CCNA Routing and Switching
Connecting Networks
Skill-Based Assessment – Packet Tracer
A few things to keep in mind while completing this activity:
- Do not use the browser Back button or close or reload any Exam windows during the exam.
- Do not close Packet Tracer when you are done. It will close automatically.
- Click the Submit Assessment button to submit your work.
Objectives
In this Packet Tracer Skills Based Assessment, you will do as follows:
- Configure PPP encapsulation and CHAP authentication for serial links.
- Configure a GRE tunnel.
- Configure OSPF.
- Configure BGP.
- Configure standard and extended IPv4 ACLs.
- Configure IPv6 ACLs.
For the sake of time, many repetitive, but important, configuration tasks have been omitted from this assessment. Many of these tasks, especially those related to security, are essential elements of a network configuration. The intent of this activity is not to diminish the importance of full device configurations.
The IP addresses for all the devices have been configured and some of the routing configurations are already completed in this activity.
You are required to configure the devices as follows:
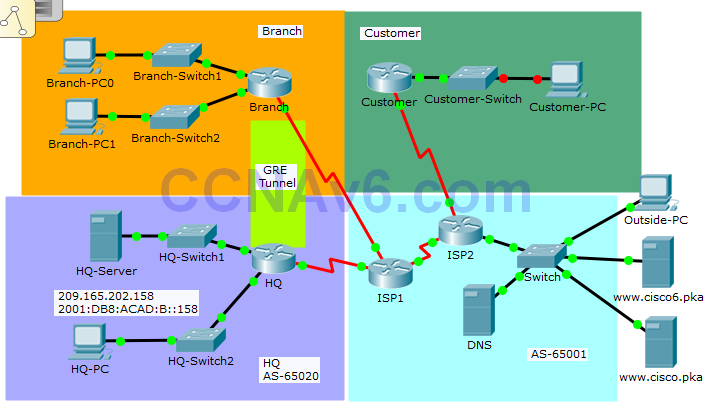
Branch:
- Configure PPP and CHAP authentication on the appropriate interface.
- Configure GRE tunnel.
- Configure OSPF.
- Configure standard IPv4 ACL.
Customer:
- Configure standard IPv4 ACLs.
HQ:
- Configure PPP and CHAP authentication on the appropriate interface.
- Configure GRE tunnel.
- Configure OSPF.
- Configure standard and extended IPv4 ACLs.
- Configure IPv6 ACLs.
Note: All the routers in AS 65001 are locked and no configurations are performed by the students. Furthermore, all the switches are pre-configured.
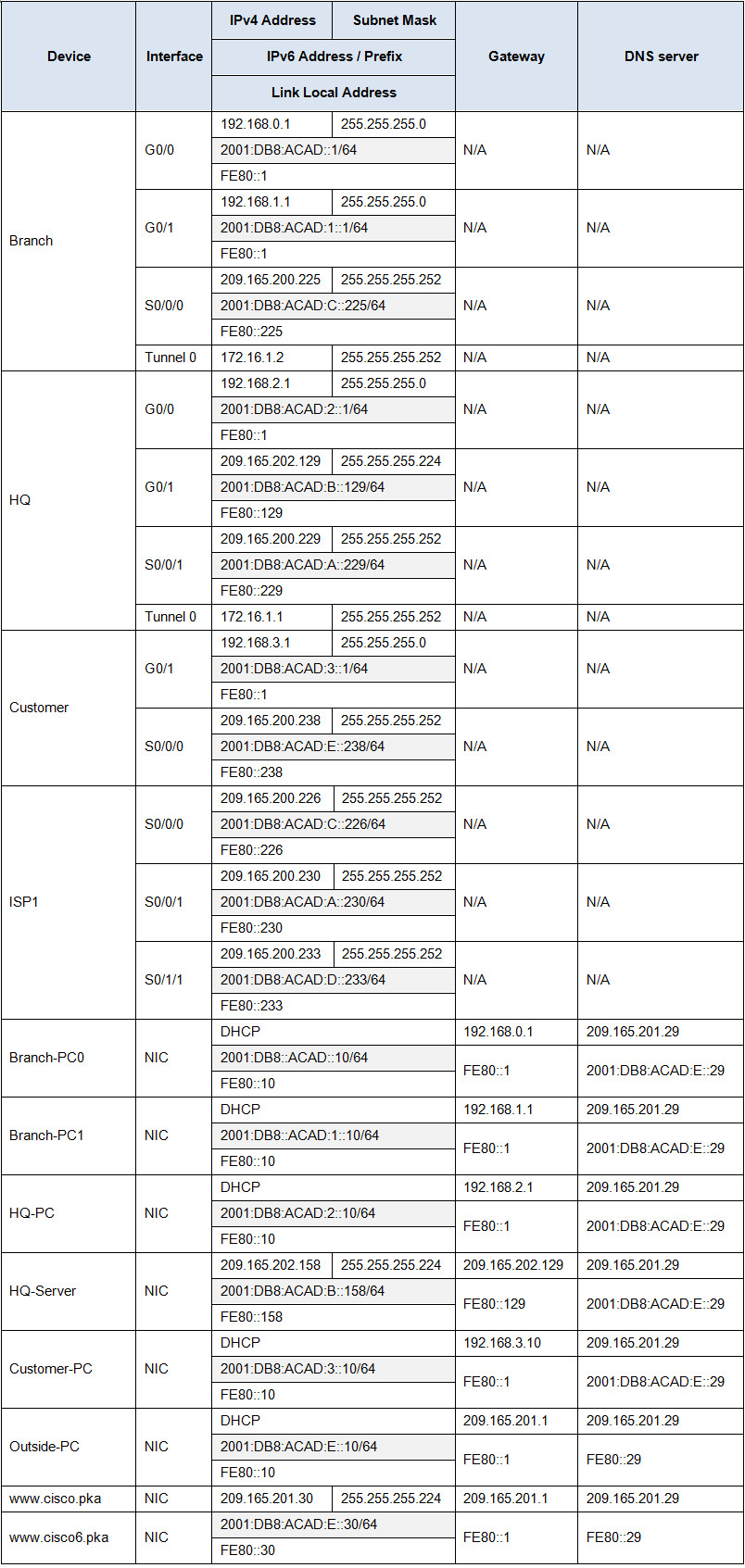
Addressing Table
Instructions
Step 1: Configure PPP encapsulation and authentication.
