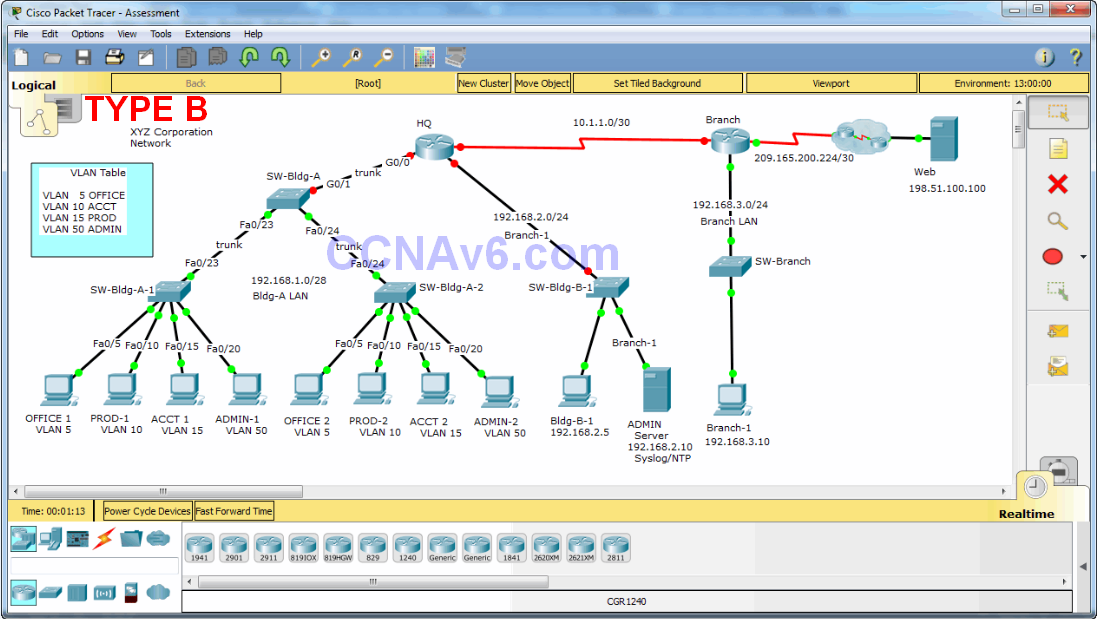
Introduction
In this practice skills assessment, you will configure the Science Academy network. You will perform basic router configuration tasks, address router interfaces and hosts, and configure VLANs, trunking, and routing between VLANs. You will also configure and customize RIPv2 and control access to router vty lines with a standard named ACL. For a full list of tasks, see below.
You are not required to configure the following:
- SW-Bldg-B-1
- SW-Branch
- BLDG-B-1
- Branch-1
- Admin
- Web
- Hosts attached to SW-Bldg-A-2
All IOS device configurations should be completed from a direct terminal connection to the device console. In addition, many values that are required to complete the configurations have not been given to you. In those cases, create the values that you need to complete the requirements.
You will practice and be assessed on the following skills:
- Configuration of initial device settings
- Interface addressing
- Configuration of VLANs and trunking
- Routing between VLANs
- Dynamic routing with RIPv2
- Configuration of standard ACLs
- Switch port security configuration
- Remote switch management configuration
- Syslog and NTP configuration
You will configure specific devices the following:
HQ:
- Basic device configuration
- Interface addressing
- Routing between VLANs
- RIPv2 routing
- Standard numbered ACL on vty
- Syslog logging with NTP timestamping
Branch:
- RIPv2 routing
SW-Bldg-A:
- VLANs and trunking
- Management interface
SW-Bldg-A-1:
- VLANs and trunking
- Port security
- Management interface
SW-Bldg-A-2:
- VLANs and trunking
- Management interface
SW-Bldg-A-1 Hosts:
- IP addresses
- Subnet masks
- Default gateways
Addressing Table
Use the following addresses to configure the network. Some addresses are preconfigured on devices that you are not required to configure, and are provided for reference purposes only.
