1. Which two characteristics are associated with UDP sessions? (Choose two.)
- Destination devices receive traffic with minimal delay.
- Transmitted data segments are tracked.
- Destination devices reassemble messages and pass them to an application.
- Received data is unacknowledged.
- Unacknowledged data packets are retransmitted.
2. What happens if part of an FTP message is not delivered to the destination?
- The message is lost because FTP does not use a reliable delivery method.
- The FTP source host sends a query to the destination host.
- The part of the FTP message that was lost is re-sent.
- The entire FTP message is re-sent.
3. A host device needs to send a large video file across the network while providing data communication to other users. Which feature will allow different communication streams to occur at the same time, without having a single data stream using all available bandwidth?
- window size
- multiplexing
- port numbers
- acknowledgments
4. What kind of port must be requested from IANA in order to be used with a specific application?
- registered port
- private port
- dynamic port
- source port
5. What type of information is included in the transport header?
- destination and source logical addresses
- destination and source physical addresses
- destination and source port numbers
- encoded application data
6. What is a socket?
- the combination of the source and destination IP address and source and destination Ethernet address
- the combination of a source IP address and port number or a destination IP address and port number
- the combination of the source and destination sequence and acknowledgment numbers
- the combination of the source and destination sequence numbers and port numbers
7. What is the complete range of TCP and UDP well-known ports?
- 0 to 255
- 0 to 1023
- 256 – 1023
- 1024 – 49151
8. Which flag in the TCP header is used in response to a received FIN in order to terminate connectivity between two network devices?
- FIN
- ACK
- SYN
- RST
9. What is a characteristic of a TCP server process?
- Every application process running on the server has to be configured to use a dynamic port number.
- There can be many ports open simultaneously on a server, one for each active server application.
- An individual server can have two services assigned to the same port number within the same transport layer services.
- A host running two different applications can have both configured to use the same server port.
10. Which two flags in the TCP header are used in a TCP three-way handshake to establish connectivity between two network devices? (Choose two.)
- ACK
- FIN
- PSH
- RST
- SYN
- URG
11. A PC is downloading a large file from a server. The TCP window is 1000 bytes. The server is sending the file using 100-byte segments. How many segments will the server send before it requires an acknowledgment from the PC?
- 1 segment
- 10 segments
- 100 segments
- 1000 segments
12. Which factor determines TCP window size?
- the amount of data to be transmitted
- the number of services included in the TCP segment
- the amount of data the destination can process at one time
- the amount of data the source is capable of sending at one time
13. During a TCP session, a destination device sends an acknowledgment number to the source device. What does the acknowledgment number represent?
- the total number of bytes that have been received
- one number more than the sequence number
- the next byte that the destination expects to receive
- the last sequence number that was sent by the source
14. What information is used by TCP to reassemble and reorder received segments?
- port numbers
- sequence numbers
- acknowledgment numbers
- fragment numbers
15. What does TCP do if the sending source detects network congestion on the path to the destination?
- The source host will send a request for more frequent acknowledgments to the destination.
- The source will decrease the amount of data that it sends before it must receive acknowledgements from the destination.
- The destination will request retransmission of the entire message.
- The source will acknowledge the last segment that is sent and include a request for a smaller window size in the message.
16. What is a characteristic of UDP?
- UDP datagrams take the same path and arrive in the correct order at the destination.
- Applications that use UDP are always considered unreliable.
- UDP reassembles the received datagrams in the order they were received.
- UDP only passes data to the network when the destination is ready to receive the data.
17. What does a client do when it has UDP datagrams to send?
- It just sends the datagrams.
- It queries the server to see if it is ready to receive data.
- It sends a simplified three-way handshake to the server.
- It sends to the server a segment with the SYN flag set to synchronize the conversation.
18. What happens if the first packet of a TFTP transfer is lost?
- The client will wait indefinitely for the reply.
- The TFTP application will retry the request if a reply is not received.
- The next-hop router or the default gateway will provide a reply with an error code.
- The transport layer will retry the query if a reply is not received.
19. A host device is receiving live streaming video. How does the device account for video data that is lost during transmission?