a. Configure PPP encapsulation for the link between HQ and ISP1 and the link between Branch and ISP1.
b. Configure CHAP authentication between the links.
c. Configure the correct username and the password cisco123 for CHAP authentication on both HQ and Branch.
Step 2: Configure a GRE tunnel with routing.
a. Configure a GRE tunnel between HQ and Branch.
b. Configure OSPF 1 to route the traffic between the LANs of HQ and Branch through the GRE tunnel. Summarize the networks attached to Branch.
Step 3: Configure BGP.
Configure BGP between ISP1 in Internet cluster and 209.165.202.128/27 network on HQ.
a. Use AS number 65020 for HQ.
b. Configure ISP1 as the BGP neighbor.
c. Only advertise the 209.165.202.128 / 27 network into BGP.
Step 4: Configure ACLs for NAT.
a. Configure a standard access list numbered 1 on Branch to allow NAT for hosts in network 192.168.0.0 /23.
b. Configure a standard access list numbered 1 on HQ to allow NAT for hosts in network 192.168.2.0 /24.
c. Configure a standard access list numbered 1 on Customer to allow NAT for hosts in network 192.168.3.0 /24.
Step 5: Configure a standard ACL to restrict remote access to the Customer router.
A standard ACL named VTY_ADMIN is configured to limit access via VTY to the Customer router. This ACL will only allow hosts from the LAN attached to the G0/1 interface and the hosts from the LANs on Branch router to access the Customer router. All the other connections to VTY should fail.
a. Configure one ACL named VTY_ADMIN with three ACEs in the following order:
1) Allow any hosts from the LAN attached to the G0/1 interface of Customer router to access the router.
2) Allow the hosts from the LANs in the Branch network to Customer router remotely.
3) All other remote connections are denied.
b. Apply the ACL to the appropriate interface.
Note: Use the public IPv4 addresses in the ACLs when the private IPv4 addresses have been mapped to public IPv4 addresses.
Step 6: Configure an extended ACL to restrict access to the HQ LAN.
a. Configure an extended ACL named HTTP_ACCESS that allows Branch LANs, Customer LANs and the LAN inside HQ to access HQ-Server via the web browser.
Configure this ACL with the following 5 ACEs in the following order:
1) Allow the hosts from the Branch network to access the HQ-Server.
2) Allow the hosts from the Customer LANs to access the HQ-Server.
3) Allow the internal network 192.168.2.0 /24 to access the HQ-Server.
4) Allow ICMP replies to HQ-Server from any networks.
5) Explicitly deny all other traffic from accessing the HQ-Server.
b. Apply the ACL to the HQ G0/1 interface.
Note: Use the public IPv4 addresses in the ACLs when the private IPv4 addresses have been mapped to public IPv4 addresses.
Step 7: Configure an IPv6 access list to restrict access to the HQ LAN.
a. Configure an IPv6 access list named HTTP6_ACCESS that allows Branch LANs, Customer LANs and the LAN inside HQ to access HQ-Server via the web browser.
b. Configure this ACL with the following 6 ACEs in the following order:
1) Allow the hosts from the Branch (2001:DB8:ACAD::/64) to access the HQ-Server.
2) Allow the hosts from the Branch (2001:DB8:ACAD:1::/64) to access the HQ-Server.
3) Allow the hosts from the Customer LANs to access the HQ-Server.
4) Allow the internal network 2001:DB8:ACAD:2::/64 to access the HQ-Server.
5) Allow ICMP from HQ-Server to the other networks.
6) Explicitly deny all other traffic from accessing the HQ-Server.
c. Apply the ACL to the HQ G0/1 interface.
A few things to keep in mind while completing this activity:
- Do not use the browser Back button or close or reload any Exam windows during the exam.
- Do not close Packet Tracer when you are done. It will close automatically.
- Click the Submit Assessment button to submit your work.