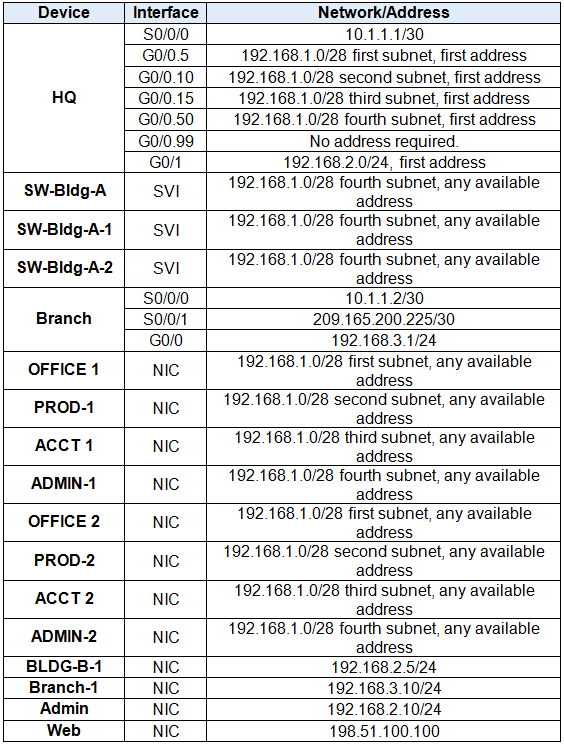
VLAN Table
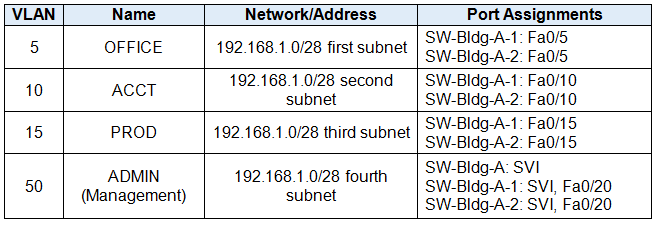
Step1: Basic Device Configuration
Complete a basic device configuration on the HQ router. Perform the following tasks:
- Disable DNS lookup.
- Configure the device with the name shown in the addressing table.
- Configure password encryption.
- Assign the encrypted type of privileged EXEC password.
- Configure a MOTD banner to warn users that unauthorized access is prohibited.
- Configure the console line so that router status messages will not interrupt command line input.
- Configure the console to require a password for access.
- Configure the VTY ports to only accept connections over SSH. Use the following values:
Domain Name: cisco.com
Local Username: admin
User Password: class
Modulus: 1024
Version: 2
The values for your SSH configuration must match these values exactly in order for you to receive credit for your configuration.
Step 2: Interface Addressing HQ
Activate and configure the G0/1 and S0/0/0 interfaces of the HQ router with the IP addresses given in the Addressing Table. The G0/0 interface will be configured later in the assessment.Configure descriptions for these interfaces.
Step 3: VLANs and Trunking
Configure the SW-Bldg-A, SW-Bldg-A-1, and SW-Bldg-A-2 switches with VLANs and trunking according to the values in the VLAN table.
- Add the VLANs to the switches.
- Name the VLANs exactly as shown in the VLAN table.
- Configure the links between the SW-Bldg-A, SW-Bldg-A-1, and SW-Bldg-A-2 switches as trunks. Configure the link between SW-Bldg-A and HQ as a trunk. All trunking interfaces should be statically configured as trunks.
- Assign the appropriate ports to the VLANs.
Step 4: Routing Between VLANs
Configure routing between VLANs on the HQ router. Use the information in the addressing and VLAN tables.
Step 5: Access Control List Configuration
Configure a named standard ACL that meets the following requirements:
- The list should be named block15. The name must match this value exactly in order for you to receive credit for your work.
- Prevent any host with an address on the VLAN15subnetwork from accessing the VLAN10 subnetwork.
- All other hosts should be permitted
- The list should have two statements. One statement for each requirement in steps 5b and 5c.
Step 6: Switch Virtual Interface (SVI) Configuration
Configure the switch virtual management interfaces on SW-Bldg-A, SW-Bldg-A-1, and SW-Bldg-A-2. Use the information in the addressing and VLAN tables for your configuration. All switches should be reachable from hosts on other networks for the purpose of this assessment.
Step 7: Switch Port Security Configuration
Improve network security by configuring the SW-Bldg-A-1 switch with the following. You are only required to configure these settings on this one switch for this assessment.
- Disable ALL unused switch ports.
- Activate port security on all ports that have hosts connected.
- Allow only a maximum of two MAC addresses to access the active switch ports.
- Configure the switch ports to automatically learn the two allowed MAC addresses and record the addresses in the running configuration.
- Configure the switch ports so that, if the maximum number of addresses for each port is exceeded, packets with unknown source addresses are dropped until a sufficient number of secure MAC addresses are removed. Notification that a violation has occurred is not required.
Step 8: Dynamic Routing
Configure RIPv2 routing on HQ and Branch.
- Configure RIPv2 on HQ and Branch so that all networks are reachable.
- Configure all LAN physical interfaces so that RIP updates are not sent out to the LANs.
- Be sure to use the version of RIP that supports classless routing.