- The device will immediately request a retransmission of the missing data.
- The device will use sequence numbers to pause the video stream until the correct data arrives.
- The device will delay the streaming video until the entire video stream is received.
- The device will continue receiving the streaming video, but there may be a momentary disruption.
20. Why does HTTP use TCP as the transport layer protocol?
- to ensure the fastest possible download speed
- because HTTP is a best-effort protocol
- because transmission errors can be tolerated easily
- because HTTP requires reliable delivery
21. When is UDP preferred to TCP?
- when a client sends a segment to a server
- when all the data must be fully received before any part of it is considered useful
- when an application can tolerate some loss of data during transmission
- when segments must arrive in a very specific sequence to be processed successfully
22. Which three application layer protocols use TCP? (Choose three.)
- SMTP
- FTP
- SNMP
- HTTP
- TFTP
- DHCP
23. Refer to the exhibit. Consider a datagram that originates on the PC and that is destined for the web server. Match the IP addresses and port numbers that are in that datagram to the description. (Not all options are used.)
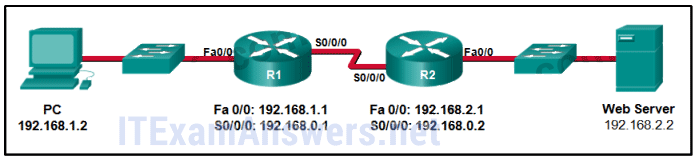
destination IP address -> 192.168.2.2
destination port number -> 80
source IP address -> 192.168.1.2
source port number -> 2578
24. What information is used by TCP to reassemble and reorder received segments?
- sequence numbers
- acknowledgment numbers
- fragment numbers
- port numbers
Older Version
25. Refer to the exhibit. How many broadcast domains are there?
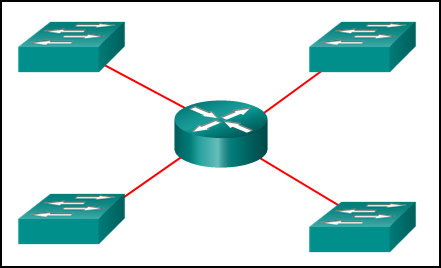
- 1
- 2
- 3
- 4
26. How many usable host addresses are there in the subnet 192.168.1.32/27?
- 32
- 30
- 64
- 16
- 62
27. How many host addresses are available on the network 172.16.128.0 with a subnet mask of 255.255.252.0?
- 510
- 512
- 1022
- 1024
- 2046
- 2048
28. A network administrator is variably subnetting a network. The smallest subnet has a mask of 255.255.255.248. How many host addresses will this subnet provide?
- 4
- 6
- 8
- 10
- 12
29. Refer to the exhibit. A company uses the address block of 128.107.0.0/16 for its network. What subnet mask would provide the maximum number of equal size subnets while providing enough host addresses for each subnet in the exhibit?
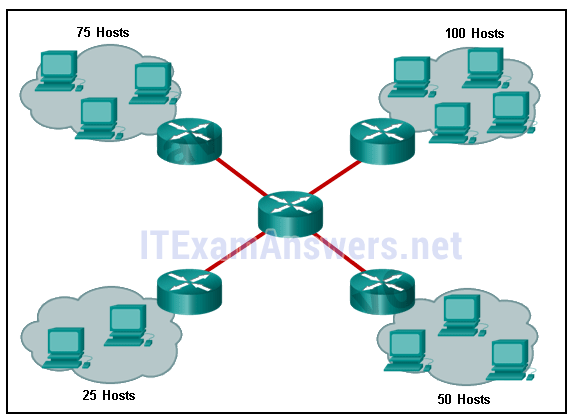
- 255.255.255.0
- 255.255.255.128
- 255.255.255.192
- 255.255.255.224
- 255.255.255.240
30. Refer to the exhibit. The network administrator has assigned the LAN of LBMISS an address range of 192.168.10.0. This address range has been subnetted using a /29 prefix. In order to accommodate a new building, the technician has decided to use the fifth subnet for configuring the new network (subnet zero is the first subnet). By company policies, the router interface is always assigned the first usable host address and the workgroup server is given the last usable host address. Which configuration should be entered into the properties of the workgroup server to allow connectivity to the Internet?