Objectives
In this Packet Tracer Skills Based Assessment, you will do as follows:
- Configure PPP encapsulation and CHAP authentication for serial links.
- Configure a GRE tunnel.
- Configure OSPF.
- Configure BGP.
- Configure standard and extended IPv4 ACLs.
- Configure IPv6 ACLs.
For the sake of time, many repetitive, but important, configuration tasks have been omitted from this assessment. Many of these tasks, especially those related to security, are essential elements of a network configuration. The intent of this activity is not to diminish the importance of full device configurations.
The IP addresses for all the devices have been configured and some of the routing configurations are already completed in this activity.
You are required to configure the devices as follows:
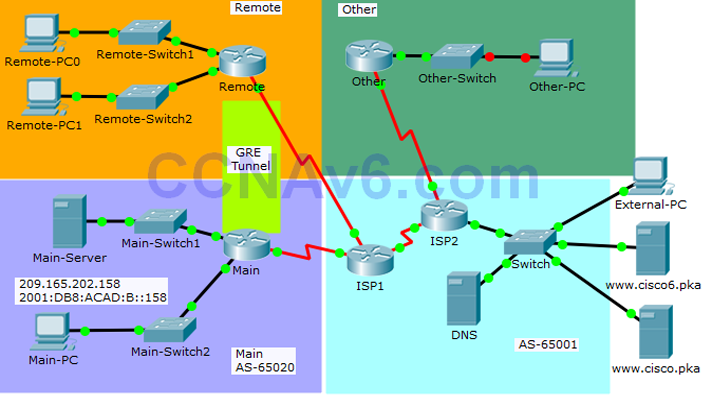
Remote:
- Configure PPP and CHAP authentication on the appropriate interface.
- Configure GRE tunnel.
- Configure OSPF.
- Configure standard IPv4 ACL.
Other:
- Configure standard IPv4 ACLs.
Main:
- Configure PPP and CHAP authentication on the appropriate interface.
- Configure GRE tunnel.
- Configure OSPF.
- Configure standard and extended IPv4 ACLs.
- Configure IPv6 ACLs.
Note: All the routers in AS 65001 are locked and no configurations are performed by the students. Furthermore, all the switches are pre-configured.
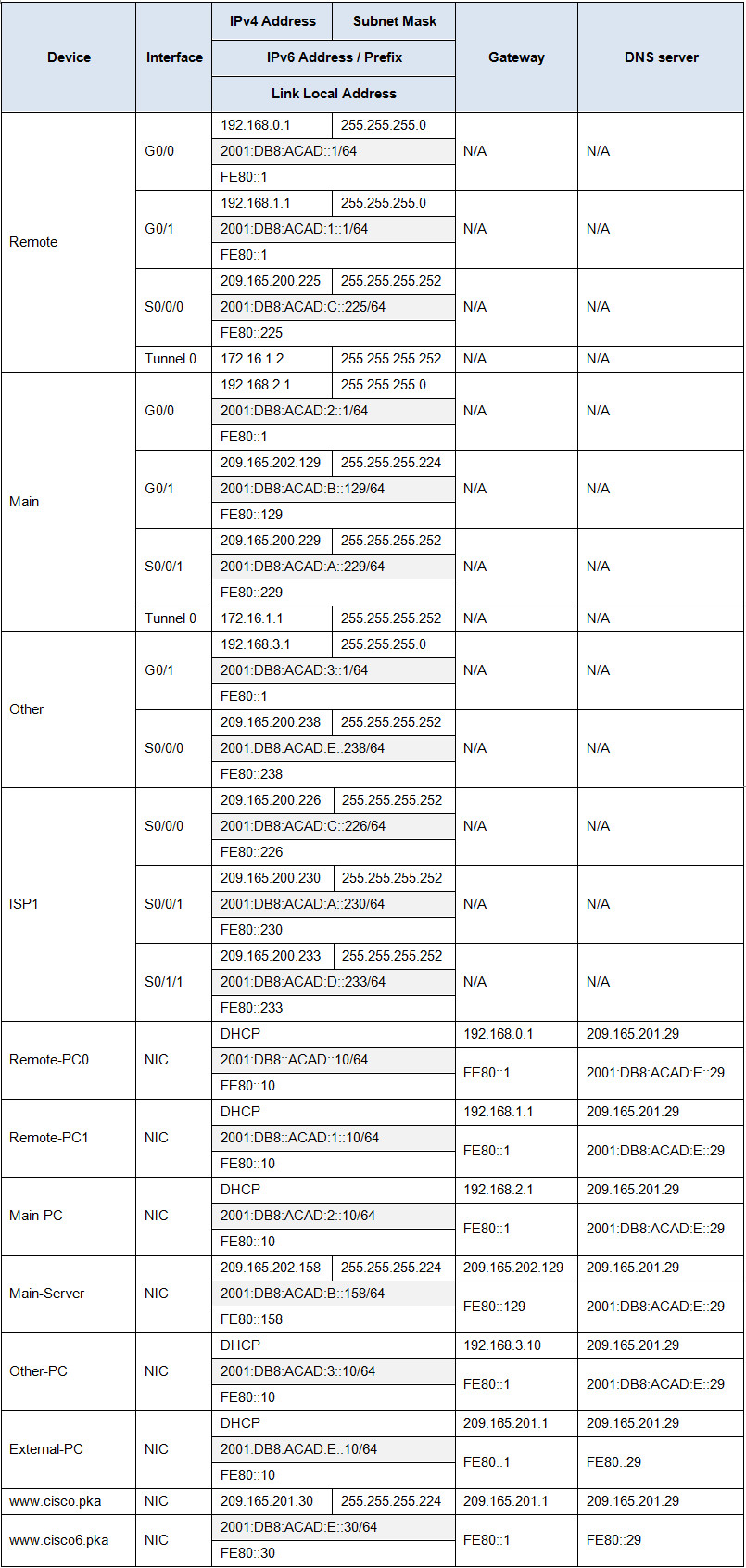
Addressing Table
Instructions
Step 1: Configure PPP encapsulation and authentication.