- Prevent RIP from automatically summarizing networks.
- Configure RIP to automatically send the default route that is already configured on Branchto HQ.
Step 9: Configure Network Monitoring
Configure NTP and Syslog server logging on HQ.
- Activate the logging and debug timestamp services.
- Configure HQas an NTP client. The NTP server is Admin with the address of 192.168.2.10.
- Configure Syslog to send debug levelmessages to the Admin logging server.
Step 10: Configure Host Addressing
Address the hosts that are connected to SW-Bldg-A-1 so that they have connectivity to the IP address of the Web server on the Web. Use the information provided in the Addressing Table.
Intructions- Answers Script - Type B
HQ - Router
enable configure terminal no ip domain-lookup hostname HQ service password-encryption enable secret class banner motd $users that unauthorized access is prohibited$ line console 0 logging synchronous password cisco login exit ip domain-name cisco.com username admin password class crypto key generate rsa yes 1024 ip ssh version 2 line vty 0 15 transport input ssh login local exit interface gigabitEthernet 0/1 ip address 192.168.2.1 255.255.255.0 no shutdown description Branch-1 int s0/0/0 ip address 10.1.1.1 255.255.255.252 no shutdown description Connection-to-Branch exit interface g0/0.5 encapsulation dot1Q 5 ip address 192.168.1.1 255.255.255.240 interface g0/0.10 encapsulation dot1Q 10 ip address 192.168.1.17 255.255.255.240 interface g0/0.15 encapsulation dot1Q 15 ip address 192.168.1.33 255.255.255.240 interface g0/0.50 encapsulation dot1Q 50 ip address 192.168.1.49 255.255.255.240 exit int g0/0 no sh no shutdown exit ip access-list standard block15 deny 192.168.1.32 0.0.0.15 permit any line vty 0 4 access-class block15 in int g0/0.10 ip access-group block15 out exit Router rip version 2 network 10.1.1.0 network 192.168.1.0 network 192.168.1.16 network 192.168.1.32 network 192.168.1.48 network 192.168.2.0 no auto-summary passive-interface g0/0.5 passive-interface g0/0.10 passive-interface g0/0.15 passive-interface g0/0.50 passive-interface g0/0 passive-interface g0/1 exit service timestamps log datetime msec service timestamps debug datetime msec ntp server 192.168.2.10 logging 192.168.2.10 logging trap debugging ntp update-calendar
Branch - Router
en conf ter router rip version 2 network 10.1.1.0 network 192.168.3.0 default-information originate no auto-summary passive-interface s0/0/1 passive-interface g0/0
SW-Bldg-A (Switch)
enable configure terminal vlan 5 name OFFICE vlan 10 name ACCT vlan 15 name PROD vlan 50 name ADMIN exit interface f0/23 switchport mode trunk interface f0/24 switchport mode trunk interface g0/1 switchport mode trunk exit int vlan 50 ip address 192.168.1.50 255.255.255.240 no shutdown exit ip default-gateway 192.168.1.49
SW-Bldg-A-1
enable configure terminal vlan 5 name OFFICE vlan 10 name ACCT vlan 15 name PROD vlan 50 name ADMIN exit int f0/23 switchport mode trunk int f0/5 switchport mode access switchport access vlan 5 switchport port-security switchport port-security maximum 2 switchport port-security mac-address sticky switchport port-security violation protect int f0/10 switchport mode access switchport access vlan 10 switchport port-security switchport port-security maximum 2 switchport port-security mac-address sticky switchport port-security violation protect switchport port-security mac-address sticky 0001.C933.4067 int