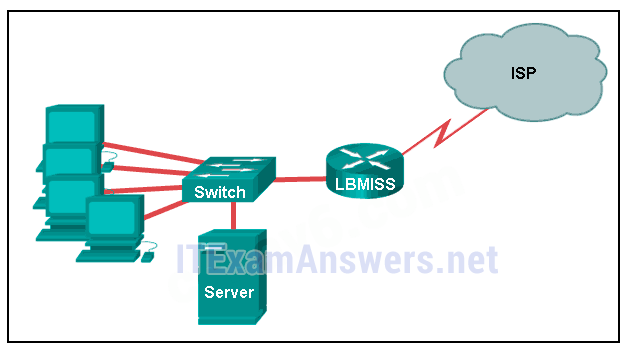
- IP address: 192.168.10.65 subnet mask: 255.255.255.240, default gateway: 192.168.10.76
- IP address: 192.168.10.38 subnet mask: 255.255.255.240, default gateway: 192.168.10.33
- IP address: 192.168.10.38 subnet mask: 255.255.255.248, default gateway: 192.168.10.33
- IP address: 192.168.10.41 subnet mask: 255.255.255.248, default gateway: 192.168.10.46
- IP address: 192.168.10.254 subnet mask: 255.255.255.0, default gateway: 192.168.10.1
31. How many bits must be borrowed from the host portion of an address to accommodate a router with five connected networks?
- two
- three
- four
- five
32. A company has a network address of 192.168.1.64 with a subnet mask of 255.255.255.192. The company wants to create two subnetworks that would contain 10 hosts and 18 hosts respectively. Which two networks would achieve that? (Choose two.)
- 192.168.1.16/28
- 192.168.1.64/27
- 192.168.1.128/27
- 192.168.1.96/28
- 192.168.1.192/28
33. In a network that uses IPv4, what prefix would best fit a subnet containing 100 hosts?
- /23
- /24
- /25
- /26
34. Refer to the exhibit.
Given the network address of 192.168.5.0 and a subnet mask of 255.255.255.224, how many total host addresses are unused in the assigned subnets?
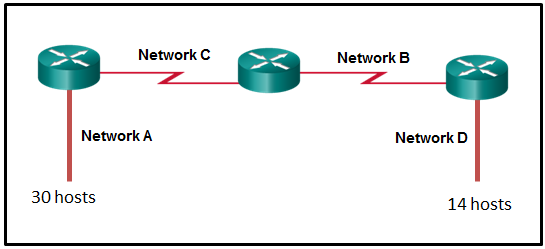
- 56
- 60
- 64
- 68
- 72
35. When developing an IP addressing scheme for an enterprise network, which devices are recommended to be grouped into their own subnet or logical addressing group?
- end-user clients
- workstation clients
- mobile and laptop hosts
- hosts accessible from the Internet
36. A network administrator needs to monitor network traffic to and from servers in a data center. Which features of an IP addressing scheme should be applied to these devices?
- random static addresses to improve security
- addresses from different subnets for redundancy
- predictable static IP addresses for easier identification
- dynamic addresses to reduce the probability of duplicate addresses
37. Which two reasons generally make DHCP the preferred method of assigning IP addresses to hosts on large networks? (Choose two.)
- It eliminates most address configuration errors.
- It ensures that addresses are only applied to devices that require a permanent address.
- It guarantees that every device that needs an address will get one.
- It provides an address only to devices that are authorized to be connected to the network.
- It reduces the burden on network support staff.
38. Refer to the exhibit. A computer that is configured with the IPv6 address as shown in the exhibit is unable to access the internet. What is the problem?
- The DNS address is wrong.
- There should not be an alternative DNS address.
- The gateway address is in the wrong subnet.
- The settings were not validated.