a. Configure PPP encapsulation for the link between Main and ISP1 and the link between Remote and ISP1.
b. Configure CHAP authentication between the links.
c. Configure the correct username and the password 321cisco for CHAP authentication on both Main and Remote.
Step 2: Configure a GRE tunnel with routing.
a. Configure a GRE tunnel between Main and Remote.
b. Configure OSPF 1 to route the traffic between the LANs of Main and Remote through the GRE tunnel. Summarize the networks attached to Remote.
Step 3: Configure BGP.
Configure BGP between ISP1 in Internet cluster and 209.165.202.128/27 network on Main.
a. Use AS number 65020 for Main.
b. Configure ISP1 as the BGP neighbor.
c. Only advertise the 209.165.202.128 / 27 network into BGP.
Step 4: Configure ACLs for NAT.
a. Configure a standard access list numbered 1 on Remote to allow NAT for hosts in network 192.168.0.0 /23.
b. Configure a standard access list numbered 1 on Main to allow NAT for hosts in network 192.168.2.0 /24.
c. Configure a standard access list numbered 1 on Other to allow NAT for hosts in network 192.168.3.0 /24.
Step 5: Configure a standard ACL to restrict remote access to the Other router.
A standard ACL named VTY_ADMIN is configured to limit access via VTY to the Other router. This ACL will only allow hosts from the LAN attached to the G0/1 interface and the hosts from the LANs on Remote router to access the Other router. All the other connections to VTY should fail.
a. Configure one ACL named VTY_ADMIN with three ACEs in the following order:
1) Allow any hosts from the LAN attached to the G0/1 interface of Other router to access the router.
2) Allow the hosts from the LANs in the Remote network to Other router remotely.
3) All other remote connections are denied.
b. Apply the ACL to the appropriate interface.
Note: Use the public IPv4 addresses in the ACLs when the private IPv4 addresses have been mapped to public IPv4 addresses.
Step 6: Configure an extended ACL to restrict access to the Main LAN.
a. Configure an extended ACL named HTTP_ACCESS that allows Remote LANs, Other LANs and the LAN inside Main to access Main-Server via the web browser.
Configure this ACL with the following 5 ACEs in the following order:
1) Allow the hosts from the Remote network to access the Main-Server.
2) Allow the hosts from the Other LANs to access the Main-Server.
3) Allow the internal network 192.168.2.0 /24 to access the Main-Server.
4) Allow ICMP replies to Main-Server from any networks.
5) Explicitly deny all other traffic from accessing the Main-Server.
b. Apply the ACL to the Main G0/1 interface.
Note: Use the public IPv4 addresses in the ACLs when the private IPv4 addresses have been mapped to public IPv4 addresses.
Step 7: Configure an IPv6 access list to restrict access to the Main LAN.
a. Configure an IPv6 access list named HTTP6_ACCESS that allows Remote LANs, Other LANs and the LAN inside Main to access Main-Server via the web browser.
b. Configure this ACL with the following 6 ACEs in the following order:
1) Allow the hosts from the Remote (2001:DB8:ACAD::/64) to access the Main-Server.
2) Allow the hosts from the Remote (2001:DB8:ACAD:1::/64) to access the Main-Server.
3) Allow the hosts from the Other LANs to access the Main-Server.
4) Allow the internal network 2001:DB8:ACAD:2::/64 to access the Main-Server.
5) Allow ICMP from Main-Server to the other networks.
6) Explicitly deny all other traffic from accessing the Main-Server.
c. Apply the ACL to the Main G0/1 interface.
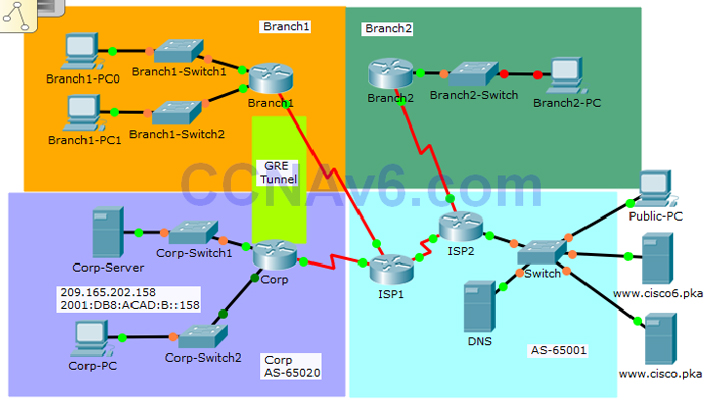
A few things to keep in mind while completing this activity:
- Do not use the browser Backbutton or close or reload any Exam windows during the exam.