f0/15 switchport mode access switchport access vlan 15 switchport port-security switchport port-security maximum 2 switchport port-security mac-address sticky switchport port-security violation protect switchport port-security mac-address sticky 0090.211A.8676 int f0/20 switchport mode access switchport access vlan 50 switchport port-security switchport port-security maximum 2 switchport port-security mac-address sticky switchport port-security violation protect switchport port-security mac-address sticky 0001.C70C.EC63 exit int vlan 50 ip address 192.168.1.51 255.255.255.240 no shutdown exit ip default-gateway 192.168.1.49 int range f0/1-4 shutdown int range f0/6-9 shutdown int range f0/11-14 shutdown int range f0/16-19 shutdown int range f0/21-22 shutdown int f0/24 shutdown int range g0/1-2 shutdown
SW-Bldg-A-2
enable configure terminal vlan 5 name OFFICE vlan 10 name ACCT vlan 15 name PROD vlan 50 name ADMIN exit int f0/24 switchport mode trunk exit interface f0/5 switchport mode access switchport access vlan 5 interface f0/10 switchport mode access switchport access vlan 10 interface f0/15 switchport mode access switchport access vlan 15 interface f0/20 switchport mode access switchport access vlan 50 int vlan 50 ip add 192.168.1.52 255.255.255.240 no sh exit ip default-gateway 192.168.1.49 interface FastEthernet0/24 switchport mode trunk
Host Addressing
| Hosts | OFFICE 1 | PROD-1 | ACCT 1 | ADMIN-1 |
| IP Address | 192.168.1.10 | 192.168.1.26 | 192.168.1.42 | 192.168.1.58 |
| Subnet mask | 255.255.255.240 | 255.255.255.240 | 255.255.255.240 | 255.255.255.240 |
| Default gateway | 192.168.1.1 | 192.168.1.17 | 192.168.1.33 | 192.168.1.49 |
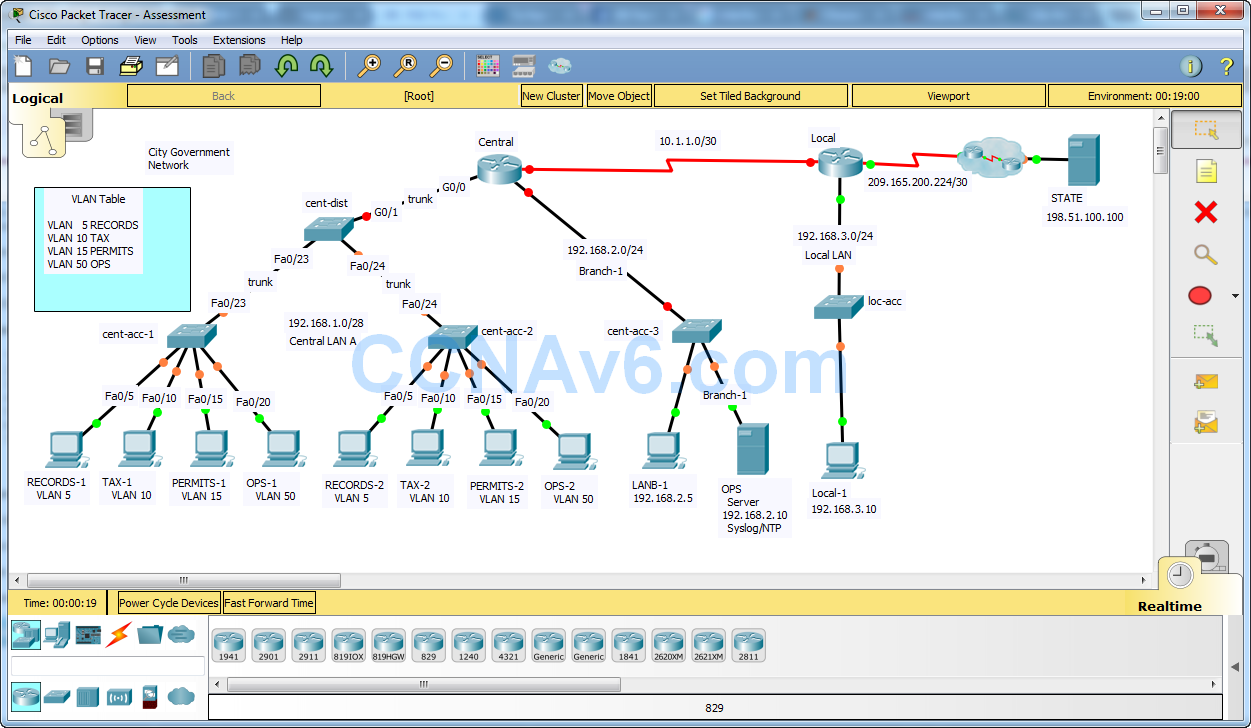
Intructions- Answers Script - Type C
Central - Router
enable configure terminal no ip domain-lookup hostname Central service password-encryption enable secret class banner motd $users that unauthorized access is prohibited$ line console 0 logging synchronous password cisco login exit ip domain-name cisco.com username admin password class crypto key generate rsa yes 1024 ip ssh version 2 line vty 0 15 transport input ssh login local exit interface gigabitEthernet 0/1 ip address 192.168.2.1 255.255.255.0 no shutdown description Local-1 int s0/0/0 ip address 10.1.1.1 255.255.255.252 no shutdown description Connection-to-Local exit interface g0/0.5 encapsulation dot1Q 5 ip address 192.168.1.1 255.255.255.240 interface g0/0.10 encapsulation dot1Q 10 ip address 192.168.1.17 255.255.255.240 interface g0/0.15 encapsulation dot1Q 15 ip address 192.168.1.33 255.255.255.240 interface g0/0.50 encapsulation dot1Q 50 ip address 192.168.1.49 255.255.255.240 exit int g0/0 no sh no shutdown exit ip access-list standard block15 deny 192.168.1.32 0.0.0.15 permit any line vty 0 4 access-class block15 in int g0/0.10 ip access-group block15 out exit Router rip version 2 network 10.1.1.0 network 192.168.1.0 network 192.168.1.16 network 192.168.1.32 network 192.168.1.48 network 192.168.2.0 no auto-summary passive-interface g0/0.5 passive-interface g0/0.10 passive-interface g0/0.15 passive-interface g0/0.50 passive-interface g0/0 passive-interface g0/1 exit service timestamps log datetime msec service timestamps debug datetime msec ntp server 192.168.2.10 logging 192.168.2.10 logging trap debugging ntp update-calendar
Local - Router
en conf ter router rip version 2 network 10.1.1.0 network 192.168.3.0 default-information originate no auto-summary passive-interface s0/0/1 passive-interface g0/0