39. When subnetting a /64 IPv6 network prefix, which is the preferred new prefix length?
- /66
- /70
- /72
- /74
40. What is the subnet address for the address 2001:DB8:BC15:A:12AB::1/64?
- 2001:DB8:BC15::0
- 2001:DB8:BC15:A::0
- 2001:DB8:BC15:A:1::1
- 2001:DB8:BC15:A:12::0
41. Which two notations are useable nibble boundaries when subnetting in IPv6? (Choose two.)
- /62
- /64
- /66
- /68
- /70
42. Fill in the blank.
In dotted decimal notation, the IP address 172.25.0.126 is the last host address for the network 172.25.0.64/26.
43. Fill in the blank.
In dotted decimal notation, the subnet mask 255.255.254.0 will accommodate 500 hosts per subnet.
Consider the following range of addresses:
2001:0DB8:BC15:00A0:0000::
2001:0DB8:BC15:00A1:0000::
2001:0DB8:BC15:00A2:0000::
…
2001:0DB8:BC15:00AF:0000::
The prefix-length for the range of addresses is /60
44. Fill in the blank.
A nibble consists of 4 bits.
45. Open the PT Activity. Perform the tasks in the activity instructions and then answer the question. What issue is causing Host A to be unable to communicate with Host B?
- The subnet mask of host A is incorrect.
- Host A has an incorrect default gateway.
- Host A and host B are on overlapping subnets.
- The IP address of host B is not in the same subnet as the default gateway is on.
46. Refer to the exhibit. Given the network address of 192.168.5.0 and a subnet mask of 255.255.255.224, how many addresses are wasted in total by subnetting each network with a subnet mask of 255.255.255.224?
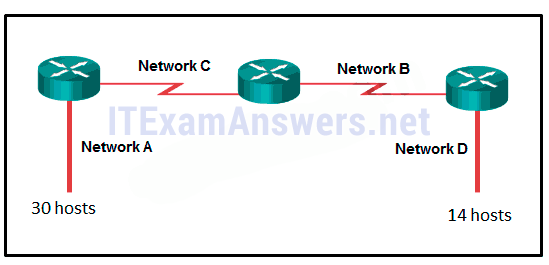
- 56
- 60
- 64
- 68
- 72
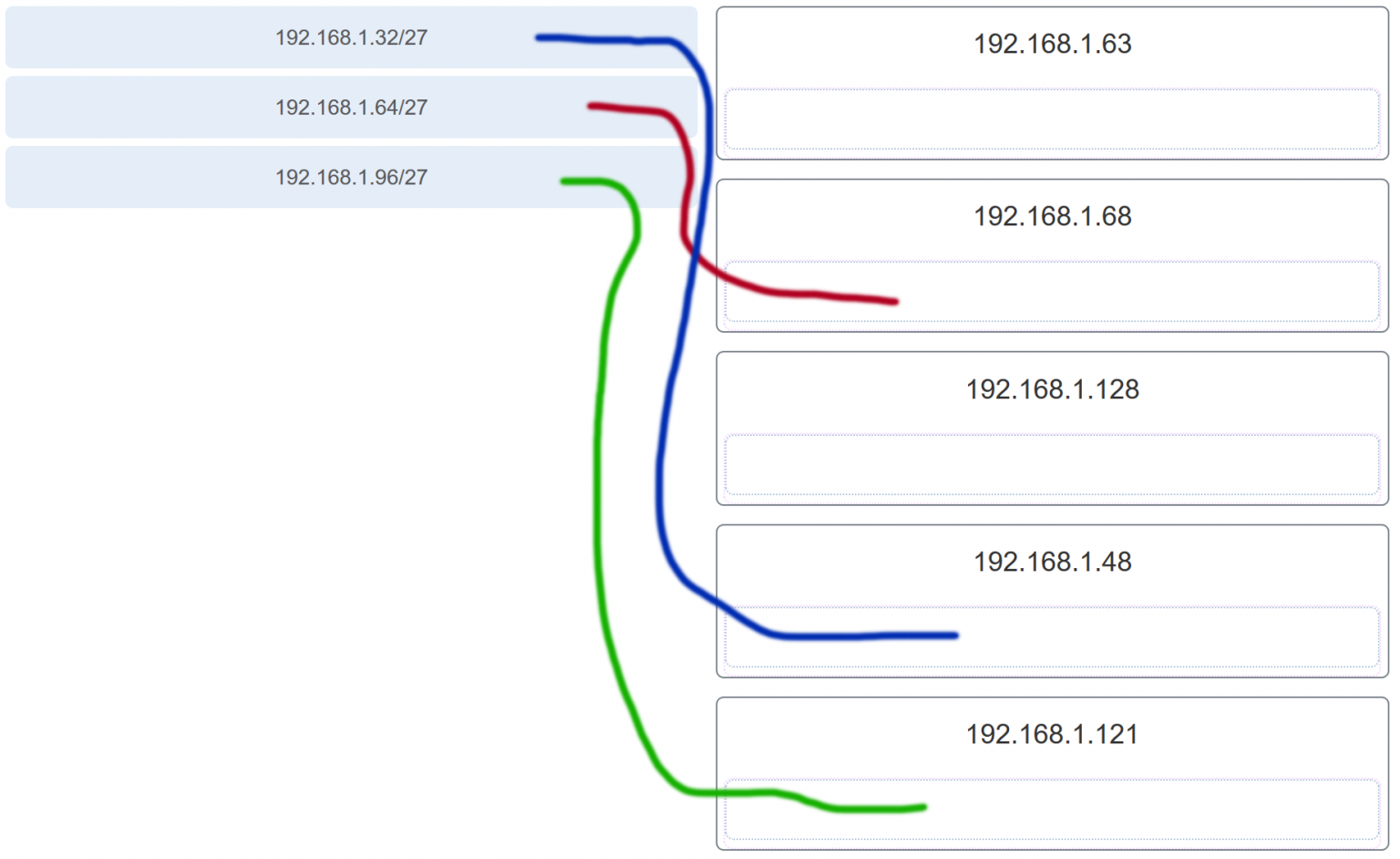
47. Match the subnetwork to a host address that would be included within the subnetwork. (Not all options are used.)
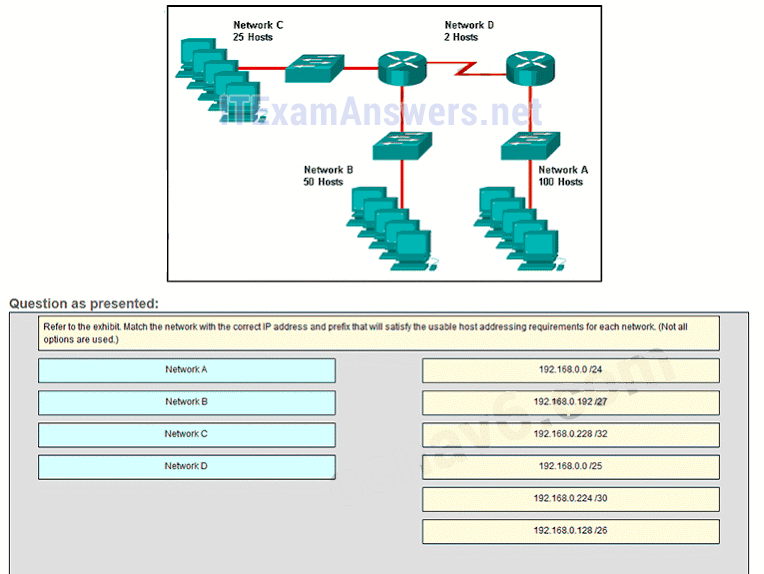
48. Refer to the exhibit. Match the network with the correct IP address and prefix that will satisfy the usable host addressing requirements for each network. (Not all options are used.)