- Do not close Packet Tracer when you are done. It will close automatically.
- Click the Submit Assessmentbutton to submit your work.
Objectives
In this Packet Tracer Skills Based Assessment, you will do as follows:
- Configure PPP encapsulation and CHAP authentication for serial links.
- Configure a GRE tunnel.
- Configure OSPF.
- Configure BGP.
- Configure standard and extended IPv4 ACLs.
- Configure IPv6 ACLs.
For the sake of time, many repetitive, but important, configuration tasks have been omitted from this assessment. Many of these tasks, especially those related to security, are essential elements of a network configuration. The intent of this activity is not to diminish the importance of full device configurations.
The IP addresses for all the devices have been configured and some of the routing configurations are already completed in this activity.
You are required to configure the devices as follows:
Branch1:
- Configure PPP and CHAP authentication on the appropriate interface.
- Configure GRE tunnel.
- Configure OSPF.
- Configure standard IPv4 ACL.
Branch2:
- Configure standard IPv4 ACLs.
Corp:
- Configure PPP and CHAP authentication on the appropriate interface.
- Configure GRE tunnel.
- Configure OSPF.
- Configure standard and extended IPv4 ACLs.
- Configure IPv6 ACLs.
Note: All the routers in AS 65001 are locked and no configurations are performed by the students. Furthermore, all the switches are pre-configured.
Addressing Table
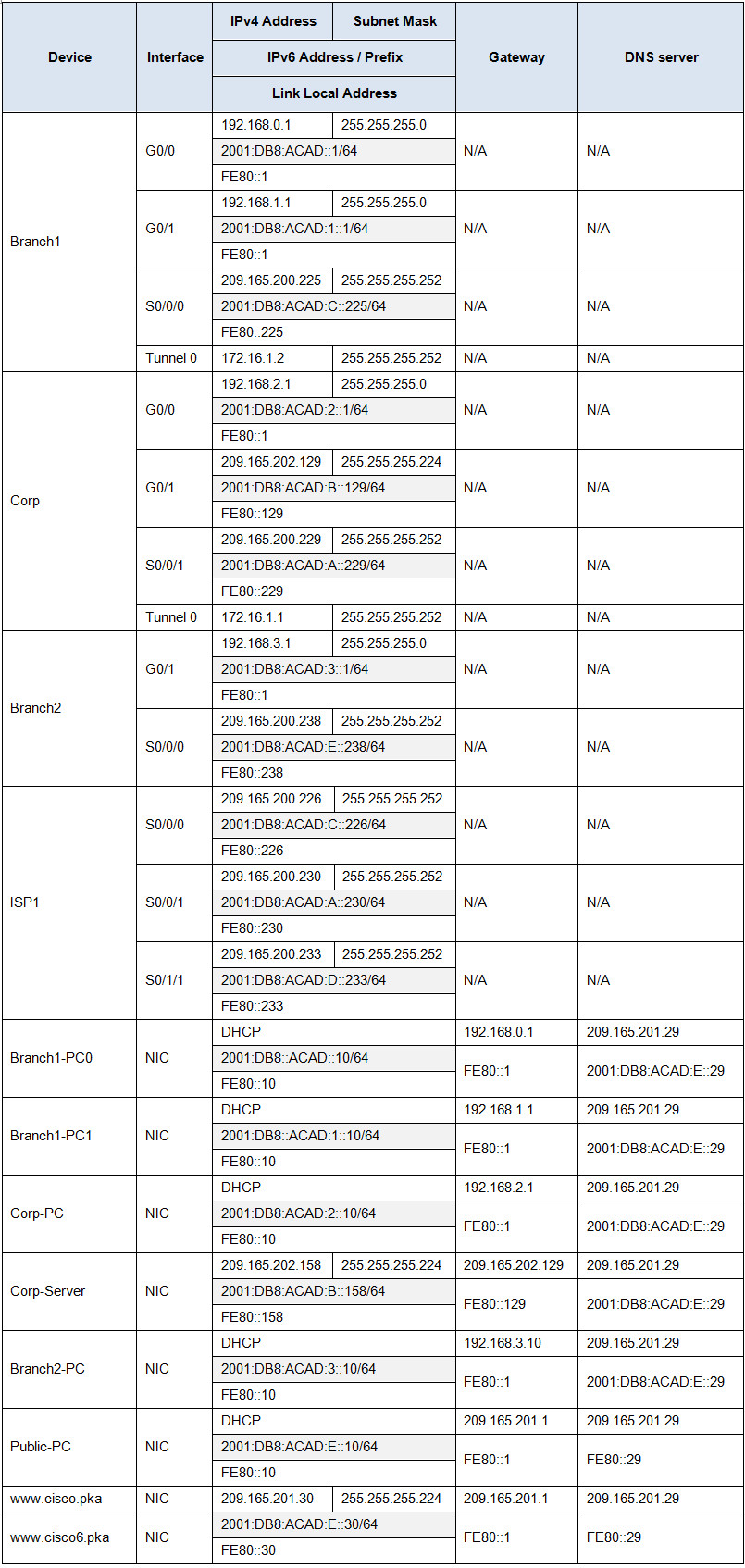
Instructions
Step 1: Configure PPP encapsulation and authentication.
a. Configure PPP encapsulation for the link between Corpand ISP1 and the link between Branch1 and ISP1.
b. Configure CHAP authentication between the links.
c. Configure the correct username and the password Ciscofor CHAP authentication on both Corp and Branch1.