cent-dist (Switch)
enable configure terminal vlan 5 name RECORDS vlan 10 name TAX vlan 15 name PERMITS vlan 50 name OPS exit interface f0/23 switchport mode trunk interface f0/24 switchport mode trunk interface g0/1 switchport mode trunk exit int vlan 50 ip address 192.168.1.50 255.255.255.240 no shutdown exit ip default-gateway 192.168.1.49
cent-acc-1
enable configure terminal vlan 5 name RECORDS vlan 10 name TAX vlan 15 name PERMITS vlan 50 name OPS exit int f0/23 switchport mode trunk int f0/5 switchport mode access switchport access vlan 5 switchport port-security switchport port-security maximum 2 switchport port-security mac-address sticky switchport port-security violation protect int f0/10 switchport mode access switchport access vlan 10 switchport port-security switchport port-security maximum 2 switchport port-security mac-address sticky switchport port-security violation protect switchport port-security mac-address sticky 0001.C933.4067 int f0/15 switchport mode access switchport access vlan 15 switchport port-security switchport port-security maximum 2 switchport port-security mac-address sticky switchport port-security violation protect switchport port-security mac-address sticky 0090.211A.8676 int f0/20 switchport mode access switchport access vlan 50 switchport port-security switchport port-security maximum 2 switchport port-security mac-address sticky switchport port-security violation protect switchport port-security mac-address sticky 0001.C70C.EC63 exit int vlan 50 ip address 192.168.1.51 255.255.255.240 no shutdown exit ip default-gateway 192.168.1.49 int range f0/1-4 shutdown int range f0/6-9 shutdown int range f0/11-14 shutdown int range f0/16-19 shutdown int range f0/21-22 shutdown int f0/24 shutdown int range g0/1-2 shutdown
cent-acc-2
enable configure terminal vlan 5 name RECORDS vlan 10 name TAX vlan 15 name PERMITS vlan 50 name OPS exit int f0/24 switchport mode trunk exit interface f0/5 switchport mode access switchport access vlan 5 interface f0/10 switchport mode access switchport access vlan 10 interface f0/15 switchport mode access switchport access vlan 15 interface f0/20 switchport mode access switchport access vlan 50 int vlan 50 ip add 192.168.1.52 255.255.255.240 no sh exit ip default-gateway 192.168.1.49 interface FastEthernet0/24 switchport mode trunk
Host Addressing
| Hosts | RECORDS-1 | TAX-1 | PERMITS-1 | OPS-1 |
| IP Address | 192.168.1.10 | 192.168.1.26 | 192.168.1.42 | 192.168.1.58 |
| Subnet mask | 255.255.255.240 | 255.255.255.240 | 255.255.255.240 | 255.255.255.240 |
| Default gateway | 192.168.1.1 | 192.168.1.17 | 192.168.1.33 | 192.168.1.49 |
Download Packet Tracer .PKA file:


For type c on central router it say description Local-1. But shouldn’t say description Branch-1.
Also the description connection to local-1. It should say description connection to Branch-1
You might need to check your type c answer for central router
Got 90 % thanks!
THANK YOU SO MUCH!!!!!! 100% SCORE TESTED!
thankyou so much!!!! IT HELPED A LOT
thank you so much!!!!
shouldn’t we fill out IP addresses for the second network (RECORDS-2, TAX-2, PERMITS-2, OPS-2)?
thanks was helpful
Thanks a lot !
Thank you MASTER !!!
many thanks
pitty there is no text, Introduction
and ip-table
pity you can’t spell pity correctly lmao
Thanks :)
thank you this helped me with my mbo
Thank you