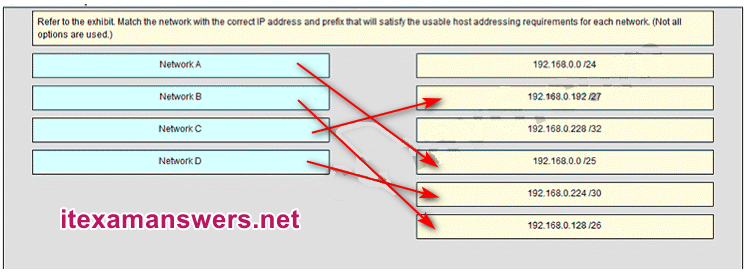
Place the options in the following order:
– not scored –
Network C
– not scored –
Network A
Network D
Network B
49. Which three features can be configured in the BIOS settings to secure a computer? (Choose three.)
- MAC filtering
- drive encryption
- TPM
- file encryption
- TKIP key
- passwords
50. Refer to the exhibit. A network administrator has configured OSPFv2 on the two Cisco routers. The routers are unable to form a neighbor adjacency. What should be done to fix the problem on router R2?
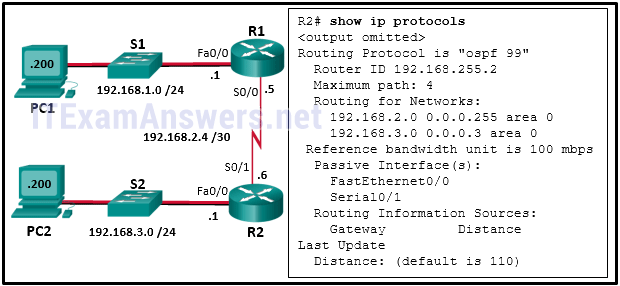
- Implement the command no passive-interface Serial0/1.
- Implement the command network 192.168.2.6 0.0.0.0 area 0 on router R2.
- Change the router-id of router R2 to 2.2.2.2.
- Implement the command network 192.168.3.1 0.0.0.0 area 0 on router R2.

Which three features can be configured in the BIOS settings to secure a computer? (Choose three.)
MAC filtering
passwords
drive encryption
TKIP key
file encryption
TPM
Quais duas flags no cabeçalho TCP são usadas em um handshake triplo de TCP para estabelecer conectividade entre dois dispositivos de rede? (Escolha duas.)
FIN
ACK
URG
SYN
PSH
RST
23The graphic displays the following:Router R1 is connected to switch S1 and has the IP address 192.168.1.1 on interface Fa0/0. Switch S1 is connected to PC1 and PC1 has the IP address 192.168.1.200 /24. The network shown below switch S1 is 192.168.1.0 /24.Router R1 S0/0 has IP address 192.168.2.5 /30 and is connected to router R2 on interface S0/1 with IP address 192.168.2.6 /30. The network shown between router R1 and R2 is 192.168.2.4 /30.Router R2 is connected to switch S2 and has the IP address 192.168.3.1 on interface Fa0/0. Switch S2 is connected to PC2 and PC2 has the IP address 192.168.3.200.
The network shown below switch S2 is 192.168.3.0 /24.In addition to the topology is some partial router command
output:R2# show ip protocols
Routing Protocol is “ospf 99”
Router ID 192.168.255.2
Maximum path: 4
Routing for Networks:
192.168.2.0 0.0.0.255 area 0
192.168.3.0 0.0.0.3 area 0
Reference bandwidth unit is 100 mbps
Passive Interface(s):
FastEthernet0/0
Serial0/1
Routing Information Sources:
Gateway Distance
Last Update Distance: (default is 110)
Q. Refer to the exhibit. A network administrator has configured OSPFv2
on the two Cisco routers. The routers are unable to form a neighbor
adjacency. What should be done to fix the problem on router R2?
1)Change the router-id of router R2 to 2.2.2.2.
2)Implement the command network 192.168.3.1 0.0.0.0 area 0 on router R2.
3)Implement the command network 192.168.2.6 0.0.0.0 area 0 on router R2.
4) Implement the command no passive-interface Serial0/1.
what information is used by TCP to reassemble and reorder received segments?
sequence numbers
acknowledgment numbers
fragment numbers
port numbers
Google it
sequence numbers*
godislovegodislove
thanks
GOOD JOB…….VERY HELPFUL
router has interfaces connected to multiple OSPF areas?
Muchas gracias. Me ayudó bastante.
wow, thanks a lot… your site is just full of information. you’re doing a great job… keep it up.. I always give you a return to your hard work on every visit when I feel the need of your website.
the CISCO certificate is so useful for the placements drive