Step 2: Configure a GRE tunnel with routing.
a. Configure a GRE tunnel between Corpand Branch1.
b. Configure OSPF 1to route the traffic between the LANs of Corp and Branch1 through the GRE tunnel. Summarize the networks attached to Branch1.
Step 3: Configure BGP.
Configure BGP between ISP1 in Internet cluster and 209.165.202.128/27 network on Corp.
a. Use AS number 65020for Corp.
b. Configure ISP1as the BGP neighbor.
c. Only advertise the 209.165.202.128 / 27network into BGP.
Step 4: Configure ACLs for NAT.
a. Configure a standard access list numbered 1on Branch1 to allow NAT for hosts in network 192.168.0.0 /23.
b. Configure a standard access list numbered 1on Corp to allow NAT for hosts in network 192.168.2.0 /24.
c. Configure a standard access list numbered 1on Branch2 to allow NAT for hosts in network 192.168.3.0 /24.
Step 5: Configure a standard ACL to restrict remote access to the Branch2 router.
A standard ACL named VTY_ADMIN is configured to limit access via VTY to the Branch2 router. This ACL will only allow hosts from the LAN attached to the G0/1 interface and the hosts from the LANs on Branch1 router to access the Branch2 router. All the other connections to VTY should fail.
a. Configure one ACL named VTY_ADMINwith three ACEs in the following order:
1) Allow any hosts from the LAN attached to the G0/1 interface of Branch2 router to access the router.
2) Allow the hosts from the LANs in the Branch1 network to Branch2 router remotely.
3) All other remote connections are denied.
b. Apply the ACL to the appropriate interface.
Note: Use the public IPv4 addresses in the ACLs when the private IPv4 addresses have been mapped to public IPv4 addresses.
Step 6: Configure an extended ACL to restrict access to the Corp LAN.
a. Configure an extended ACL named HTTP_ACCESSthat allows Branch1 LANs, Branch2 LANs and the LAN inside Corp to access Corp-Server via the web browser.
Configure this ACL with the following 5 ACEs in the following order:
1) Allow the hosts from the Branch1 network to access the Corp-Server.
2) Allow the hosts from the Branch2 LANs to access the Corp-Server.
3) Allow the internal network 192.168.2.0 /24 to access the Corp-Server.
4) Allow ICMP replies to Corp-Server from any networks.
5) Explicitly deny all other traffic from accessing the Corp-Server.
b. Apply the ACL to the CorpG0/1 interface.
Note: Use the public IPv4 addresses in the ACLs when the private IPv4 addresses have been mapped to public IPv4 addresses.
Step 7: Configure an IPv6 access list to restrict access to the Corp LAN.
a. Configure an IPv6 access list named HTTP6_ACCESSthat allows Branch1 LANs, Branch2 LANs and the LAN inside Corp to access Corp-Server via the web browser.
b. Configure this ACL with the following 6 ACEs in the following order:
1) Allow the hosts from the Branch1 (2001:DB8:ACAD::/64) to access the Corp-Server.
2) Allow the hosts from the Branch1 (2001:DB8:ACAD:1::/64) to access the Corp-Server.
3) Allow the hosts from the Branch2 LANs to access the Corp-Server.
4) Allow the internal network 2001:DB8:ACAD:2::/64 to access the Corp-Server.
5) Allow ICMP from Corp-Server to the other networks.
6) Explicitly deny all other traffic from accessing the Corp-Server.
c. Apply the ACL to the CorpG0/1 interface.
Answers – Intructions
On Router 1: HQ – Main – Corp (Note: Username & Password for CHAP authentication)
en
conf ter
username ISP1 password cisco123 (or Cisco or 321cisco)
int s0/0/0
encapsulation ppp
ppp authentication chap
exit
interface tunnel 0
ip address 172.16.1.1 255.255.255.252
tunnel source s0/0/0
tunnel destination 209.165.200.225
tunnel mode gre ip
exit
router ospf 1
network 192.168.2.0 0.0.0.255 area 0
network 172.16.1.0 0.0.0.3 area 0
exit
router bgp 65020
network 209.165.202.128 mask 255.255.255.224
neighbor 209.165.200.230 remote-as 65001
exit
access-list 1 permit 192.168.2.0 0.0.0.255
ip access-list extended HTTP_ACCESS
permit tcp host 209.165.200.225 host 209.165.202.158 eq 80
permit tcp host 209.165.200.238 host 209.165.202.158 eq 80
permit ip 192.168.2.0 0.0.0.255 host 209.165.202.158
permit icmp any host 209.165.202.158 echo-reply
deny ip any any
int g0/1
ip access-group HTTP_ACCESS out
exit
ipv6 access-list HTTP6_ACCESS
permit tcp 2001:DB8:ACAD::/64 host 2001:DB8:ACAD:B::158 eq 80
permit tcp 2001:DB8:ACAD:1::/64 host 2001:DB8:ACAD:B::158 eq 80
permit tcp 2001:DB8:ACAD:3::/64 host 2001:DB8:ACAD:B::158 eq 80
permit ipv6 2001:DB8:ACAD:2::/64 host 2001:DB8:ACAD:B::158
permit icmp any host 2001:DB8:ACAD:B::158 echo-reply
deny ipv6 any host 2001:DB8:ACAD:B::158
interface g0/1
ipv6 traffic-filter HTTP6_ACCESS out
On Router 2: Branch – Remote – Branch1 (Note: Username & Password for CHAP authentication)
en
conf ter
username ISP1 password cisco123 (or Cisco or 321cisco)
int s0/0/0
encapsulation ppp
ppp authentication chap
exit
interface tunnel 0
ip address 172.16.1.2 255.255.255.252
tunnel source s0/0/0
tunnel destination 209.165.200.229
tunnel mode gre ip
exit
router ospf 1
network 172.16.1.0 0.0.0.3 area 0
network 192.168.0.0 0.0.0.255 area 0
network 192.168.1.0 0.0.0.255 area 0
exit
access-list 1 permit 192.168.0.0 0.0.1.255
On Router 3: Customer – Other – Branch2
en conf t access-list 1 permit 192.168.3.0 0.0.0.255 ip access-list standard VTY_ADMIN permit 192.168.3.0 0.0.0.255 permit host 209.165.200.225 deny any line vty 0 4 access-class VTY_ADMIN in

100% with the script below:
@@@@@@@@@@@@@@@@@ On Router 1: HQ – Main – Corp
En
Config t
Int s0/0/0
Encapsulation ppp
Ppp authentication chap
Exit
Username ISP1 password cisco123
Int Tunnel 0
Tunnel mode gre ip
Tunnel source s0/0/0
Tunnel destination 209.165.200.225
Ip address 172.16.1.1 255.255.255.252
exit
router ospf 1
network 192.168.2.0 0.0.0.255 area 0
network 172.16.1.0 0.0.0.3 area 0
exit
route bgp 65020
neighbor 209.165.200.230 remote-as 65001
network 209.165.202.128 mask 255.255.255.224
exit
access-list 1 permit 192.168.2.0 0.0.0.255
exit
exit
en
config t
ip access-list extended HTTP_ACCESS
permit tcp host 209.165.200.225 host 209.165.202.158 eq 80
permit tcp host 209.165.200.238 host 209.165.202.158 eq 80
permit ip 192.168.2.0 0.0.0.255 host 209.165.202.158
permit icmp any host 209.165.202.158 echo-reply
deny ip any any
exit
int g0/1
ip access-group HTTP_ACCESS out
exit
ipv6 access-list HTTP6_ACCESS
permit tcp 2001:DB8:ACAD::/64 host 2001:DB8:ACAD:B::158 eq 80
permit tcp 2001:DB8:ACAD:1::/64 host 2001:DB8:ACAD:B::158 eq 80
permit tcp 2001:DB8:ACAD:3::/64 host 2001:DB8:ACAD:B::158 eq 80
permit ipv6 2001:DB8:ACAD:2::/64 host 2001:DB8:ACAD:B::158
permit icmp any host 2001:DB8:ACAD:B::158 echo-reply
int g0/1
ipv6 traffic-filter HTTP6_ACCESS out
exit
@@@@@@@@@@@@@@@@@ On Router 2: Branch – Remote – Branch1
En
Config t
Int s0/0/0
Encapsulation ppp
Ppp authentication chap
Exit
username ISP1 password cisco123
int Tunnel 0
tunnel mode gre ip
tunnel source s0/0/0
tunnel destination 209.165.200.229
ip address 172.16.1.2 255.255.255.252
exit
router ospf 1
network 192.168.0.0 0.0.0.255 area 0
network 192.168.1.0 0.0.0.255 area 0
network 172.16.1.0 0.0.0.3 area 0
exit
exit
en
config t
access-list 1 permit 192.168.0.0 0.0.1.255
@@@@@@@@@@@@@@@@@ On Router 3: Customer – Other – Branch2
en
conf t
access-list 1 permit 192.168.3.0 0.0.0.255
ip access-list standard VTY_ADMIN
permit 192.168.3.0 0.0.0.255
permit host 209.165.200.225
deny any
exit
line vty 0 4
access-class VTY_ADMIN in
exit
ip access-list extended HTTP_ACCESS
100% i done it today thanks!
I got 100% Thanks :) I’m frustrated with 85% before….
Thanks!!! 100% Just finished!
Hello sir. I have the same lab scenario as yours just routers names are changed but my extended ACLs don’t work even IP addresses are the same as yours.
Admin kindly help me with my query.
Hi, I want to download the packettracert file to this lab ?
HI, is this the final exam for CCNA 4?
No, this is a practice skill exam, after this test will the final exam.
HI, is this the final exam for CCNA 4? I am asking because scan ospf and scan eigrp are inluded in ccna 3, same with rse 3 , are part of ccna 3, scaling networks , for this reason I don’t understand why are in this ccna 4. I would appreciatte if someone can answer. Thanks
Yes, this is final practice skill for CCNA 4.
Hi there I have written everything down from the black screen, what was incorrect?. I need to know asap as I have an exam today, so please get back to me soon.
Please note that the passwords of routers are different in a different in each type
Is everything up to date on the black screen you have provided with the commands?
At step 7 you forgot “deny any any” which is actually the 6th ACE. 6 ACE is required in step 7.
And the correct HQ configuration is “tunnel source s0/0/1 not s0/0/0
excuse “deny ipv6 any any”
Thanks u!
I just finished the exam last January 10, 2019, I got 100% from the configurations stated above, hope this info helps.
do you mean the commands given in the black screen?
i got a 97% on this, but the only problem I have is the VTY_ADMIN
Fixed VTY_ADMIN, please try again and please comment your results, thanks :)
On Router: Customer – Other – Branch2 (Access-list)
change the network address from 209.165.200.225 0.0.0.3 to 209.165.200.224 0.0.0.3
***************************************************************************************
Access-list 1 permit 192.168.3.0 0.0.0.255
ip access-list standard VTY_ADMIN
permit 192.168.3.0 0.0.0.255
permit 209.165.200.224 0.0.0.3
deny any
Line vty 0 4
Access-class VTY_ADMIN in
Some of the configurations are missing and wrong….
For HQ – Main – Corp: (Add the Tunnel Mode at the end of Tunnel configuration)
—————————————–
interface tunnel 0
ip address 172.16.1.1 255.255.255.252
tunnel source s0/0/0
tunnel destination 209.165.200.225
tunnel mode gre ip
exit
For Branch – Remote – Branch1: (Add the Tunnel Mode at the end of Tunnel configuration, change the wildcard mask of 192.168.0.0 from 0.0.1.255 to 0.0.0.255, and Add the network of 192.168.1.0 to the OSPF)
—————————————–
interface tunnel 0
ip address 172.16.1.2 255.255.255.252
tunnel source s0/0/0
tunnel destination 209.165.200.229
tunnel mode gre ip
exit
router ospf 1
network 192.168.0.0 0.0.0.255 area 0
network 192.168.1.0 0.0.0.255 area 0
network 172.16.1.0 0.0.0.3 area 0
exit
Thanks so much
dear brother, please kindly reply me , where i am found .pkt question for practice.
Hi friends
in your configuration IPv4 ACL the addressing networks are wrong and you did not used wildcard mask so I think the correct answers are as folows
*******************************************************
ip access-list extended HTTP_ACCESS
permit tcp 209.165.200.224 0.0.0.3 host 209.165.202.158 eq 80
permit tcp 209.165.200.236 0.0.0.3 host 209.165.202.158 eq 80
permit ip 192.168.2.0 0.0.0.255 any
permit icmp any any echo-reply
deny ip any any
ipv6 access-list HTTP6_ACCESS
permit tcp 2001:DB8:ACAD::/63 host 2001:DB8:ACAD:B::158 eq 80
permit tcp 2001:DB8:ACAD:3::/64 host 2001:DB8:ACAD:B::158 eq 80
permit ipv6 2001:DB8:ACAD:2::/64 any
permit icmp any any echo-reply
deny ipv6 any any
Thanks so much!! :)
why in 1st line at HTTP6_ACCESS
the prefix is \63
I found in Corp-Server the DNS for ip and ipv4 changed. I am not sure….just have a look
Still 94%?
can you pliz give us the option to unlock the topology
I just finished the exam; I got 94%
For VTY_ADMIN ACL
instead of the line
permit host 209.165.200.225
Use this:
permit 209.165.200.225 0.0.0.3
Updated. Thanks MrBunnyHat! :)
Try this
****************************************
ip access-list extended HTTP_ACCESS
permit tcp 209.165.200.224 0.0.0.3 host 209.165.202.158 eq 80
permit tcp 209.165.200.236 0.0.0.3 host 209.165.202.158 eq 80
permit ip 192.168.2.0 0.0.0.255 any
permit icmp any any echo-reply
deny ip any any
*********************************
ipv6 access-list HTTP6_ACCESS
permit tcp 2001:DB8:ACAD::/63 host 2001:DB8:ACAD:B::158 eq 80
permit tcp 2001:DB8:ACAD:3::/64 host 2001:DB8:ACAD:B::158 eq 80
permit ipv6 2001:DB8:ACAD:2::/64 any
permit icmp any any echo-reply
deny ipv6 any any
Thanks so much!! :)
Hi friend sorry but your network address (permit 209.165.200.225 0.0.0.3) is wrong
so the correct answer is
permit 209.165.200.224 0.0.0.3
Thanks